As part of the Core Security Identity Governance and Administration portfolio of solutions, previously offered by Courion, the Visual Identity Suite (VIS) empowers organizations to see user privileges and access certifications in a whole new way—leveraging an intelligent, visual-first approach. With an easy-to-use, visual interface, you can see common user entitlements and quickly identify outliers to make informed decisions about who has access to what. VIS enables you to see what access looks like in your business, so you can intelligently mitigate identity risk, better enforce least privilege access, and manage identity chaos within your organization.
Identity Governance with an Intelligent, Visual-First Approach
Mitigating identity risk in your organization requires intelligent and visible identity governance across all of your environments. This means leveraging a visual-first approach for the creation and management of roles and access reviews, combined with intelligence-enabled context, to simplify your identity governance and administration processes.
It means using an industry-leading role designing tool with a graphical matrix display to group like-access privileges together, so you can better understand the access that individuals have in common and what outliers might be present. And it means adopting an easy-to-use, easy-to-understand access review method that enhances access certification accuracy by providing context and guidance so that users can better understand what they are reviewing.
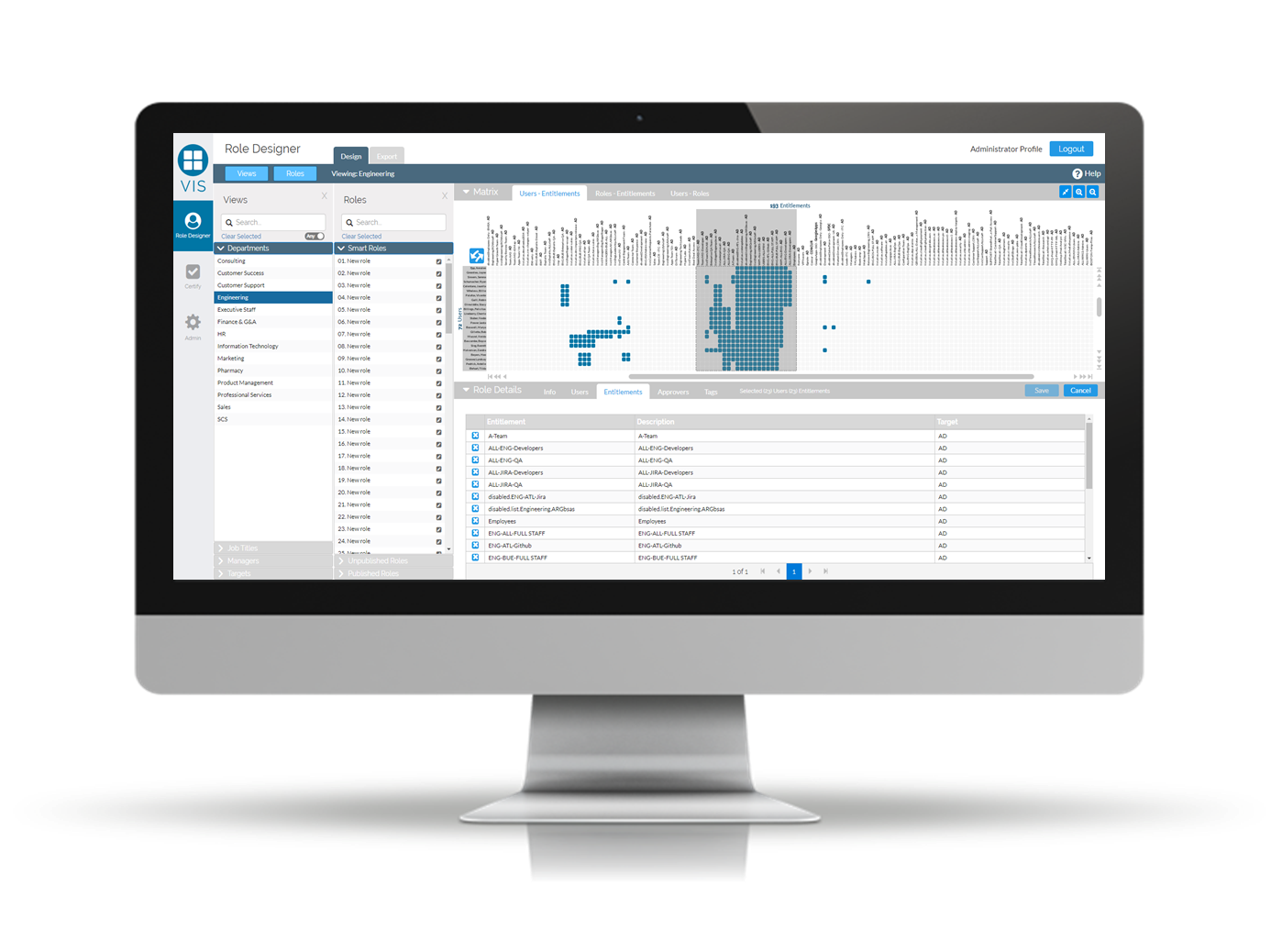
Visual Identity Suite is offered in a cloud delivery model and works with any Identity Governance and Administration solution. VIS features the following two product modules:
Core Role Designer
A modern way of building roles. With Core Role Designer, it is easy to see patterns of access that should define roles by examining the clusters of access across individual users. Common access clusters establish a clearly defined role.
A modern way of building roles. With Core Role Designer, it is easy to see patterns of access that should define roles by examining the clusters of access across individual users. Common access clusters establish a clearly defined role.
Core Certify
Deliver a visual-first approach by automatically clustering like-access together to simplify the access certification process. As part of this cloud-delivered suite, Core Certify allows managers to simultaneously accept or reject clusters of access for multiple users with just a few clicks, saving time, increasing accuracy, and reducing certification fatigue.
Deliver a visual-first approach by automatically clustering like-access together to simplify the access certification process. As part of this cloud-delivered suite, Core Certify allows managers to simultaneously accept or reject clusters of access for multiple users with just a few clicks, saving time, increasing accuracy, and reducing certification fatigue.
What Does the Visual Identity Suite Do?
Intelligent Role-Based Access
Organizations that apply access intelligence and incorporate a visual-first approach to role creation, access governance, and role management decrease identity-related risks across the business, enhance their security posture, and more effectively safeguard critical data, systems, and assets.
Core Role Designer shows logical groupings of users and entitlements that give you the intelligence, power, and control to create the right roles for your organization. This enables you to focus on role assignments rather than individual accounts, decreasing access risks and bolstering organizational security. Then as your business grows and evolves, Role Designer learns how your access environment is changing and can automatically suggest changes to role definitions. This reduces role-overlap, avoids overprovisioning, and incorporates new access so your role definitions keep pace with the access requirements of your users
Streamlined Access Certification
A visual-first approach that relies on intelligent-enabled context for access certification saves time and streamlines the entire identity governance process. But reviewing endless rows of entitlements, whether in a spreadsheet or in a web portal, without the necessary context to create accurate roles or certify access is overwhelming and complicated. And it often leads to rubber stamping, which causes security risks, inaccuracies, and an excessive distribution of access.
Core Certify simplifies the access certification process, while reducing identity-related risks. Leverage leading-edge graphical visualizations to clearly and quickly see common user entitlements and rapidly identify outliers. Accelerate and improve the accuracy of access reviews and approvals with the ability to easily and intelligently view user access and entitlements within the same dashboard.
Key Benefits
- Reduce identity-related access risks
- Simplify and streamline identity governance processes
- Safeguard critical data, systems, and assets
- Stay compliant with industry standards and government regulations
- Focus on role definitions and role assignments rather than individual accounts
- View privileges and access certifications through a user-friendly interface
- Keep pace with the evolving access requirements of your users
- Reduce the risk of errors and increase reviewer accuracy
- Save time and eliminate spreadsheets as part of the access review process
Enterprise Application Integrations with the Visual Identity Suite
An identity governance and administration solution is only as good as the data it can access. The Visual Identity Suite leverages end-to-end integrations with the most popular platforms, enterprise applications, systems, and identity providers available today, including Amazon Web Services, Microsoft Azure Active Directory, Okta, SailPoint, and Core Privileged Access Manager (BoKS). These powerful integrations streamline data collection, role assignments, and access remediation, ensuring you can easily integrate critical data from your most important applications into VIS.

