What Is SIEM?

SIEM—or Security Information and Event Management—are solutions that monitor an organization's IT environment, relaying actionable intelligence and enabling security teams to manage potential vulnerabilities proactively.
This software provides valuable insights into potential security threats through a centralized collection and analysis of normalized security data pulled from a variety of systems. Think of it as a lens that sharpens your view across the big picture to help you focus your team’s efforts on where they can have the most impact, protecting your business and your customers from devastating data breaches.
A Brief History of SIEM
Gartner coined the term ‘SIEM’ (pronounced “sim”) in a 2005 report called “Improve IT Security With Vulnerability Management.” The term brings together the concepts of security event management (SEM) with security information management (SIM) to achieve the best of both worlds.
SEM covers the monitoring and correlating of events in real time as well as alert the configuration and console views related to these activities. SIM takes this data to the next phase, which includes storage, analysis, and reporting of the findings.
How Does a SIEM Work?
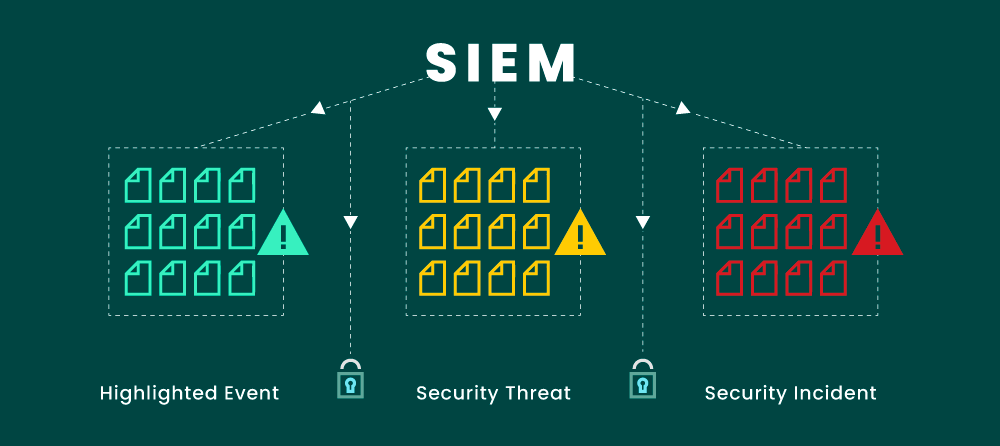
A security event is any occurrence in a IT environment that has the possibility of becoming a vulnerability, or an indication that the environment has already been exploited. Such events include unauthorized access, configuration changes, and abnormal user activity. A SIEM helps interpret these events to determine what threats pose the most risk and how they should be prioritized.
Managing Security Events Without SIEM
It’s no secret that security threats are increasing, and they can come from both internal and external sources. To address these issues, IT organizations have put various systems in place to protect against intrusion and a host of different threats. The downside of these safeguards is they generate so much monitoring data that IT teams are then faced with the problem of interpreting it all to pinpoint actual problems.
For example, syslog servers ping with every security notification, which can number in the thousands, or even millions depending on the size of the environment. Security teams can feel as though they are drowning in a sea of security warnings. In fact, the volume of security data flowing to understaffed IT security groups is largely useless unless it can be quickly analyzed and filtered into actionable alerts. Given the reams of data in question, it’s no longer possible for organizations to use manual analysis to handle this job. This is where SIEM solutions step in.
Managing Security Events With SIEM Software
It’s difficult to know which events are truly critical and which can be ignored. There could truly be no threats, or multiple incidents may be occurring that simply have not yet affected performance. A SIEM gives security teams a leg up in understanding the difference between a low-risk threat and one that could be detrimental to the business by centralizing and analyzing event data in real-time, looking for and prioritizing threats from a variety of assets within an IT environment—networks, applications, devices, user activity logs, different operating systems, databases, firewalls, or network appliances.
Not only is security data now flowing into a centralized view of your infrastructure, data is also normalized. This means that despite thousands or millions of inputs coming from different systems and sources, everything can be translated into a common format ready for the SIEM solution to conduct its analysis and correlation. This takes the workload off a security team and enables them to leverage a streamlined view of activity and potential concerns. Read more >
What Does Core Access Do?
Why Does SIEM Matter?
It’s no secret that security threats are increasing, and they can come from both internal and external sources. One rapidly rising concern is that of employees who accidentally misconfigure security settings in a way that leaves your data vulnerable to attack. To address these issues, IT organizations have put various systems in place to protect against intrusion and a host of different threats.
The downside of these safeguards is they generate so much monitoring data that IT teams are then faced with the problem of interpreting it all to pinpoint actual problems. In fact, the volume of security data flowing to understaffed IT security groups is largely useless unless it can be quickly analyzed and filtered into actionable alerts. Given the reams of data in question, it’s no longer possible for organizations to use manual analysis to handle this job. This is where SIEM solutions step in.
With SIEM software, IT professionals have an effective method of automating processes and centralizing security management in a way that helps them simplify the difficult task of protecting sensitive data. SIEM tools gives these experts a leg up in understanding the difference between a low-risk threat and one that could be determinantal to the business.


What’s the Difference Between SIEM and Vulnerability Management?
Vulnerability management focuses on proactively uncovering security weaknesses across the IT ecosystem using various software tools like vulnerability scanners and application security tools. SIEM tools inform vulnerability management by providing important intelligence about potential active threats in a user-friendly format to help staff concentrate their efforts.
An effective vulnerability management program includes creating sustainable processes to eliminate as many vulnerabilities as possible. However, it’s impossible to eradicate every single vulnerability in an environment and that’s where SIEM comes in — to help monitor and identify in real-time any potential security risks.
Most IT devices, systems, and applications provide security logging data — and lots of it — enough that security teams can easily be overwhelmed with data and miss potential threats. SIEM tools streamline and amplify security logging data processes by centralizing the collection of data from IT systems and allowing companies to gain visibility into their environments. A SIEM analyzes logging data, filtering out benign events and providing actionable information on incidents that pose the most risk. SIEM is an impactful tool that can help advance any vulnerability management program.
What Are the Benefits and Capabilities of SIEM?
SIEM solutions have the ability to:
- Centralize your view of potential threats
- Determine which threats require remediation, and which are simply noise
- Escalate issues to the appropriate security analysts who can take fast action
- Include context for security events to enable well-informed fixes
- Document detected events and how they were remedied in an audit trail
- Show compliance with key industry regulations in an easy reporting format
Over the years, SIEM technology has evolved, with vendors developing features that differentiate these tools from one another, such as:
- Centralized management and executive dashboards
- Monitoring unique data sources
- Long term event storage
- Predictable pricing models
- Tiered options to match organization's security needs
- Multi-tenancy capabilities
While this allows an organization to find a more specialized solution, it does make evaluation all the more important. Those interested in deploying a SIEM solution should look for additional features that best suit their particular environment. Given the number of SIEM solutions on the market today and the capabilities described above, it’s helpful to explore some of these features in depth to better understand exactly how a SIEM safeguards IT infrastructures.
What Are Use Cases for SIEM?
With a SIEM solution in place, your administrators gain insights into potential security threats across critical networks through data normalization and threat prioritization, relaying actionable intelligence and enabling proactive vulnerability management. There are multiple use cases in which a SIEM can mitigate cyber risk. By monitoring an organization's data streams, a SIEM can detect abnormal behavior and suspicious activity with:
Logins and logouts
User additions, deletions, and privilege changes
User behavior
Configuration alterations
Services starting and stopping
Roles added or changed

How do Enterprises and SMBs Benefit from SIEM?
Any organization can benefit from Security Information and Event Management (SIEM) solutions, though they are often seen as a necessity only for large enterprises with massive environments to monitor for security threats. While this may have been true over a decade ago, in the early days of SIEM. Since then organizational IT infrastructures have become increasingly multifaceted, and the threat landscape continues to evolve.
These days, small to medium sized businesses (SMBs) also struggle to manually manage the security of their IT environments. A SIEM can help any SMB gain visibility into their environment, providing insights on critical access and reducing the risk of security breaches. Read more >
Discover What a SIEM Can Do For Your Organization
Watch a SIEM in action in an on-demand demo and see how you can get visibility into your environment.
What Are the Different Types of SIEM Solutions?
Organizations of all different sizes from various industries can benefit from a SIEM solution. That said, it’s important to take the time to think about your particular needs to find a SIEM that’s the best solution for you.
Open Source SIEM
Open source SIEM solutions provide basic functionality that can be great for smaller organizations that are just beginning to log and analyze their security event data. These solutions are great for experimentation—to figure out what you really need to monitor and track, and take action when you identify suspicious behavior. Over time, many IT pros find that open source SIEM software is too labor-intensive to be a viable option as the organization grows.
Read more >
Open source SIEM solutions provide basic functionality that can be great for smaller organizations that are just beginning to log and analyze their security event data. These solutions are great for experimentation—to figure out what you really need to monitor and track, and take action when you identify suspicious behavior. Over time, many IT pros find that open source SIEM software is too labor-intensive to be a viable option as the organization grows.
Free SIEM
Always free SIEM solutions are obviously budget friendly and are typically straightforward and easy to use. However, they may or may not offer enough stability and functionality. Free but limited tools provide you with solutions from reputable companies that can offer sufficient coverage and functionality. However, as organizations quickly grow, their security needs grow with them. Further devices will need coverage, and more robust features start to become more of a necessity.
Read More >
Always free SIEM solutions are obviously budget friendly and are typically straightforward and easy to use. However, they may or may not offer enough stability and functionality. Free but limited tools provide you with solutions from reputable companies that can offer sufficient coverage and functionality. However, as organizations quickly grow, their security needs grow with them. Further devices will need coverage, and more robust features start to become more of a necessity.
Enterprise SIEM
Robust features, ease of use, and support are the standard items that make enterprise solutions stand apart from their free SIEM solution counterparts. However, enterprise SIEM solutions can be very different from one another. For example, a majority of SIEM tools are intended for huge organizations and would be far too complex and costly for smaller organizations. These businesses would instead search for a mid-range SIEM solution that still provides all the critical functionality and is more intuitive to use. To ensure your organization's priorities align with the tool, conducting a SIEM software comparison is always necessary.
Read More >
Robust features, ease of use, and support are the standard items that make enterprise solutions stand apart from their free SIEM solution counterparts. However, enterprise SIEM solutions can be very different from one another. For example, a majority of SIEM tools are intended for huge organizations and would be far too complex and costly for smaller organizations. These businesses would instead search for a mid-range SIEM solution that still provides all the critical functionality and is more intuitive to use. To ensure your organization's priorities align with the tool, conducting a SIEM software comparison is always necessary.
What Should You Look for in a SIEM Solution?
Given the number of SIEM solutions available, it's helpful to consider and prioritize the features that will best support your security monitoring efforts. Key areas to evaluate include:
1. Security Event Prioritization
Quickly determine which events are most critical and which are lower priority with a solution that has easy to use controls that can be adjusted as you see fit.
2. Normalization of Disparate Data Sources
Organizations with multiple technologies need a solution that normalizes this disparate data into a common format so security teams can quickly determine what the data means and what to do with it.
3. Data Enrichment
A solution with data enrichment capabilities provides additional context and event details to enable thorough forensic analysis.
4. Real-Time Threat Detection
Detect threats quickly to minimize the impact of a breach with a solution that can log, correlate, and prioritize events in real-time.
5. Streamlined Incident Response
Increase efficiency with a solution that can be tailored to automatically escalate events to the right person on your team.
6. Out-of-the-Box Security
In order to rapidly configure newly connected data sources, look for a solution that has out-of-the-box security templates that automatically apply the appropriate security controls and escalation rules.
7. Security and Compliance Reporting
Most organizations need to adhere to best practices and regulations, which requires a solution that can easily generate reports with the necessary information to prove compliance.
What Are the Different Types of SIEM Deployments?
SIEM and the Cloud
Security professionals erroneously assume the big cloud computing vendors (e.g., Amazon Web Services - AWS®, Microsoft Azure®, and Google Cloud Platform™) automatically apply rigid security controls to any data in their purview. Unfortunately, this isn’t the case. In fact, this responsibility falls squarely on your team’s shoulders, and many companies have experienced hacks or breaches by failing to properly secure data on their cloud servers. SIEM software can act as an overlay to many of the systems you rely on every day to guard against security threats affecting cloud-deployed data.


Multi Tenancy SIEM
In its original architectural context, multi tenancy establishes the difference between an apartment building and a single residence home. When used in technology, it describes a single instance of hardware or software that has more than one resident. Multi tenancy is perhaps most commonly recognized in conjunction with cloud computing, in which multiple users or groups reside on a single cloud server. It is also regularly seen in Software as a Service (SaaS) applications.
Certain SIEM solutions also have this capability. Clear partitions are in place to allow each tenant the ability to use it for their own environment. Each instance can be tailored specifically to meet the requirements and needs for any given infrastructure. Data remains strictly siloed to ensure both privacy and security. For instance, a Security Operations Center (SOC) that oversees multiple agencies would create a different tenant for each agency.
What is SIEM’s Role in Regulatory Compliance?
SIEM software gained popularity with large businesses working to comply with the Payment Card Industry Data Security Standard (PCI DSS). In addition, it has highly useful applications in helping you meet regulations for the EU’s General Data Protection Regulation (GDPR), Sarbanes-Oxley (SOX), and others. These laws require organizations to have mechanisms in place to detect threats and resolve them quickly. This means you have to know what’s happening in a wide-reaching IT infrastructure that could span on-premises, cloud, and hybrid environments.
A SIEM solution is key to getting the right kind of insight in place to monitor data and act quickly for threats determined to be cause for alarm. When all this activity is captured in a detailed audit trail, auditors can see your organization is taking the necessary steps to protect its data.
SIEM Solutions from Core Security
Event Manager
Comprehensive security and event management (SIEM) solution
that provides real-time threat detection and prioritization.