Within an increasing regulatory landscape, organizations today must control and limit access to data and information. Core Compliance empowers organizations to simplify the access review process and respond to ongoing regulatory compliance. Identify and manage access rights across systems, platforms, and applications in a single interface, eliminating the need to review spreadsheet after spreadsheet. Certify and manage access privileges, so you can validate and effectively enforce least privilege access across your enterprise. Immediately respond to compliance audit demands to ensure adherence to regulations like HIPAA, SOX, PCI-DSS, and GDPR.
Monitoring Access Continuously
Organizations that view regulatory compliance through the lens of identity governance recognize they should monitor access continuously and provide access only to those individuals that need it, enabling their business to stay more compliant. But access reviews must be simple and easy to complete. If not, managers and reviewers may have the tendency to approve access in bulk to save time, also known as rubber stamping their approvals.
Leveraging an easier review process leads to greater accuracy, improved reporting, and greater adoption within the organization. Core Compliance enables organizations to easily understand which users have access to specific systems and which users are outliers in their privileges. It ensures access to information is strictly controlled and helps organizations demonstrate they are taking action to meet compliance requirements.
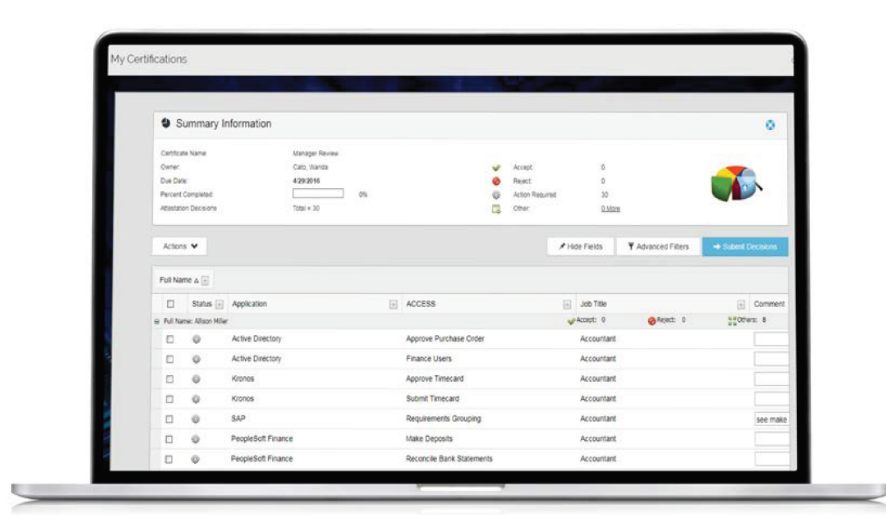
What Does Core Compliance Do?
Certify and Manage Access Rights
Users should not be granted more access privileges than necessary to perform their job or business function. Core Compliance enables authorized managers to easily review and certify user access rights leveraging a business-friendly view of entitlements. Within a single interface, managers can confirm or remediate user access using language they understand, and take immediate action when they identify access rights that are inconsistent with policy or regulatory requirements. Automatic notifications remind business managers to confirm user access rights on a schedule or according to company policy.
Users should not be granted more access privileges than necessary to perform their job or business function. Core Compliance enables authorized managers to easily review and certify user access rights leveraging a business-friendly view of entitlements. Within a single interface, managers can confirm or remediate user access using language they understand, and take immediate action when they identify access rights that are inconsistent with policy or regulatory requirements. Automatic notifications remind business managers to confirm user access rights on a schedule or according to company policy.
Reduce Risk and Demonstrate Compliance
Within the climate of regulatory compliance, it is imperative for organizations to review user access periodically. This is especially true as the number of users and identities grow within the business and access needs change. Core Compliance mitigates identity risk associated with unauthorized access and enables companies to meet stringent government and industry regulations by automating the discovery, analysis, and management of user access rights. Compliance and attestation within Core Compliance allows companies to effectively respond to auditor and regulatory demands for data, demonstrating ongoing compliance within corporate policies and key industry and government requirements.
Within the climate of regulatory compliance, it is imperative for organizations to review user access periodically. This is especially true as the number of users and identities grow within the business and access needs change. Core Compliance mitigates identity risk associated with unauthorized access and enables companies to meet stringent government and industry regulations by automating the discovery, analysis, and management of user access rights. Compliance and attestation within Core Compliance allows companies to effectively respond to auditor and regulatory demands for data, demonstrating ongoing compliance within corporate policies and key industry and government requirements.
Conduct Immediate Access Reviews with Micro-Certifications
Since the time between new provisioning and the next audit or review process can be fairly lengthy, it is important to have a set of controls that can quickly identify anomalous access, especially when that access violates an important policy, such as segregation of duties or privileged access. Core Compliance allows organizations to take advantage of automated micro-certifications to ensure any new or revised access or entitlements can be immediately reviewed. Micro-certifications allow managers to be alerted when an employee may have new or different access than what is expected, or if access is gained through an outside process, commonly referred to as out of band. Authorized managers can then perform an immediate review associated with the event and take required action.
Since the time between new provisioning and the next audit or review process can be fairly lengthy, it is important to have a set of controls that can quickly identify anomalous access, especially when that access violates an important policy, such as segregation of duties or privileged access. Core Compliance allows organizations to take advantage of automated micro-certifications to ensure any new or revised access or entitlements can be immediately reviewed. Micro-certifications allow managers to be alerted when an employee may have new or different access than what is expected, or if access is gained through an outside process, commonly referred to as out of band. Authorized managers can then perform an immediate review associated with the event and take required action.
Key Benefits
- Automate the discovery, analysis and management of user access rights
- Conduct access certifications to applications and file shares
- Remediate inappropriate or high-risk access without requiring a provisioning engine
- Demonstrate compliance with company policy and relevant regulations to auditors, regulators, and other interested parties
Key Features
“[Core Security’s] solution will allow us to manage access controls for all users across a variety of target systems and applications while supporting business operations ...helping us improve compliance, mitigate risk, and deliver a streamlined experience to all users simultaneously.”
