Robust reporting capabilities are a critical part of Core Impact’s centralized toolset, as pen test reports are used to plan and prioritize remediation efforts, as well as prove compliance for regulations like PCI DSS, GDPR, and HIPAA.
Manual pen test reporting can be a time-consuming effort that varies in details and quality. Core Impact’s automated reporting features ensure consistency and increase efficiency, creating a thorough record for all aspects of a pen testing engagement.
Reporting Categories and Formats
A number of reports, including the executive summary, cover all three vectors, and are classified under general reports. There are also vector specific reports covering the three types of pen tests that Core Impact performs:
Reports are typically formatted as spreadsheets, with some offering charts and graphs that can be tailored as needed. Final versions of reports can also be generated as pdfs to deliver to clients or stakeholders.
General Reports
- Delta Report: This report provides a side-by-side display of the test statistics of two workspaces for comparison. For example, a pen tester may run the same test twice, once as an admin user, and once as a user with lesser privileges in order to spot differences between the two user accounts.
- Activity Report: This report provides a detailed list of all the modules run during a penetration test, to show exactly what work testers completed.
- Identity Report: This report provides details about identities collected by brute force or post-exploitation actions.
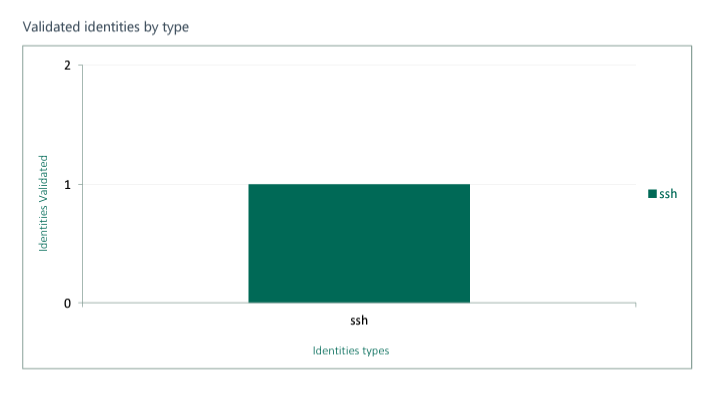
Image taken from Network Host Report
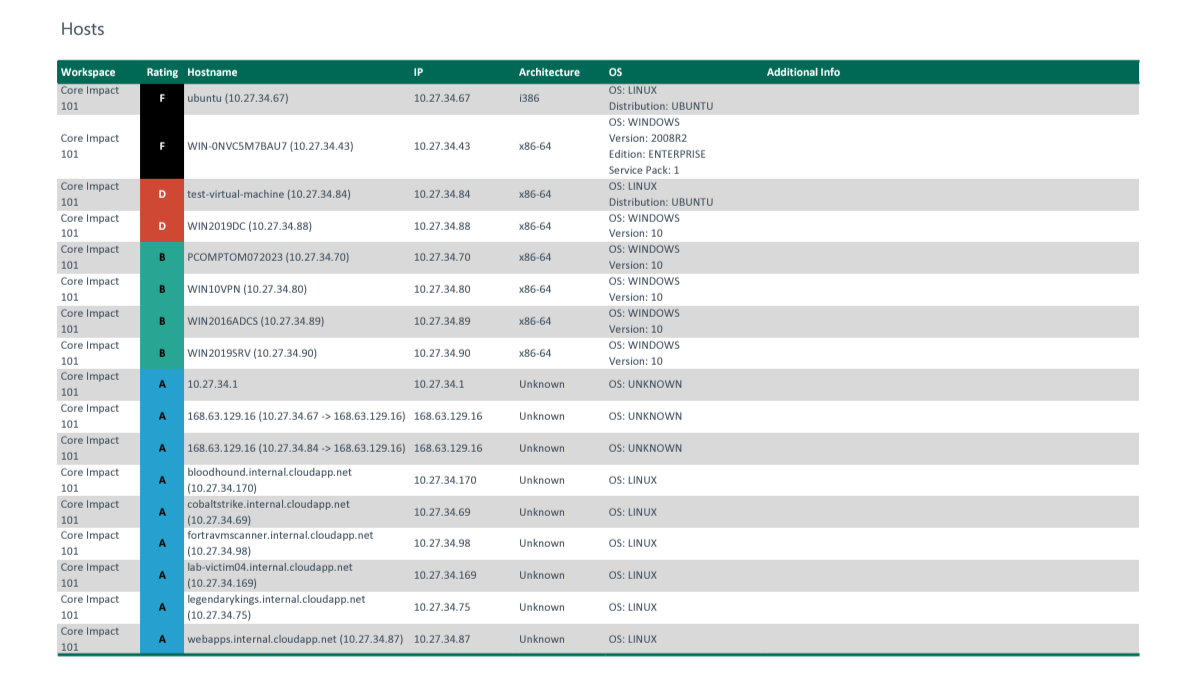
Image taken from Network Host Report
- Executive Report: This summary report fully covers every pen testing activity Core Impact completed throughout an engagement, along with the test results. Data includes summaries of:
- Exploited vulnerabilities
- Discovered hosts and network devices
- Targeted users
- Most exploited vulnerabilities by operating system
- Most exploited vulnerabilities overall
- Attack Graph Report: Any successful breach of a system during a penetration test can be graphically represented, showing the type of attack used, and any systems or applications involved.
- Network Host Report: Available for both network and client-side pen tests, this report provides information about any hosts tested during the pen test. Details include the number of compromised hosts, CVE names of vulnerabilities, services and applications found on each host, and the average number of exploited vulnerabilities on compromised hosts.
- FISMA Exploited Vulnerabilities Report: This summary report includes all the necessary information and formatting to meet the requirements of the U.S. Government Federal Information Security Management Act (FISMA). This report can also be used to help you gain National Institute of Standards and Technology (NIST) compliance.
- Trend Report: This summary report provides a graphic representation of the changes across two or more workspaces over a given time period. Reports can be run daily, weekly, monthly, or yearly to show both short-term and long-term trends.
- Vulnerability Report: This report provides information about vulnerabilities that were successfully exploited on each host, and includes CVE and CVSS numbers for additional details.
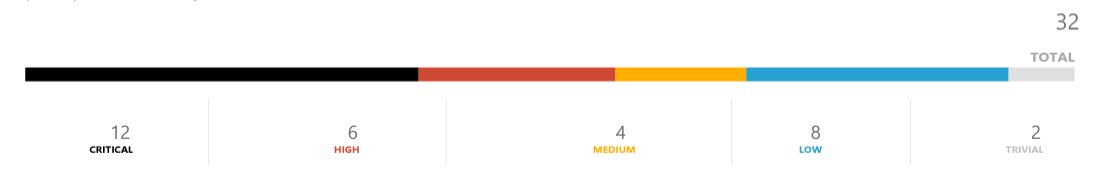
Image taken from Network Host Report
Network Reports
PCI Vulnerability Validation Report
This report is formatted to meet PCI DSS compliance requirements, and uses data imported from external vulnerability scanners and provides validation and severity information for the vulnerabilities found during a scan.
Network Remediation Validation Report
This report should be run after an engagement is over and measures have been taken to improve security. It provides a comparison to the original results to see if remediation efforts successfully resolved the security weaknesses uncovered by the initial tests.
Network Wellness Report
Network Wireless Report
WiFi Fake Access Points Report
WiFi MiTM Report
Client-Side Reports
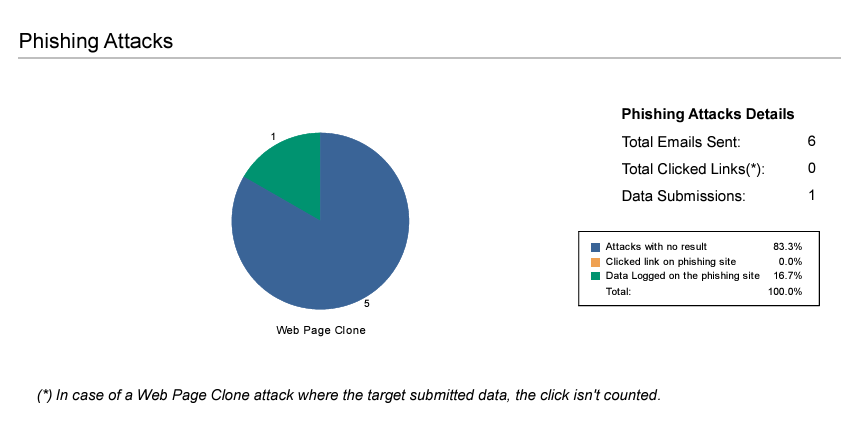
Image taken from Client-Side Phishing Report
- Client-Side Phishing Report: This report provides a detailed summary of phishing campaign simulations, and includes information on targets, as well percentages for targets who viewed the email, visited the phishing web site, and who entered data once on the site.
- User Report: This report gives a detailed list of any users that were discovered and targeted during a client-side pen test.
- Information Publicly Accessible Report: This report provides the results of the client-side information gathering test, which includes a search of discovered documents and metadata.
- Client-Side Penetration Test Report: This report includes detailed summaries of client-side pen tests, including attack types, exploits used, and email messages sent to deliver attacks or link them to a malicious site.
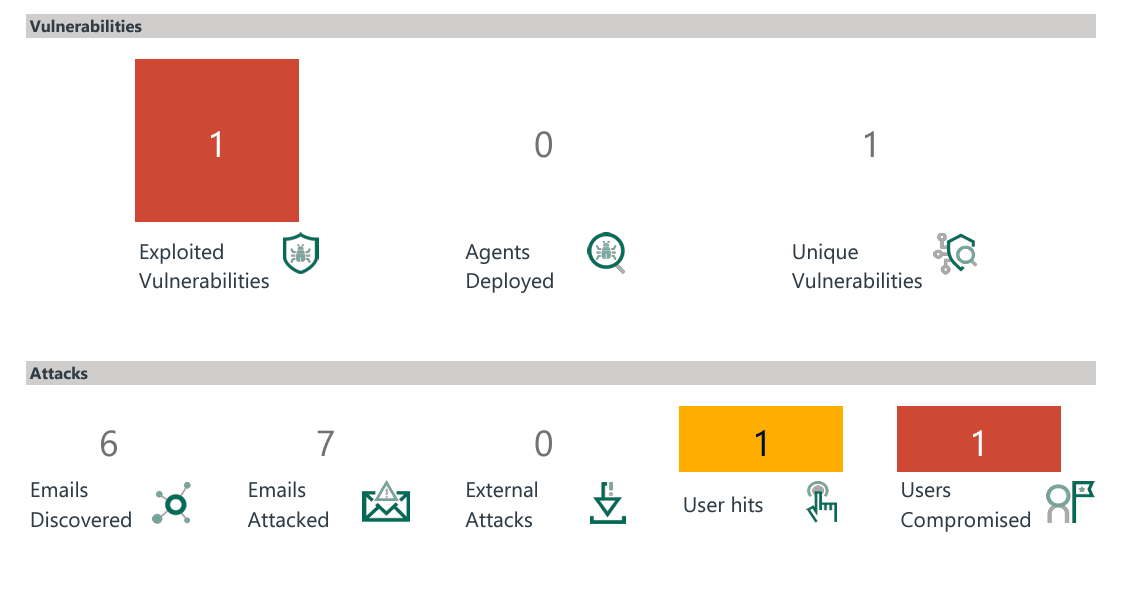
Image taken from Client-Side Penetration Test Report
Web Application Reports

Image taken from Webapps Executive Report
- Web Apps Executive Report: This summary report provides the information obtained during the pen test, including discovered hosts, compromised vulnerabilities, and executed tasks.
- Web Apps Remediation Validation Report: This report should be run after an engagement is over and measures have been taken to improve security. It provides a comparison to the original results to see if remediation efforts successfully resolved the security weaknesses uncovered by the initial tests.
- Web Apps Vulnerability Report: This report provides a list of all the vulnerabilities that were successfully exploited, along with additional information, such as which web page had the vulnerability, and how much access the vulnerability provided.
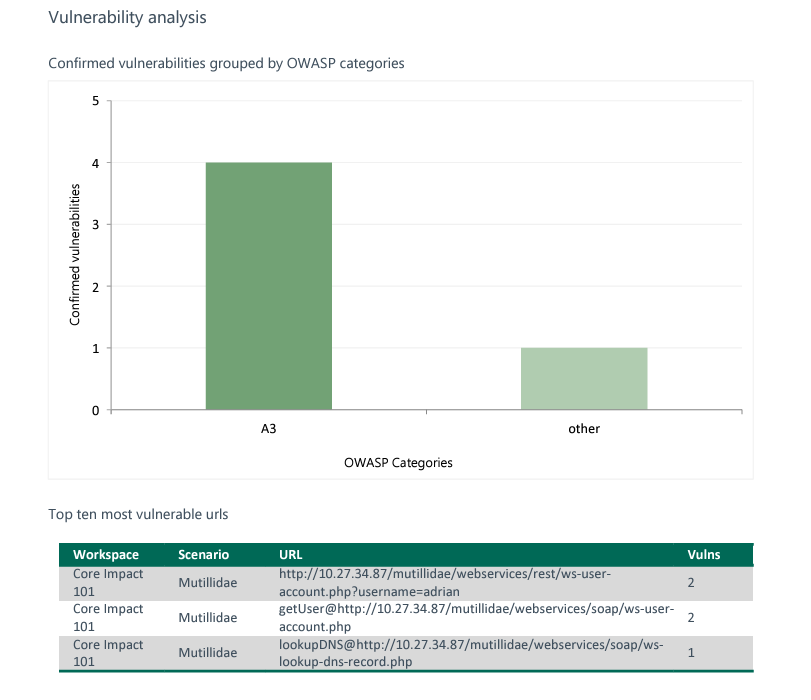
Image taken from Webapps Executive Report
MITRE ATT&CK™ Reports
The MITRE ATT&CK framework is a matrix of tactics and techniques used by real-world threat actors that has become a standard in defensive security, helping cybersecurity professionals create threat models to better prepare against risks that threaten the safety of critical data. Core Impact offers two reporting types that map and categorize engagements in MITRE.
The ATT&CK Navigator Report
The NIST 800 Navigator Report
Reporting with the Plextrac Integration

Gather all your pen testing data in one place. With Core Impact’s integration with Plextrac, you can collect reporting information from vulnerability scanners and any other tools used during your pen test, consolidating the information so it can be shared as one comprehensive report.
Get to Know Core Impact
Find out about all of Core Impact's many features like agents, phishing capabilities, reporting, and more.