This Core Impact in 20 Minutes training session covers post-exploitation techniques, specifically highlighting some of the things you can do within Core Impact after initially compromising a system.
Once you have an initial compromise within a system, there are a number of things you’ll want to explore from that compromised device such as information gathering, privileged escalation, backdoors and persistence.
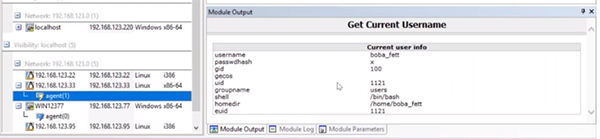
Username Discovery
In this example, we’ll start on the network side of Core Impact. If you right click on the agent you’ve already deployed, there are a number of post exploitation techniques against the machine such as Shell access, and credential harvesting with Mimikatz. If you want to see the username, simply right click on the agent and select “Get Username.”
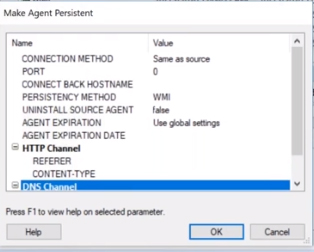
Persistent Agent
You can also right click on the agent and make yourself persistent. You can do this either manually or by using a module within Core Impact to set your parameters. When you make yourself persistent, it will write it to the machine. This is different from the initial compromise of the machine which is in memory. This will actually write something to the machine so clean up will need to be a little bit different, so it’s important to keep that in mind.
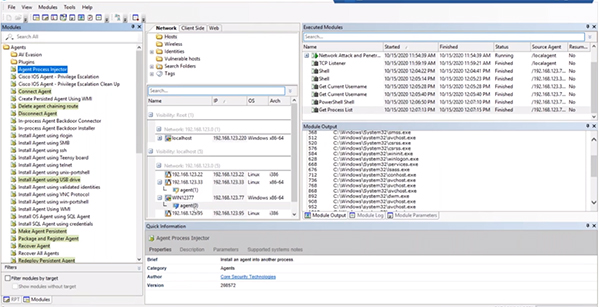
Process Injection
You can also right click on an agent to see the process list. You can also inject yourself into a process by running the “Agent Process Injector” module. A new agent will be deployed with the new process.
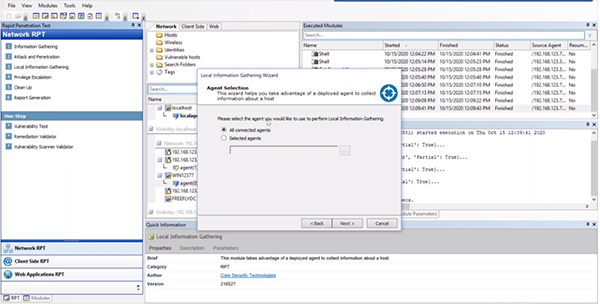
All of the manual post exploitation techniques within Core Impact can be found within the “Local” folder within the “Information Gathering” folder. When you click on an agent, the capabilities that are applicable to that agent will be highlighted to make it easier for you to identify what might be best to run.
They can also be found in the RPT area under the “Local Information Gathering” step. This will run all applicable information gathering steps for your agent by dragging it to the agent you want to work with.