Some time ago, Core Impact added a module that supports the use BloodHound, a data analysis tool that uncovers hidden relationships within an Active Directory (AD) environment. This module enabled the collection of Active Directory information through the Agent using SharpHound. Additional modules have now been added to allow Core Impact users to further utilize Bloodhound. In this blog, we’ll dive into how Core Impact users can put these new modules into action during their engagements.
Reconnaissance of Active Directory
When performing a penetration test, operators will often evaluate the Active Directory looking for misconfigurations that could allow finding credentials to escalate privileges or move laterally.
While Core Impact provides (thanks to its own modules and the embedded usage of Impacket) a clear and easy workflow to compromise Active Directory, it is very common for penetration testers to also leverage the power of Bloodhound to identify attack paths, the shortest paths to high value targets, or other misconfigurations.
With the initial module, it was possible to import data into Bloodhound, look for attack paths there, and then try to follow them within Core Impact.
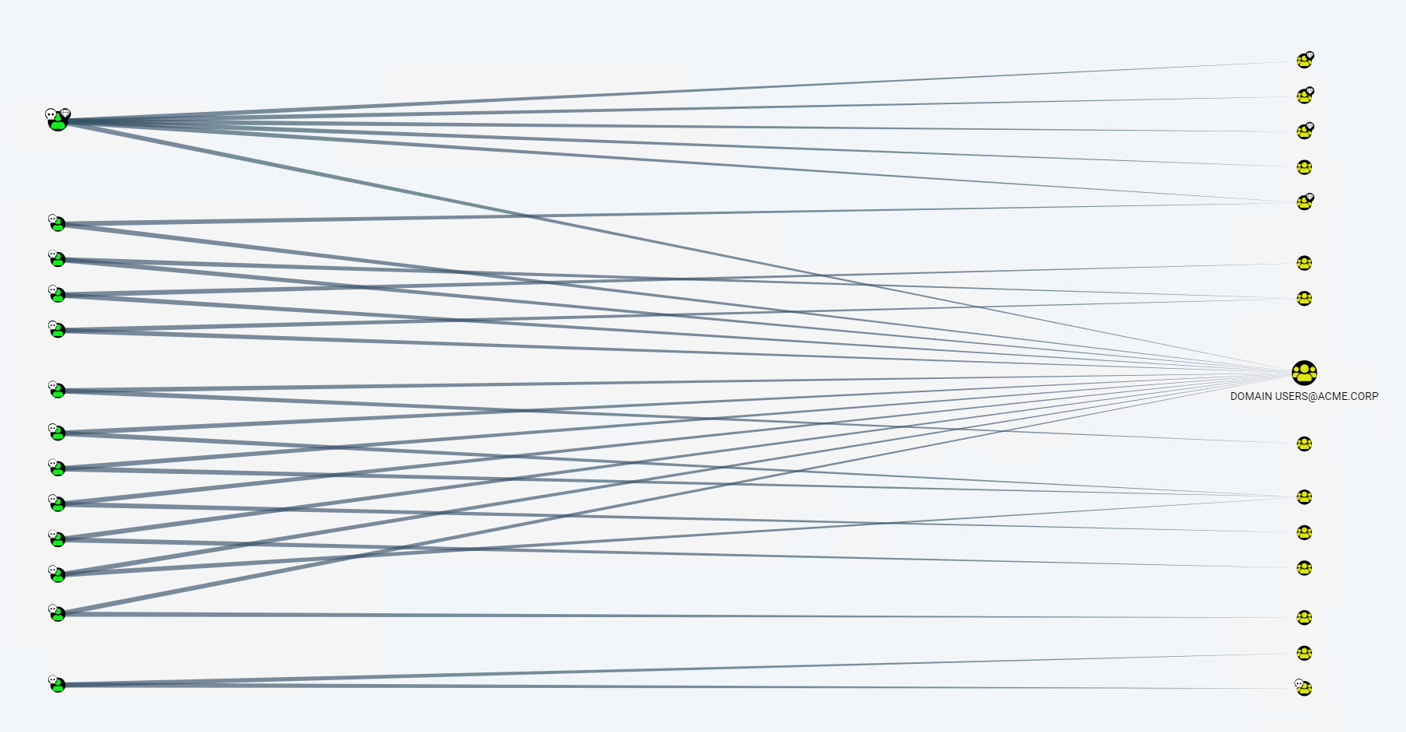
New BloodHound Modules
With this new update, Core Impact and Bloodhound are even more compatible, bringing together the best of both worlds.
The first new module imports BloodHound users into Core Impact as Identities. The second module focused on synchronizing Core Impact and Bloodhound data from Active Directory information gathering tasks.
This second module, which is the most feature rich, can perform the following actions:
- Validate existence of Core Impact stored identities in the BloodHound database
- For existing users:
- Mark them as Owned in BloodHound if they are validated in Impact
- If the password is in plain text, the attribute “plaintextpassword” is set with the password value, following the same standard as in the TrustedSec CrackHound Tool.
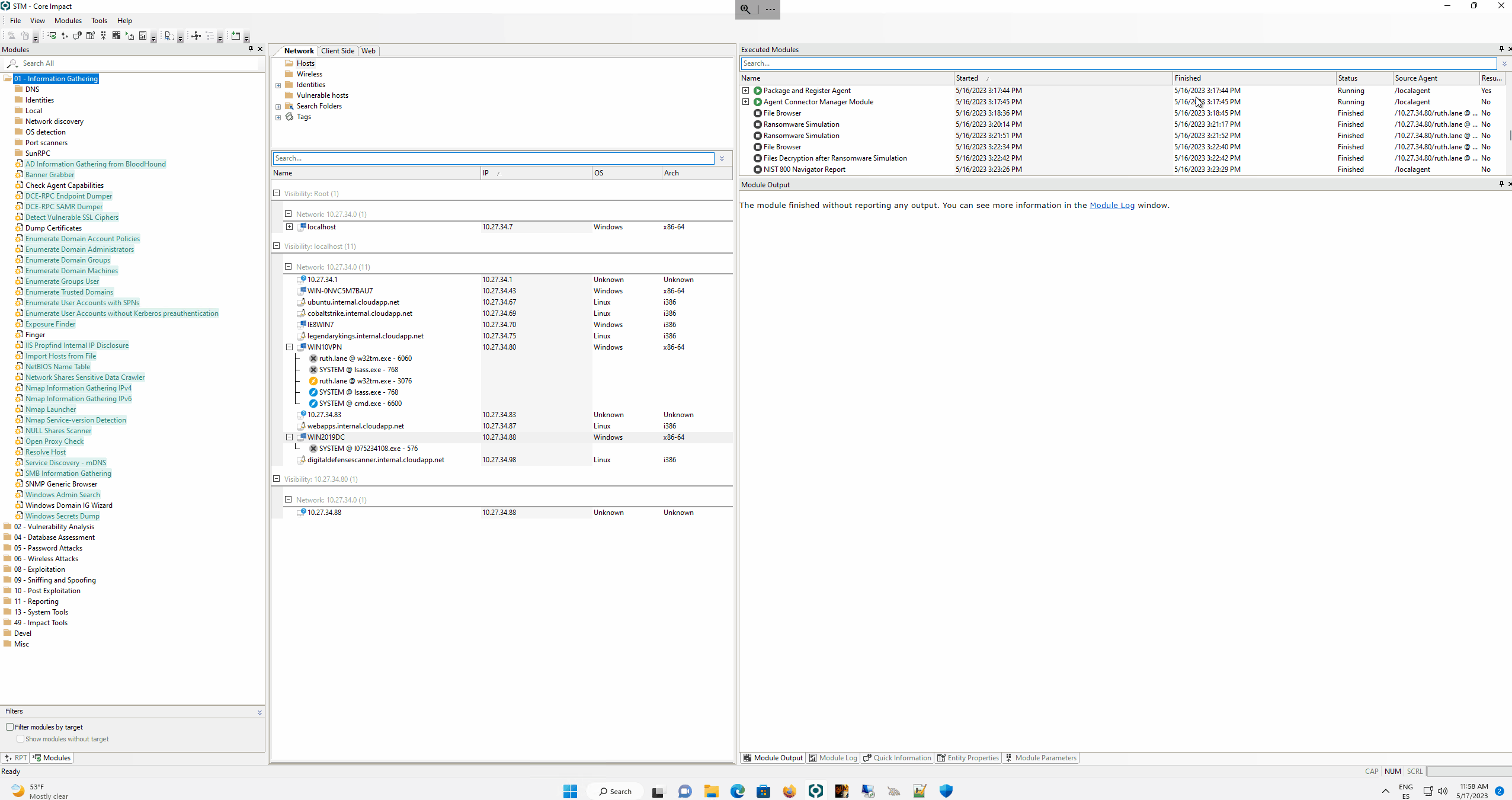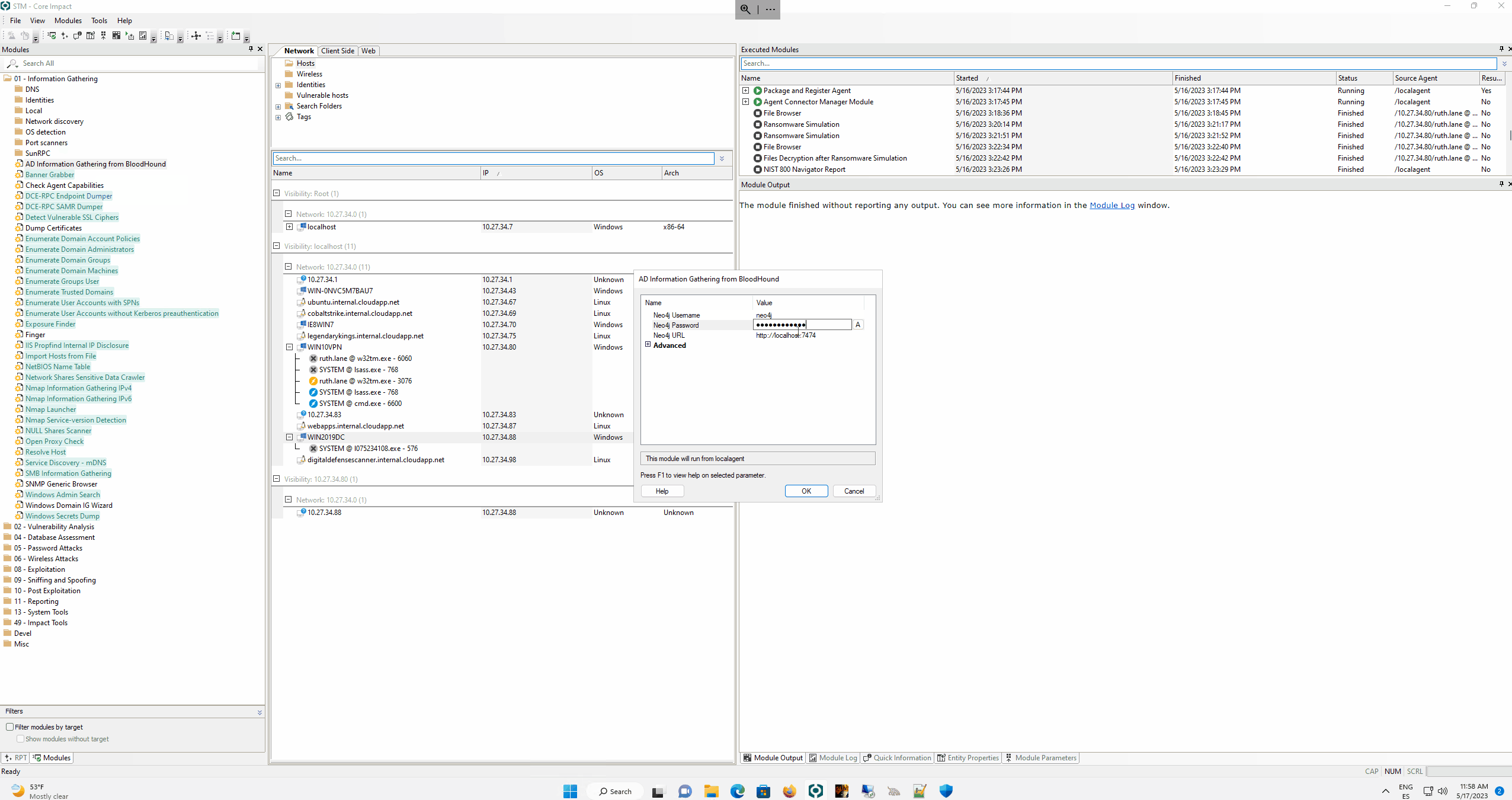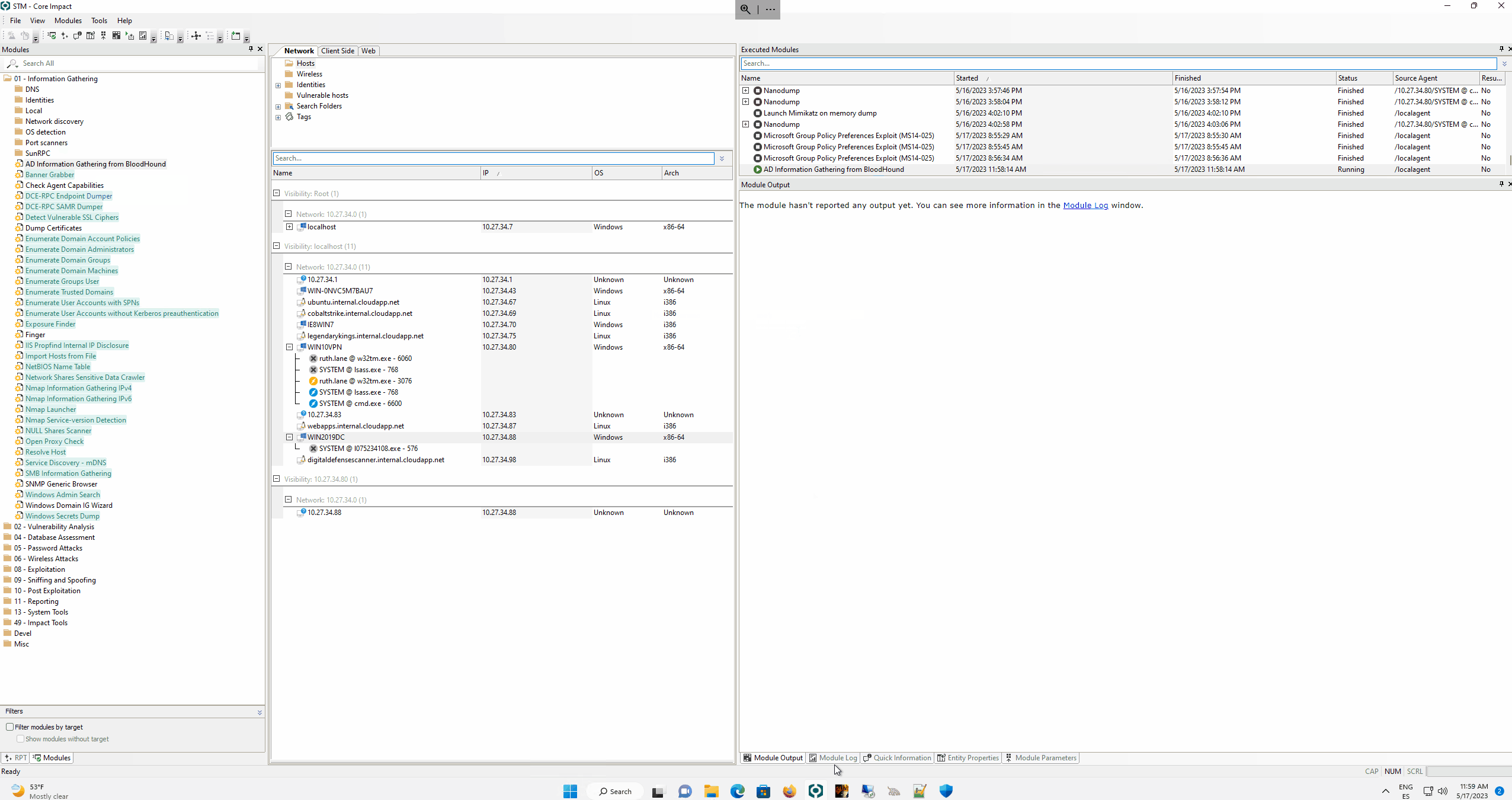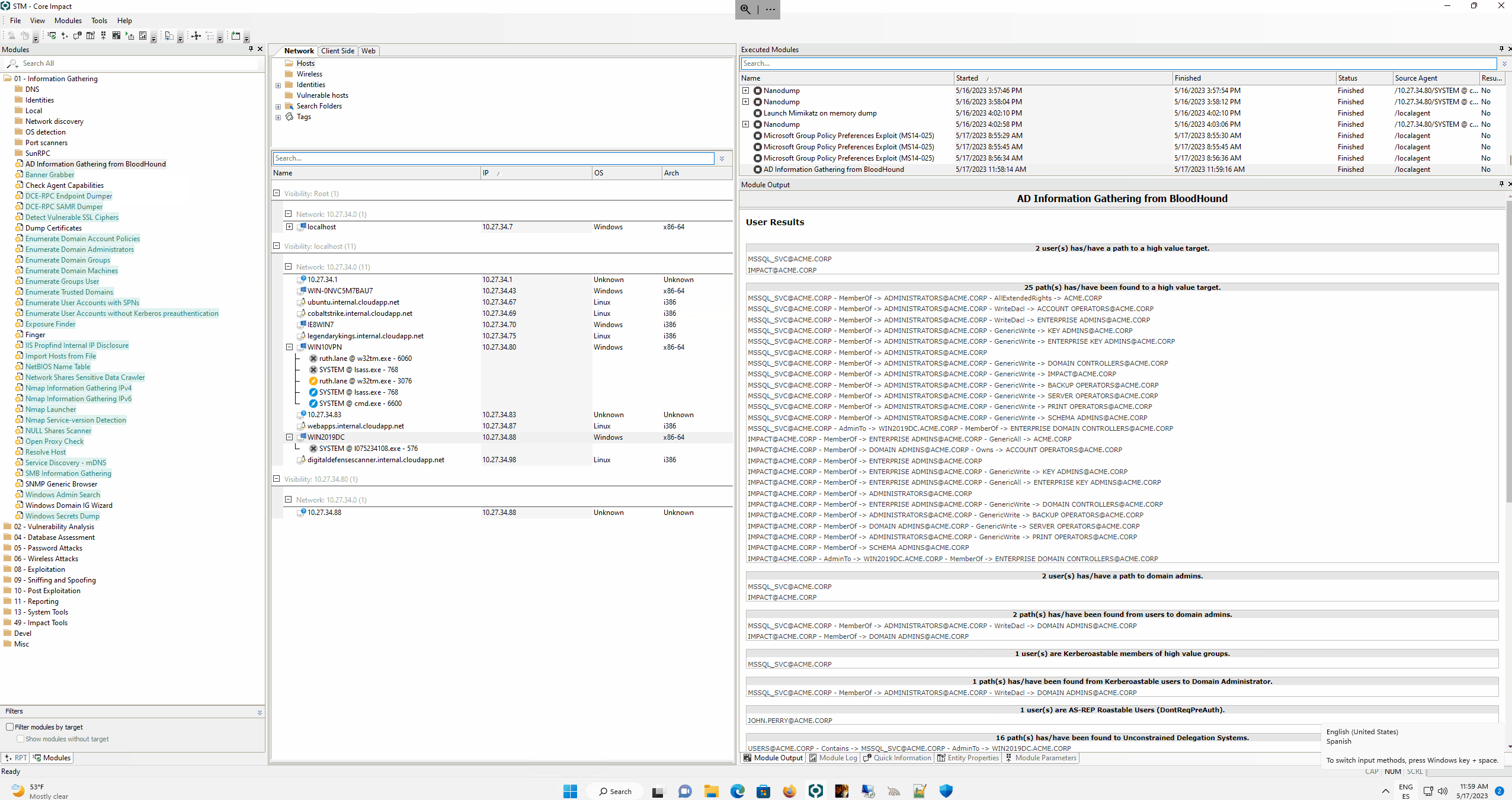
- Execute queries through the Neo4j API to retrieve:
- Users with paths to high value targets
- Shortest paths to high value targets
- Users with paths to Domain Admin
- Paths to Domain Admin High value Kerberoastable users
- Path to Domain Admin from Kerberoastable users
- AS-REP Roastable users
- Paths to Unconstrained Delegation Systems
- Computers with paths to high value targets
- Mark the users associated to the deployed agents as Owned in BloodHound
- Mark the computers with privileged deployed agents as Owned in BloodHound
- Display the report in the module output:
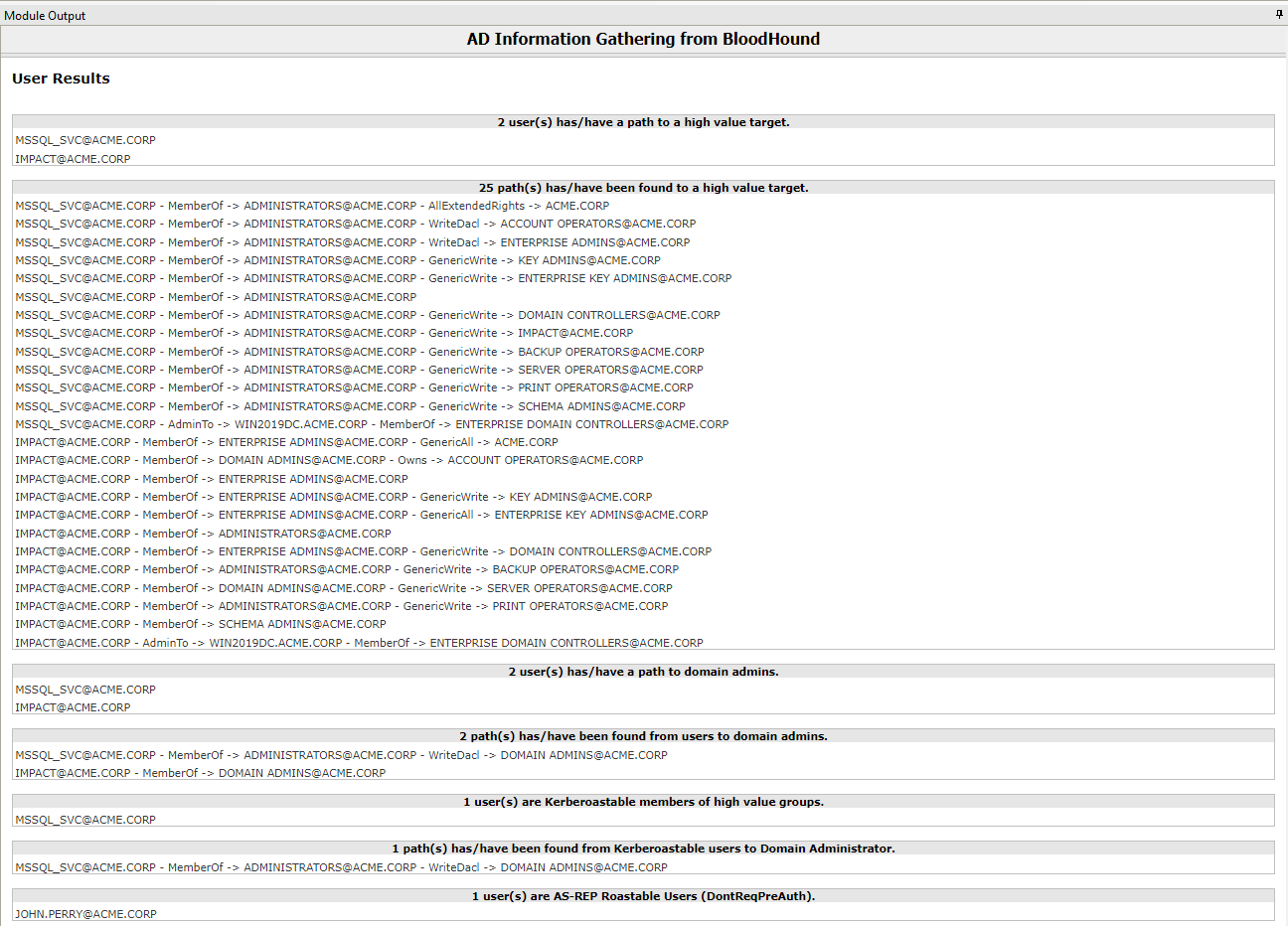
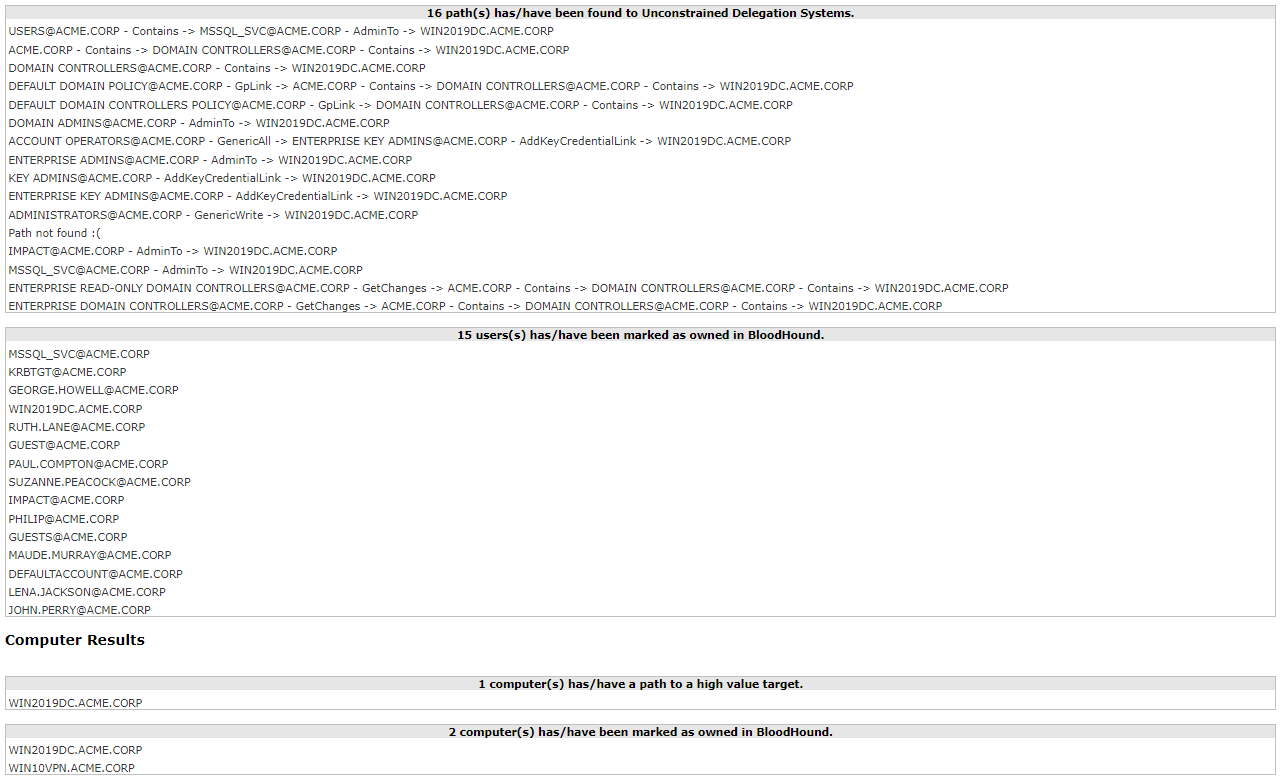
All this information retrieved allows the operator decide what the next most valuable steps are to continue with the Active Directory attack.
Below you can enjoy a short demo of this new module in action:
Centralizing Security with Core Impact
Solutions that work with one another can help to maximize resources, reduce console fatigue, and standardize reporting. With increased interoperability with tools like Bloodhound, Core Impact can help serve as a point of centralization, helping organizations to advance their infrastructure protection programs without overcomplicating strategies.
References
This module takes inspiration from the following modules:
- pyCobaltHound by NVISOsecurity
- Max by knavesec
- CrackHound from TrustedSec
- BloodHound by SpecterOps
Want to see more Core Impact features in action?
Check out the on-demand demo of this powerful pen testing tool.



