Given its functionality as a multifaceted toolset, there are some features of Core Impact that users may not have taken advantage of. In this post, we’ll talk about SOCKS tunneling. Namely, we’ll walk through use cases of Core Impact’s SOCKS proxy capabilities and how to use it together with Cobalt Strike.
What is SOCKS Tunneling?
SOCKS Tunneling allows operators to run Core Impact modules and exploits through the Cobalt Strike Beacon chain without having to deploy an agent in the compromised network.
Use Case: Remote Code Execution Exploits through SOCKs
The first use case is related to compromising a Linux machine in the target network using a Remote Code Execution exploit. Starting an engagement with Core Impact brings two features into Cobalt Strike that can be especially handy in a real-world engagement: Exploits and a Linux implant.
The architecture set up and traffic flow will look like this:
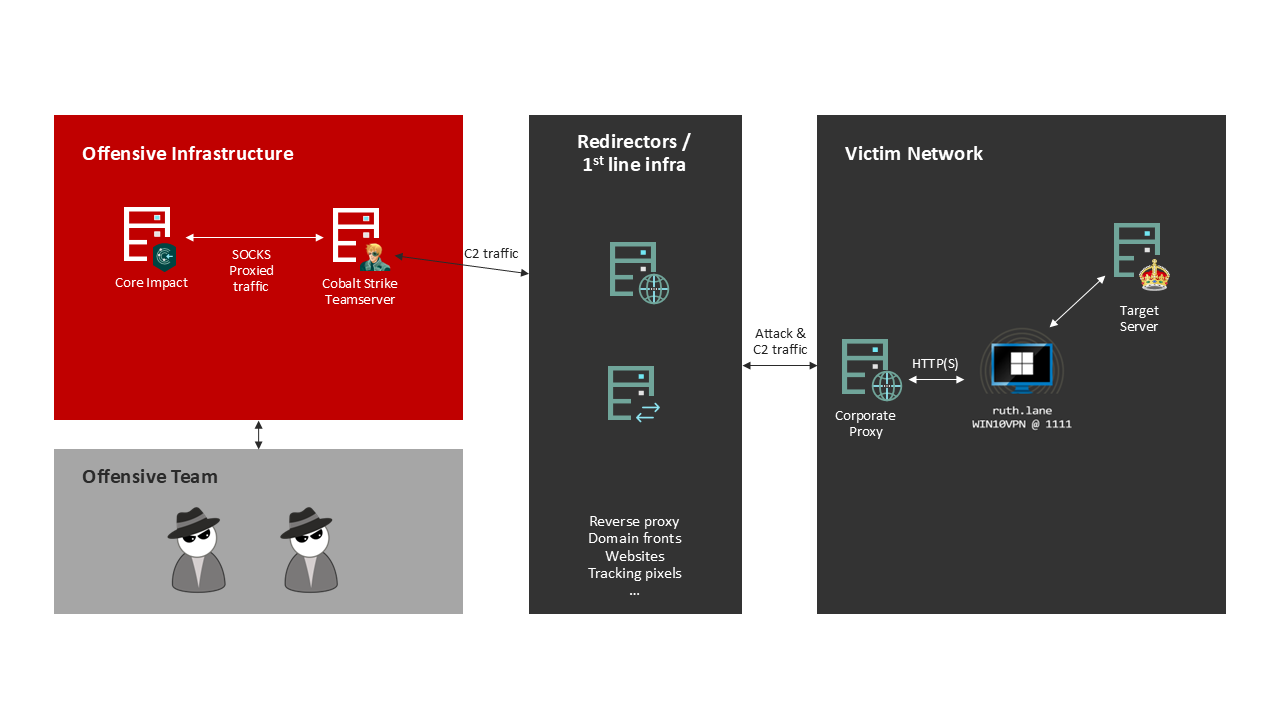
And the workflow steps would be:
- Core Impact sends the exploit through the SOCKs Proxy port at the teamserver and it is redirected to the remote beacon
- The remote code execution exploit is executed on the target system
- If the Exploit is successful, a new Core Impact implant is deployed!
- The C2 traffic returns to Core Impact through the Beacon chain to establish the connection.
- The target machine is then compromised.
Use Case: NTLM relaying via Cobalt Strike
Despite the work that Microsoft is doing to enhance the security of its operating system by improving defense mechanisms against NTLM relay attacks, unfortunately, these attacks continue to persist.
For this use case, red teamers can help organizations prepare for these types of attacks. Operators can relay an NTLM connection through Cobalt Strike’s SOCKs proxy to leverage the unpatched Active Directory Certificate Services (AD CS) vulnerability in the Web Enrollment Feature. This is not trivial for several reasons.
Assuming you’ve compromised a Windows endpoint, normally the port 445 will already be bound by the Operating System. To overcome this situation, we'll use the smbtakeover tool from zyn3rgy that unbinds and rebinds the 445/TCP port without loading a driver, loading a module into LSASS, or rebooting the target machine.
Once that is done, we'll use the rportfwd command which will bind the 445 port on the compromised machine, tunnel that traffic back to the team server, and forward it to the specified Core Impact IP and port.
As Rastamouse stated in his blog, in a real-world scenario, you'd set things up in reverse order to make sure everything's ready to go before redirecting the traffic, so you don't miss anything important.
The architecture set up and traffic flow will look like this:
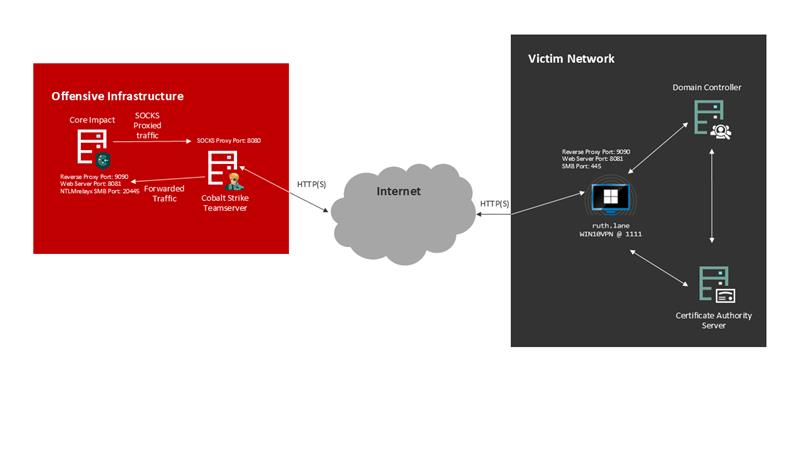
And the workflow steps would be:
- Assuming we already have the SOCKs proxy started in Cobalt Strike and the tunnel active within Core Impact, the next step would be to launch the NTLMrelayx module inside Core Impact. We would be then ready to start receiving connections.
- Go to Cobalt Strike and unbind the 445 port using the smbtakeover tool.
- Start the reverse port forward from 445 in the beacon to the NTLMrelayx SMB server port. When a connection is received through the port 445 , it will be redirected to the NTLMrelay server running within Core Impact.
- When a connection is received, Cobalt Strike will tunnel the traffic all the way to Core Impact where NTLMrelayx is listening and the connection is relayed through the SOCK proxy to the target machine in the internal network. That connection is then stored in the Core Impact connection store to be used in further attacks.
Check out the video below to see both of these use cases in action:
The Value of Extending Engagements
Core Impact and Cobalt Strike interoperability through SOCKS proxy provides extensive opportunities for enhanced red teaming operations. To purchase Core Impact or learn more about the benefits of bundling these tools, please contact us.
Credits and References
- https://github.com/zyn3rgy/smbtakeover
- https://rastamouse.me/ntlm-relaying-via-cobalt-strike/
- Why Relay Attacks Are Still Common and How to Prevent Them | Core Security Blog



