Core Impact Issues Latest Exploit for Log4Shell Vulnerability
The Log4Shell vulnerability, a serious remote code execution vulnerability in the Apache Log4j2 library, is one of the best candidates for winning several Pwnie awards in 2022.
What is the Log4Shell Vulnerability?
CVE-2021-44228 is an improper input validation vulnerability (CWE-20). Any attacker who controls log messages or log message parameters is able to execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. This can occur in any application that uses the open-source library and affects versions Log4j 2.0-beta9 up to 2.14.1. This vulnerability is incredibly dangerous, scoring a perfect 10 on 10 in the CVSS rating system, indicative of the severity of the issue.
Log4Shell poses enough of a threat that the Cybersecurity & Infrastructure Security Agency (CISA) has issued an alert advising organizations to take action by upgrading to Log4j 2.15.0 or applying the recommended mitigations that are listed in the Apache Log4j 2.15.0 Announcement.
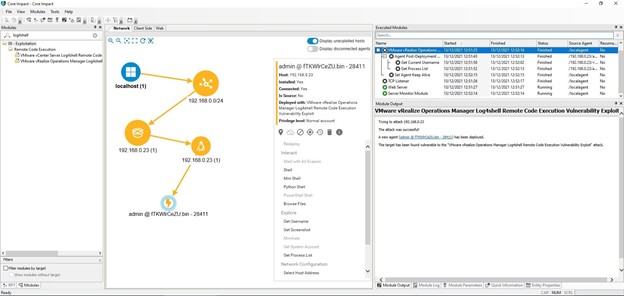
The Log4shell exploit being used against vRealize Operations Manager on Core Impact
Proactively Responding to Log4Shell with Core Impact
Core Impact customers can be proactive in their response since they can effortlessly run a pen test to see if this vulnerability is present in their infrastructures. Our exploits team has already created exploits for two VMware products: the VMware vRealize Operations Manager Log4shell Remote Code Execution Vulnerability Exploit and VMware vCenter Server Log4shell Remote Code Execution Vulnerability Exploit. Both are now available in the latest release of Core Impact, version 21.2. Please also note that at this time, Core Impact is not impacted by the Log4Shell vulnerability.
Core Impact's commercial grade exploit library is regularly updated with new exploits written and tested by pen testing experts. Our exploits team works to swiftly create high value and reliable exploits that will benefit our customers and help them achieve their pen testing goals.
Protecting Against Log4Shell and the Importance of Regular Pen Testing
As mentioned earlier, a patch is available for CVE-2021-44228. There are mitigations available for different affected products and, as advised by CISA, the option of upgrading to Log4j 2.15.0 or applying the recommended mitigations by vendors. However, mitigations may be incorrectly implemented, and patches are not always properly applied—sometimes something as simple as failure to restart can mean that you're still at risk. The best way to be sure that your IT environment is no longer at risk is to verify remediation efforts using Core Impact's one-step remediation validator.
Want to stay up to date on the latest exploits?
Subscribe to receive regular email updates on new exploits available for Core Impact.

