As part of the Core Security Identity Governance and Administration portfolio of solutions, previously known as Courion, Access Assurance Suite is an intelligent identity and access management (IAM) software solution that enables organizations to deliver informed provisioning, meet ongoing regulatory compliance, and leverage actionable analytics for improved identity governance. Comprised of four industry-leading modules, our identity management software offers the most intelligent and efficient path to mitigating identity risk, and provides a complete solution for streamlining the provisioning process, reviewing access requests, managing compliance, and enforcing robust password management.
Core Access
A convenient web portal where end users can request access and managers can review, approve, or deny access. Using a shopping cart approach, Core Access delivers an efficient and user-friendly experience, replacing paper forms, emails, and tickets used to manage access. Plus the ability to leverage roles enables access to be assigned quickly and accurately.
A convenient web portal where end users can request access and managers can review, approve, or deny access. Using a shopping cart approach, Core Access delivers an efficient and user-friendly experience, replacing paper forms, emails, and tickets used to manage access. Plus the ability to leverage roles enables access to be assigned quickly and accurately.
Core Provisioning
As the backend fulfillment engine for Core Access, Core Provisioning uses software connectors to programmatically create and manage user accounts based on policies and permissions set up in Core Access. Our solution offers automated provisioning actions on hundreds of applications used across industries, organizations, and departments.
As the backend fulfillment engine for Core Access, Core Provisioning uses software connectors to programmatically create and manage user accounts based on policies and permissions set up in Core Access. Our solution offers automated provisioning actions on hundreds of applications used across industries, organizations, and departments.
Core Compliance
Core Compliance enables organizations to identify and manage access rights for systems, platforms, and applications in a single interface, eliminating the need to review spreadsheet after spreadsheet. Immediately respond to compliance audit demands to ensure adherence to regulations like SOX, HIPAA, PCI-DSS, and GDPR.
Core Compliance enables organizations to identify and manage access rights for systems, platforms, and applications in a single interface, eliminating the need to review spreadsheet after spreadsheet. Immediately respond to compliance audit demands to ensure adherence to regulations like SOX, HIPAA, PCI-DSS, and GDPR.
Core Password and Secure Reset
Core Security provides a complete, integrated solution for automated password management. Core Password and Secure Reset work together to provide a convenient and secure password reset solution for your organization. Leverage simple, secure self-service password resets to automate password management and reduce access risks. Easily enforce robust password policies and empower users to streamline security in your organization.
Core Security provides a complete, integrated solution for automated password management. Core Password and Secure Reset work together to provide a convenient and secure password reset solution for your organization. Leverage simple, secure self-service password resets to automate password management and reduce access risks. Easily enforce robust password policies and empower users to streamline security in your organization.
What Does Identity Management Software Do?
Key Benefits
-
Review access requests, easily provide approvals, and manage user privileges in a single portal
- Save time by automating account creation and access assignment for any type of user
- Identify and manage access rights for systems, applications, and data in a single interface
- Eliminate spreadsheets as part of the access review process
- Enforce robust password policies and empower users with self-service password resets
- Strengthen compliance with corporate security policies, industry standards, and government regulations
- Get up and running quickly with minimal services required
Instant Insight Into What's Going On In Your Business
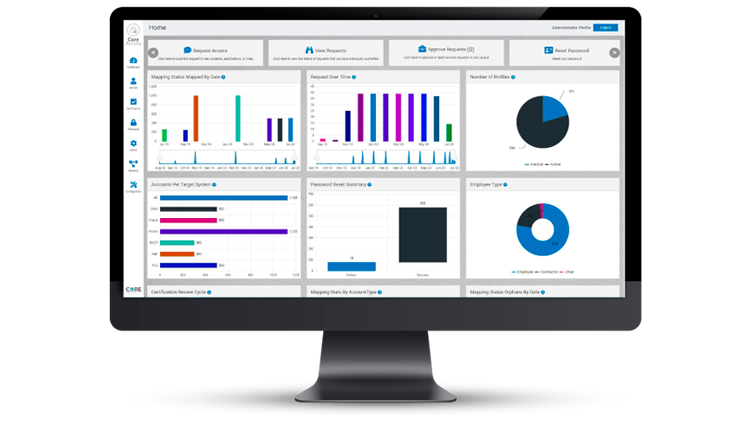
Within IGA, understanding operational value is key to success. So Access Assurance Suite offers a modern interface with intuitive dashboards that show at-a-glance metrics and KPIs. This ensures you can easily access your most important information—fast—and prioritizes visibility into what’s going on in your business.
Access Assurance Suite also offers automated workflow configuration, streamlined data management, and built-in data collection to get you up and running in no time. And whether you have a hybrid environment or are fully on cloud, Access Assurance has enhanced deployment options to include private cloud deployments—making it easy to embrace and support your cloud strategy.
Key Features

The Access Assurance Suite is a good choice for organizations that require a balanced approach to provisioning and access governance, with built in support for analytics.
Featured Resources
See Access Assurance Suite in Action
Find out how the right identity management software solution can help you mitigate identity risk in your organization.