NTLM (NT Lan Manager) relay attacks are still a significant threat to the security of Windows based networks. Though it is a well-known attack method that has been around for many years, it is no less dangerous than when it first emerged. In fact, it has been an attack method that is currently popular with “aggressive” hacking groups, including the Russian APT28. These groups have successfully used relay attacks to target multiple high-value targets worldwide.
In this post, we will look into the details on how to simulate this kind of attack within Core Impact to uncover hidden attack paths that nefarious actors could leverage to access high-value confidential information.
Lab Setup
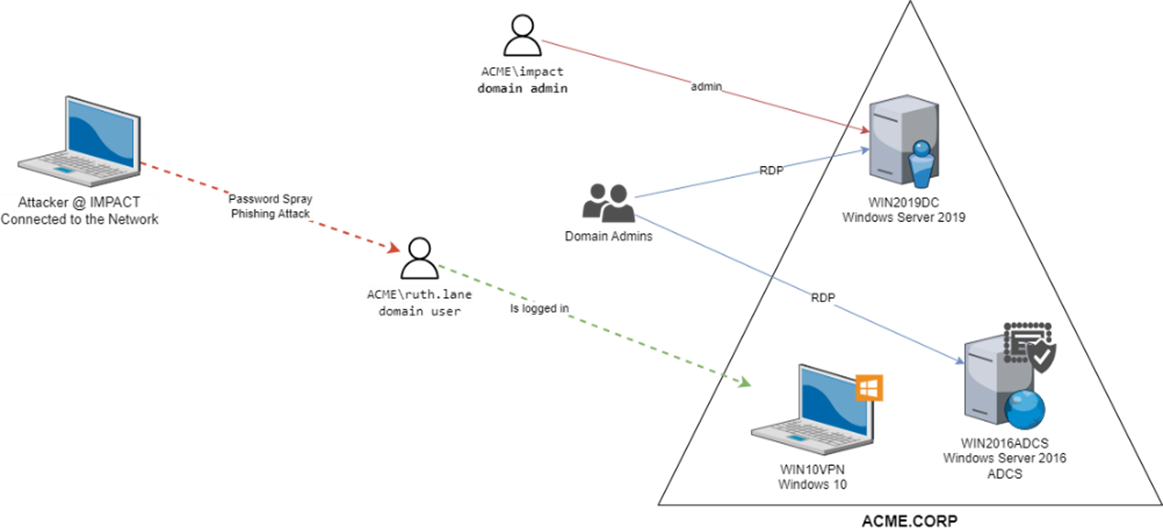
The attack lab consists of four machines:
- A Windows Server 2019 as a Domain Controller (WIN2019DC).
- A Windows Server 2016 as Certificate Server (WIN2016ADCS).
- A Windows 10 Workstation (WIN10VPN).
- A Windows 11 Workstation with Core Impact installed (IMPACT) as the Attack machine.
Domain Controller Setup (WIN2019DC)
The domain controller is set up with default configurations. You can follow our setup walkthrough.
Workstation Setup (WIN10VPN)
The workstation machine needs to be added to the Domain and the DNS server should be updated with the Domain Controller address. You can follow our setup walkthrough.
Certificate Authority Setup (WIN2019ADCS)
The Certificate Authority machine needs the to be configured with Web Enrollment services installed. You can follow our setup walkthrough.
The Attack Machine (IMPACT)
The attack machine is a standard Windows 11 box with Core Impact installed and access to the vulnerable network. You can follow our setup walkthrough.
Simulating the Relay Attack
As a starting point, we have compromised a Domain User (ruth.lane) on the WIN10VPN machine. The machine is part of the ACME.CORP domain.
The attack steps are:
- Force the Domain Controller (WIN2019DC) to authenticate to the Core Impact machine (IMPACT) running the module NTLMrelayx using the Coercer module.
- Use NTLMrelayx to relay the Domain Controller credentials to the AD CS (Active Directory Certificate Services) on WIN2019ADCS.
- Obtain the PFX certificate for the WIN2019DC$ machine account.
- Ask for a TGT (Ticket Granting Ticket) using the previously obtained certificate.
- Get the NT Hash for the Domain Controller machine account.
- Obtain the NT hashes for the domain users using a DCSync attack.
- Deploy an agent in the Domain Controller.
- Enjoy your newly obtained Domain Admin permissions!
Steps 1-3: Get the Domain Controller Machine Account Certificate.
Demo
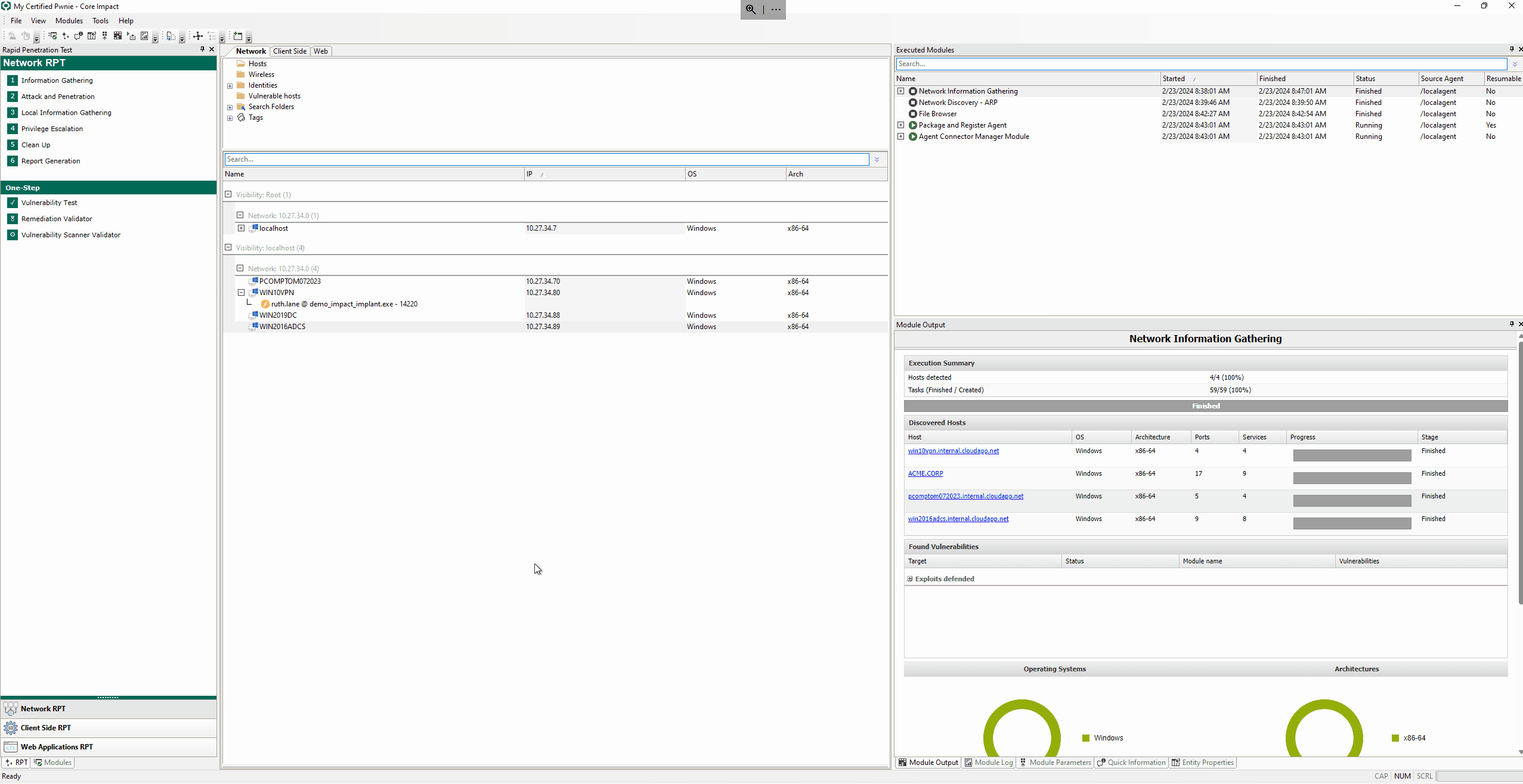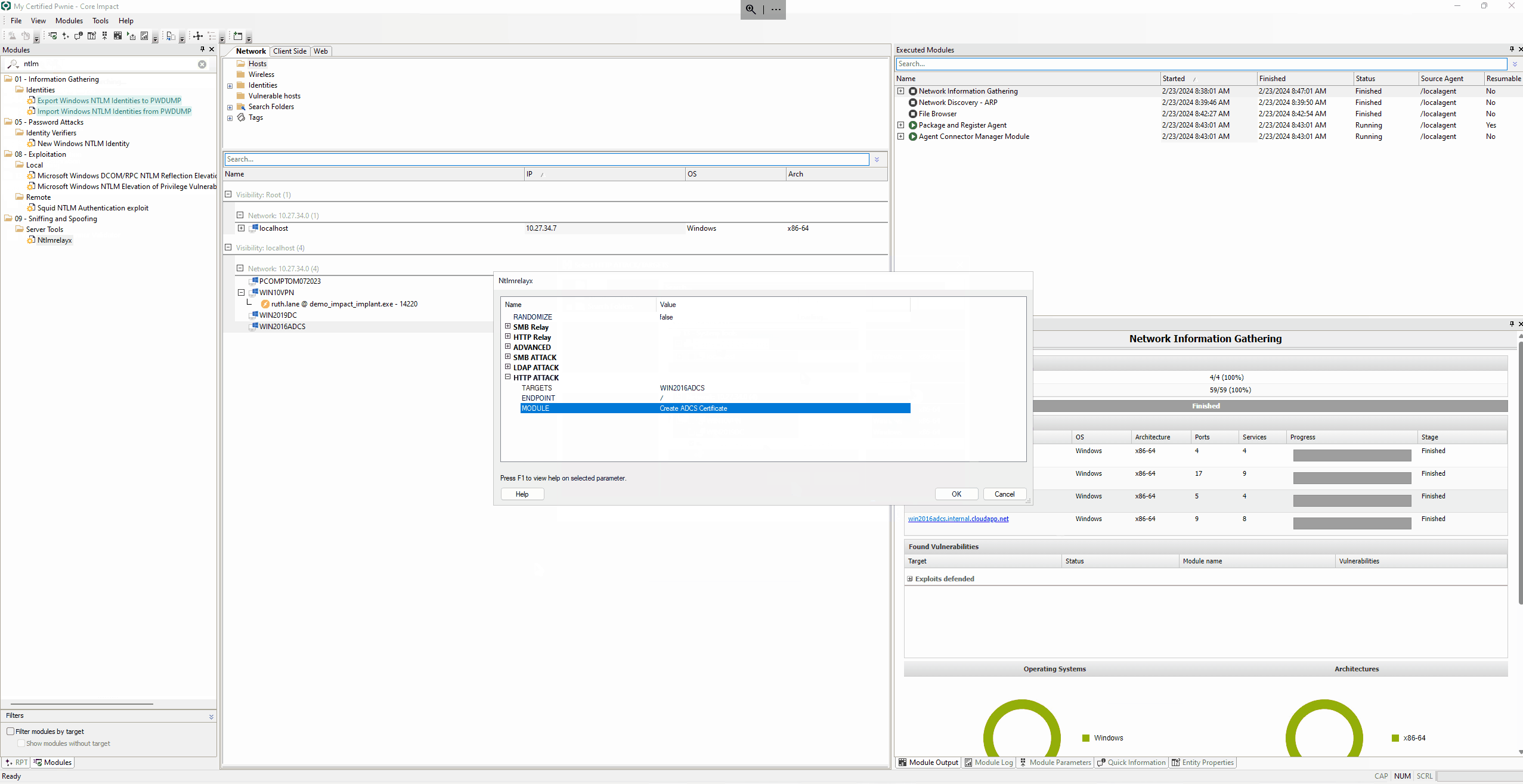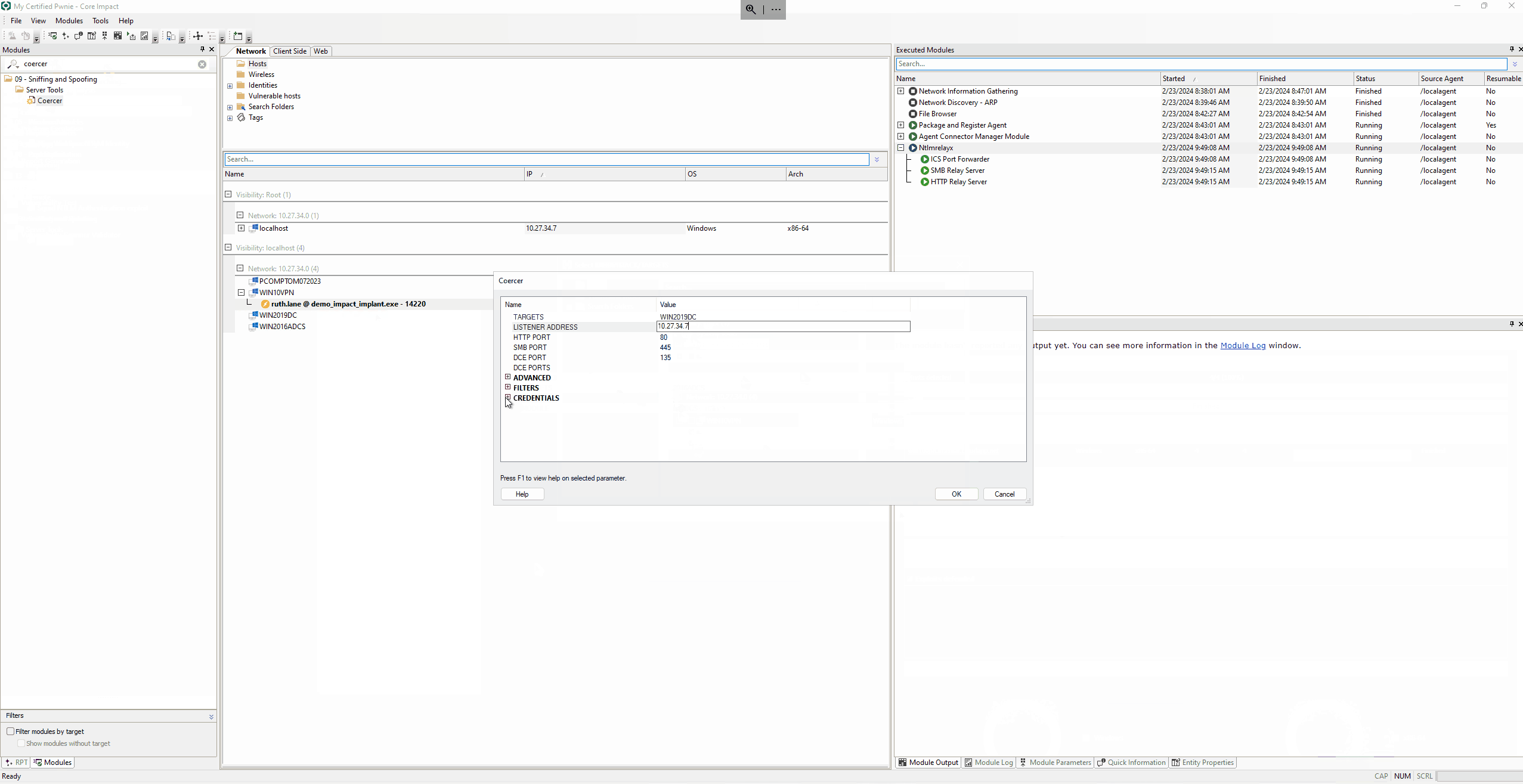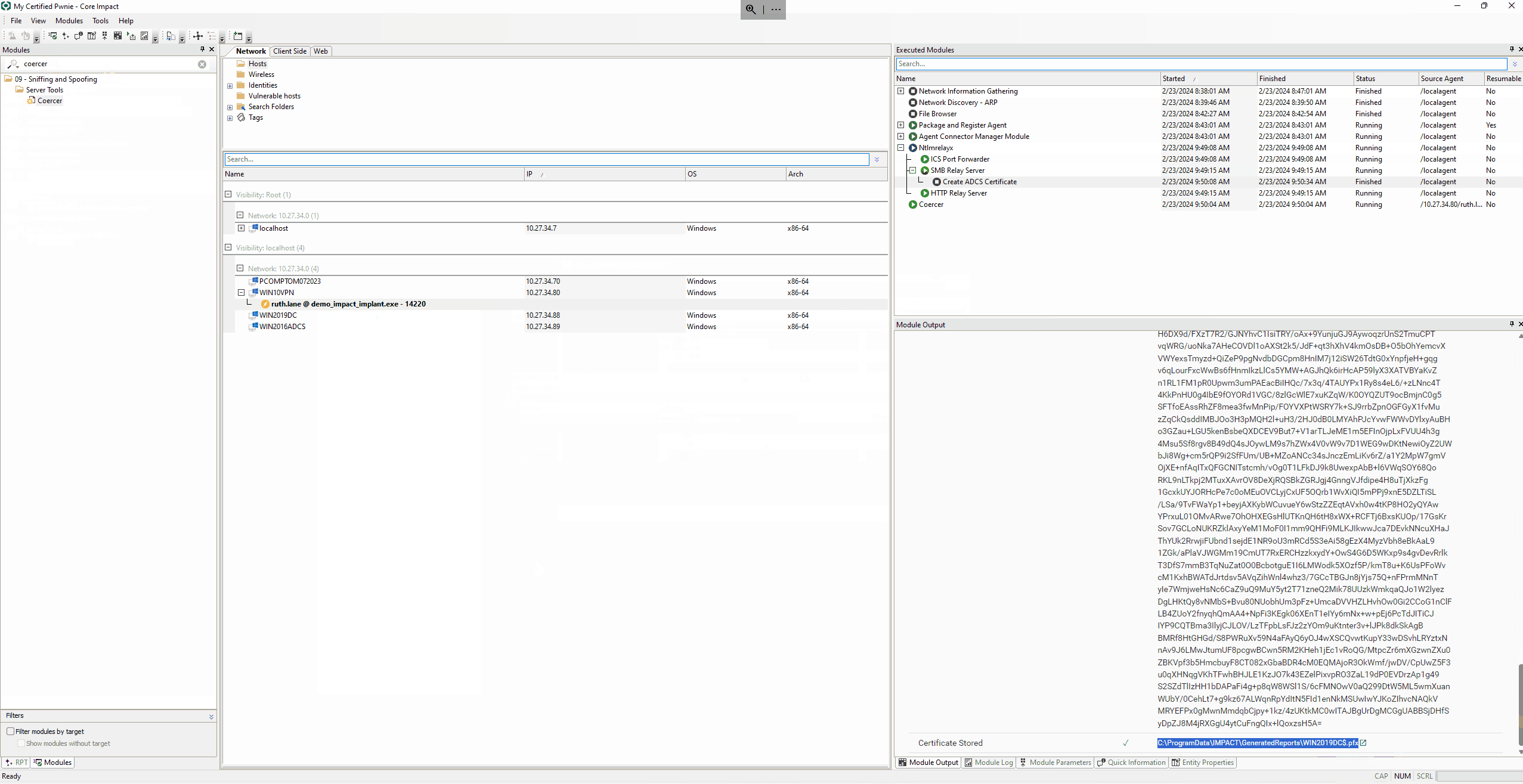
NTLMrelayx Configuration
Before you can force an authentication from the Domain Controller, you need to configure the NTLM relay with the Ntlmrelayx module to set it up. The target host for the Create ADCS Certificate attack will be the WIN2019ADCS and the endpoint /certsrv/certfnsh.asp.
Coercion
The second step is to force the Domain Controller (WIN2019DC) to authenticate to the Core Impact machine using the Coercer module. Running the module is very straightforward:
- Select the agent in the WIN10VPN machine as Source Agent.
- Double click on the Coercer module to set the WIN2019DC machine as TARGET, the IMPACT machine IP as LISTENER ADDRESS, and fill the credentials info.
If everything goes well, the Domain Controller will request a certificate from the Certificate Authority and the obtained certificate will be stored in the Core Impact machine.
Steps 4-5: Obtain a TGT With the Generated Certificate.
Demo
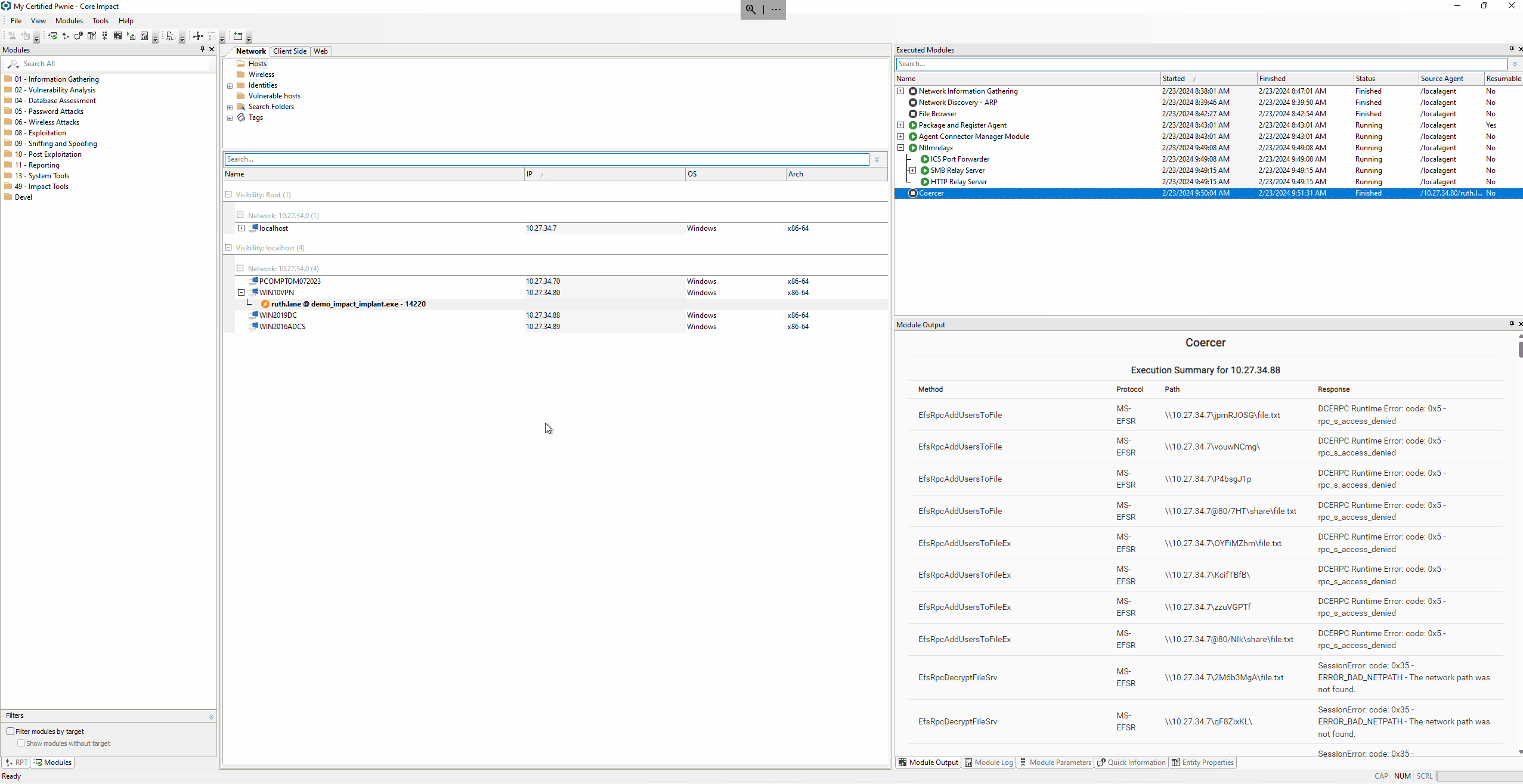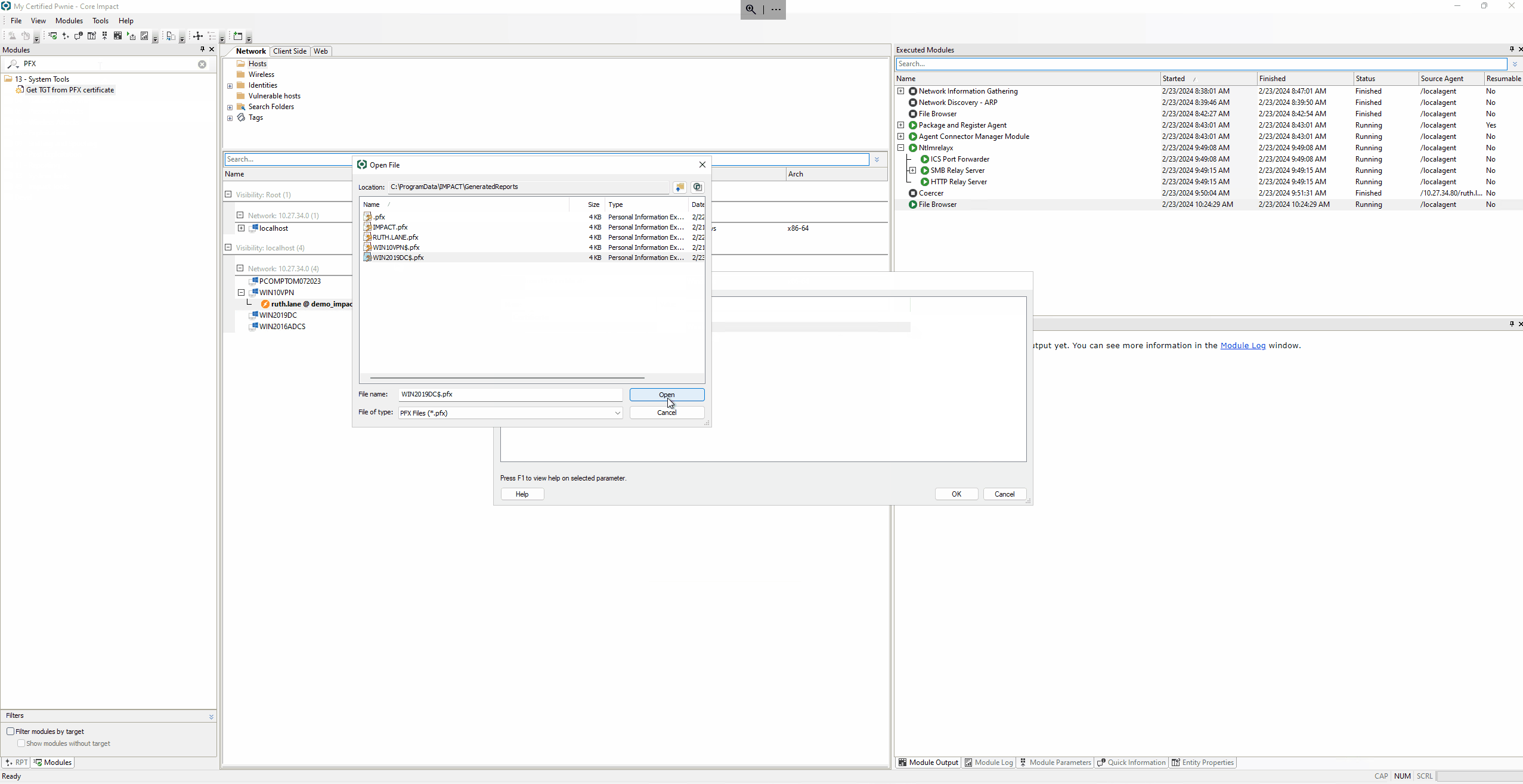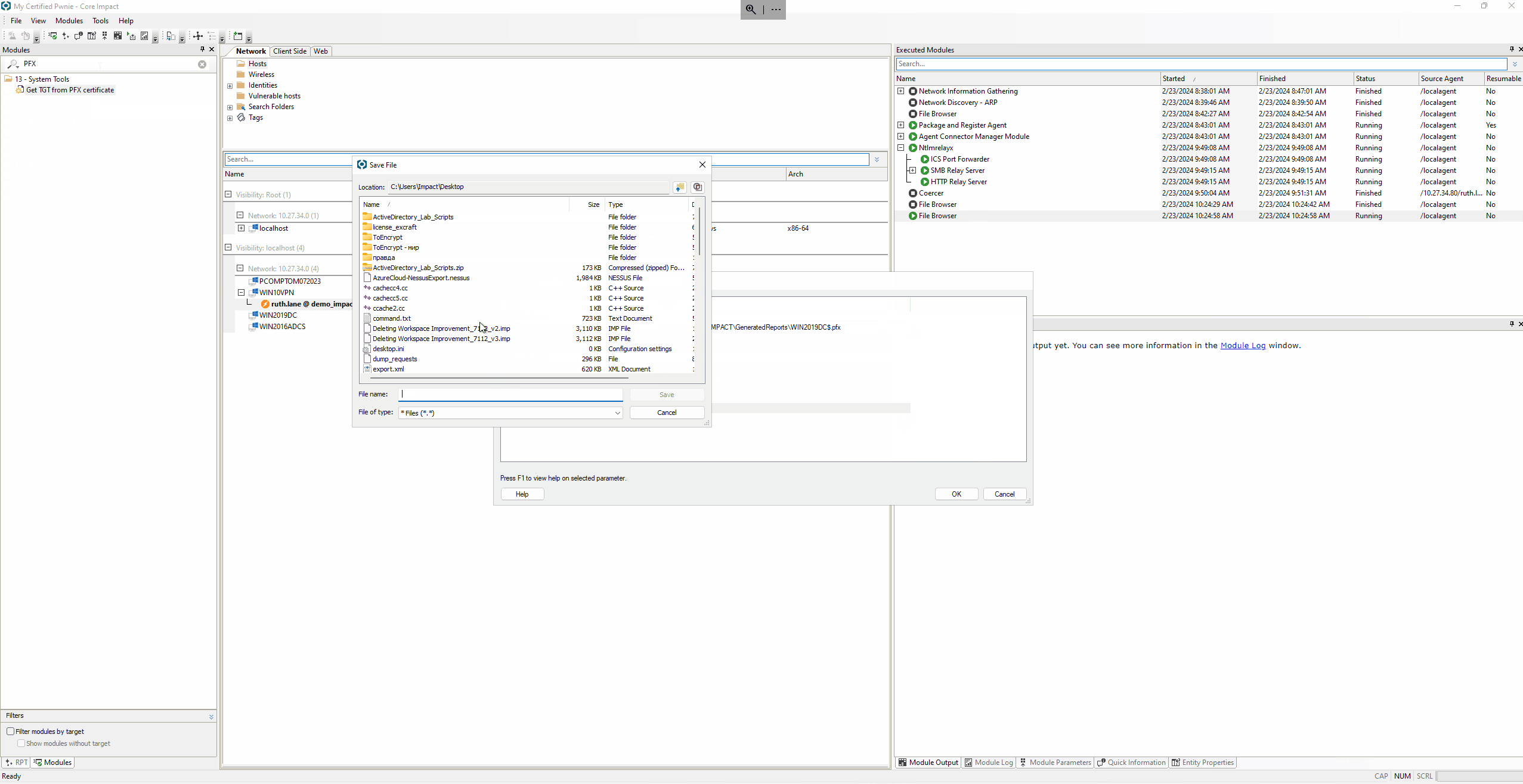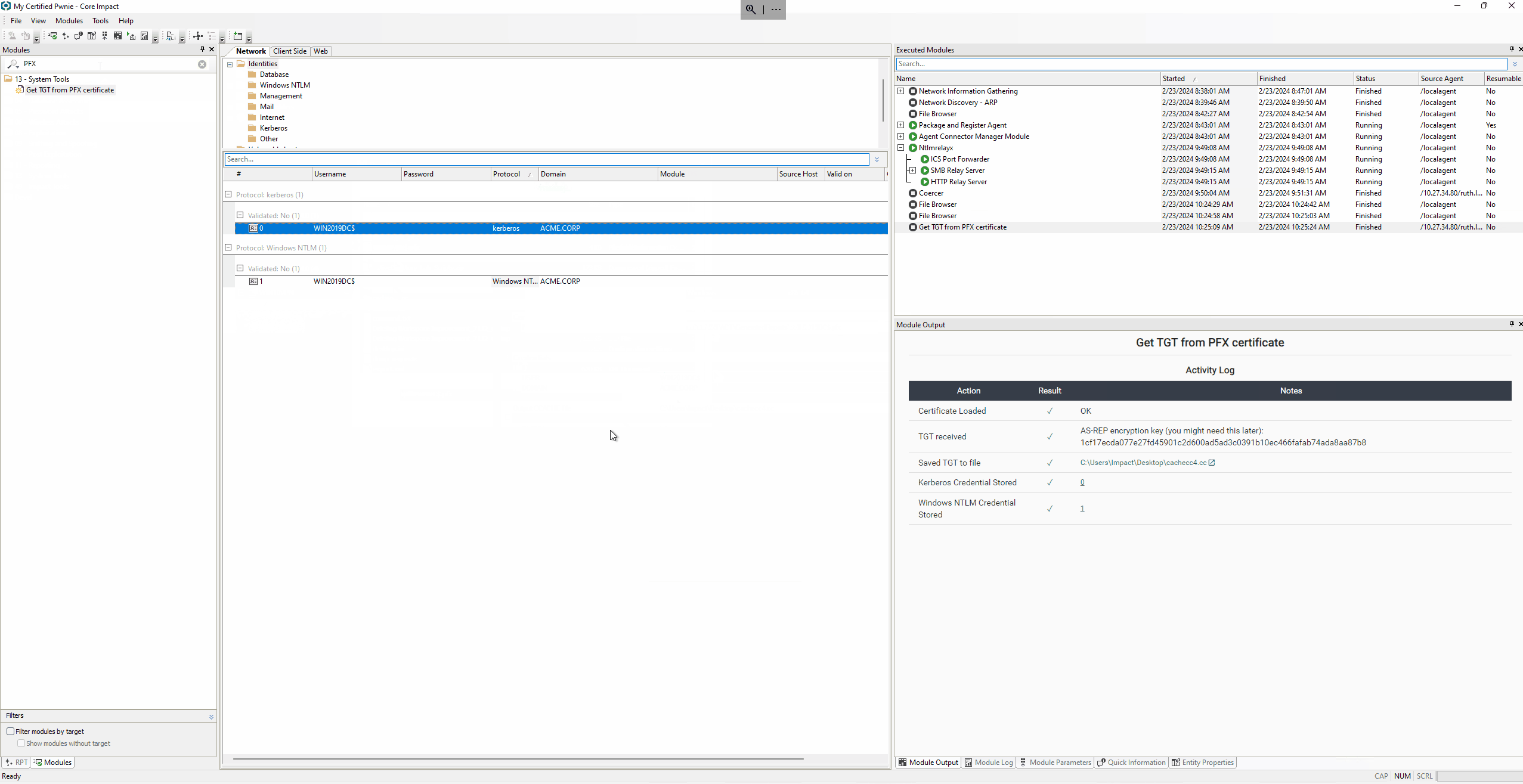
Get TGT from PFX certificate.
With the generated certificate it is now possible to impersonate the Domain Controller machine account (WIN2019DC$) and request a Ticket Granting Ticket (TGT) to authenticate to the Domain Controller without credentials.
The TGT is requested with the Get TGT from PFX certificate module that uses a technique described by dirkjanm in the PKINITtools project.
Once the TGT is received, the module will automatically obtain the NT Hash and will store two different credentials: the Kerberos protocol with the TGT and a Windows NTLM with the NT Hash.
Steps 6-8: Obtain a TGT With the Generated Certificate.
Demo
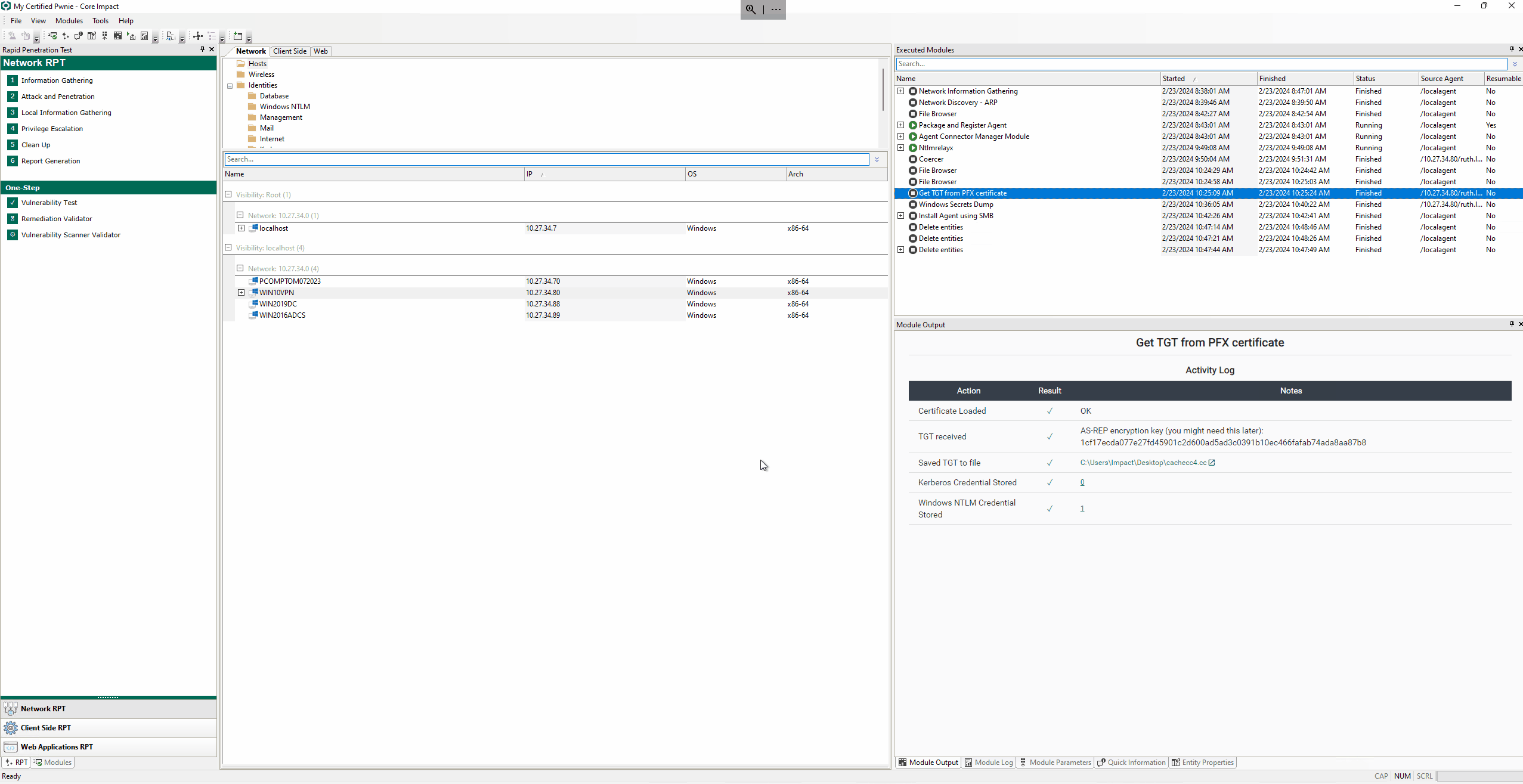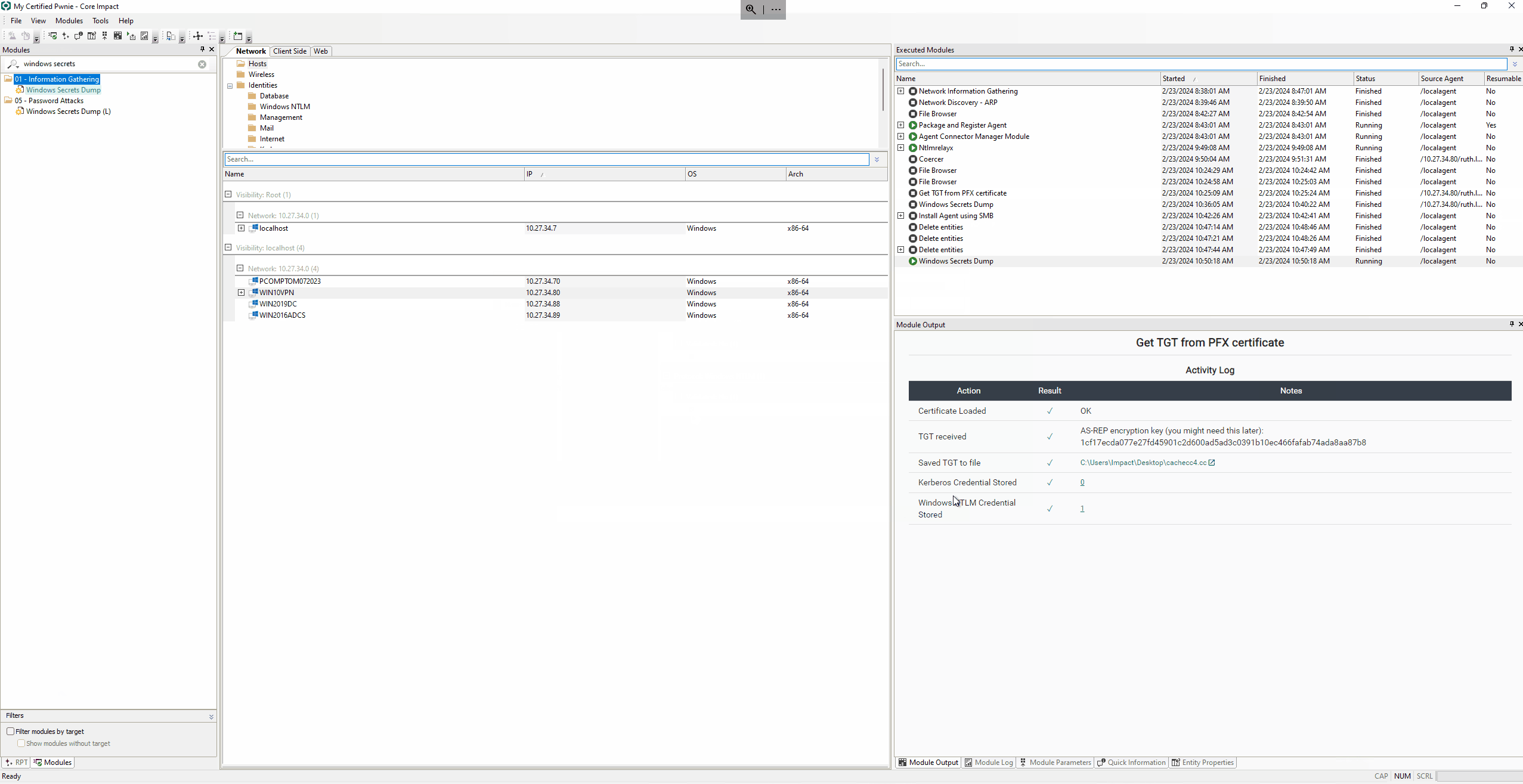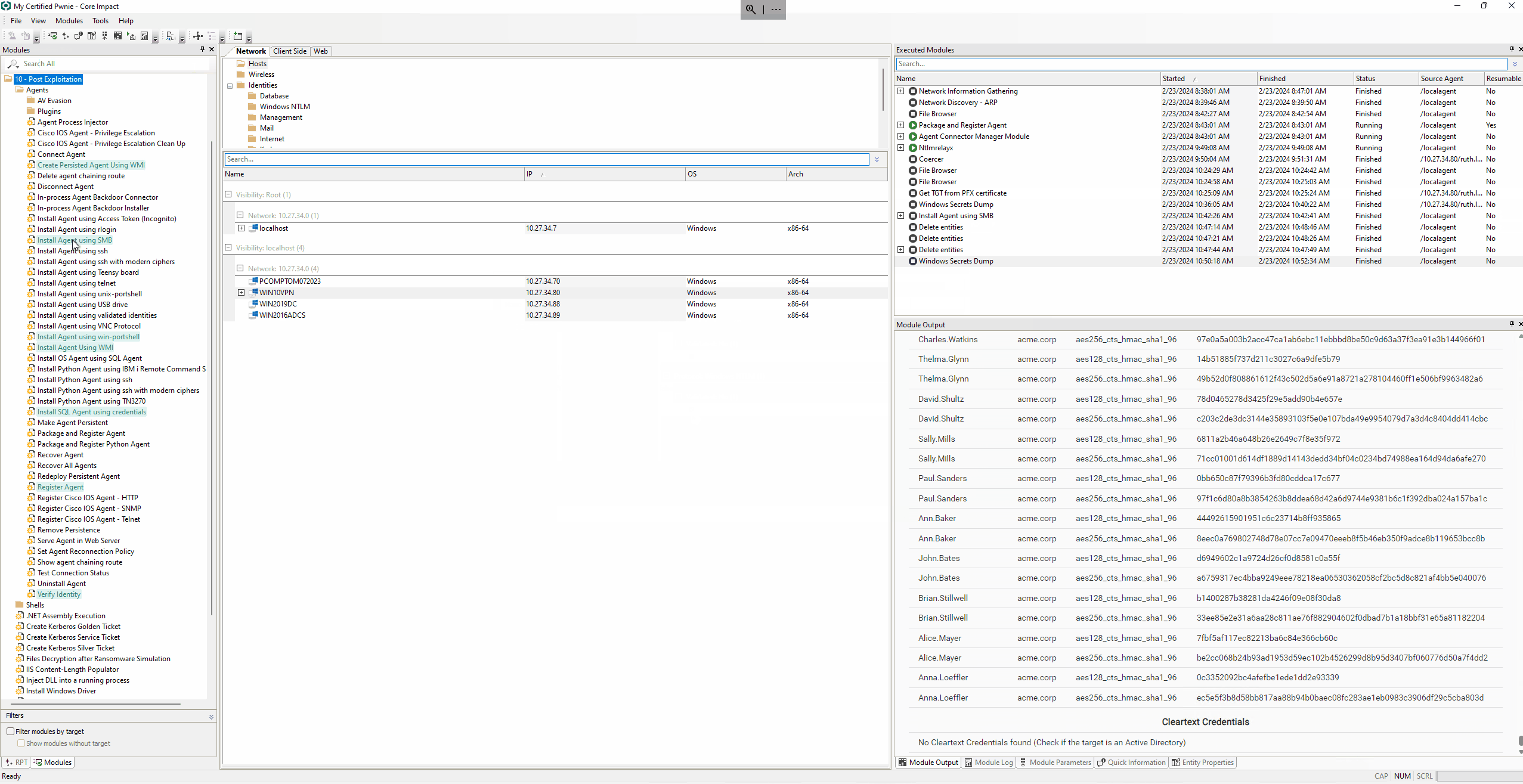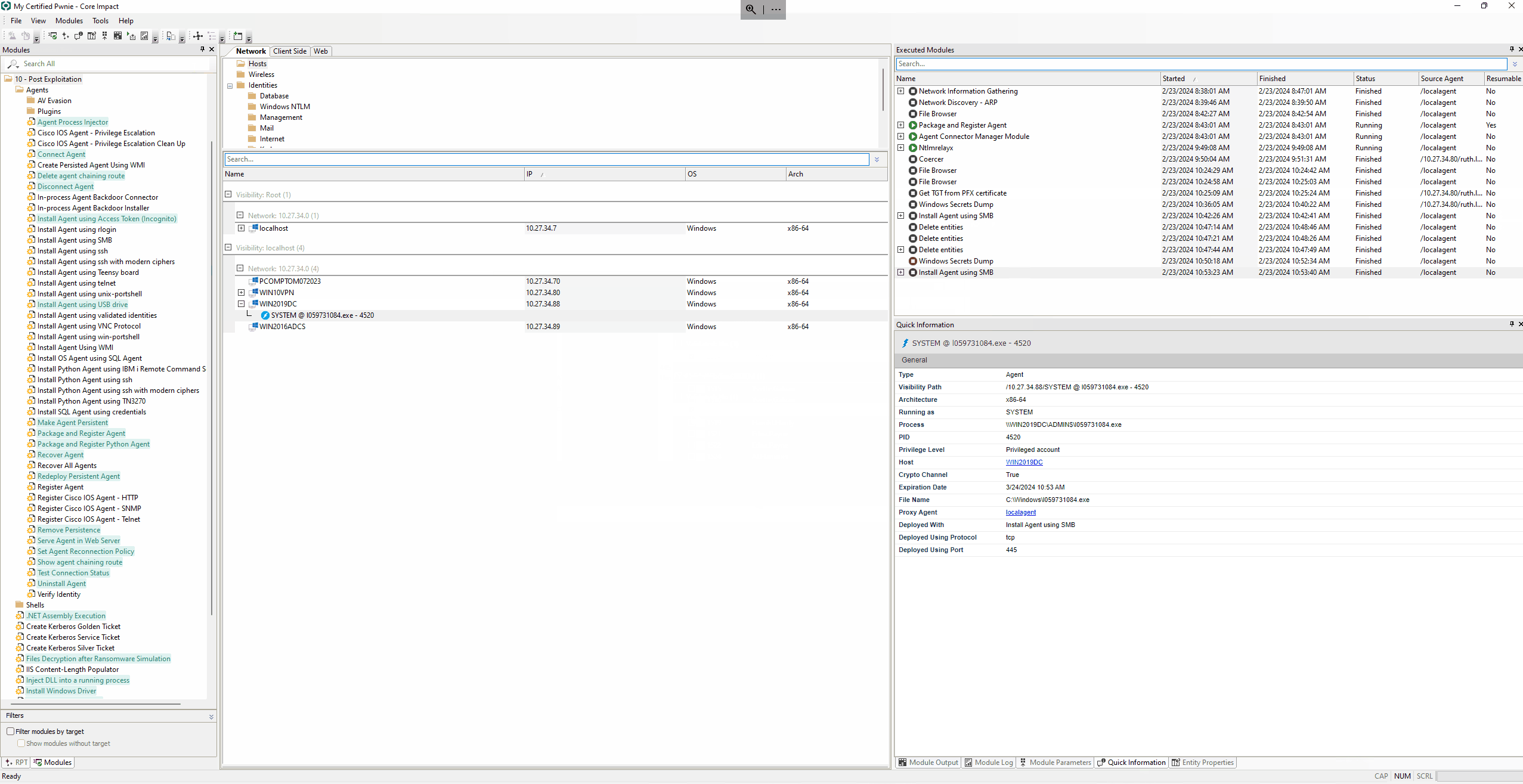
Dcsync using Windows Secrets Dump
With any of the generated identities, you can run the module Windows Secrets Dump on the Domain Controller (WIN2019DC) and perform the DCSync attack to retrieve all the domain hashes.
These hashes can be reused on further steps of the attack or can be sent to the Core CloudCypher Service to attempt to crack them.
Next, get the krbtgt hash that enables the creation of a golden ticket to access any service within the domain and the impact hash that can be used with the pass-the-hash technique and authenticate to the domain controller.
Install an agent using SMB.
With the impact Windows NTLM identity, you can deploy an agent via SMB into the Domain Controller as SYSTEM and get persistence as Domain Administrator.
You can go further in your test following the full walkthrough for Core Impact.
Mitigations
- Enable EPA and disable HTTP on AD CS servers (MS KB5005413).
- Disable NTLM Authentication on your Windows domain controller and on any AD CS Servers in your domain (MS KB5005413).
- Enable Require SSL, which will enable only HTTPS connections on AD CS servers (MS KB5005413).
Credits and References
Learn more about Core Impact
See Core Impact's feature in action in our on-demand demo.


