Man-in-the-Middle attacks often give penetration testers some advantages of being able to take information from a user without them knowing it. This video discusses how to perform these types of attacks using Core Impact.
Man-in-the-Middle attacks are a popular way to give penetration testers some advantages of being able to take information from a user without them knowing. Man-in-the-middle attacks require three components to be successful.
There's the victim and they are going to be trying to communicate with some type of entity—whether it be a Web application or the Web server. There's also going to be the person in the middle who'll be intercepting the victim's communication. The critical component of this is that the victim is unaware that there's a man in the middle harvesting information or relaying information, whether it be DNS or IP address. That gives the attacker some leverage of being able to fool a user. This can happen when someone is trying to log into a bank site and they want to confirm some contact information. Or maybe you're able to send a successful phishing email. Once they click on that link in the email, you're redirected to another site, in which case the user puts in information into the site and you're able to take credentials from that. Or you're able to send a link to a user, they click on the link, you download a payload, and then you put some type of a password sniffer or cookie sniffer on that machine.
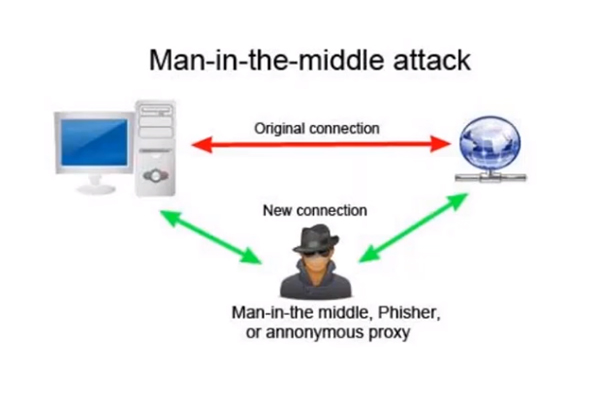
We'll try to cover some of these from a phishing standpoint as well as a Web application standpoint today within Core Impact.
User Setup
For this training we have a lab set up, but if you are doing your own phishing, you might setup something separately or use it an SMTP relay. It really depends on the environment.
We’ll start by going to the client side to perform the phishing attacks. We’ll set up a couple of users by either importing users or by reaching out and identify users. For this example, we’ll call it test user collection and victim at local host. In the real world, you would actually have a recipient that is part of an e-mail environment.
If we wanted to put something from a legitimate user, you don't have to actually be from a part of their e-mail environment. Within Core Impact you can just put in whatever e-mail you want. All you need to do is relay that mail over to them and then on this side, we have this user log in and receive the mail.
Phishing Campaign
Now we’ve got an attacker and a victim. For this example, we’ll go straight to the exploit folder and click the “Client-Side Phishing (Web Page Clone)” exploit. We’re going to clone a Web site and send it to the user. When they click on the link, it's going to redirect them somewhere. Once they are redirected there, I'm going to have them put in their credentials so we can harvest that information. If you have an SMTP server that you want to relay off of, you would put that in here and then username and password. There are some free sites that gives you the capabilities of doing that.
User Credentials
For this example, let's say we’re going to go to LinkedIn login screen and after that we’ll redirect them to LinkedIn so they won't know the difference. You can take a look over in the module log to see what’s happening, what’s taking place, and see if it was successfully sent through.

Now we’ll go back over to the user I sent the email to. The user says “Oh no, I’ve got to update my security. Let me go to the portal.” So they click the link and it's redirecting them to LinkedIn. The user will enter an email and password to sign in.
Let's take a look and see what's happening back in Core Impact. We can now see what they've actually submitted in the “Quick Information” area. Now we can take this back over to the network side and start doing some attacking. This was a quick way of doing man-in-the-middle attack using phishing.
Agent Packaging
Another technique you can utilize is actually packaging up an agent and sending it via email. An agent is really just a payload and Core Impact has a couple of different ways of doing that. You can do it by downloadable link or directly as an executable, or you could package that up into a VBA script. For this example, we’ll just going to send it over as an executable.
You’ll want to click on “Send Agent by E-Mail” and fix your parameters.
In this example the victim will think there's security updates and then I see that there’s some executables. They’ll click to download it.
Back over on the Core Impact side, all of this information has been captured. And since we’re sending an actual payload, what we're wanting to see on the Core side is if a user clicks the link, then they download the payload and an agent is placed on the machine.
Not only do we have their credentials from here, but we also have a payload on their machine. And this is really what you want when you have Core Impact. You want to be able to land agents somehow. If you right click on the agent I have all a variety of capabilities now that you could run from here.