Introduction
The 2020 Identity and Access Management Report reveals the increasing importance of managing access as part of an organization’s overall risk management and security posture. At the same time, a majority of organizations are, at best, only somewhat confident in the effectiveness of their identity and access management program. The 2020 Identity and Access Management Report highlights what is and what is not working for security operations teams in securing access to sensitive data, systems, and applications.
IAM
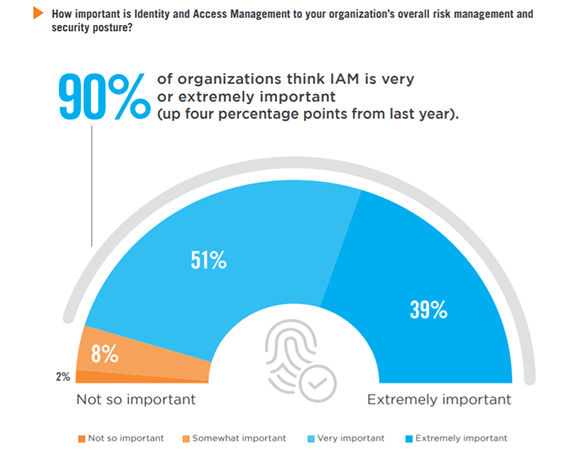
Nine out of ten organizations confirm that identity and access management is very to extremely important as part of their cybersecurity and risk management posture (90%). This is a 4 percentage point increase compared to last year’s survey and confirms the rising importance of IAM.
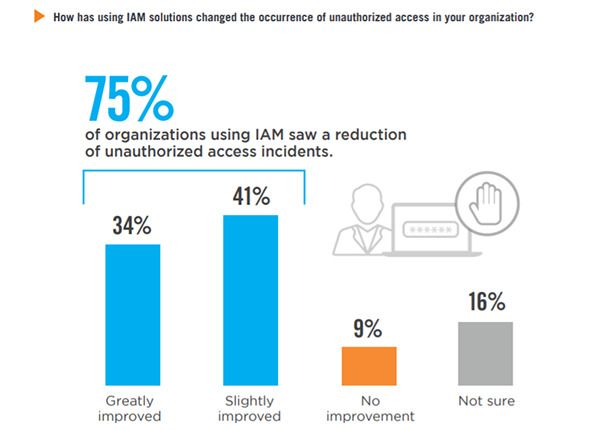
For 75% of organizations, utilizing identity and access management solutions has resulted in a reduction of unauthorized access incidents. Only a small fraction of 9% report no improvement.
RBAC
Organizations prioritize role-based access control as the most critical IAM capability (62%), followed by single sign-on (53%) and compliance/auditor reporting (51%).
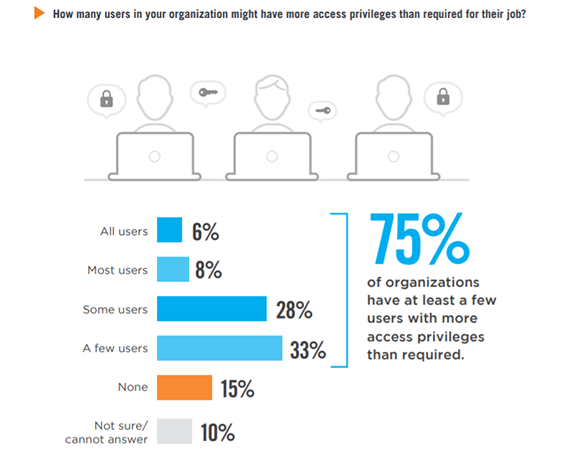
75% of organizations have at least a few users with more access privileges than required. That is up by 5 percentage points compared to last year’s survey.
This 2020 Identity and Access Management Report has been produced by Cybersecurity Insiders, the 400,000 member information security community, to explore the latest trends, key challenges, gaps and solution preferences for Identity and Access Management (IAM).
Importance of IAM Rising
Nine out of ten organizations confirm that Identity and Access Management is very to extremely important as part of their cybersecurity and risk management posture. This is a four percentage point increase compared to last year’s survey and confirms the rising importance of IAM.
IAM Program Effectiveness
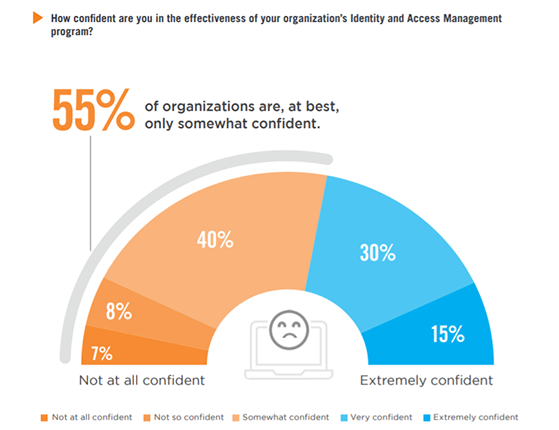
Fifty-five percent are, at best, only somewhat confident in the effectiveness of their identity and access management program. This response represents a small decline in the share of organizations that expressed confidence in their IAM posture last year.
Unauthorized Access
Organizations that experienced unauthorized access to sensitive systems and data reported they were most negatively impacted by disrupted business activities (23%). This is closely followed by system downtime (22%), reduced employee productivity (17%), and increased helpdesk load (tied at 17%).
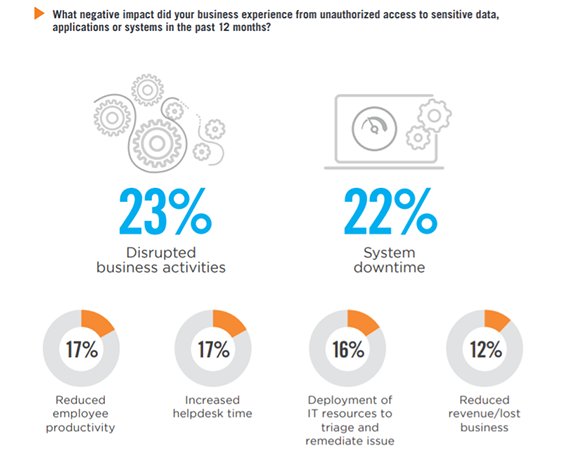
Data loss 12% | Negative publicity/ reputational damage 10% | Loss/compromise of intellectual property 10% | None/no business impact due to unauthorized access 10% | Lawsuit/legal issues 7% | Customer loss 7% | Regulatory fines 2% | Other 2%
Critical IAM Capabilities
Organizations in our survey prioritize role-based access control as the most critical IAM capability (73%), up by five percentage points compared to last year’s survey. This is followed by single sign-on capabilities (60%), and system and application access monitoring (53%).
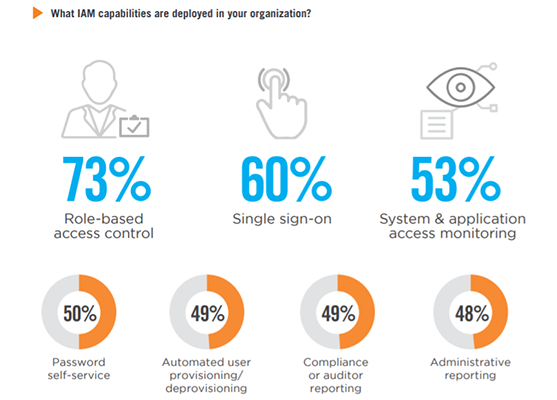
Considerations for contract or temporary staff 44% | User monitoring 44% | Integration with service desk/ITSM solutions 43% | Streamlined user certification/auditing 33% | Advanced analytics (e.g., as Artificial Intelligence (AI) or Machine Learning (ML)) 17% | Other 6%
Learn why IAM solutions have become an even more critical part of an organization's risk management strategy.
Designing Roles
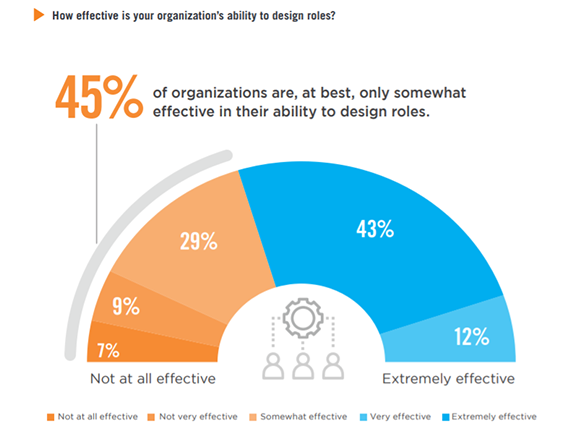
We asked organizations how effective they are in their ability to design roles as part of their identity and Access Management program. Role design enables organizations to focus on role definitions and assignments rather than individual accounts and entitlements. Only 45% are, at best, somewhat effective in their ability to design roles.
Excessive Access Privileges
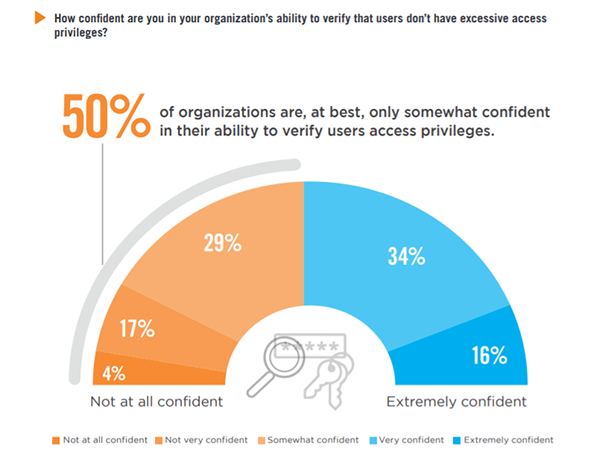
Fifty percent of organizations are, at best, only somewhat confident in their ability to verify that users don’t have excessive access privileges.
Seventy-five percent of organizations have at least a few users with more access privileges than required. This is an increase of five percentage points compared to last year.
Key Drivers for IAM
When asked about the key drivers for developing their IAM programs, organizations rank security as the biggest driver (76%), followed by operational efficiency (62%) and breach prevention (46%).
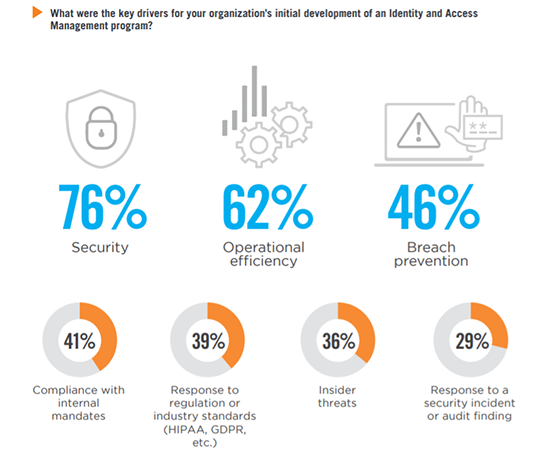
Poor user experience 19% | Not applicable/We do not have an Identity and Access Management program 5% | Other 2%
IAM Investment Priorities
Over the next 12 months, organizations prioritize investment in privileged access management (57%), up five percentage points since last year to become the number one priority. This is followed by multi-factor authentication (49%), and identity management and governance (42%).
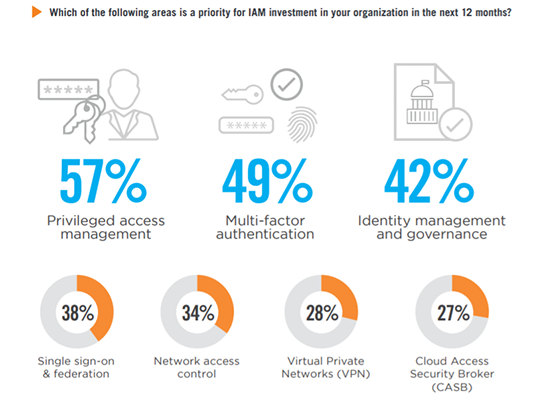
Identity analytics 22% | Web application firewall 20% | Enterprise directory 18% | Software Defined Perimeter (SDP) 14% | Other 5%
Read a case study to see how a large healthcare organization established a comprehensive IAM strategy and approach.
Authentication Methods
Not surprisingly, by far the most popular authentication method is username and password (88%), followed by software tokens (48%) and out-of-band authentication (41%) – a 21 percentage point jump compared to last year.
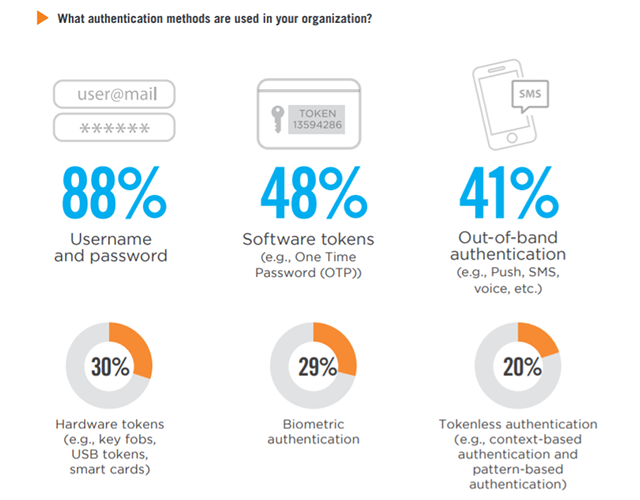
Social identity credentials (e.g., using LinkedIn, Facebook, Twitter, etc.) 8% | Other 4%
Critical Capabilities
Organizations in our survey prioritize role-based access control as the most critical IAM capability (62%), followed by single sign-on (53%) and compliance/auditor reporting (51%).
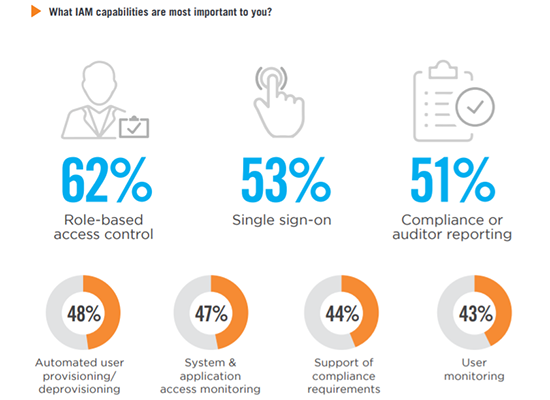
Password self-service 41% | Administrative reporting 39% | Workflow and case management 32% | Streamlined user certification/ auditing 30% | Considerations for contract or temporary staff 30% | Access request dashboards 27% | Ability to personalize platform 24% | Other 1%
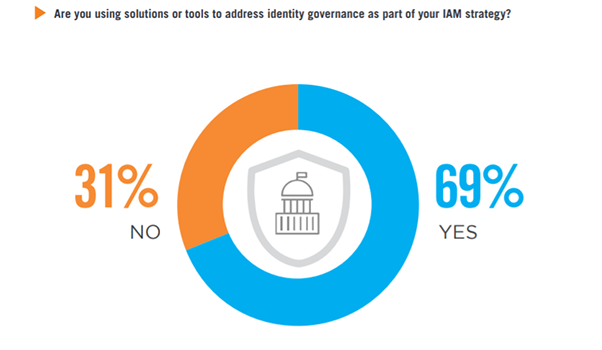
Identity Governance
A majority of organizations (69%) are using solutions to address identity governance as part of their IAM strategy, a two percent increase from last year. Identity governance administration policies help define and standardize levels of access rights based on roles or job duties. Identity governance solutions can help streamline the provisioning process, adhere to relevant regulations, and provide actionable analytics.
New IAM insights are available! Get the latest trends in the 2021 Identity and Access Management Report.
Reduction of Unauthorized Access
For 75% of organizations, utilizing Identity and Access Management solutions has resulted in a reduction of unauthorized access incidents. Only a small fraction of 9% report no improvement.
Key Challenges
Lack of automation and having to manually create and refine access rules and roles (38%) leads the list of key challenges for managing access. This is followed by lack of skilled staff (36%) and increasing use of mobile devices (32%).
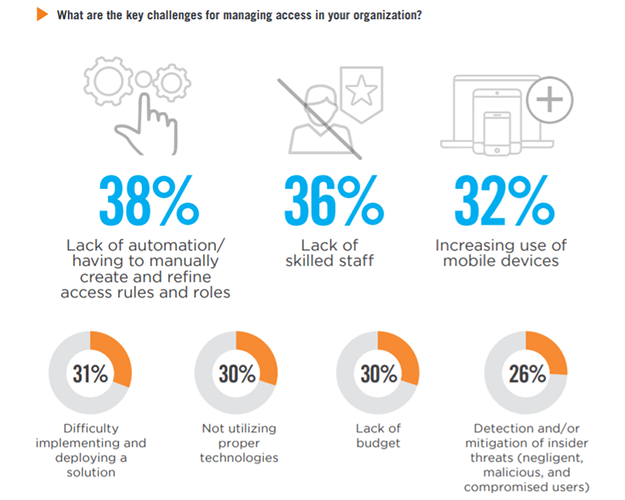
Migration to the cloud 26% | Poor integration/interoperability between security solutions 25% | Increasing number of regulations and mandates 23% | Changes to the organization (due to re-organization, acquisition, etc.) 23% | Evolving threat landscape 22% User/staff turnover 21% | Poor vendor support 18% | Password management 17% | Application sprawl 16% | Lack of management support 14% | Lack of clearly defined access policies and procedures 13% | Reviewing and approving user roles 13% Lack of proper reporting tools 12% | Lack of effective IAM solutions available in the market 9% | Other 1%
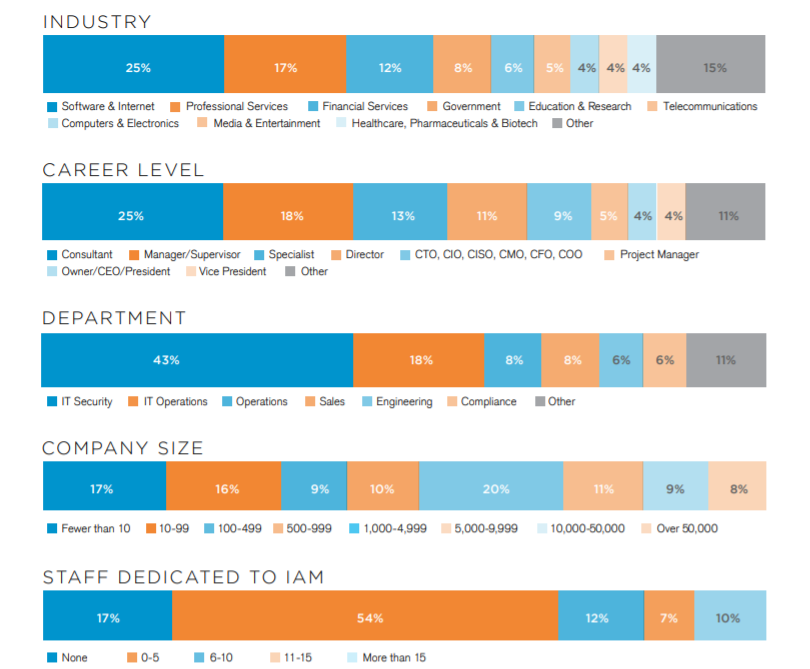
Methodology & Demographics
The Identity and Access Management Report is based on the results of a comprehensive online survey of cybersecurity professionals, conducted in May of 2020 to gain deep insight into the latest trends, key challenges and solutions for identity and access management. The respondents range from technical executives to IT security practitioners, representing a balanced cross-section of organizations of varying sizes across multiple industries.