Introduction
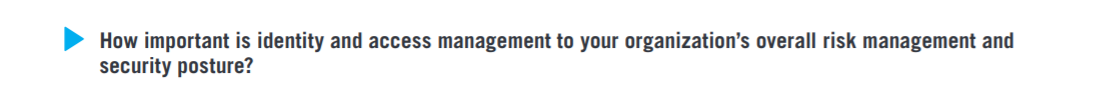
The 2019 Identity and Access Management Report reveals the increasing importance of managing access for a significant majority of organizations (86%) as part of their overall risk management and security posture. At the same time, a majority of organizations (53%) are, at best, only somewhat confident in the effectiveness of their identity and access management program.
In the context of this survey report, the purpose of Identity and Access Management is to grant access privileges for the right enterprise assets to the right users in the right context of their role or scope of responsibilities within an organization.
The 2019 Identity and Access Management Report highlights what is and what is not working for security operations teams in securing access to their sensitive data, systems, and applications:
RBAC
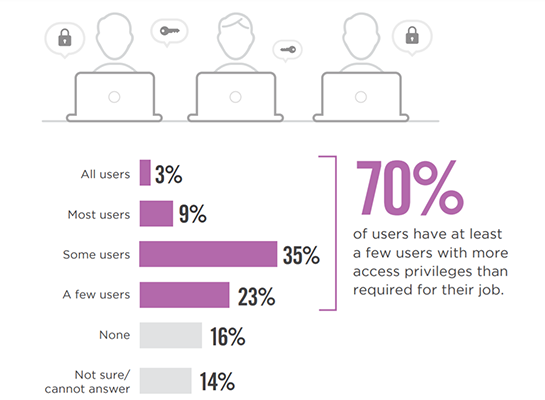
70% of organizations have at least a few users with more access privileges than required for their job.
66% view role-based access control as most important to them.
IAM
75% of organizations using IAM saw a reduction of unauthorized access incidents.
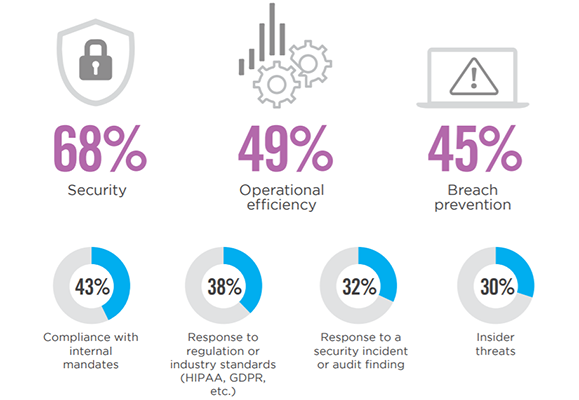
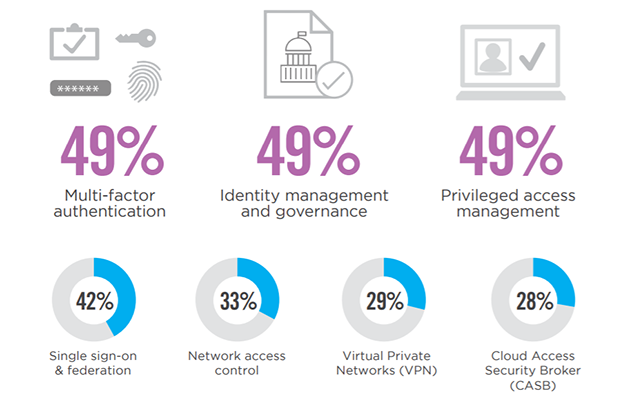
49% deem identity management and governance, multi-factor authentication, and privileged access management as a priority for IAM investment in the next 12 months.
This 2019 Identity and Access Management Report has been produced by Cybersecurity Insiders, the 400,000 member information security community, to explore the latest trends, key challenges, gaps and solution preferences for Identity and Access Management (IAM).
Importance of IAM
Identity and access management is very important to extremely important to a significant majority of organizations (86%) as part of their overall risk management and security posture.
IAM Program Effectiveness
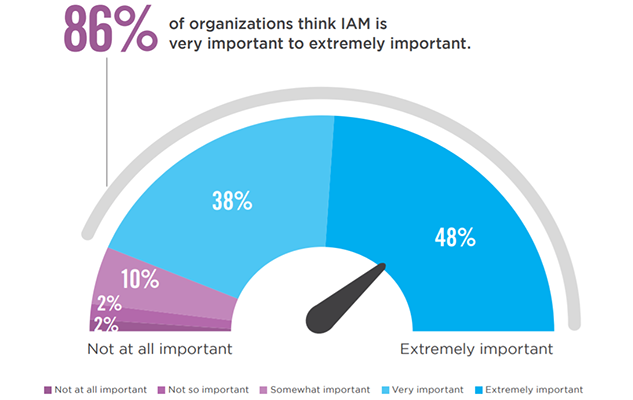
A majority of organizations (53%) are, at best, only somewhat confident in the effectiveness of their identity and access management program. Forty-seven percent are very confident to extremely confident.

IAM Capabilities
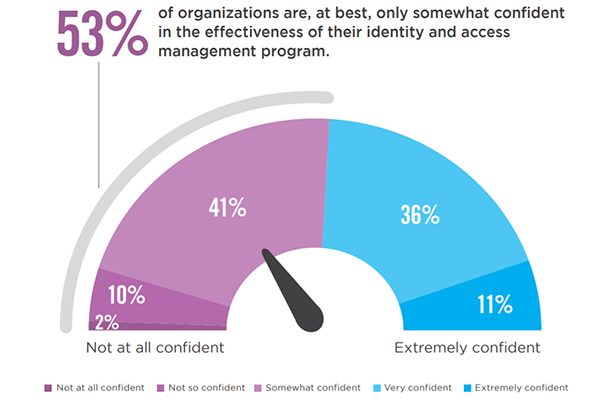
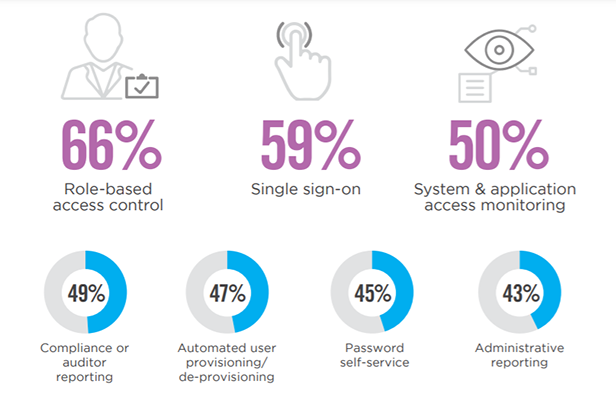
The most frequently deployed IAM capabilities include role-based access control (68%), followed by single sign-on (57%) and self-service password management (50%).


Excessive Access Privileges
Bulk approvals of access requests, departmental/role changes, and not reviewing user access periodically often leads to excessive access privileges. A large majority of organizations (70%) report at least a few users with more access privileges than required for their job.

Learn why IAM solutions have become an even more critical part of an organization's risk management strategy.
Key Drivers for IAM
Organizations prioritize security (68%) over operational efficiency (49%) and breach prevention (45%) as the key drivers for developing an IAM program.

IAM Investment Priority
Over the next 12 months, organizations equally prioritize multi-factor authentication (49%), identity management and governance (49%) and privileged access management (49%).
Authentication Methods
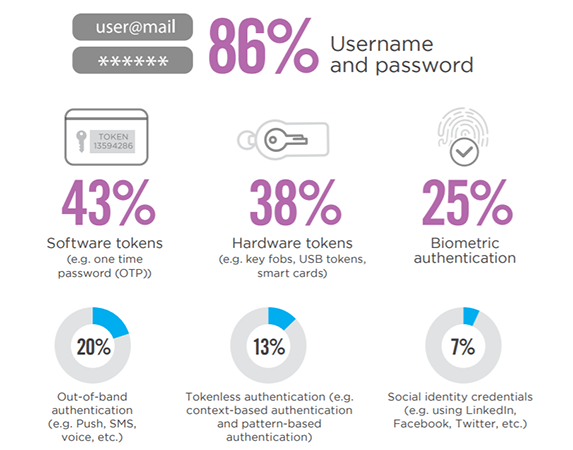
Not surprisingly, by far the most popular authentication method is username and password (86%), followed by software tokens (43%) and hardware tokens (38%).
Read a case study to see how a large healthcare organization established a comprehensive IAM strategy and approach.
Critical Capabilities
Organizations in our survey prioritize role-based access control as the most critical IAM capability (66%), followed by single sign-on (59%) and system and application access monitoring (50%).

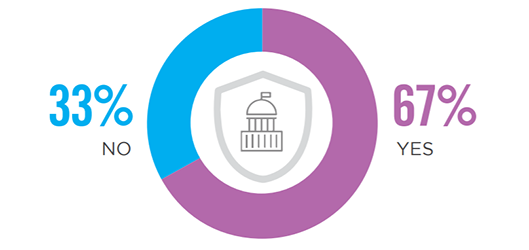
Identity Governance
A majority of organizations surveyed (67%) are using identity governance solutions as part of their IAM strategy. Identity governance and administration policies help define and standardize levels of access rights based on roles or job duties. Identity governance solutions can help streamline the provisioning process, adhere to relevant regulations, and provide actionable analytics.
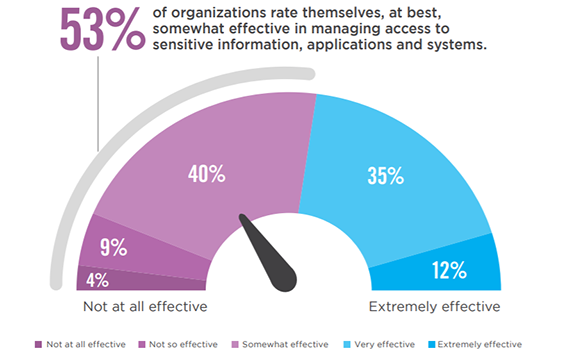
Access Management Effectiveness
A majority (53%) of organizations rate themselves, at best, somewhat effective in managing access to sensitive information, applications and systems.
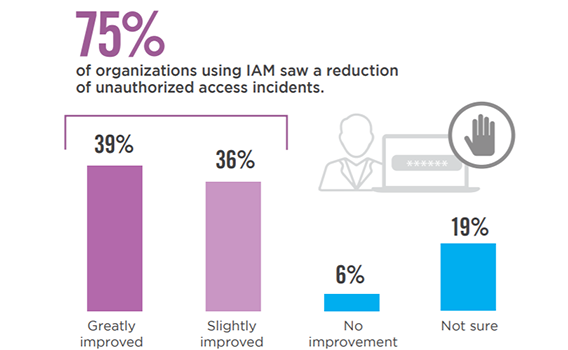
Reduction of Unauthorized Access
For 75% of organizations, utilizing identity and access management solutions has resulted in a reduction of unauthorized access incidents. Only a small fraction of 6% report no improvement.
New IAM insights are available! Get the latest trends in the 2021 Identity and Access Management Report.
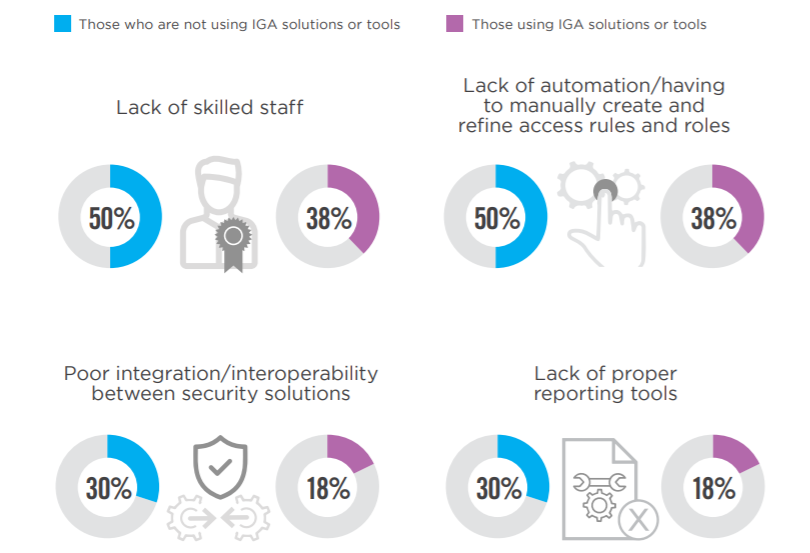
Key Challenges
Those not using Identity Governance and Administration (IGA) solutions or tools report a lack of skilled staff, automation, and proper reporting tools in addition to poor integration/interoperability between security solutions as key challenges in their organization more frequently than those using IGA solutions.
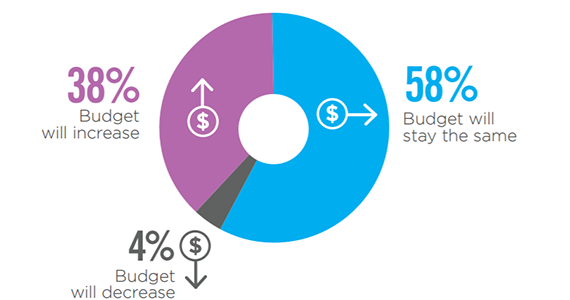
Budget Trend
On balance, IAM budget will increase for 38% of organizations that participated in the survey. Only 4% report a planned budget reduction over the next 12 months.

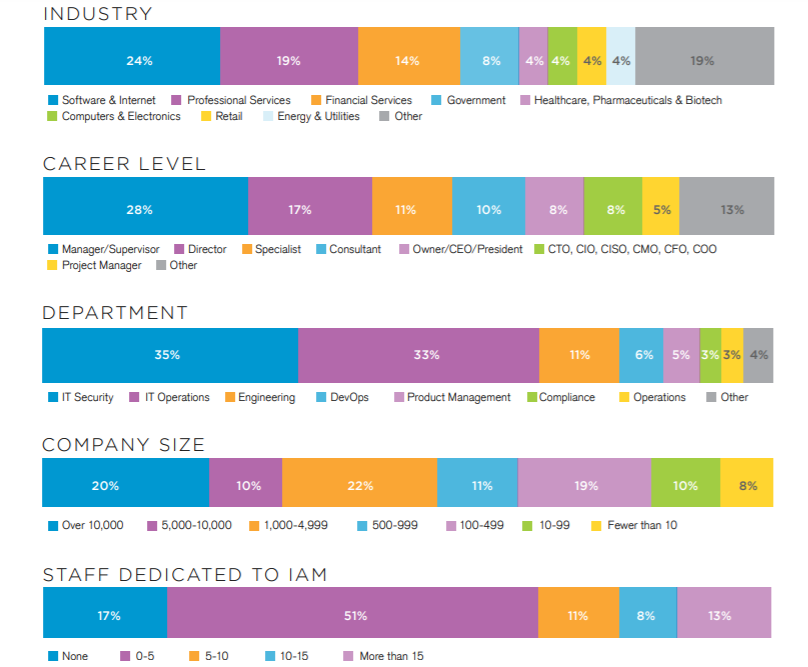
Methodology & Demographics
This Identity and Access Management is based on the results of a comprehensive online survey of cybersecurity professionals, conducted in June of 2019 to gain deep insight into the latest trends, key challenges and solutions for identity and access management. The respondents range from technical executives to IT security practitioners, representing a balanced cross-section of organizations of varying sizes across multiple industries.
See how Identity and Access Management solutions can mitigate identity-related access risks in your organization.