Enhance your penetration testing efforts while maintaining efficiency and consistency with Core Impact Pro.
A one year license of Core Impact Pro is $12,600*. Core Impact can also be bundled with our advanced adversary simulation tool, Cobalt Strike, for $15,750*.
*Pricing for US Only
Start the Purchase Process in Three Simple Steps
Fill out the form to the right.
Complete a brief vetting process, required by the government since Core Impact is a powerful penetration testing tool that uses the same techniques as threat actors.
Receive your Core Impact license(s) and begin pen testing.

| Core Impact | Basic $9,450* user/year |
Pro $12,600* user/year |
Enterprise Varied Pricing |
|---|---|---|---|
|
TESTS
|
|||

|

|

|
|

|

|
||

|
|||

|
|||
|
FEATURES
|
|||

|

|

|
|

|

|

|
|

|

|

|
|

|

|

|
|

|

|

|
|

|

|

|
|

|

|
||

|

|
||

|

|
||

|
|||

|
|||

|
|||
|
Customer Portal and email support
|
Customer Portal and email support
|
Phone, Customer Portal and email support
|
|
|
INTEROPERABILITY
|
|||

|

|

|
|
Not sure which package is right for you?
After completing the form on this page, you'll be contacted by one of our experts, who can consult with you on which version of Core Impact will best suit your unique business needs.
Why Choose Core Impact?
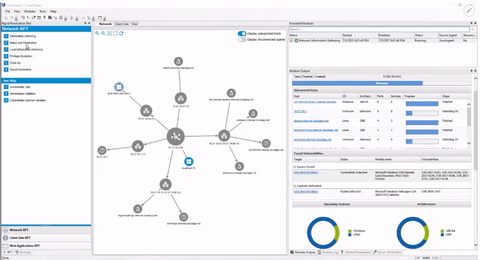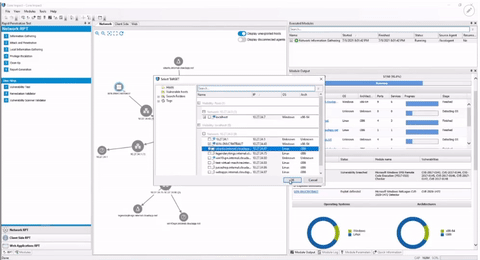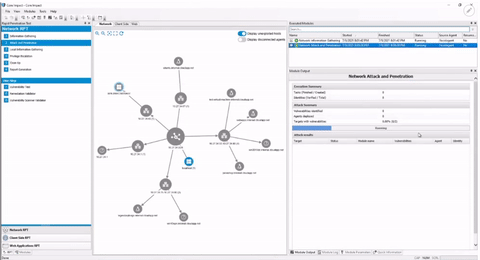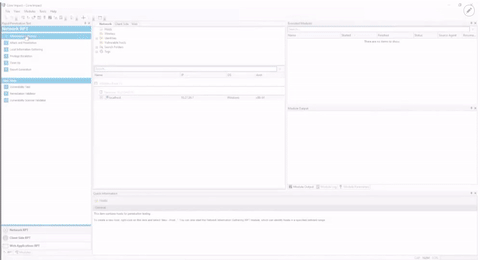
Core Impact is simple enough for your first test, but powerful enough for the rest. Whether you are looking to automate routine testing or simply validate remediation effectiveness, Core Impact can help you meet your penetration testing goals.
Use intuitive automation wizards to swiftly discover, test, and report.
Explore a stable library of professionally written and validated exploits.
Centralize your pen testing toolkit—from information gathering to reporting.
