Core Impact 21.6 is now available. This release sees the introduction of the Connection Store, new reporting features, a newer UI for the entities Quick Information panel, a series of quality-of-life changes and more.
(Re)Relay connections through the Connection Store
Once intercepted, connections are a very valuable asset for pen testers. There are many advantages to connections, even independently of the privileges of the victim’s account. The attack paths towards the crown jewels or other valuable assets cannot be discovered until multiple approaches have been tested.
Until now, relayed attacks could only be launched once per successful relayed authentication (one-shot), and this approach was missing several use cases, most of them involving non-administrative accounts.
This use case is covered within Impacket with the SOCKs feature. In this new version of Core Impact, we’ve leveraged the power of NTLMrelayx along with Core impact's automation, persistence, and inventory capabilities to resolve the issue in a way that is simple enough for initial testing, but also powerful enough for advanced use.
The extension of the NTLMrelayx functionality in Core Impact allows operators to:
- Keep the connections in the Connection Store as long as possible when the authentication data is successfully relayed.
- Relay the same connection to any possible protocol on demand.
- Run different Core Impact attack modules with the same connection.
This diagram describes the Connection Store functionality at a high level:
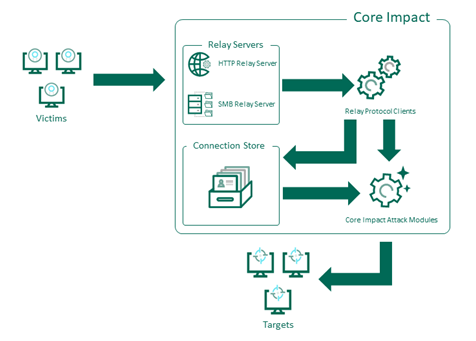
Examples of the Connection Store in Action
To understand this new feature better, we’ll go through some examples:
Users can run the NTLMrelayx module with the desired configuration for the HTTP and SMB servers on the selected agent (localagent or a remote one). The targets can be configured per protocol in the wizard or through an external file.
In the previous version of Core Impact, the relayed attacks were one-shot, and the connection could be used only once for a selected attack. With the newly released Connection Store, all the capture NTLM connections are stored and can be used at will by the operator.
In the following example, the NTLMrelayx module is launched and captures an HTTP connection and an LDAP connection. The first one is used to generate an ADCS certificate, and the second one is used to connect via LDAP to the Domain Controller and list the users valid for a Kerberoasting attack and those that could be useful for an AS-REP Roasting attack.
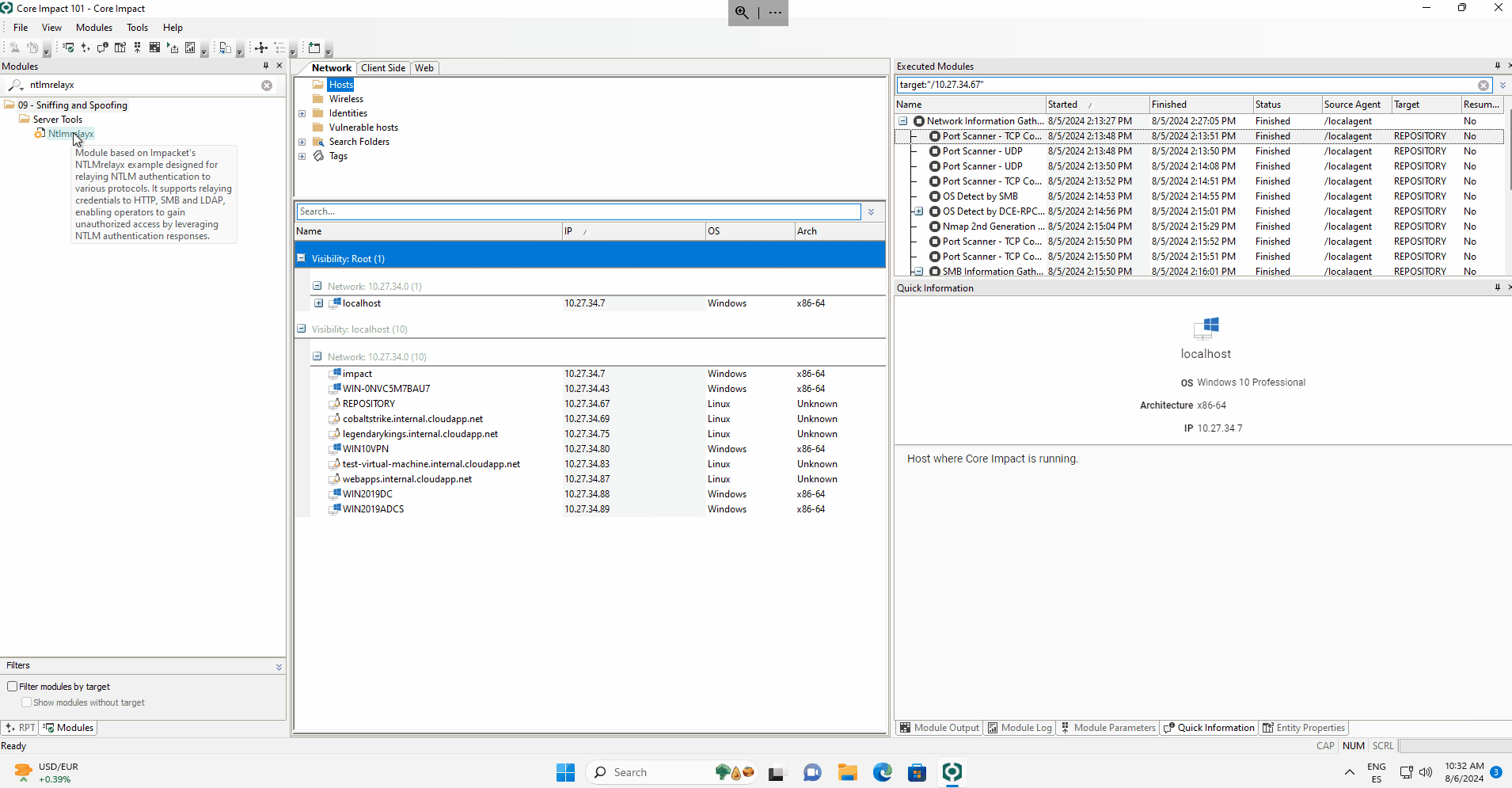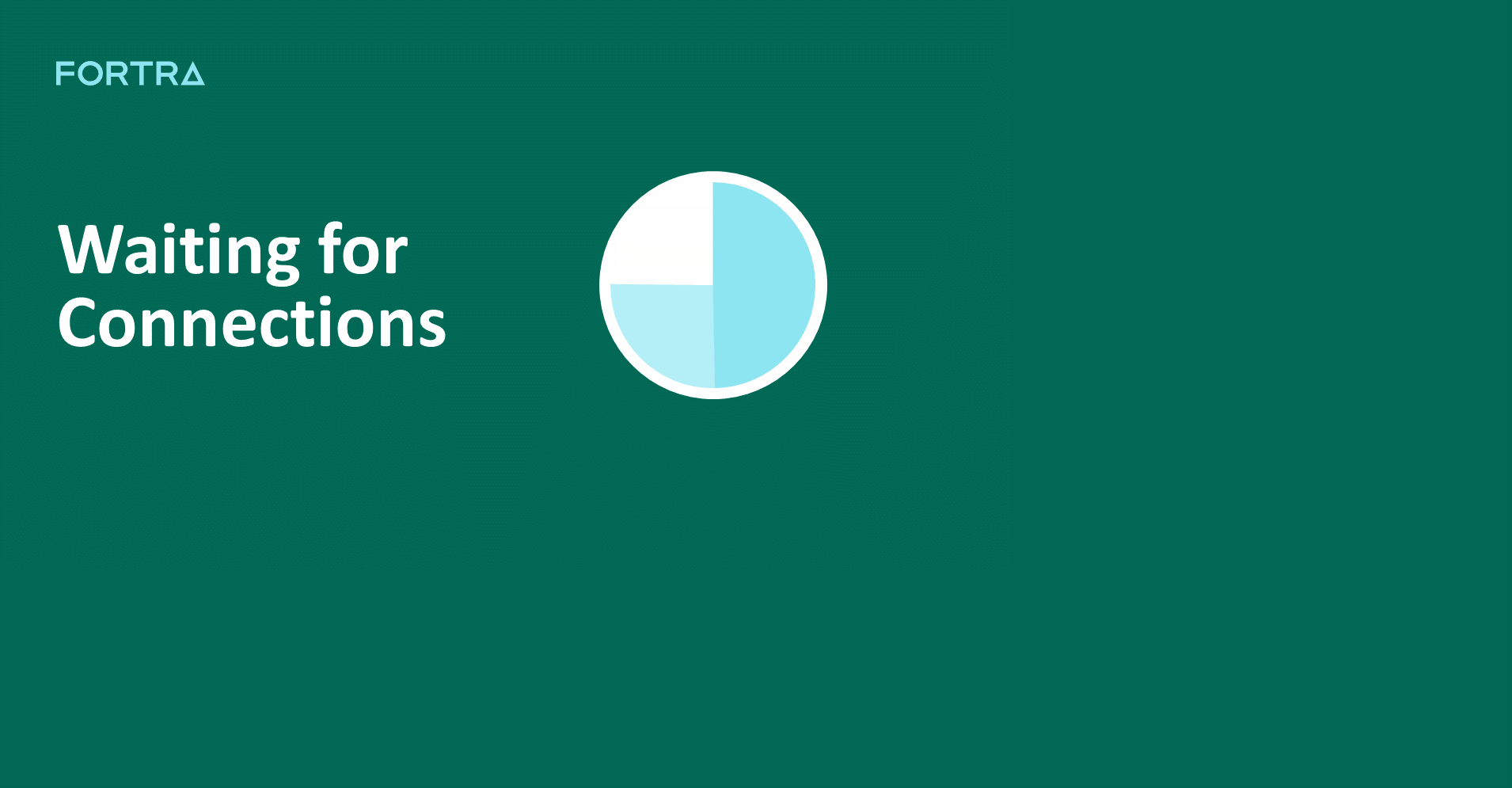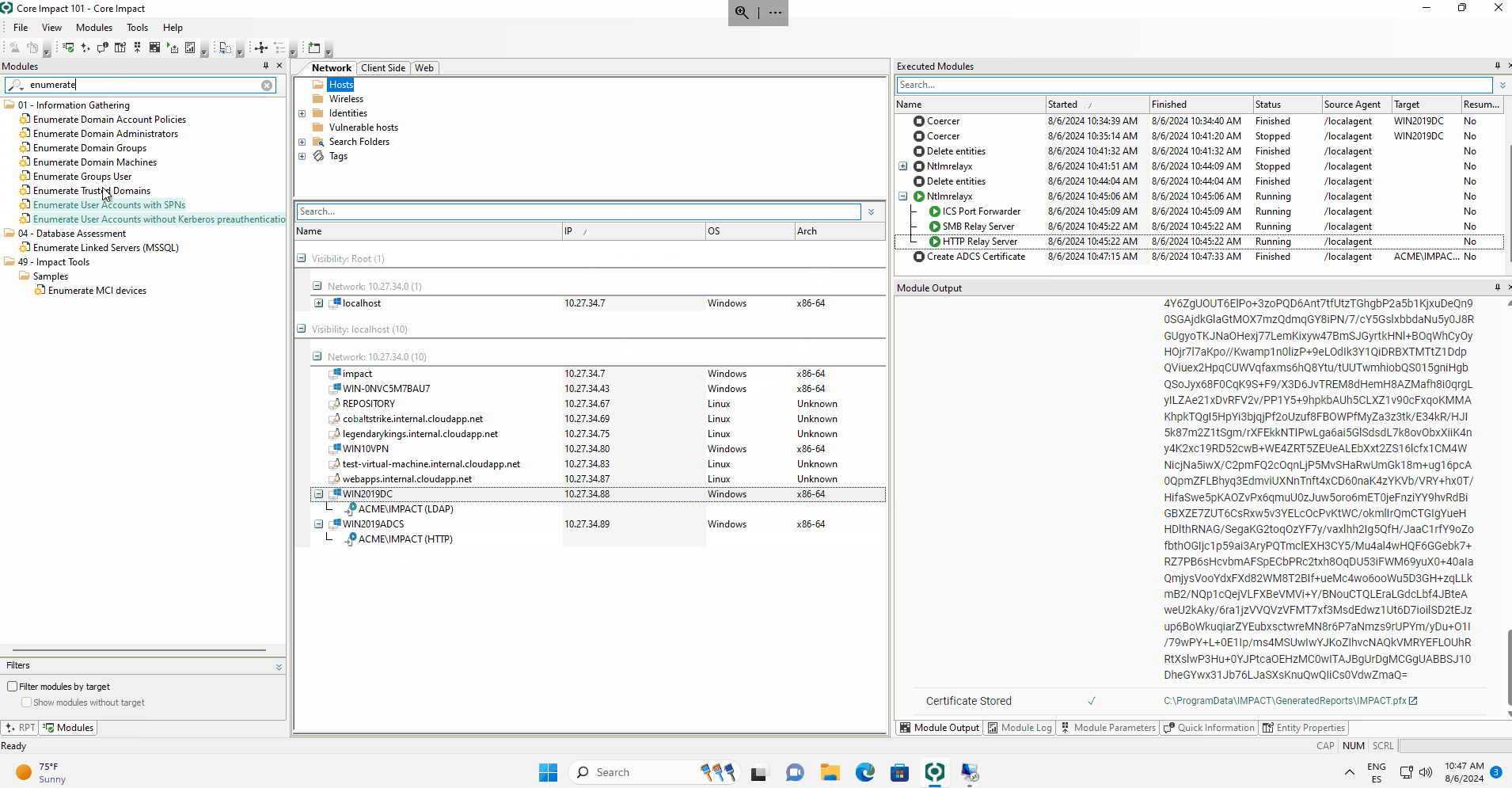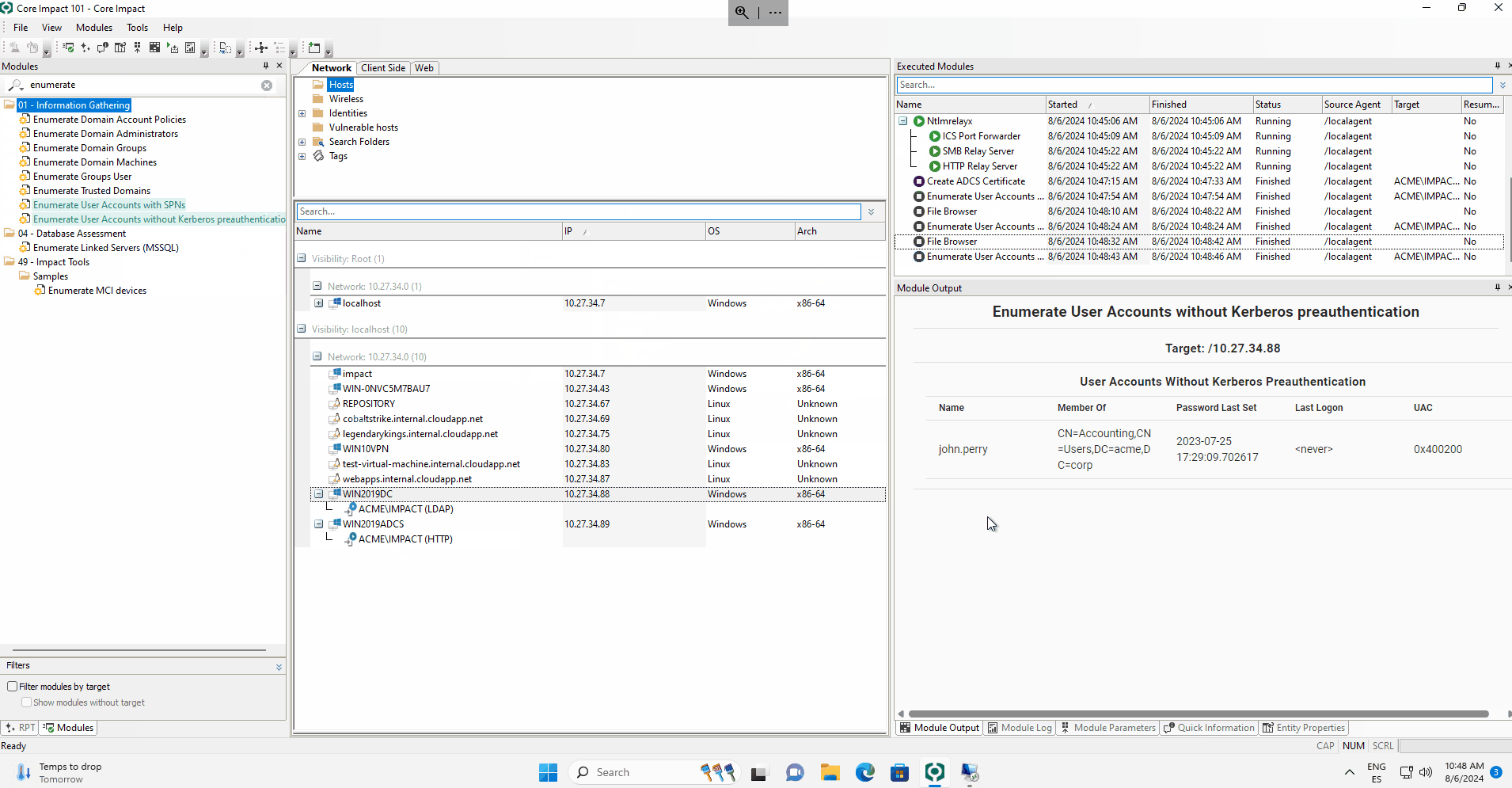
With this feature, the operator is given the control on when and how he would like to launch the selected module.
(Re)New(ed) Reports
We're excited to introduce the (re)ne(wed) reports in our latest product release. This enhancement comes with a completely revamped look and feel, designed to be more user-friendly and intuitive. With clearer visualizations, and streamlined data presentation, users can quickly grasp insights and make informed decisions.
The improved layout prioritizes readability and accessibility, reducing the time it takes to find critical information.
With our (re)new(ed) reports, complex data is transformed into comprehensible and actionable intelligence, enhancing the overall user experience.

New UI for Entities Information
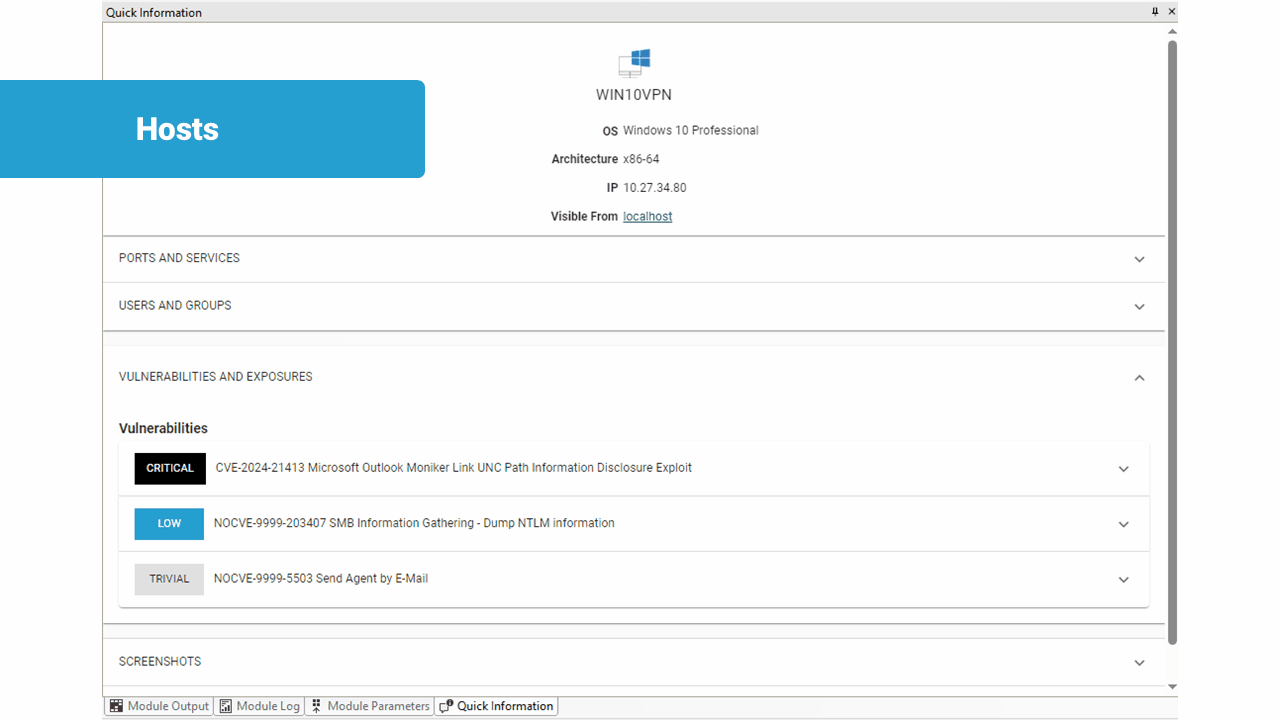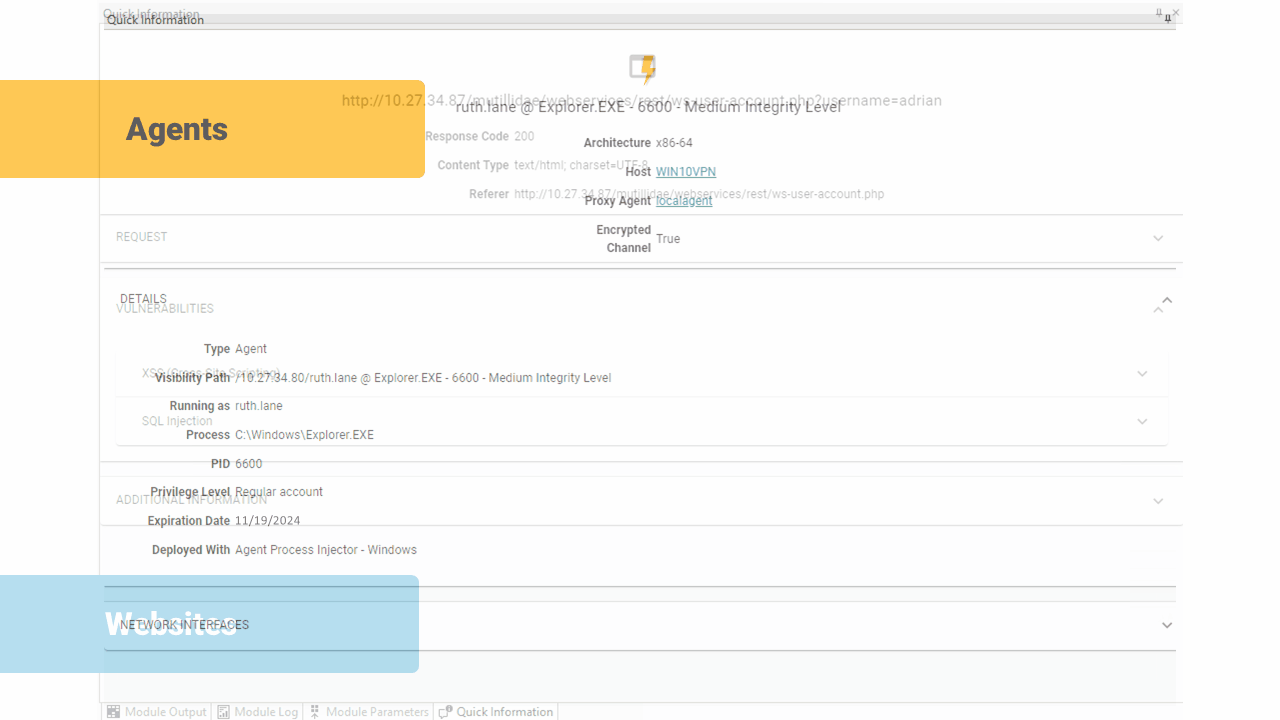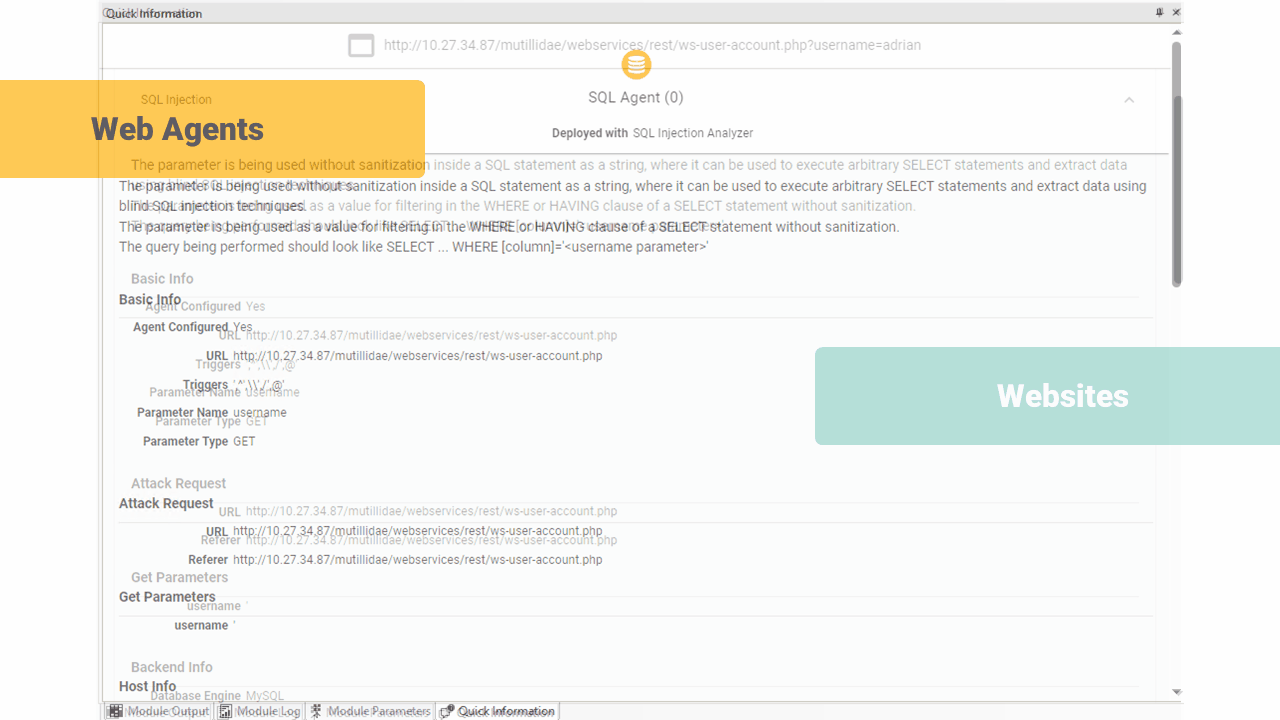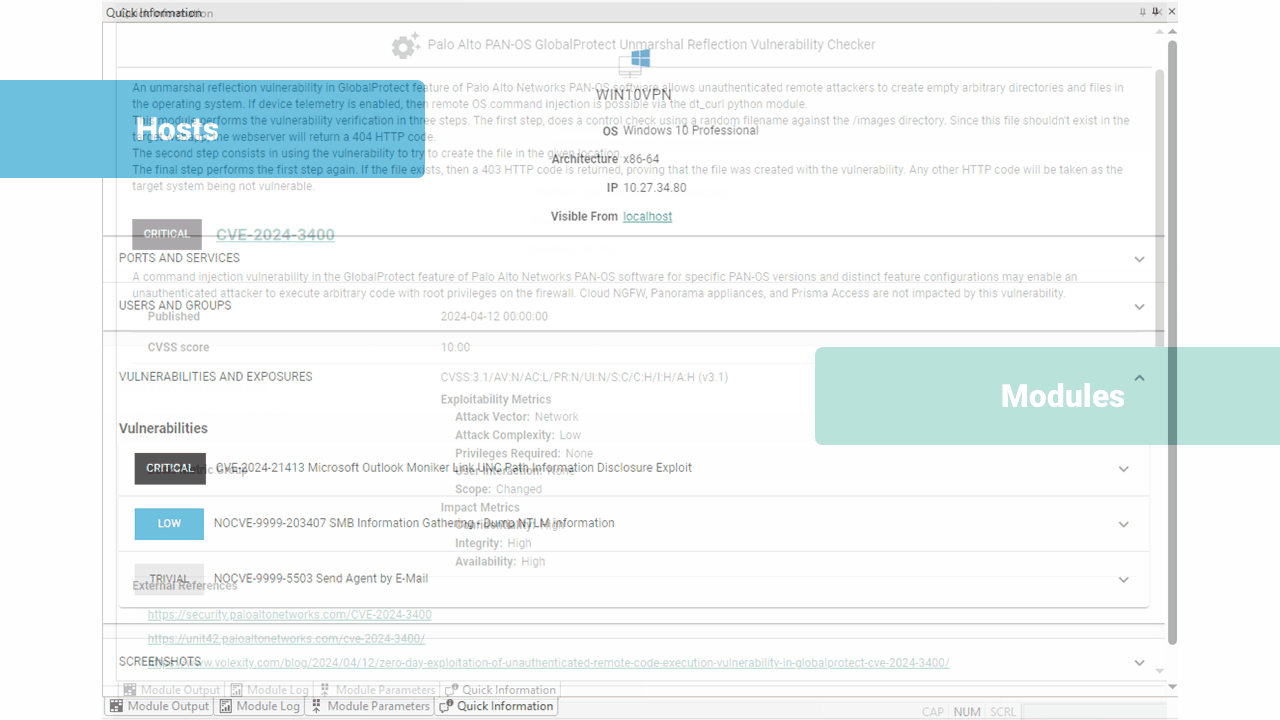
This release also brings significant enhancements to the entities Quick Information view, delivering specific visualizations for Host Information, Identities, Vulnerabilities, Exploits, and more.
This revamped interface offers a cleaner, more intuitive design, making it easier for users to navigate and interpret critical data. Each entity type now has dedicated visual representations, allowing users to quickly identify and analyze relevant information.
These tailored visualizations not only improve clarity but also enable faster navigation. The enhanced Quick Information view empowers users with the insights they need to advance through their penetration tests.
Quality of Life Updates
In addition, this release includes other updates and quality-of-life-changes:
- Fortra VM Integration: With the launch of Fortra VM, a Core Impact enhancement has been released to be able to import the results of scans and validate the reported vulnerabilities.
- Tenable Vulnerability Management Integration: This version allows to import the results of a scan run within Tenable Vulnerability management or Tenable.io into Core Impact to validate the reported vulnerabilities.
- Improved Module Output: The usability of exploits module output has been improved with the addition of a summary table with detailed information on each step done during the module execution.
- Improve Phishing attacks efficiency removing possible IOCs: The links generated for phishing attacks and client-side exploits have had IOCs removed. Additionally, running simulations has been simplified and reduces the risk of being blocked by email platforms.
- Active Directory Reconnaissance Improvements.
- Web Apps Fuzzer: This new module is focused on discovering hidden directories and pages automatically, aiding penetration testers in finding potential security weaknesses or sensitive information within a web application.
To see a full list of what’s new in Core Impact 21.6, please check out the release notes.
Training
Alongside the release of this new version, we've launched the exclusive Core Impact 101 course, available only to licensed customers. This course emphasizes practical, hands-on learning through real-world examples and exercises, designed to elevate the quality and effectiveness of penetration testing engagements conducted using Core Impact. It aims to equip users with the skills and knowledge necessary to fully leverage the platform’s capabilities.
To purchase Core Impact or learn more, please contact us.


