This video defines, discusses, and demonstrations how to conduct different types of password attacks in Core Impact, including:
- Brute force
- Dictionary
- Password Spraying
When it comes to Core Impact, people think of it just from an exploit standpoint. There are exploits within the tool, but there's a lot of other things that Core Impact can offer—like phishing and web application attacks. A lot of times the easiest way to get onto a system without having to actually exploit it, is to just grab some passwords that are easy to guess or default passwords. This training will cover where those features are located within the tool.
Dictionary Attack vs. Brute Force Attack vs. Password Spraying
A dictionary attack is just what it sounds like. You take common words from either a dictionary or a password list and you try those words against a user field or user password field.
A brute force attack is a little bit different. It is a combination of different characters or letters or numbers. This means it is not going to be something that is very human readable, like a dictionary word would be, but it'll be a combination of different letters, numbers, and characters.
Additionally, you can combine those with a dictionary attack to make a hybrid attack. For example, people often put an exclamation point instead of a one or using the @ symbol instead of a two or the letter four instead of an “A.” While dictionary attacks can be much faster because it's really just taking a plaintext password or plain text word and putting it in there, brute forcing takes a little bit more time and is more resource intensive against the system.
So what is password spraying? With password spraying you're taking those passwords that you've gotten from a phishing campaign or some other way, and you're throwing that across an enterprise of other machines or logins. Rather than just using a combination of passwords against the same system, you're taking that one password and spraying it across multiple systems or multiple logins to see if it can work on other systems. This is helpful if you're able to harvest passwords from an existing campaign or from a machine using other techniques and then take those and see if they can get you onto other machines.
Password Spraying with Core Impact
Within Core Impact we have already done some basic scanning of the environment so that we have my machines down here at the bottom. We’ve plugged in a Nessus scan and you can see all my machines are in here already. We also conducted a phishing email in an effort to gather credentials. As you can see on the right, we did send a phishing campaign email to Morty Smith, and it looks like that email has gone through successfully. However, nobody's clicked anything or done anything at this point. There’s no action on the user's part, so Core Impact has nothing to report at this point. However, we’re going to go ahead and move over to that machine.
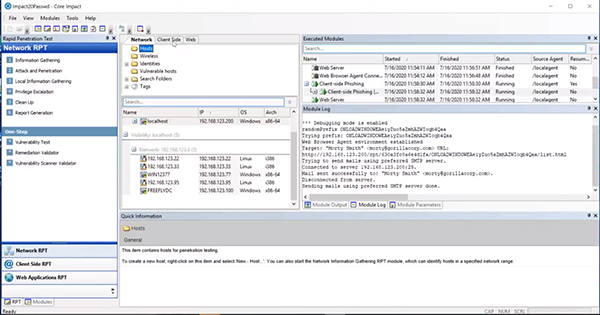
The Victim’s Standpoint
From Morty’s machine, it looks like someone sent him an email about the security policies. That sounds important to a user, so he clicks the link and goes to the security portal. At this point, Core Impact is going to redirect Morty to a spoof page. In this instance, it's just going to take Morty to another page that I've got setup for logins. In this example, we’ve utilized a local application that is used for other testing, but normally we would use the page that users would normally go to for their security portal.
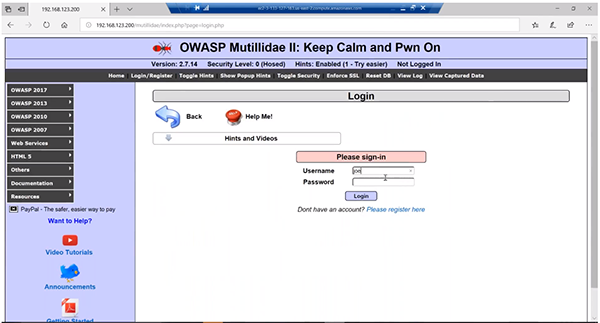
From here, we’ll try to login and use a password stored somewhere on the device. In this example we find a file and try “C0mpl3xP2ssw0rd!” and it didn’t work.
Core Impact Capture Details
Back in Core Impact we can now see that someone has clicked the link and we've captured some additional information around the browser and the IP address. This is helpful because Core Impact gives you the ability to attack some of these users as well.
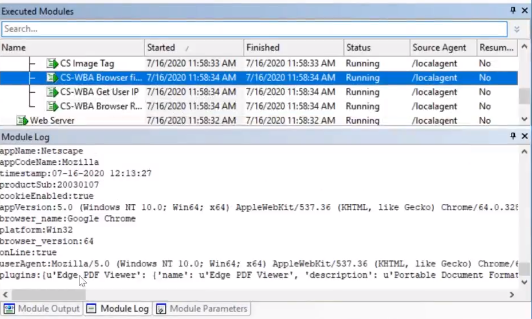
We can see that Morty clicked the link and that he submitted a form. We can event see that his “C0mpl3xP2ssw0rd!” was used. Now we have an idea of who Joe is and when we go back to the network side, can plug that information in the identities folder.
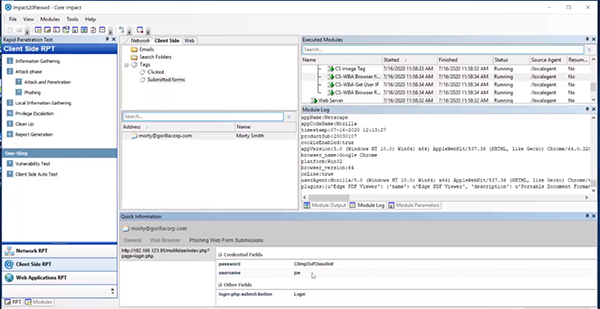
Password Attack Settings
There's a couple of ways that we can do password attacks. You can utilize the module folder system by going to “tools” and then “Identity Verifiers.” In this example, we’ll select the SMB verifier and pick a target. Core Impact will ask you if you want to use validated identities, ones you’ve grabbed, or ones you’ve imported.
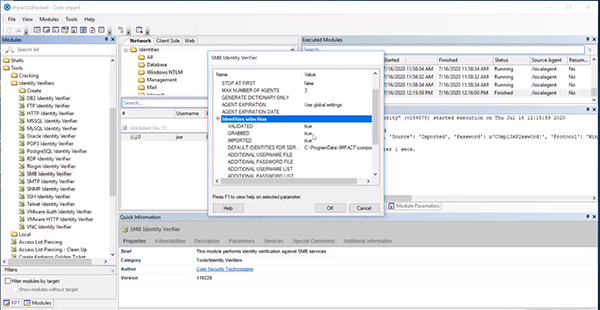
The other feature that you have is the combination. When we're talking about brute forcing, do you want to use partial identities, null passwords, or do you want there to be a variation and recombine different identities?
If you're going to be doing password attacks and you don't want to raise a bunch of alarms or you don't want to lock someone out of the account, you can change some of the ways that you do those password attacks. For example, delay between probes and max number tries per account.
Password Attack and Penetration
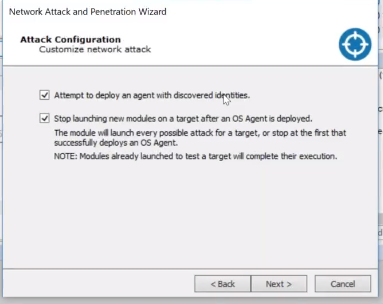
Now we’ll go over to our host and grab attack and penetration and bring it straight to the DC. Do I want to deploy an agent when I discover an identity? Correct. If I would be doing some without any usernames that we’ve already harvested, I might just try all the ones that Core Impact gives me in my dictionary list. There are certain protocols that I want to try. If I'm trying the DC, there might be only two or three services that are running on that. In which case it's going to match up based off of that.
Pivoting
It looks like because I did get “C0mpl3xP2ssw0rd!” from the phishing campaign and I did get Joe, I was able to deploy an agent using SMB. Now I know not only do I have a validated password in the environment, I can take that password and spray it across other machines. I am on the DC and right now as a privilege account, which is a pretty good place to be.
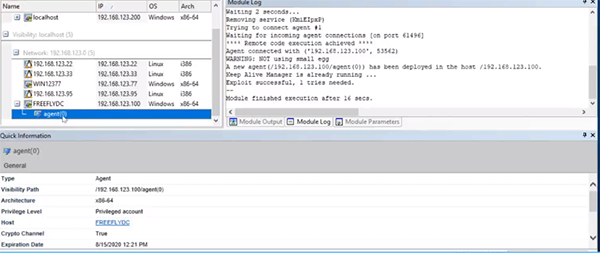
From here we might want to see if there's some other networks that we can get on by pivoting. You can right click it and hit Mimikats to start harvesting any other passwords or Kerberos tickets. All of these will be listed within my password field as well or any Kerberos tickets that I'm able to harvest.