What Is Privileged Access Management (PAM)?
Privileged Access Management, also known as PAM, is a critical security control that enables organizations to simplify how they define, monitor, and manage privileged access across their IT systems, applications, and infrastructure.

Because administrator accounts have elevated privileges that can access valuable data and execute applications or transactions—often with little or no tracking control—it can be very difficult to manage privileged accounts. Privileged Access Management software centralizes management of administrator profiles and ensures the principle of least privilege access is enforced to give users only the access they need.
Organizations rely on PAM security not only for its efficiency, but also because they are often mandated by regulations, including Sarbanes-Oxley (SOX) Section 404, the Federal and North American Energy Regulations Commission (FERC/NERC), HIPAA 2, and state level regulations such as the California Information Practice Act and the Massachusetts privacy law 201CMR17.
Read More >
PASM and PEDM
As Privileged Access Management has evolved, Gartner has established two further classifications to highlight different mechanisms of PAM solutions. These include Privileged Account and Session Management (PASM) and Privilege Elevation and Delegation Management (PEDM). PASM and PEDM are two categories of security tools that have distinct approaches in how they manage access. Both PASM and PEDM tools use the principle of least privilege, which mandates that users only have the access necessary to their job functions. While both solutions have the same goals, they have different mechanisms in how the target account is protected and accessed.
Read More >
PASM
PASM solutions are often referred to as password vaulting. Privileged account credentials are securely created and distributed exclusively by the solution. When users need access to a specific server, they request access from the vault, and are given a temporary account with full administrative privileges. This account is only valid for a single session. Additionally, the session activity is monitored and recorded.
PEDM
PEDM solutions distribute access privilege based on job roles. Instead of using temporary privileged accounts, PEDM tools assign permanent privilege to standard accounts. PEDM tools define who can have access to each part of a system as well as what they can do with that access.
What Are Privileged Accounts?
Privileged accounts are considered elevated accounts within your IT environment that hold the 'keys to the kingdom.' These types of accounts frequently have privileges to access valuable data and execute any application or transaction, typically with little or no tracking or control. A privileged account can take the form of an Administrator in Windows environments or Root in UNIX or Linux environments.
Each organization should determine what is classified as privileged data, where it is, and who has access to it. Control of privileged accounts is a major factor in compliance across regulations in every industry. Here are common types of privileged accounts:
- Local Admin Accounts
- Privileged User Accounts
- Domain Admin Accounts
- Emergency User Accounts
- Service Accounts
- Application Accounts
Because of their elevated access, privileged accounts have more significant risks than non-privileged accounts and have more potential for exploit or abuse. Privileged accounts, which can number in the hundreds in some enterprises, are frequently not tied to specific individuals, so the accounts can be used to do virtually anything, with little or no possibility of detection.
Read More >
How to Select the Right PAM Approach
Organizations struggling to achieve effective protection of privileged and root accounts often wonder what the best approach to Privileged Access Management is for their business. Here we examine three of the most common approaches to PAM security within organizations today:
Home-Grown Privileged Access Management
Home-grown solutions are typically based on operating system capabilities, available utilities such as 'sudo,' clever password management procedures, and a lot of scripts. Home-grown solutions can become extremely costly and require system administrators to do considerable programming. Home-grown solutions are also often found insufficient from an auditor’s perspective. With sensitive information subject to insider threats, the capabilities of home-grown solutions are quickly superseded.
Home-grown solutions are typically based on operating system capabilities, available utilities such as 'sudo,' clever password management procedures, and a lot of scripts. Home-grown solutions can become extremely costly and require system administrators to do considerable programming. Home-grown solutions are also often found insufficient from an auditor’s perspective. With sensitive information subject to insider threats, the capabilities of home-grown solutions are quickly superseded.
Combination of Open Source and Commercial PAM Solutions
Some organizations look to combine various commercial or open source point solutions to create an operating system environment that provides an effective approach to protecting privileged accounts. This typically involves using one solution for user provisioning, another for centrally managed secure communications (SSH), a third for password management, and possibly another tool for audit log consolidation.
While combined solutions can amount to something powerful, one important aspect is lost: centralized access management on one security system. Combining multiple technical solutions into one leaves conceptual gaps, which in turn lead to security flaws and inefficient management. And while cost-focus may be the primary driver for this option, it typically ends up costing more and exposing organizations up to more risk than commercial options.
Some organizations look to combine various commercial or open source point solutions to create an operating system environment that provides an effective approach to protecting privileged accounts. This typically involves using one solution for user provisioning, another for centrally managed secure communications (SSH), a third for password management, and possibly another tool for audit log consolidation.
While combined solutions can amount to something powerful, one important aspect is lost: centralized access management on one security system. Combining multiple technical solutions into one leaves conceptual gaps, which in turn lead to security flaws and inefficient management. And while cost-focus may be the primary driver for this option, it typically ends up costing more and exposing organizations up to more risk than commercial options.
Commercial Privileged Access Management Solutions
Organizations that want to centralize management of their privileged accounts, secure systems without slowing down productivity, and easily enforce least privileged access look to commercially available PAM solutions. Investing in an agile Privileged Access Management solution specific to your multi-platform environment provides all of the components needed for effectively protecting privileged and root accounts both proactively and adaptively, without all of the overhead, costs, and complexities of full-blown identity and access management infrastructures.
Commercial PAM solutions simplify an organization’s ability to enforce security policies, control access to critical systems and information, and provide full control over accounts, access and privilege, so IT and security teams can proactively prevent internal and external critical system attacks before they start.
Organizations that want to centralize management of their privileged accounts, secure systems without slowing down productivity, and easily enforce least privileged access look to commercially available PAM solutions. Investing in an agile Privileged Access Management solution specific to your multi-platform environment provides all of the components needed for effectively protecting privileged and root accounts both proactively and adaptively, without all of the overhead, costs, and complexities of full-blown identity and access management infrastructures.
Commercial PAM solutions simplify an organization’s ability to enforce security policies, control access to critical systems and information, and provide full control over accounts, access and privilege, so IT and security teams can proactively prevent internal and external critical system attacks before they start.
What Are the Benefits of PAM Solutions?
Improve Security with Granular Privileged Access Controls
Effective Privileged Access Management defines who can have access to each part of a system and specifies what they can do with that access. This eliminates privileged password sharing and enables you to track administrator and account activities in detail so you can specifically identify who has done what.
Read More >
Enforce Security Controls Across Your Multi-Platform Environment
Many organizations are running heterogenous Linux and UNIX server environments with a mix of legacy systems alongside new infrastructure, including on-premise servers, private cloud, and/or public cloud deployments. Managing privileged access and enforcing security policies across a variety of systems, operating systems, and environments is difficult and inefficient without the right tools in place. PAM solutions provide control over accounts and privileged access, making sure that the principle of least privilege is applied across your environment.
Extend Security to the Cloud
It is important for organizations to employ synchronized policies across on-premise and cloud environments, especially within a multi-platform Linux and UNIX environment, to effectively strengthen data security, maintain operations, and prepare for regulatory audits. Centrally managing accounts and privileged access across your on-premise and cloud environments with PAM enforces consistent security controls and provides seamless management across technology stacks.
Read More >
Ensure Compliance
Meet compliance regulations, such as PCI-DSS, HIPAA, and SOX, by architecting security into your deployment from the start. PAM solutions enable organizations to increase the granularity of access enforcement and easily meet strict compliance regulations. And automated compliance reporting provides auditors with the information they need without interrupting administrative staff.
Why Privileged Access Management Is Important
For the second year in a row, Privileged Access Management (PAM) is listed as a top security priority by Gartner. Despite being around for decades, PAM security tools are becoming increasingly vital as access privileges become more complex. In fact, experts predict that more than two thirds of organizations will implement privileged access management in their enterprise in the coming years.
Effectively managing privileged access has become a top priority for many organizations seeking to protect their data and systems from unauthorized users. That’s because inappropriate access can expose valuable organizational data, compromise sensitive information, and adversely affect system reliability. But with full control over privileged accounts, IT and security teams can help prevent internal and external attacks on critical systems before they start.
The latest Verizon Data Breach Investigations Report found that the majority of data breaches leverage privileged accounts directly. With compromised credentials a leading cause of data breaches, organizations cannot afford to ignore the importance of privileged access management. And more than ever before, companies are looking for more effective and efficient ways to protect their data with PAM solutions.
Regulatory compliance is only getting more intense as technology becomes more sophisticated. Privileged access management enables organizations to adhere to requirements. To remain compliant, many industries, particularly those dealing with sensitive information, like financial institutions, require frequent password changes.

PAM solutions reduce or eliminate the need to share passwords because technical controls restrict access only to authorized users, and can leverage stronger authentication methods.
Privileged access management is also ideal to combat insider threats and enforce the principle of least privilege, which mandates that users only have the access necessary to their job functions. Linking access to job roles, and subsequently, individual accounts, eliminates the need for superusers that have universal access. These tools can also require additional authorization for high-risk servers, providing additional protection. Finally, privileged access management provides user accountability through means like keystroke logging.
Read More >
What Are Requirements for Controlling Privileged Accounts?
The challenges associated with controlling privileged and root accounts within a multi-platform environment increases quickly as the number of people who need powerful administrative access for various job functions grows.
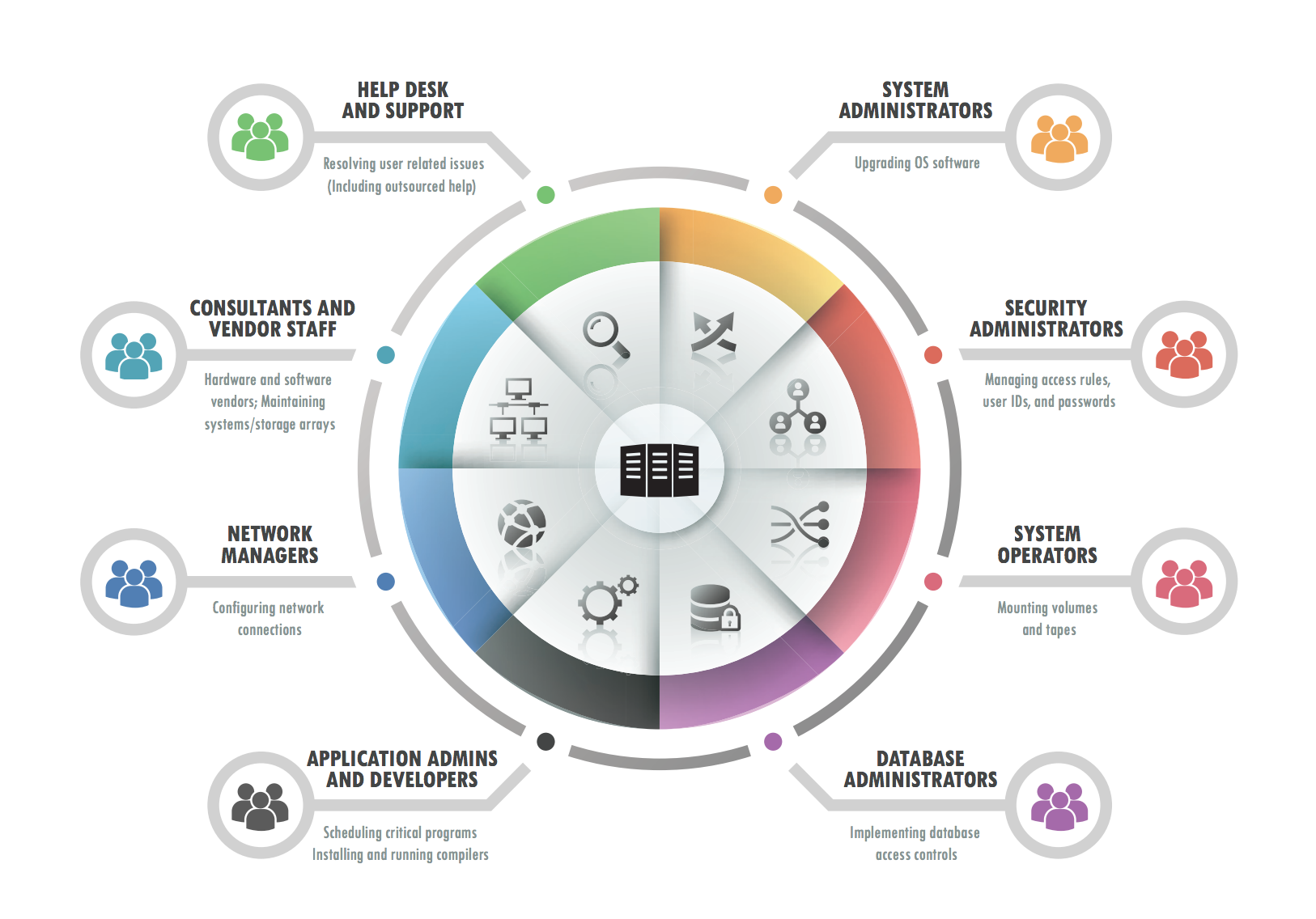
Privileged Access Management Best Practices
To effectively and efficiently manage privileged accounts, below is an overview of best practices for PAM in your organization:
- Centralize Management of User Accounts Across All Real and Virtual Servers:
Centralized administration of user accounts across your heterogeneous Linus/UNIX server environment ensures you can monitor and audit which users have access on which machines.
- Integrate with Existing Corporate Directories:
With multiple corporate directories and identity management systems, privileged account management must integrate seamlessly, so that team and group identities can be associated automatically to the correct systems, applications, and data.
- Ensure Contextual Authentication:
Contextual authentication enables organizations to target strong authentication to particular servers and roles that bring a higher level of risk.
- Enforce Secure Keystroke Logging:
For sensitive sessions, you must also have the ability to adapt to enforce full keystroke logging, so administrator activities can be tracked in full detail.
- Implement Granular Access Control:
Instead of allowing functional accounts like 'root' or 'sysdba' to log in, you need to have enforceable authorization rules that mandate the use of individual and auditable user accounts. Implement fine grain security controls to define and enforce who is granted elevated privilege, when, how and from where.
- Consolidate Audit Logging:
Protecting privileged accounts includes centralized audit logging with a detailed record of user activities. Effective PAM solutions should deliver consolidated audit logs and reports from across your server domains and be kept on a separate security domain.
Privileged Access Management from Core Security
Core Privileged Access Manager (BoKS)
Identity, Account, and Privileged Access Management Platform for Linux and UNIX
