So why are we talking about hacking of an IBM i? I think that's certainly not a headline we see very often, as IBM i systems have been considered un-hackable for years. Anyone who has worked on IBM i has heard some of these statements:
-
“Nobody Can Hack an IBM i.”
-
“Never in my 40 years in the business has anyone hacked an IBM i!”
-
“IBM i’s don’t have hacking problems like Windows computers.”
-
“IBM i’s are bullet-proof. They don’t have zero-days like other computers.”
Unfortunately, common misconfigurations on any platform may lead to a system compromise. In the end, all systems are programmed and configured by humans. The issues that we're going to talk about are not unique to the old white boxes that do not exist any longer. That technology is extinct, but it does apply even to the latest and greatest of systems, including version 7.X power systems server running IBM i.
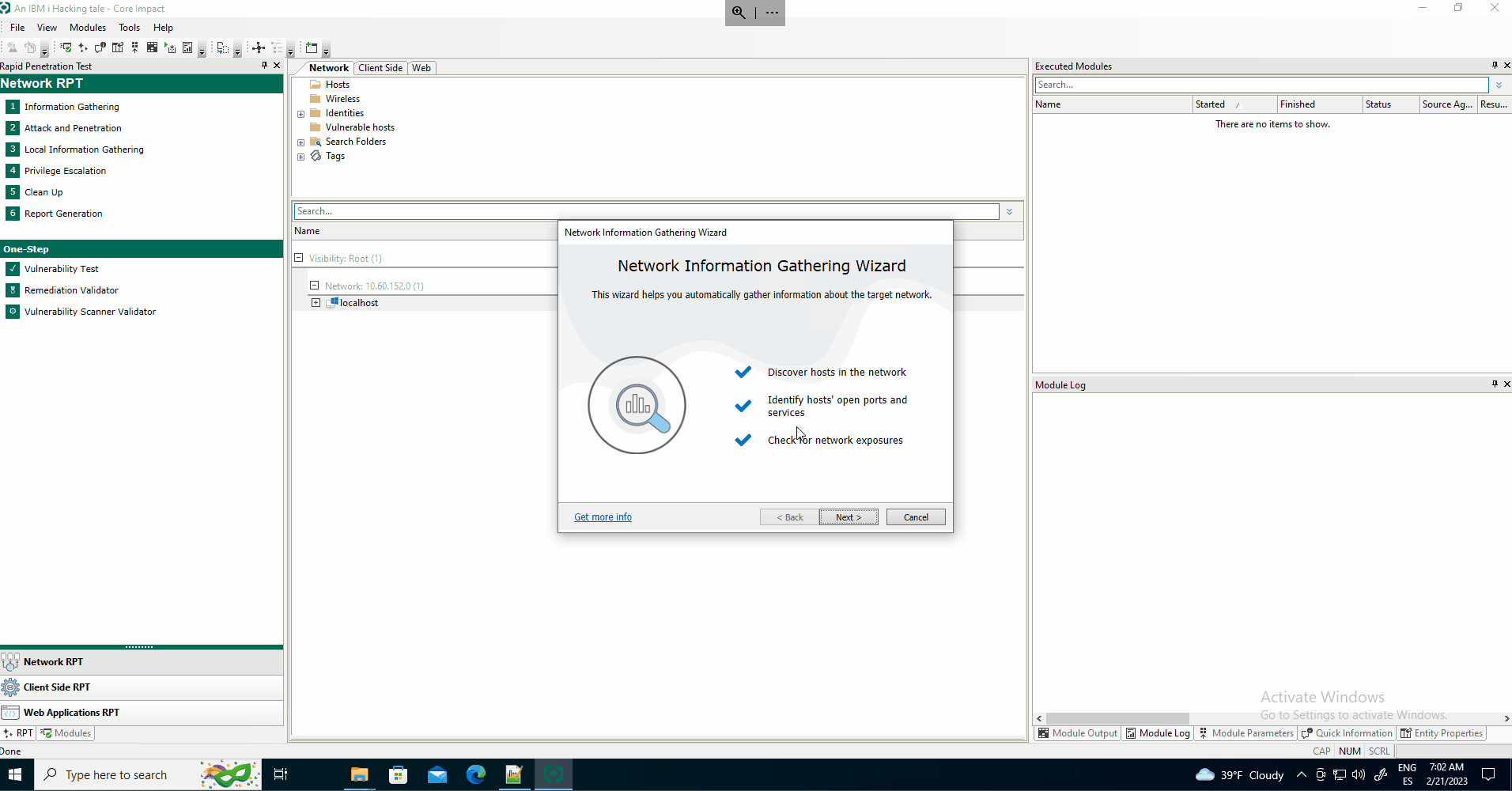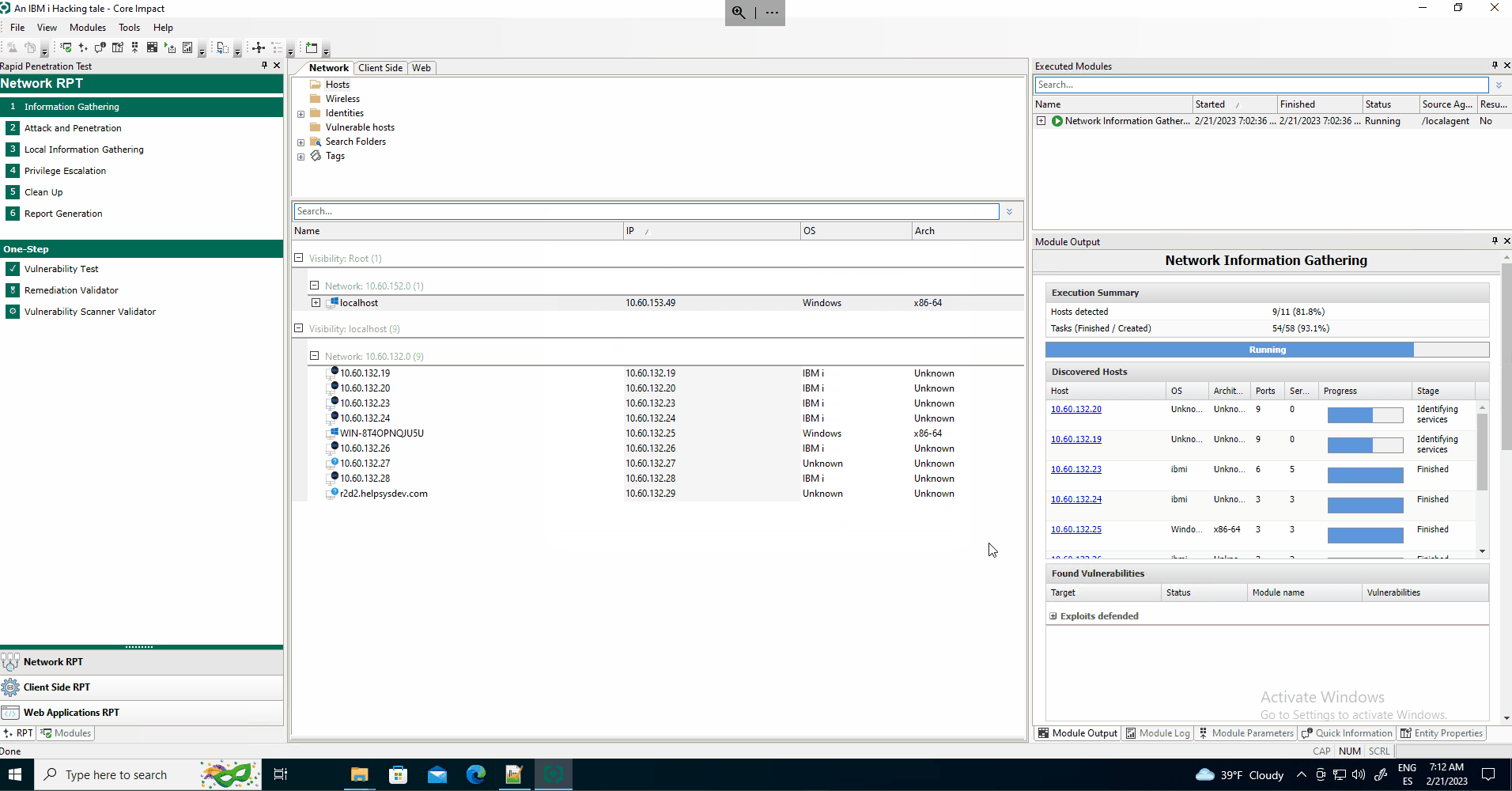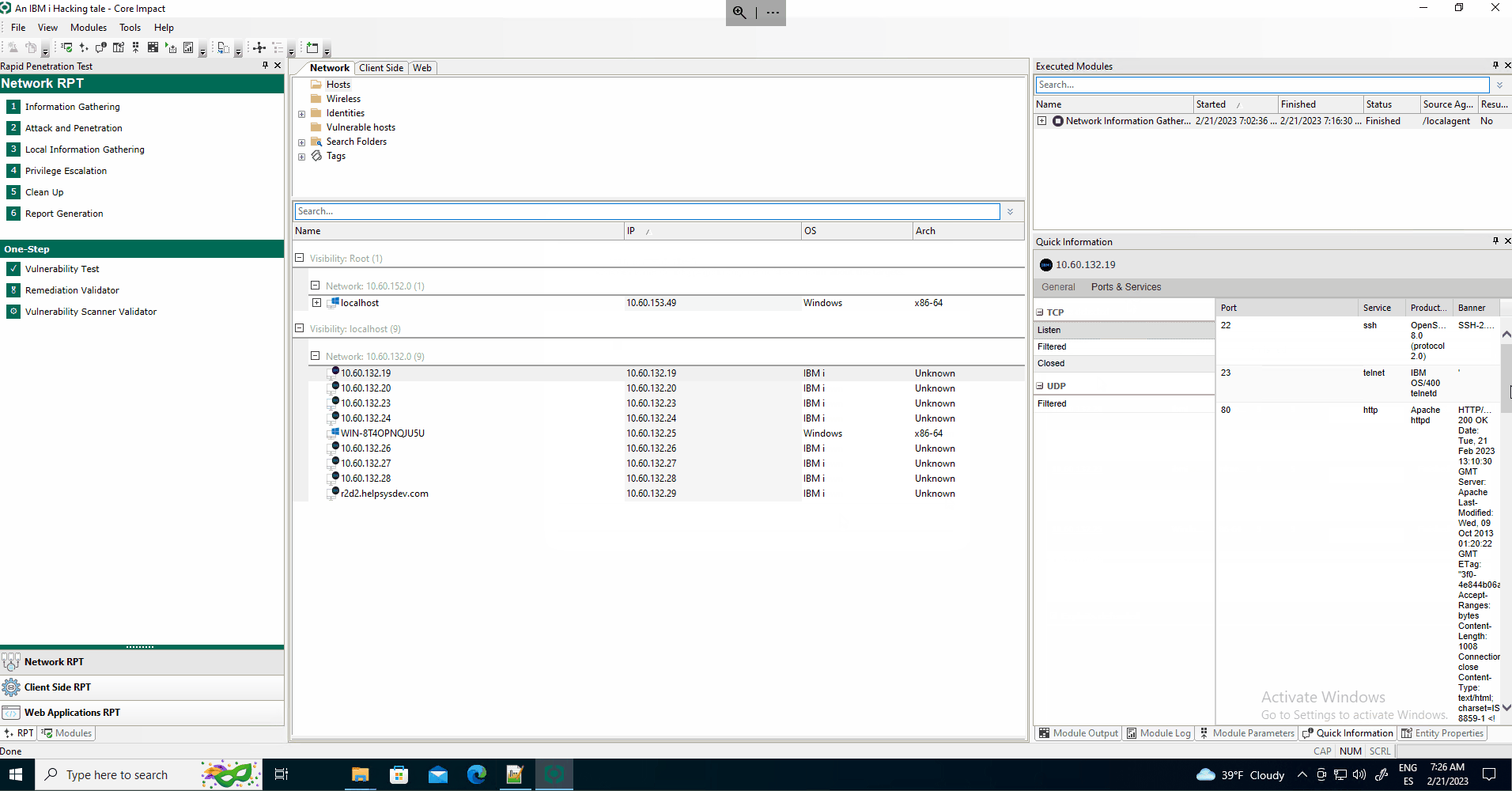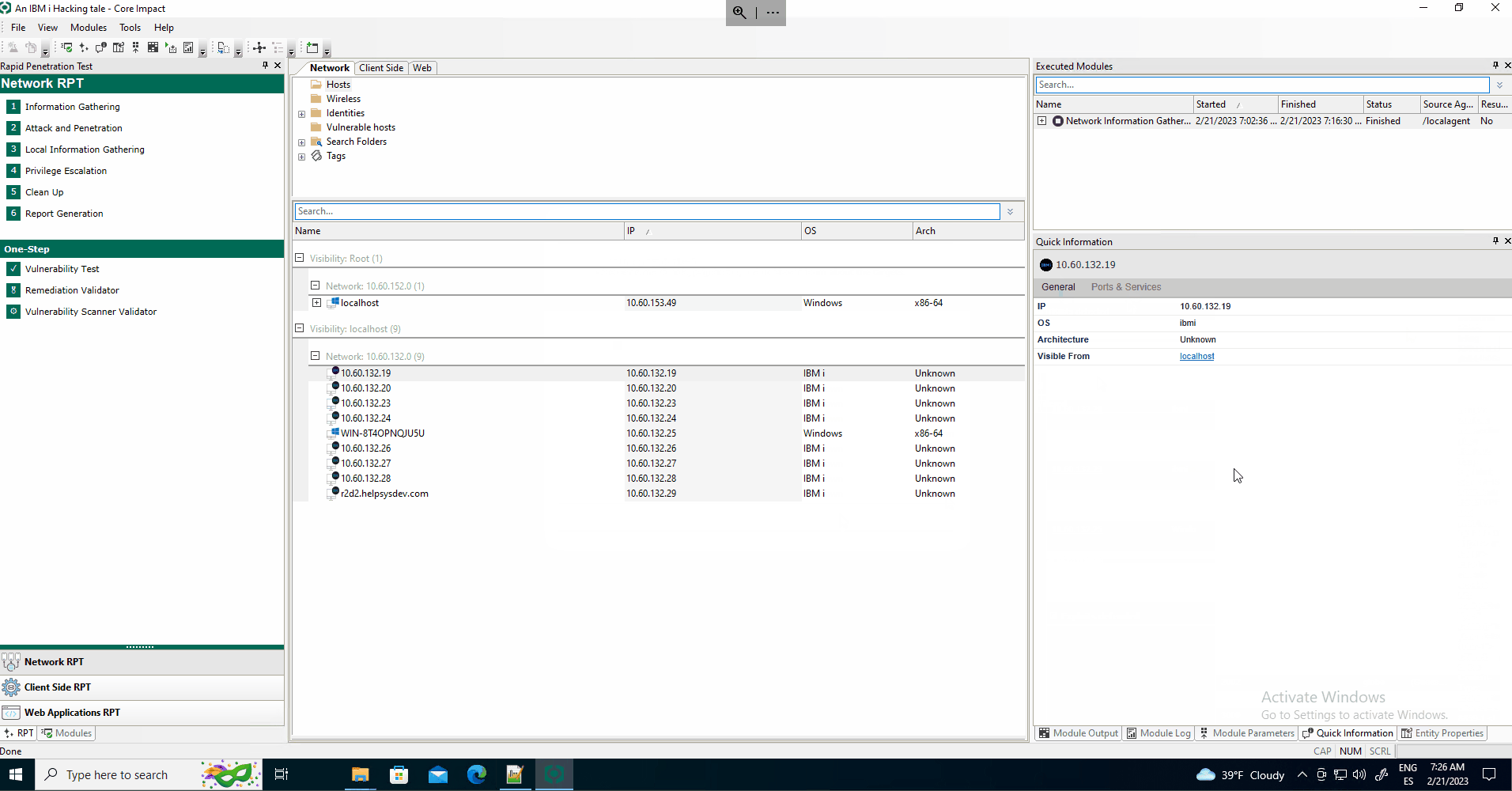
The only way to truly confirm system vulnerabilities is to try to exploit them. Security penetration testing, commonly known as ethical hacking, is a critical step organizations should take to ensure their data security.
Fortra’s Core Impact can perform Penetration Testing to figure out whether the risks identified pose a real threat to data. And now that penetration testing is available for IBM i.
There is a supplied automated walkthrough to perform an IBM i penetration test and security audit that helps ensure that it is done right and can provide an unbiased assessment of your security to help guide you towards remediation. Read on to learn about what it takes to complete a successful pen test on IBM i.
Attack and Penetrate
Now informed about their target, pen testers can begin using these newly discovered entry points, testing all the weaknesses they discovered. They will try to enter the target through these identified entry points.
The first attempt to penetrate the system would try to take advantage of misconfigurations (No password, easy to guess password or default password) in the System Default user accounts.
The Network Attack and Penetration module will launch and run the TN3270 Identity Verifier. This module spawns several child tasks to perform tests in parallel based on the configuration and rotating the tested usernames to try to prevent lockout.
After a while, the module might find a valid set of credentials on the target system and use them to deploy an OS Agent on the target.
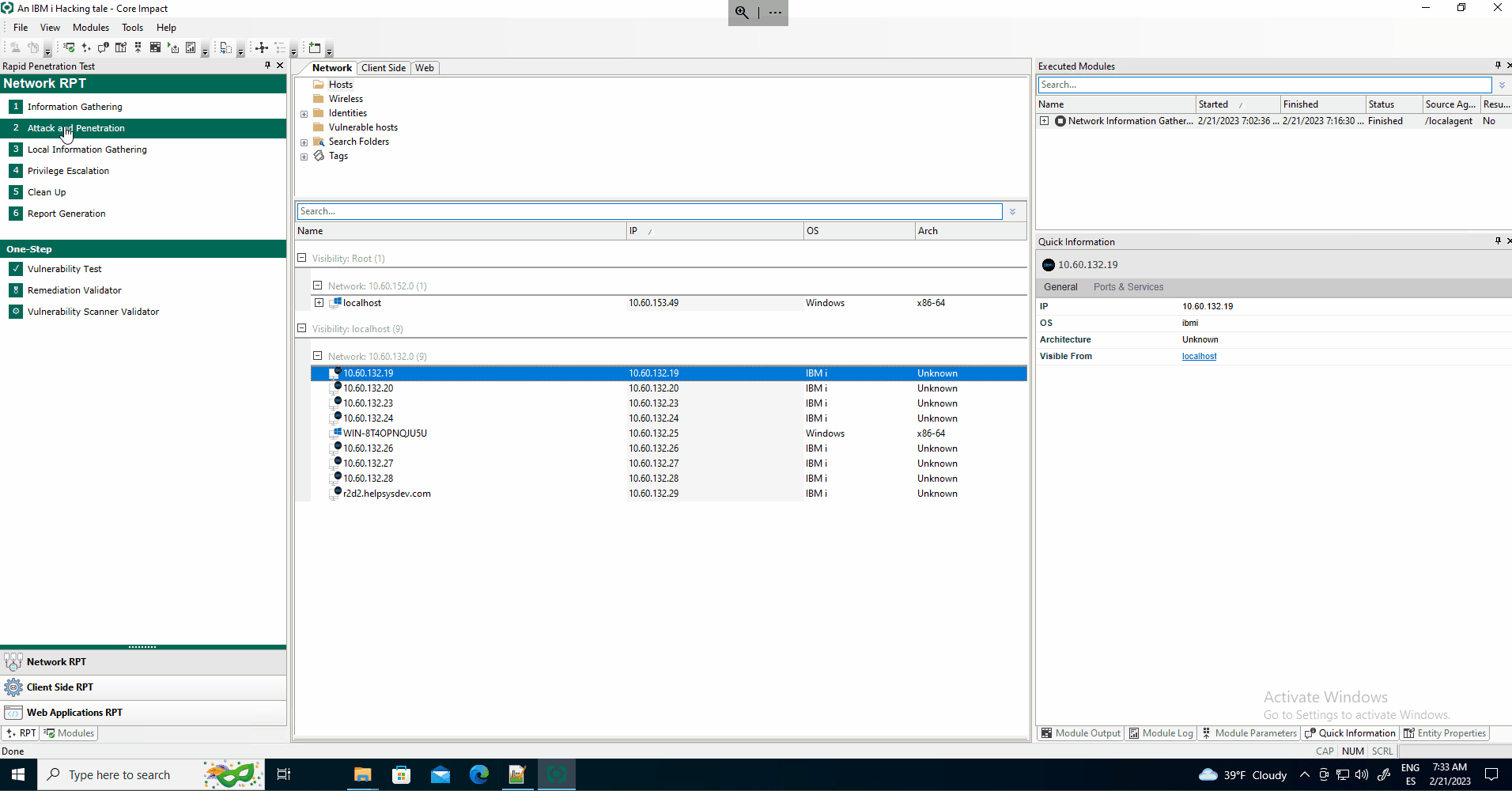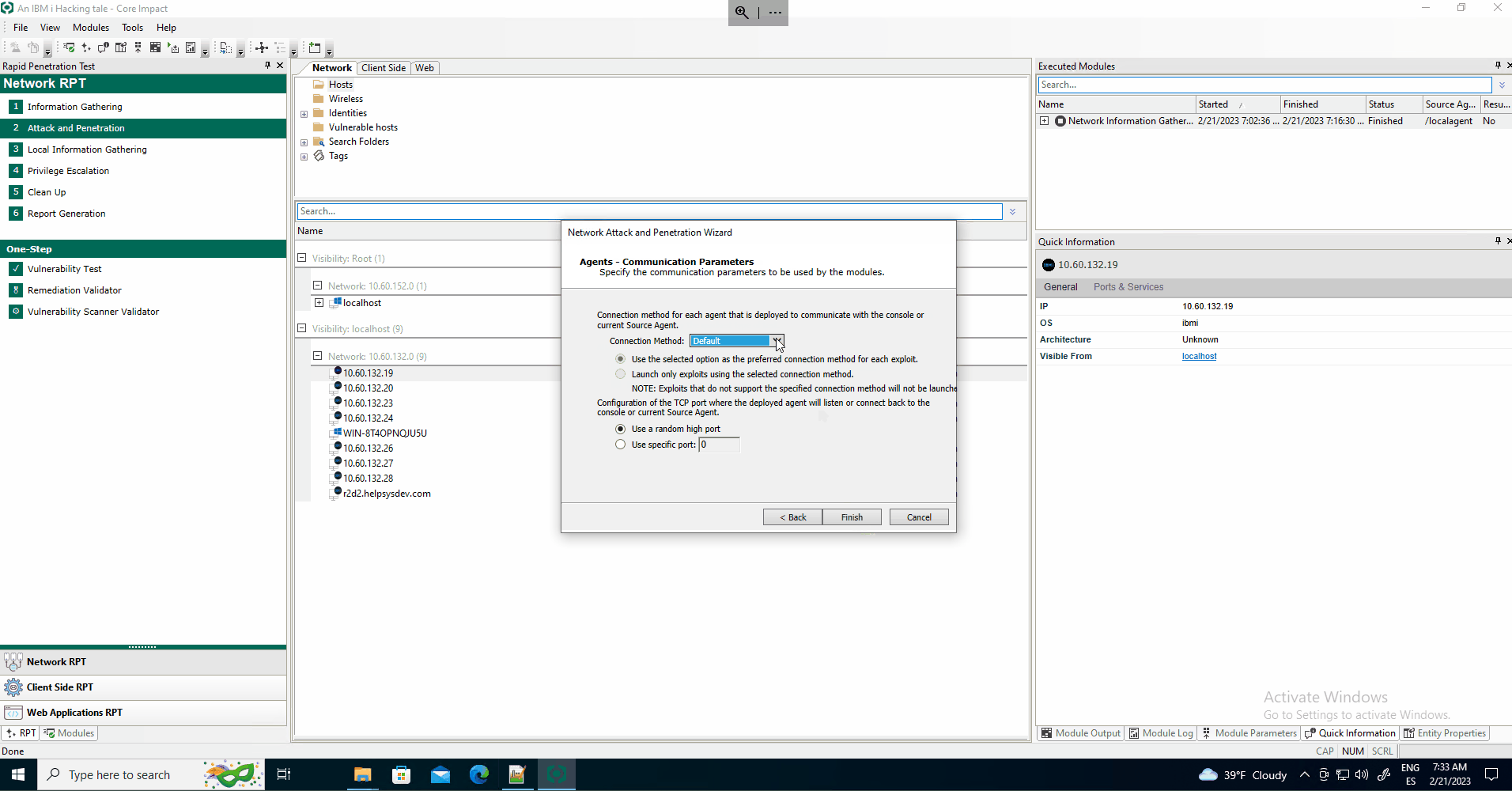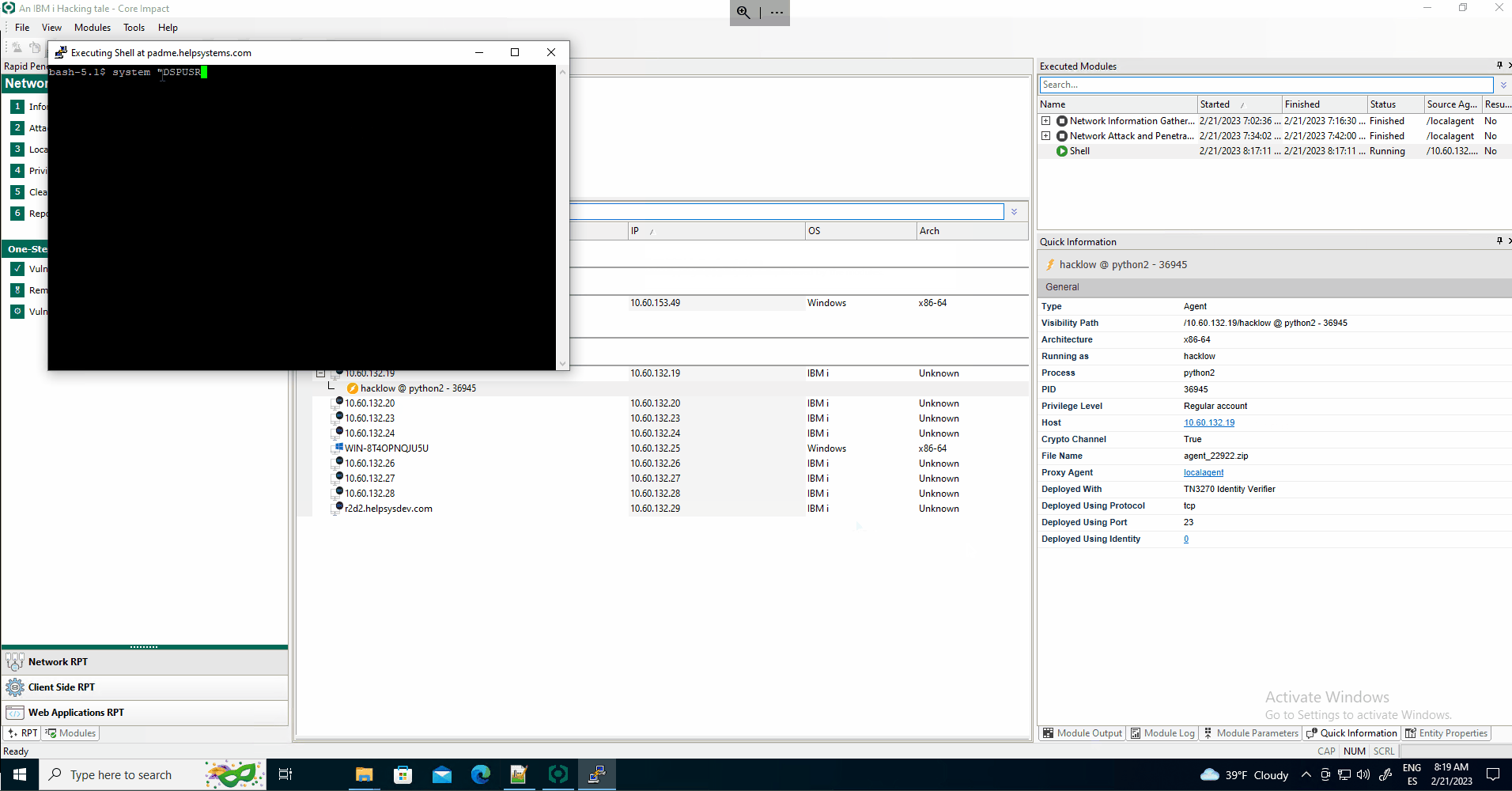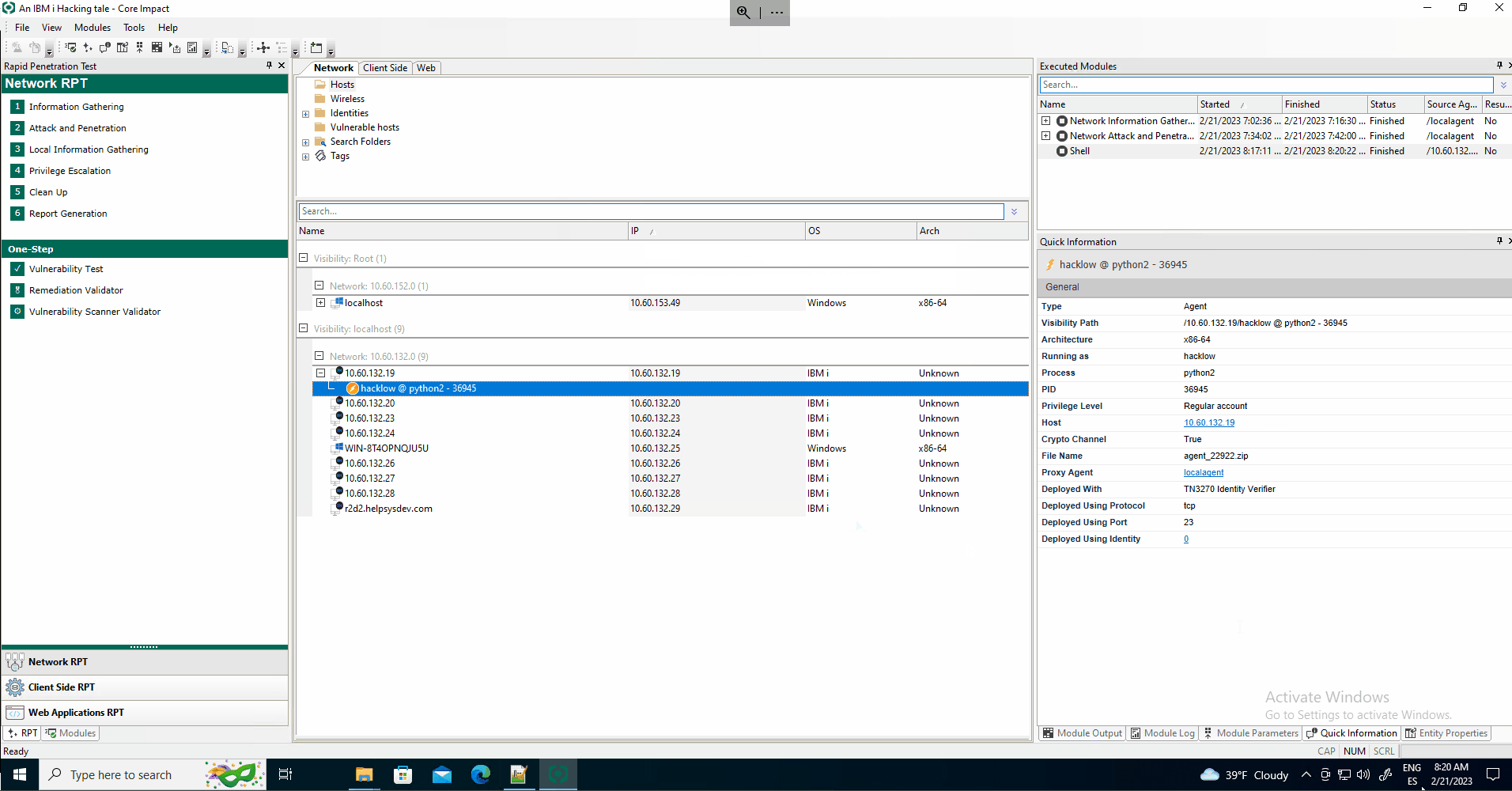
Local Information Gathering
Once inside the system, several local modules that perform information gathering can be launched through the Network Local Information Gathering RPT module.
The information specific to the IBM i systems that can be retrieved through the LIG modules is:
-
System Values assessment
-
Current Value
-
Recommended Value
-
Deviation from recommendation
-
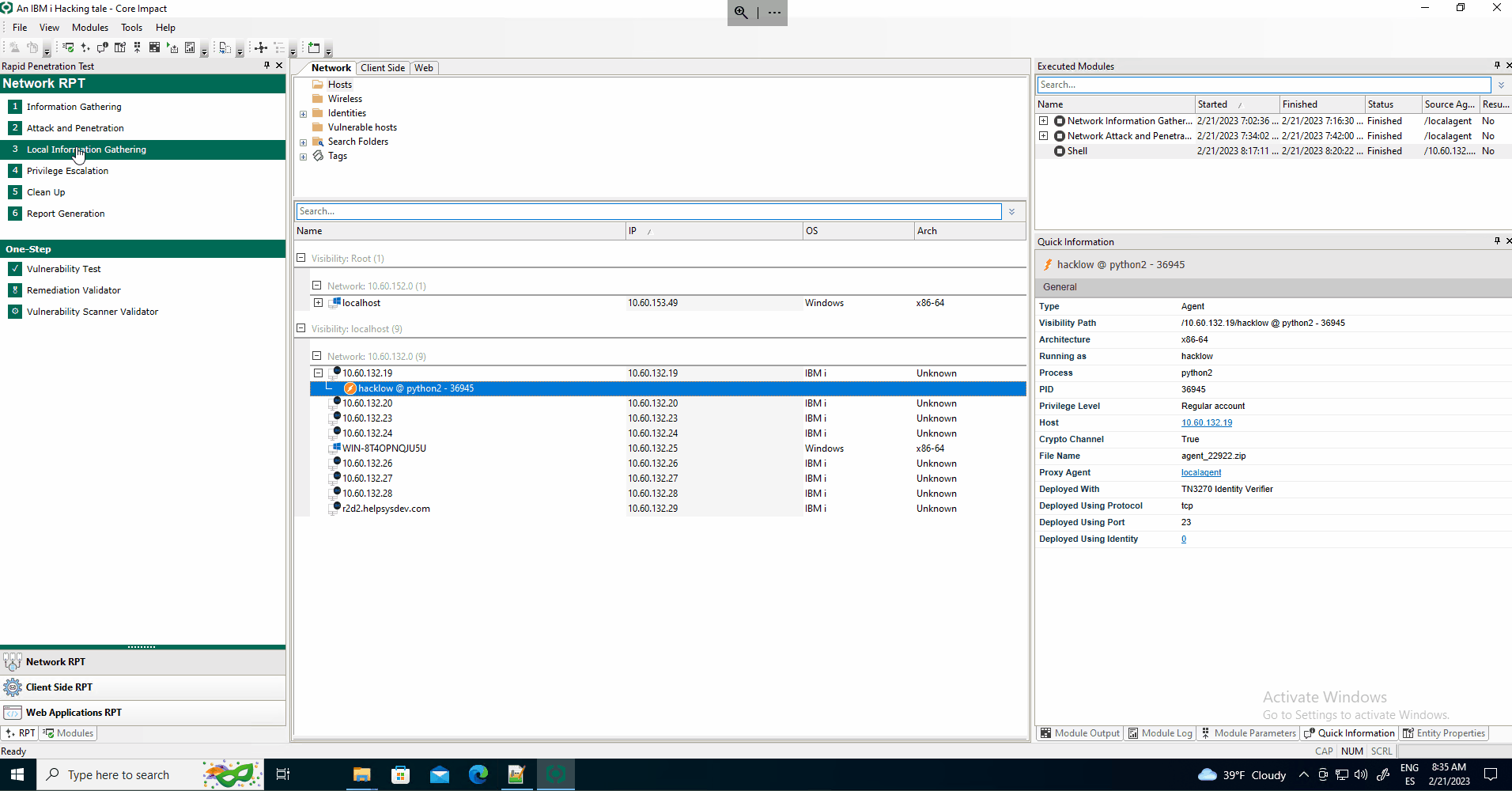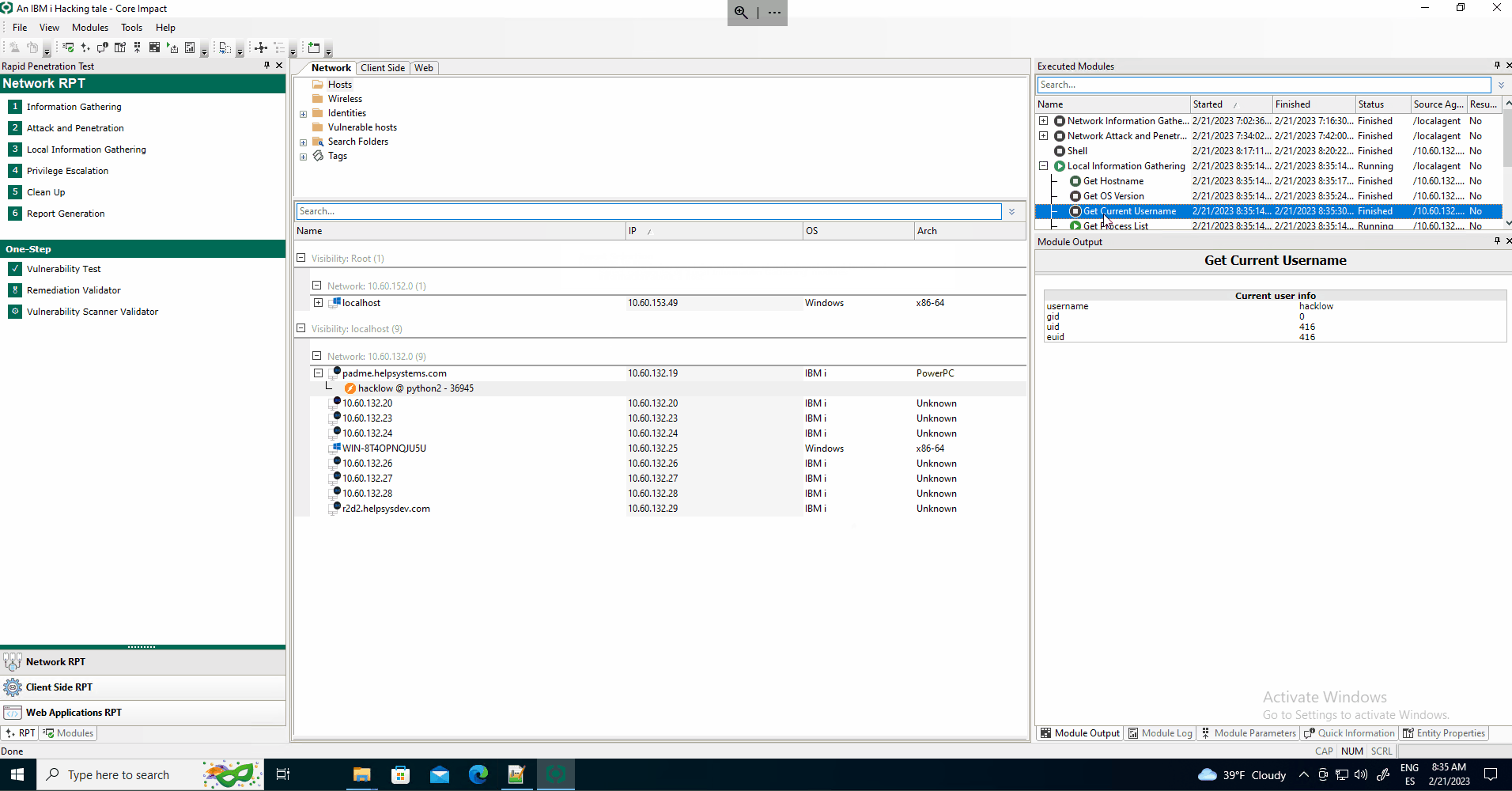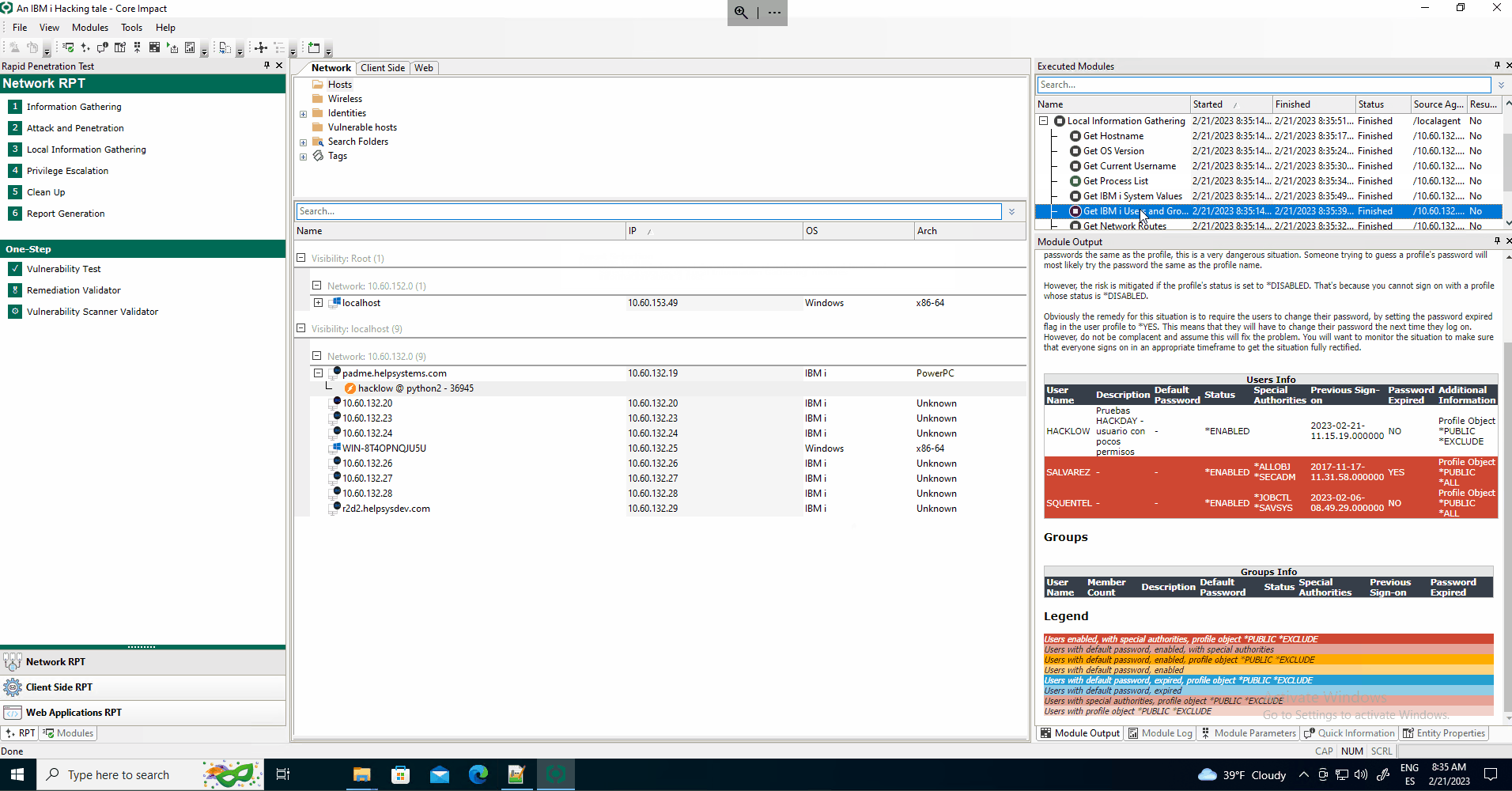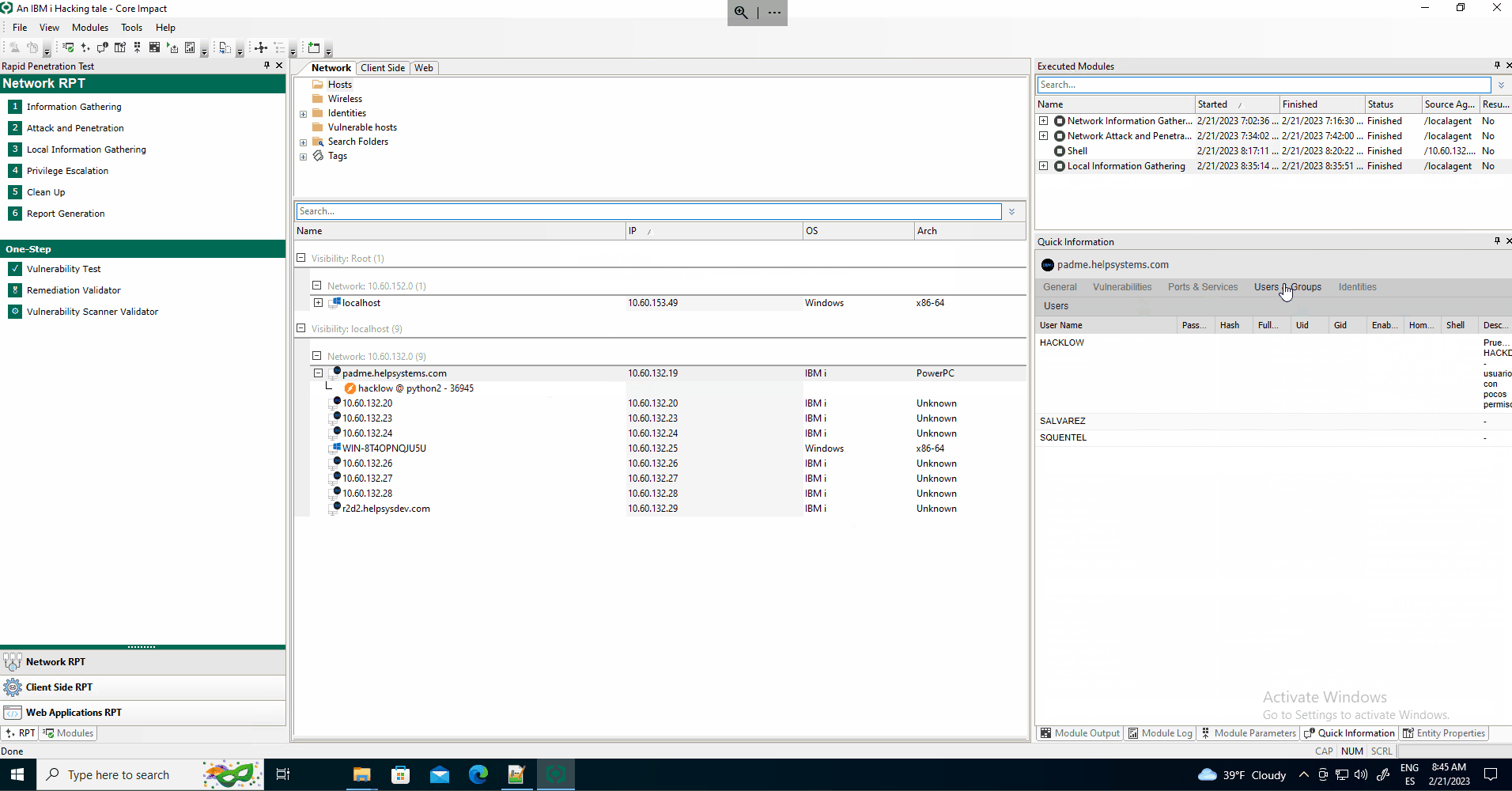
Users and Groups assessment
-
Checks the users with default password
-
Highlights users with special authorities, profile object *PUBLIC *EXCLUDE
-
Adds the users as identities that could be used further in the test
Privilege Escalation
Once inside a compromised system, they will try to elevate their access privileges within the environment, allowing them to take any number of additional actions. Gaining administrative privileges enables pen testers to identify security weaknesses in other areas and resources, like poor configuration, unguarded access to sensitive data, or ineffective management of accounts and passwords.
The OS Agent deployed through the selected identity, however, is that of a standard/limited user on the host. We can try and see whether we can elevate privileges on the system by exploiting an unpatched privilege escalation vulnerability.
The IBM i Privilege Escalation through Object Authority on User Profile module, launched automatically through the RPT, will try to elevate the privilege targeting users with special authorities having user profile authority *PUBLIC and *USE or *ALL.
If the privilege escalation process is successful, the user the agent is running with becomes privileged.
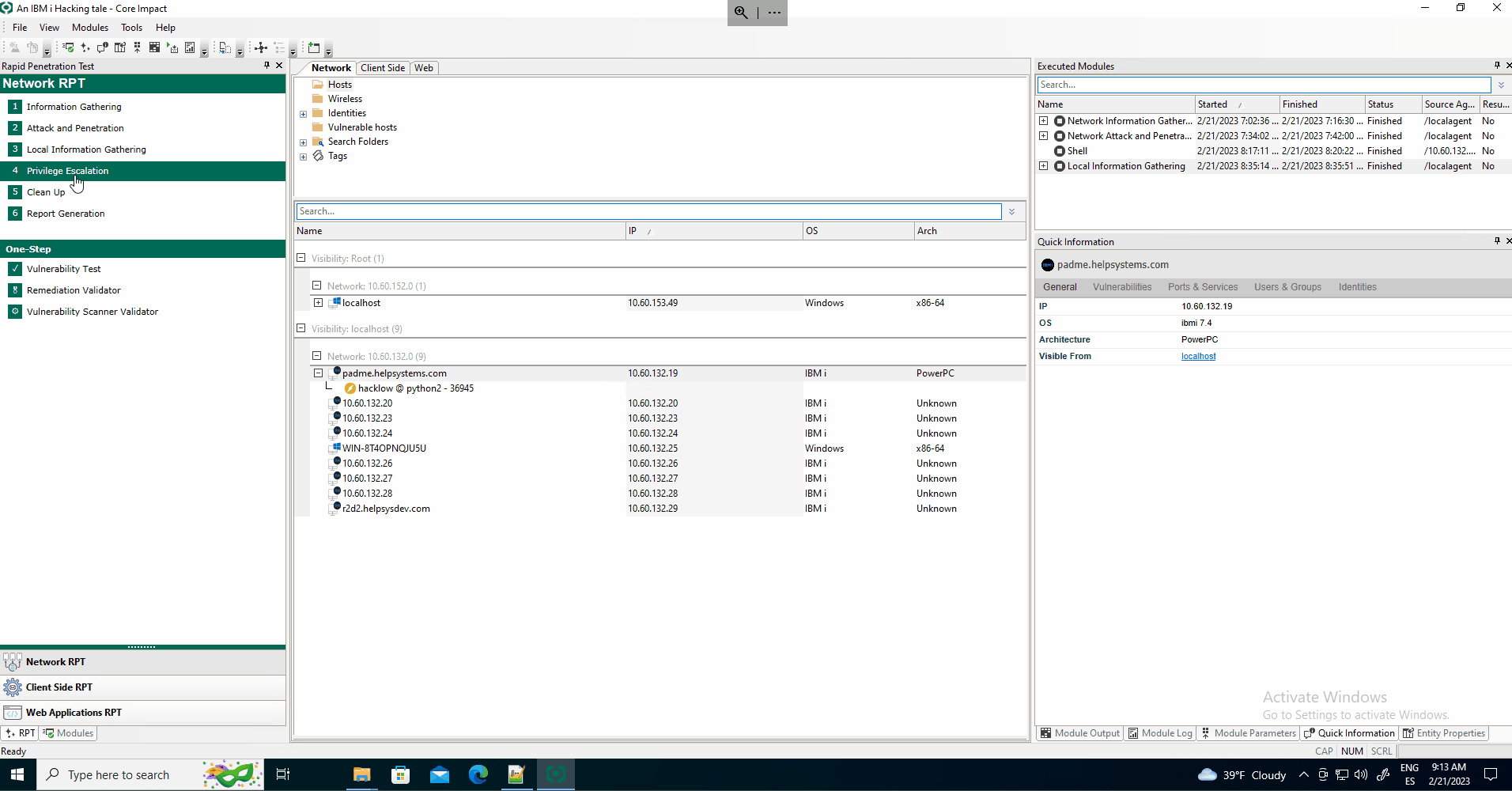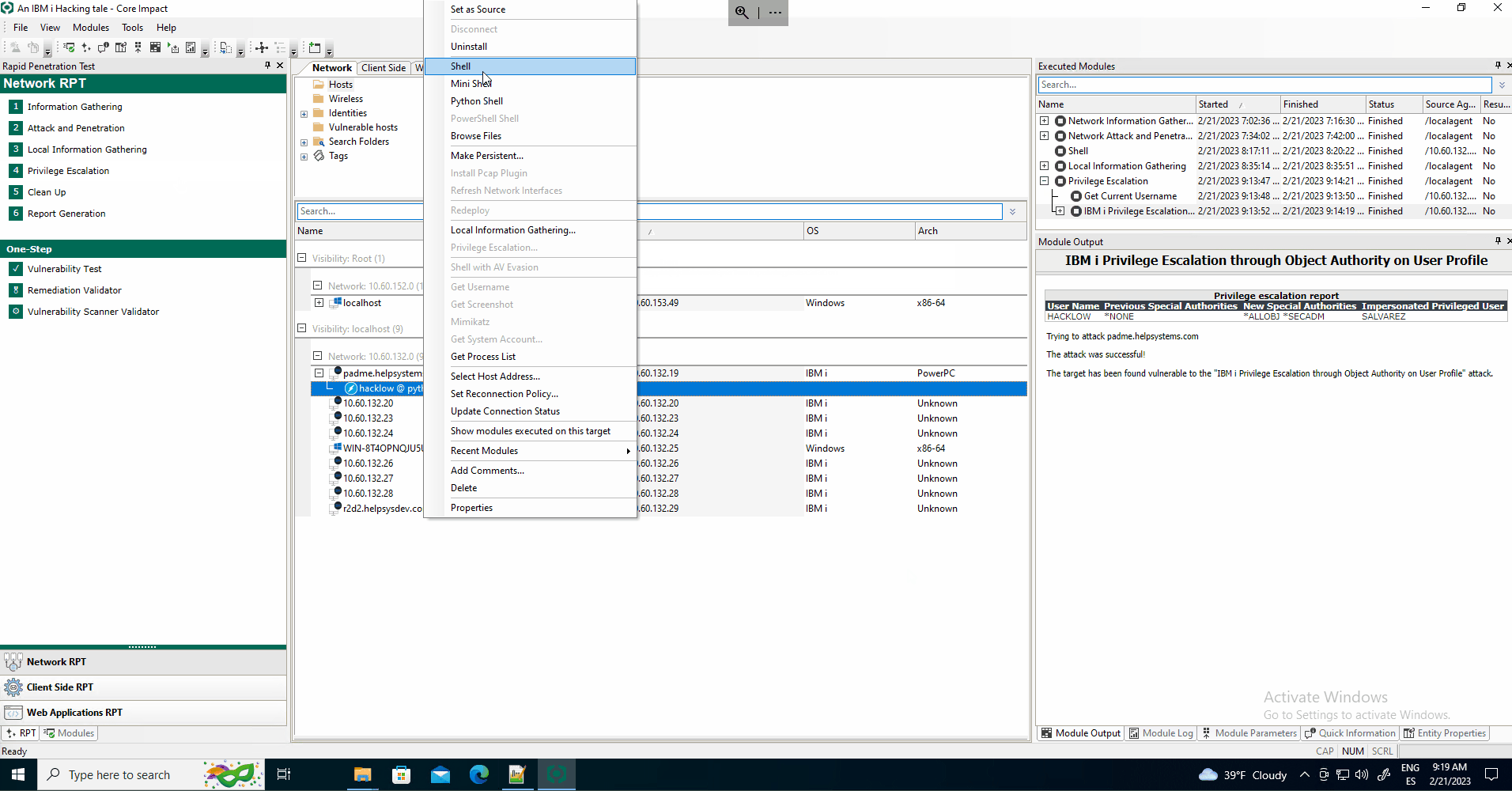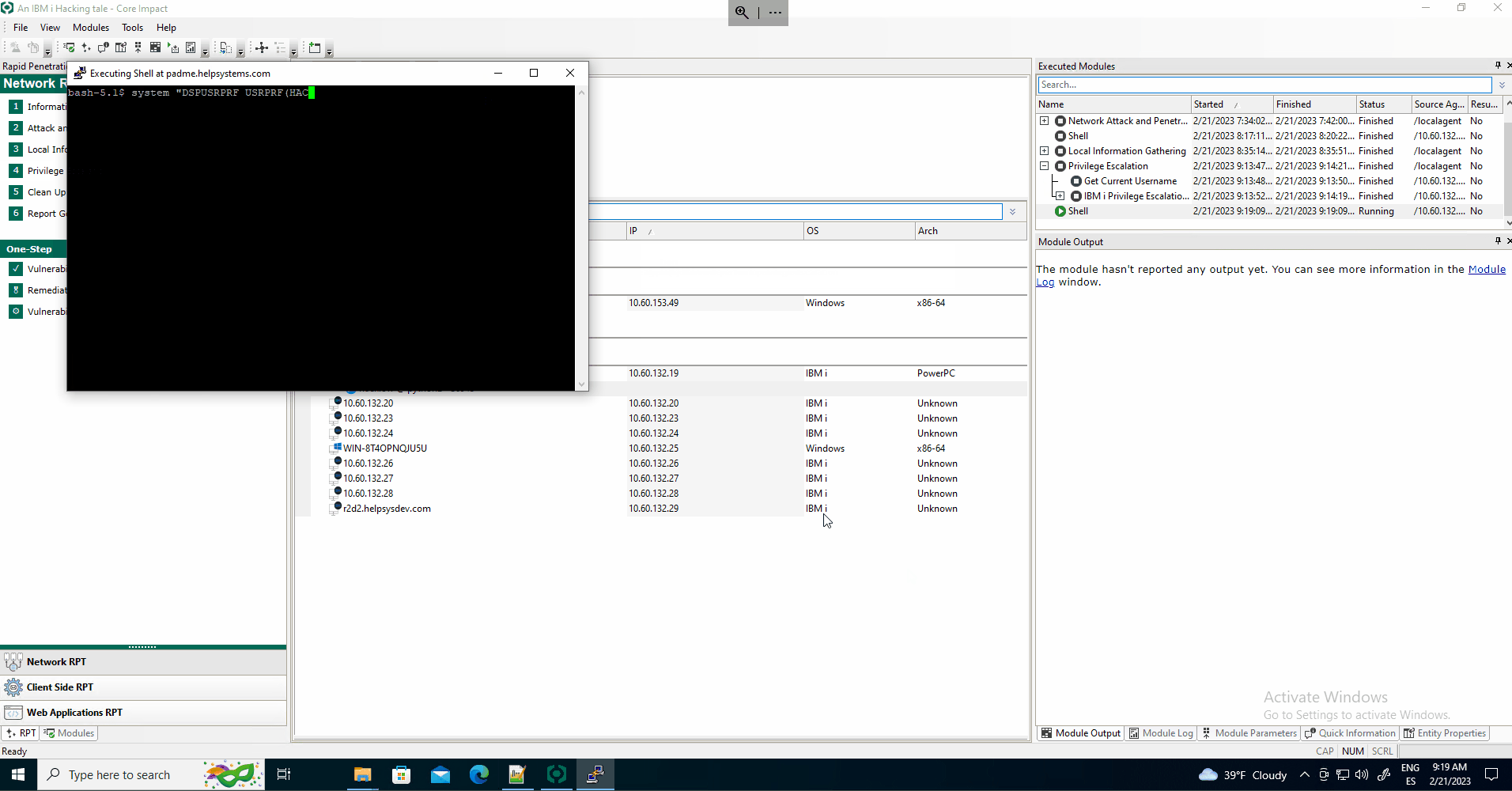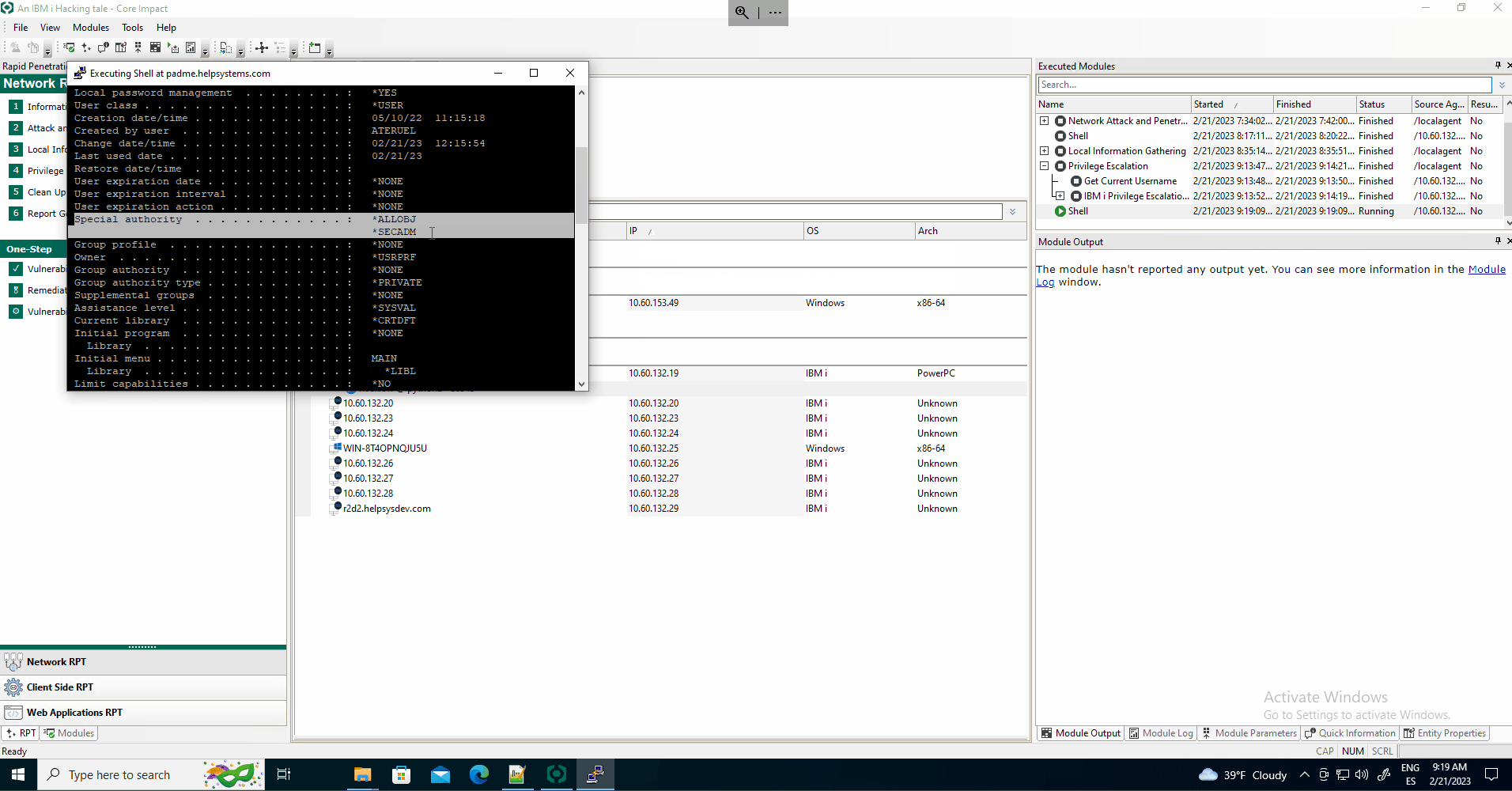
Due to the complexity of IBM i privilege management, these misconfigurations are common, especially on systems with a high number of users. While discovering an exploitable path was sufficient to progress towards project goals, it is important to uncover similar vulnerabilities in the system via configuration review.
IBM i is a securable platform, but if you're not using your security features to their full extent, you're leaving the door open for anyone—from unauthorized users to cybercriminals—to access your business data. Penetration Testing is a necessary step in knowing the risks you face and mitigating them.
