For anyone who’s been in cybersecurity for even the past five years, the trends are as unprecedented as they are obvious; attacks are now more sophisticated, subtle, and scalable than ever before.
Cybercriminals use AI to automatically find vulnerabilities, the mean time-to-exploit has now dropped to only 5 days (down from 32), and there is little to stop spray-and-pray campaigners from casting a wide net.
Against this backdrop, offensive security — specifically pen testing and red teaming — is no longer a “nice-to-have” but a core requirement for defending organizations. And not only do the two synergistically work best together; they are increasingly mandated by regulation.
The Evolution of Security Needs
Today, advanced exploits are hitting more entities in more industries than ever before. A June 2025 surge in worldwide APTs against critical infrastructure illustrates the point, and 87 percent of all security professionals report AI-based attacks on their organizations in the past year. A recent study reveals that ChatGPT can already generate attack code with 16 percent success; 50 percent with cybersecurity skills.
As cyber threats have escalated and improved, organizations have had to step up their security game to keep pace. This expanded security maturity has manifested most in defensive cybersecurity; think detection and response, firewalls, data loss prevention, email security, and data protection in the cloud.
While essential, defensive cybersecurity only represents half of what needs to be done. Attackers are coming at enterprises with every tool at their disposal; organizations cannot afford to hold back. To harness a complete approach, both defensive and offensive cybersecurity are needed.
Offensive Security Defined: Pen Testing vs. Red Teaming
Offensive security, or OffSec, rounds out cybersecurity by providing an effective way to battle-test defensive security measures.
By pen testing and red teaming, organizations refuse to be sitting ducks. Instead, they invest in available defenses, then test those defenses to ensure they are up to the challenges presented by today’s attack tactics.
Pen testing simulates targeted attacks on specific systems or applications to uncover exploitable vulnerabilities and attack paths.
This verifies which security weaknesses could be used by malicious actors to access business critical systems and data.
Red teaming provides a full-scope adversarial simulation testing people, processes, and technology. It mimics how a long-term embedded threat actor would behave after gaining access. Red team engagements are designed to test detection, response, and resilience in exactly the same way they’d be tested in a real-world attacks.
Why Pen Testing and Red Teaming?
While they share some overarching similarities, it is important to note; one is not a replacement for the other. Together they form a complete offensive security posture.
Pen testing identifies exploitable weaknesses, highlighting where you are vulnerable and allowing you to close technical gaps. Red teaming is an assessment of cyber defense, determining how well your organization can detect and respond once an attacker has exploited security gaps whether they are technical, staff related, process related, or physical security.
The Regulatory Push for Offensive Security
Not only is offensive security a best practice for all industries (especially those highly regulated industries like government, finance, and healthcare) but it is fast becoming a requirement.
-
FedRAMP: A Third-Party Assessment Organization (3PAO) must perform a FedRAMP-approved pen test annually to give cloud service providers (CSPs) Authority to Operate (ATO).
-
FFIEC: The FFIEC guidelines require financial institutions to implement penetration tests that “[subject] a system to real-world attacks” and “identify weaknesses in business processes and technical controls.” These can be performed internally or outsourced and done to the level of assurance required per risk assessments.
As the trend continues, it is likely coming to HIPAA, DORA, and other major regulations soon. As it stands now, pen testing is one of the best ways to meet certain security requirements, whether it is explicitly named or not.
Red Teaming Requirements: Regular red team engagements are currently mandatory in the following regions:
-
UK (CBEST)
-
EU (TIBER-EU)
-
Hong Kong (ICAST)
Again, whether it is explicitly required by name or not, it remains one of the best and most reliable ways to proactively evaluate and prove the efficacy of your security defenses. Just like no community would trust firefighters who refuse to do regular fire drills, no organization should feel 100 percent confident in a cybersecurity strategy that doesn’t regularly put its technology and team to the test.
As proven ways to discover and reduce risk, pen testing and red teaming will continue to be codified into more compliance frameworks in the years ahead.
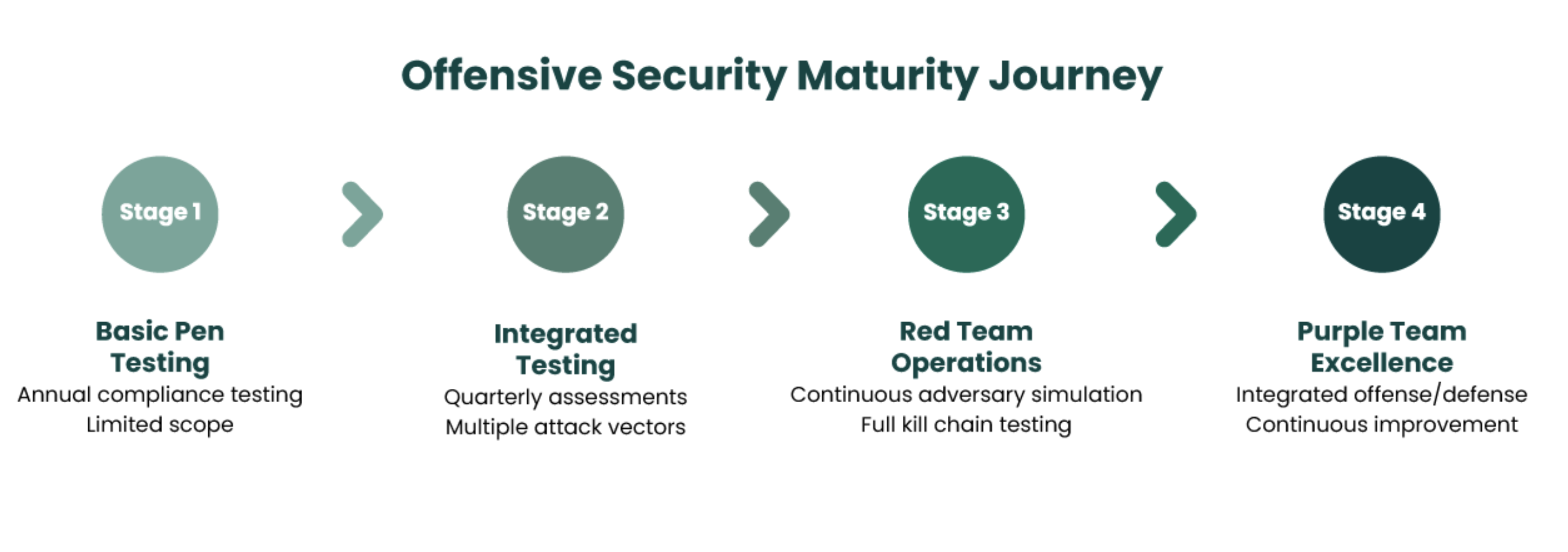
Building an Offensive Security Strategy
Security maturity is advancing across industries — for both organizations and the malicious actors that target them. To stay ahead, organizations need to empower their teams with the skills and tools needed to meet these threats at scale.
More often than not, that requires practice — the kind of practice only simulations can bring. Organizations with in-house pen testers and red teamers need to arm their teams with the tools needed to perform efficient, advanced engagements. If onsite teams aren’t an option, they can outsource this kind of essential offsec testing.
The ultimate goal from so much proactive training is for organizations to adopt a purple team mindset and create an environment where red and blue teams contribute as much as compete. Red teams can test blue team defenses while blue teams tighten defenses based on red team insights.
Only by completing the loop with leveled-up awareness and blue team tactics will the full offensive security investment be realized.
Bundle Solutions for Maximum Coverage
Our Offensive Security Bundles streamline multiple layers of complexity to create a mature security program and ensure your organization can prevent successful cyberattacks.
