Core Impact is designed to enable security teams to conduct advanced penetration tests with ease. With guided automation and certified exploits, the powerful penetration testing software enables you to safely test your environment using the same techniques as today's adversaries.
- Deployment: Core Impact runs on Windows with an integrated SQL database, physical or virtual system. Core Impact can be installed and running in 30 minutes or less.
- Platforms Monitored: Operating Systems like Windows, Linux, and Mac, Cloud (Public, Private, Hybrid), Databases, Web Services, Network Appliances, Software Applications, Critical Data
Simple enough for your first test, powerful enough for the rest.
Rapid Penetration Testing
Use automated Rapid Penetration Tests (RPTs) to discover, test, and report in just a few simple steps.
Core Certified Exploits
Test with confidence using a trusted platform designed and supported by experts for more than 20 years.
Key Features
Guided Automation
Core Impact's Rapid Penetration Tests (RPTs) are accessible automations designed to automate common and repetitive tasks. These high-level tests help optimize the use of your security resources by simplifying processes, maximizing efficiency, and enabling pen testers to focus on more complex issues.
Certified Exploits
Leverage our professionally written and validated exploit library for real-world testing capabilities. This stable library of commercial-grade exploits has real-time updates of new penetration testing exploits and tests for additional platforms as they become available, including third party exploits from ExCraft.
Multi-Vector Testing Capabilities
Replicate attacks across network infrastructure, endpoints, web, and applications to reveal exploited vulnerabilities, empowering you to immediately remediate risks.
Integrations
Integrations with other pen testing tools like Metasploit, PowerShell Empire, and Plextrac centralize your testing environment, streamlining and increasing the breadth of your program. Core Impact also integrates with and validates vulnerabilities from more than 20 popular scanners, including beSECURE, Burp Suite, Frontline VM, Nessus, Qualys, and OpenVAS to help you prioritize your greatest risks.
Patented Agents
Core Impact’s patented Core Agents simplify interactions with remote hosts. You can tell Core Impact what you’d like to do with the remote host and the agent will take care of the technical aspects.
Robust Error Prevention
Enable programmable self-destruct capabilities for agents at different levels (product, workspace, module/RPT). This means no agent is left behind after testing to drain resources or be used as a potential backdoor for attackers.
Teaming
Multiple security testers have the capability to interact in the same session, giving teams the ability to securely share data and delegate testing tasks. These shared workspaces provide a common view of discovered and compromised network targets for optimal collaboration.
Watch a Quick Demo
See product features in action with this short video.
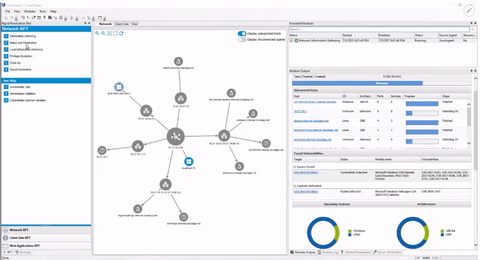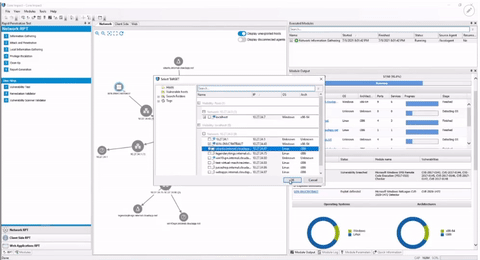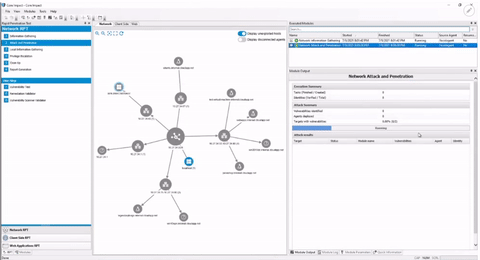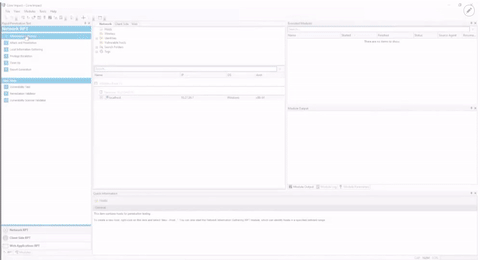
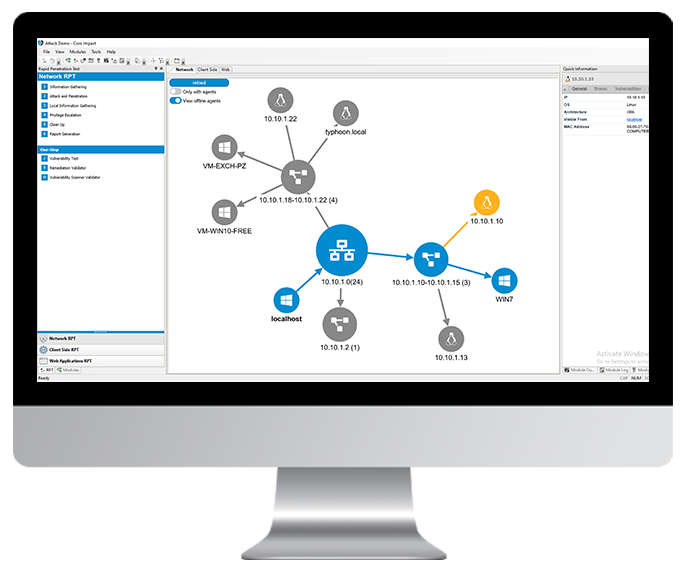
Maximize Testing Visibility
Use Core Impact's attack map to get a real-time overview of attack chains, pivoting and any other activities completed during testing. This network graph view provides visual insight that allows security teams to better determine the best path forward in the testing engagement.
Product Specs
For additional technical product specifications, view the Core Impact Technical Datasheet.
Platforms Monitored
Core Impact includes OS, services, and application exploits designed to target vulnerabilities on the following platforms:
- AIX
- Linux
- Mac OS X
- OpenBSD
- Sun Solaris
- Windows
- SCADA
Using Core Impact, tests can be conducted to test the structure of IPv6 systems and access the security of IPv6 systems using exploits to expose vulnerabilities.
Vulnerability Scanner Imports & Validation
Core Impact can import and validate results from many of the leading vulnerability scanners on the market, including:
- Acunetix® Web Security Scanner
- Retina Network Security Scanner
- HP WebInspect
- IBM Enterprise Scanner®, IBM Internet Scanner® & IBM AppScan®
- Beyond Security AVDS
- Portswigger BurpSuite
- McAfee® Vulnerability Manager
- TripWire IP360®
- Rapid7 AppSpider & Rapid7 Nexpose
- Qualys QualysGuard®
- SAINTscanner®
- Tenable Nessus® & Tenable Security Center®
- Patchlink VMS
- Trustwave AppScan®
- NMap
Deployment Requirements
You can run Core Impact on any Windows system with the following minimum specifications:
- Intel Core 2 Duo, 2.8 GHz
- 4GB RAM minimum (8GB RAM recommended)
- 4GB free hard disk space (space requirements increase with the quantity of workspaces)
- A Windows-compatible Ethernet networking card. Core Impact works with wireless network interface cards
- Internet Explorer 9.0 or later
- Screen resolution: 1024 x 768 minimum (1280 x 1024 recommended)
Core Impact runs on Windows with an integrated SQL database, physical or virtual system. Core Impact can be installed and running in 30 minutes or less.
Common Use Cases
Automate the Routine
With Core Impact, you can easily automate routine testing, including proving PCI compliance, to maximize your resources, reserving third-party testing for most robust and complex requests.
Give Your Vulnerability Scans an Ally
Core Impact validates vulnerabilities identified through more than 20 popular scanners, helping you prioritize remediation for your greatest security risks.
Measure Security Awareness
Easily simulate a phishing campaign using Core Impact’s dynamic tools to find out who is vulnerable to social engineering attacks.
Validate Remediation Effectiveness
Re-test exploited systems after a penetration test to verify that remediation measures or compensating controls are effective and working.
By Industry: Healthcare, Financial Services, Government, Higher Education, Retail, Energy & Utilities
“What takes us three hours to do manually takes ten minutes with an automated tool like Core Impact, so it makes my day easier."
See what penetration testing software can do for your organization
Conduct advanced penetration tests with ease and efficiency. See how Core Impact can streamline pen testing in your environment by requesting a free trial.
Supported Regulations
Penetration testing is a vital way to stay compliant and prove adherence to external mandates. Core Impact helps organizations better protect their sensitive data and supports multiple regulations, including:
PCI
NIST
CMMC
And more
Featured Resources

Ready to Begin Using Core Impact?