Core Impact Issues Latest Exploit for F5 BIG-IP iControl REST Vulnerability
The F5 BIG-IP iControl REST vulnerability, a critical authentication bypass vulnerability that leads to unauthenticated remote code execution, is quite simple to exploit and provides an attacker with a method to execute arbitrary system commands as root. In this blog, we’ll explore exactly what this vulnerability is and how Core Impact can help you quickly uncover and exploit it during a penetration test.
What is the F5 BIG-IP iControl REST Vulnerability?
CVE-2022-1388 is a missing authentication for critical function vulnerability (CWE-306). Any attacker able to send HTTP requests to a BIG-IP system through the management port and/or a self IP address can execute arbitrary system commands as root.
BIG-IP uses an Apache web server acting as a reverse proxy for the iControl REST service, which is a Java application. The vulnerability resides in the way that iControl and Apache performs authentication.
mod_auth_pam.so is a custom Apache module that handles client authentication. If the X-F5-Auth-Token header is present in the client request, then the request is passed to the iControl REST service. If not, the Authorization header is checked for valid credentials.
In the iControl REST service, if the X-F5-Auth-Token header exists, it is validated. If it doesn't, then the request is allowed if the X-Forwarded-Host header points to localhost.
HTTP hop-by-hop request headers is the name of the technique used to force the Apache web server to delete the X-F5-Auth-Token header. Typically, this header is processed before the Connection header. Adding X-F5-Auth-Token as a value for the Connection header will skip the authorization check and force Apache to erase the X-F5-Auth-Token header from the request before it’s passed to the iControl REST service. Also, setting the Host header to localhost will set the X-Forwarded-Host header in the iControl REST service. A basic Authorization header with “admin” as username and any type of password is also needed. The endpoint /mgmt/tm/util/bash can be used to execute commands as root.
Currently, this vulnerability can be eliminated by updating to a fixed version of BIG IP. There are also several workarounds that can be used if updating has to be delayed for any reason.
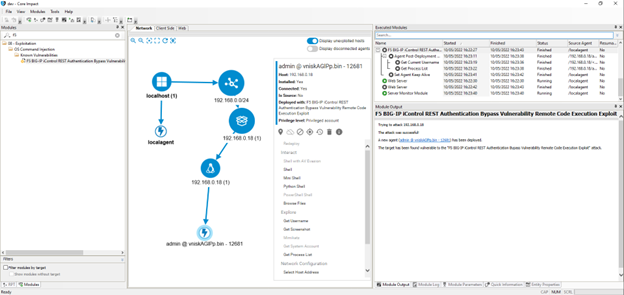
Proactively Responding to F5 BIG-IP iControl REST Vulnerability with Core Impact
Core Impact customers can be proactive in their response since they can easily run a pen test to see if this vulnerability is present in their infrastructures. Our exploits team rapidly created the exploit for this product: F5 BIG-IP iControl REST Authentication Bypass Vulnerability Remote Code Execution Exploit. It is now available in the latest release of Core Impact, version 21.2. You can see an example of how Core Impact can test for this vulnerability in the short video below:
Core Impact's commercial grade exploit library is regularly updated with new exploits, which are always written and tested by pen testing experts. Our exploits team works to swiftly create high value and reliable exploits that will benefit our customers and help them achieve their pen testing goals.
Protecting Against F5 BIG-IP iControl REST Vulnerability and the Importance of Regular Pen Testing
As mentioned earlier, a patch is available for CVE-2022-1388. There are mitigations available for differently affected versions of BIG-IP. However, mitigations may be incorrectly implemented, and patches are not always properly applied—sometimes something as simple as failure to restart can mean that you're still at risk. The best way to be sure that your IT environment is no longer at risk is to verify remediation efforts using Core Impact's one-step remediation validator.
Explore Other Core Impact Exploits
Core Impact provides up-to-date exploits they need in one place in a robust library designed to enable pen testers to safely and efficiently conduct successful penetration tests.