We are thrilled to announce the latest release of Core Impact! Version 21.5 is packed with exciting features and improvements that provide a smoother and even more efficient user experience.
Some of the new features include the option to use Impacket’s NTLMrelayx module to relay connections during an Active Directory attack, various coercion methods to trigger authentications into the relay servers, and a revamped and more user friendly interface for the Core Impact Dashboard. We have also made significant improvements to support CVSS 3 and 3.1 scoring for vulnerabilities, provided compatibility with the WiFi Pineapple Mark VII for Wireless network testing, and enhanced the web crawling process for web applications testing.
Our team has worked tirelessly to ensure that this version is the best one yet, and we hope that you enjoy using this new version as much as we enjoyed creating it!
Man-in-the-Middle and Coerced Authentications
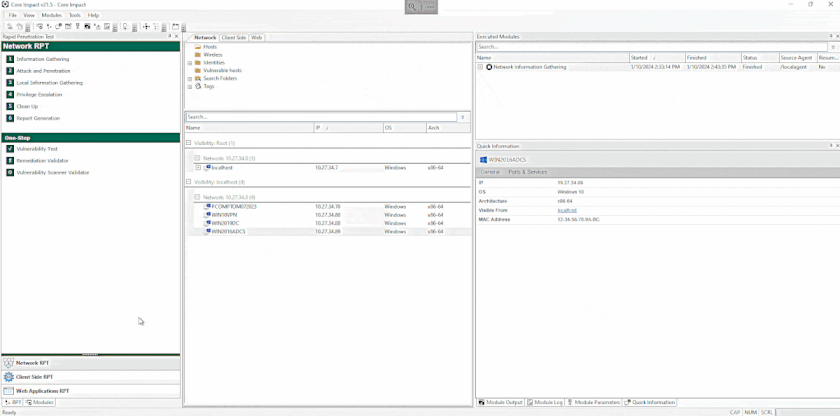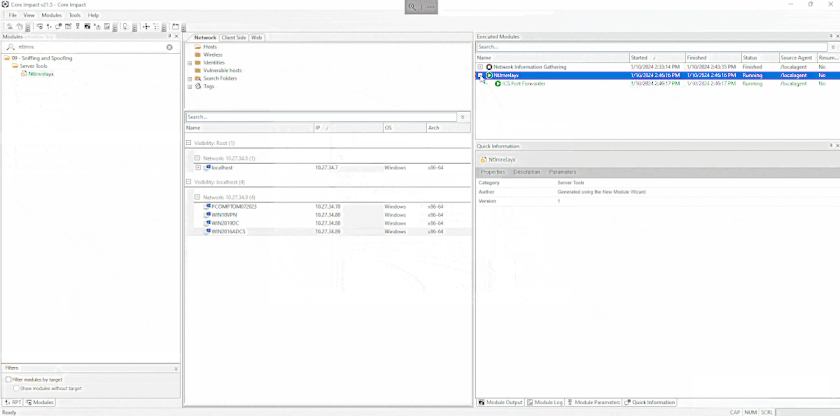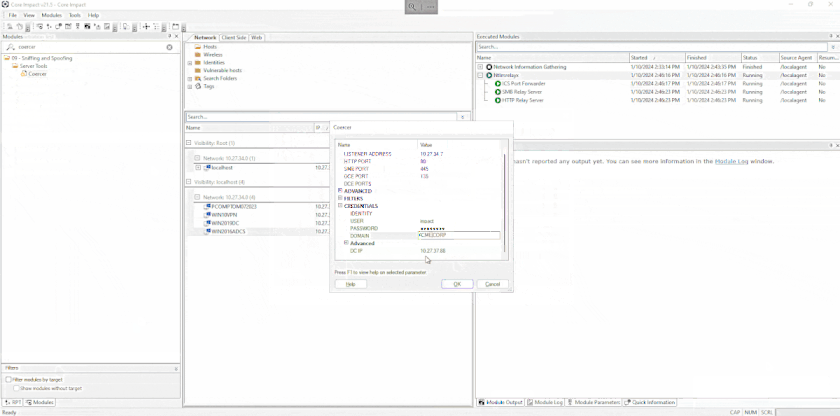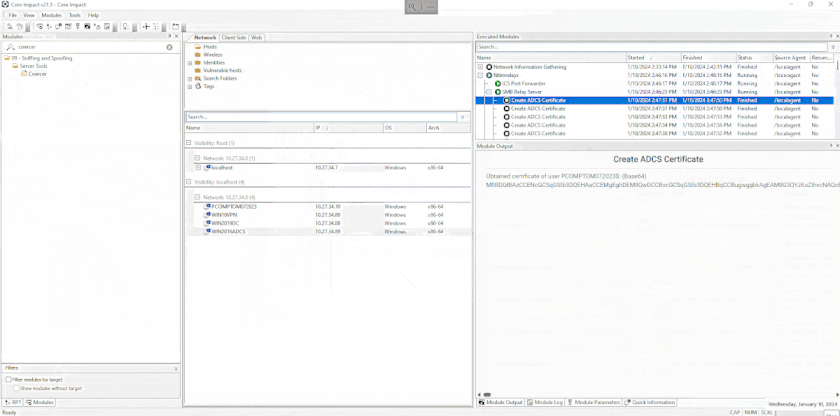
When testing Active Directory domains, attackers often use coerced authentications and man-in-the-middle (MitM) techniques to move laterally, especially when attempting authentication relaying attacks.
These techniques enable attackers to redirect traffic or coerce targets to authenticate against the attacker machine. The attackers can then capture the credentials/hashes or relay authentications.
There are many ways attackers can perform MitM or redirect/force targets to authenticate, most of which can be combined for maximum impact (and minimum stealth).
The implemented coercion methods within Core Impact are:
- PrinterBug on MS-RPRN discovered and implemented by @tifkin_ and @elad_shamir
- PetitPotam on MS-EFSR discovered and implemented by @topotam77
- ShadowCoerce on MS-FSRVP discovered by @topotam77 and implemented by @_nwodtuhs
- DFSCoerce on MS-DFSNM discovered and implemented by @filip_dragovic
- CheeseOunce on MS-EVEN discovered and implemented by @evilashz
All these attacks can be triggered from a brand new and easy to use module called Coercer. Once the authentications have been coerced, it is possible to use the new NTLMrelayx module to relay those connections to another system and automatically run an attack module to install an agent via SMB, generate a certificate using ADCS, or run some LDAP queries amongst other attacks.
You can see a short demo of this new feature below:
New Dashboard and Workspaces Management
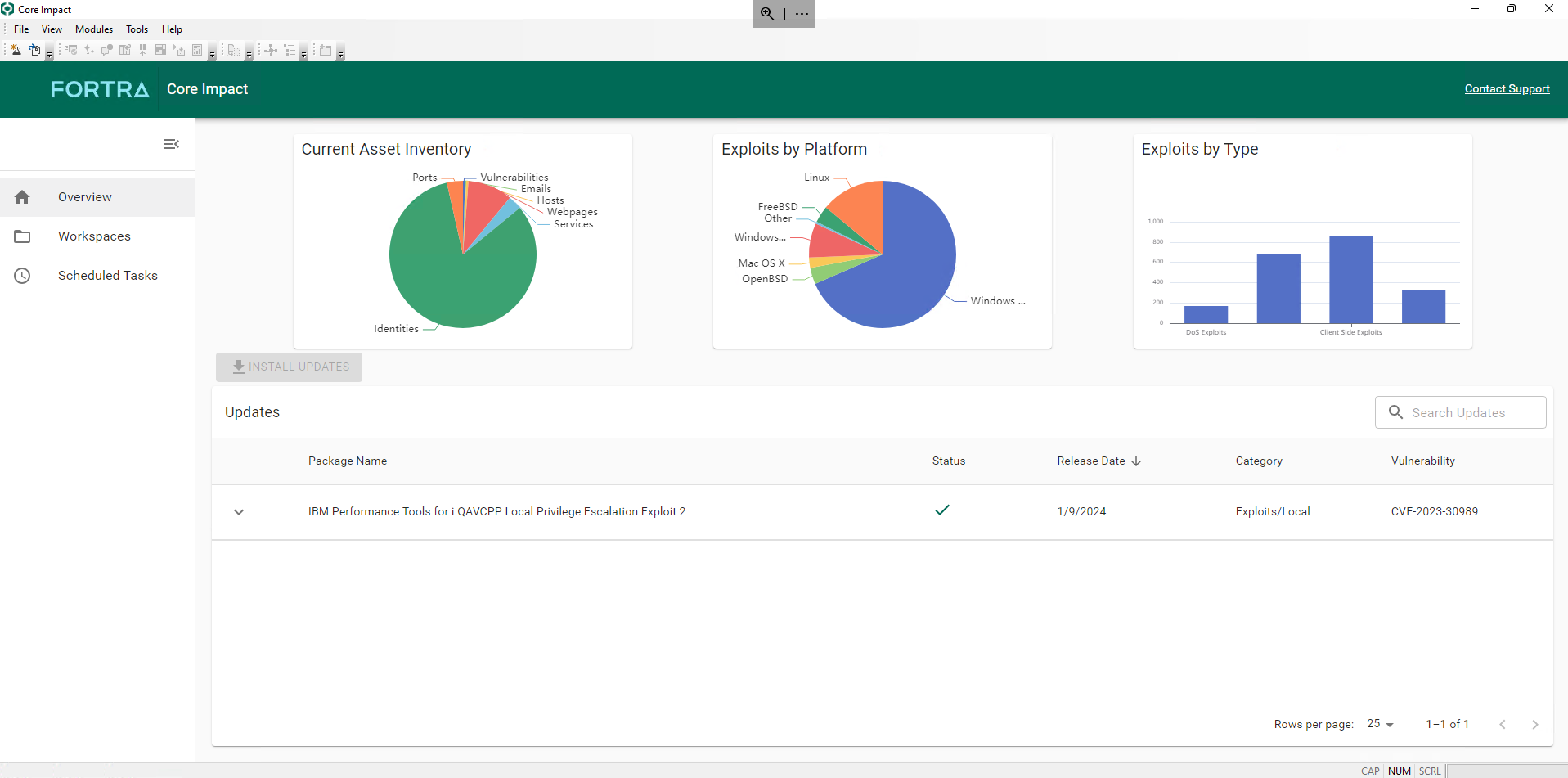
We are continuing to modernize and revamp the user interface of Core Impact. The new release includes a brand new dashboard:
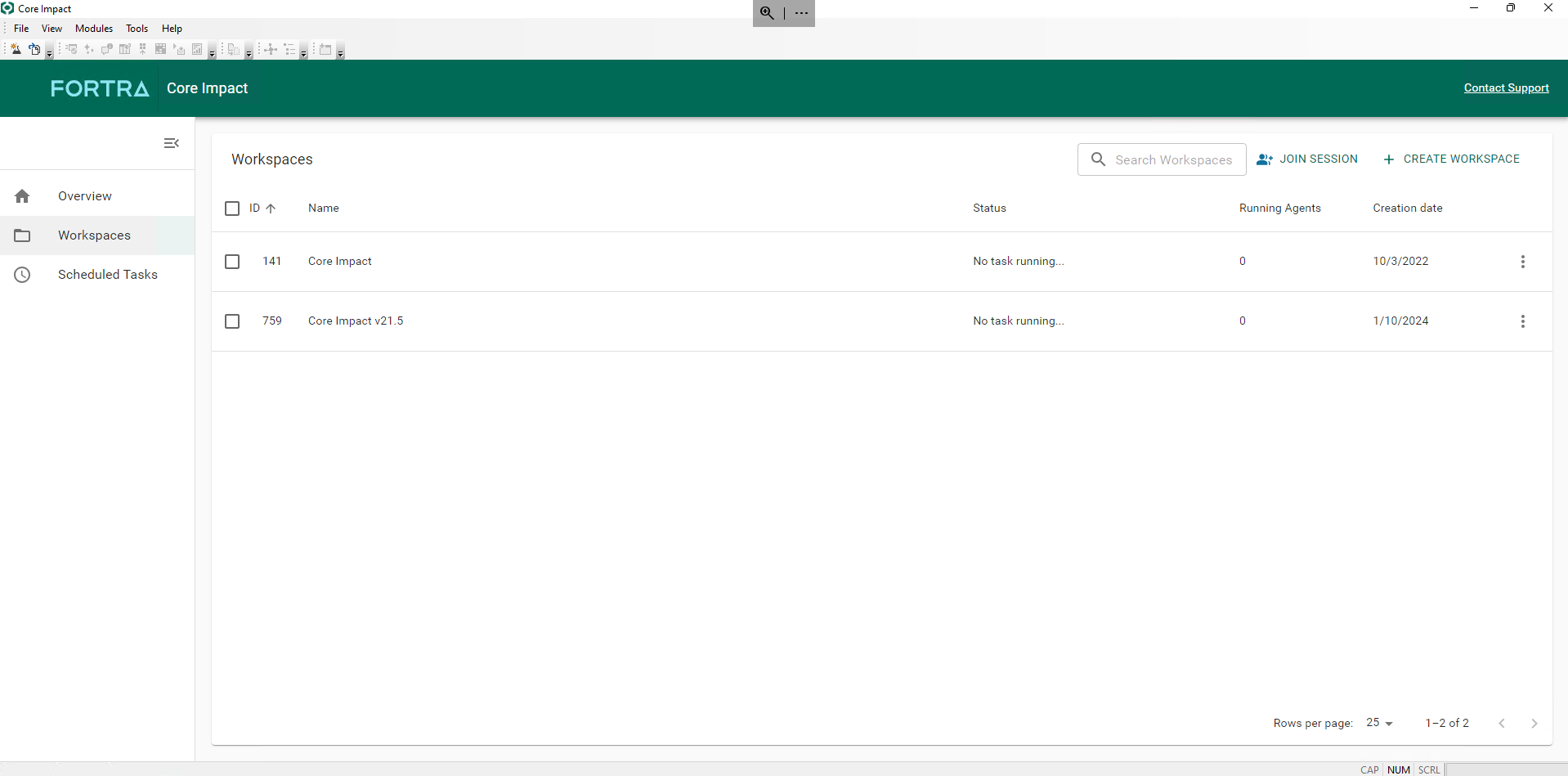
A new workspaces management view is also now available:
CVSS Scoring System
Core Impact is now supporting CVSS v3 and v3.1 as the scoring system for vulnerabilities. Additionally, the product has been prepared to support version 4.0 as soon as it is adopted by NIST NVD.
Updating to the New Release
To see a full list of what’s new in Core Impact 21.5, please check out the release notes. Licensed users can get the latest version from the Fortra Support Portal. To purchase Core Impact or learn more, please contact us.
Want to see more Core Impact features in action?
Watch a demo for a full overview of this powerful penetration testing tool.

