Reviewing endless rows of entitlements without the necessary context to certify access is overwhelming and complicated. And it often leads to rubber stamping, which causes security risks, inaccuracies, and an excessive distribution of access. As part of the Visual Identity Suite (VIS), Core Certify simplifies the access certification process, while reducing identity-related risks. With Core Certify, companies can leverage a visual-first approach to clearly and quickly see common user entitlements and rapidly identify outliers. Accelerate and improve the accuracy of access reviews and approvals with the ability to easily and intelligently view user access and entitlements within the same dashboard.
Streamlining the Access Review Process
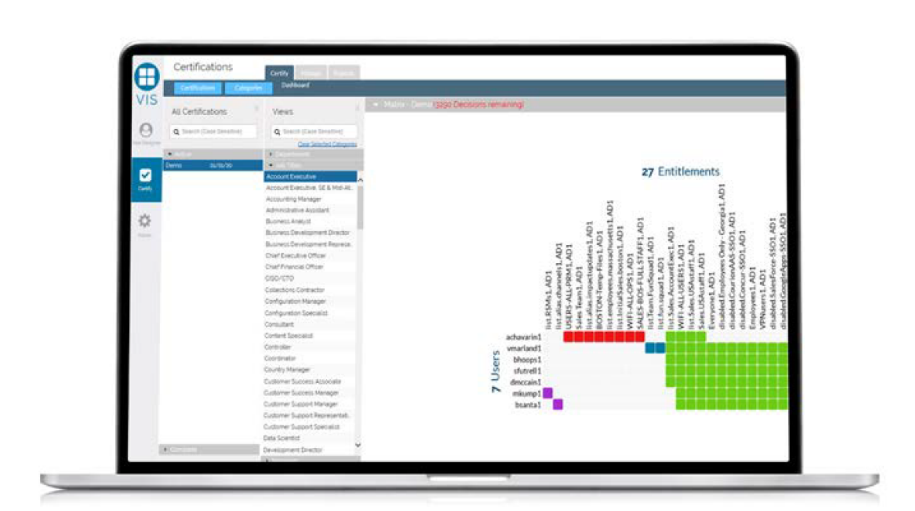
Evaluating entitlements without the right context is both complex and time consuming. But this is a common practice that often leads to excessive distribution of access. Underprovisioning users can also lead to increased risk and a lack of productivity if credential sharing occurs or users do not have the right access to do their jobs. For organizations to build a more effective identity governance program, they must empower managers and approvers to simplify the access review process.
The best way to do this is by seeing common user entitlements. This enables reviewers to easily compare access, adding essential context during the review process. Core Certify delivers a visual approach by automatically clustering like-access together. As part of the cloud-delivered VIS suite, managers can now accept or reject clusters of access—with just a few clicks—saving time, increasing accuracy, and reducing certification fatigue.
What Does Core Certify Do?
Simplifies the Complexity of Access Certifications
Certification reviews are complicated by a constantly changing group of users, compliance requirements, and system entitlements. With endless rows of entitlements to review, rubber stamping or bulk approvals are common—and that can lead to users having too much or too little access, which can magnify risks in your business. With Core Certify, you can enable access reviewers and managers the ability to easily accept or reject clusters of access—with just a few clicks—so you can streamline the entire access review process, saving time, boosting efficiencies, and enforcing least privilege access across your business.
Certification reviews are complicated by a constantly changing group of users, compliance requirements, and system entitlements. With endless rows of entitlements to review, rubber stamping or bulk approvals are common—and that can lead to users having too much or too little access, which can magnify risks in your business. With Core Certify, you can enable access reviewers and managers the ability to easily accept or reject clusters of access—with just a few clicks—so you can streamline the entire access review process, saving time, boosting efficiencies, and enforcing least privilege access across your business.
Reveals Common Entitlements
Without enough context in reviewing user access, managers may make uninformed decisions or simply give-up and approve everyone. With Core Certify, there are no more endless rows of entitlements to look through or outdated data to work from. Visualizations show you exactly what entitlements each user has, including nested or hidden entitlements, in a clear, concise view. The ability to see common clusters of entitlements, as well as outliers, empowers managers to take immediate action rather than working through a time-consuming process to determine who should have access to what systems, and when.
Without enough context in reviewing user access, managers may make uninformed decisions or simply give-up and approve everyone. With Core Certify, there are no more endless rows of entitlements to look through or outdated data to work from. Visualizations show you exactly what entitlements each user has, including nested or hidden entitlements, in a clear, concise view. The ability to see common clusters of entitlements, as well as outliers, empowers managers to take immediate action rather than working through a time-consuming process to determine who should have access to what systems, and when.
Key Benefits
- View privileges and access certifications through a user-friendly graphical interface
- Approve, deny, or delegate access with just a few clicks
- See outliers and immediately take action to remediate
- Continuously monitor access and ensure readiness for compliance audits
- End rubber stamping and bulk approvals with data that stays up-to-date
- Average deployment time is hours, not weeks or months
Key Features
Enterprise Application Integrations with Visual Identity Suite
An identity governance and administration solution is only as good as the data it can access. The Visual Identity Suite leverages end-to-end integrations with the most popular platforms, enterprise applications, systems, and identity providers available today, including Amazon AWS, Microsoft Azure Active Directory, Okta, SailPoint, and Core Privileged Access Manager (BoKS). These powerful integrations streamline data collection, role assignments, and access remediation, ensuring you can easily integrate critical data from your most important applications into VIS.
See Core Certify in Action
Discover how Core Certify enables your organization to save time, improve access review accuracy, meet regulatory compliance, and enforce least privilege access with a free 14-day trial.
