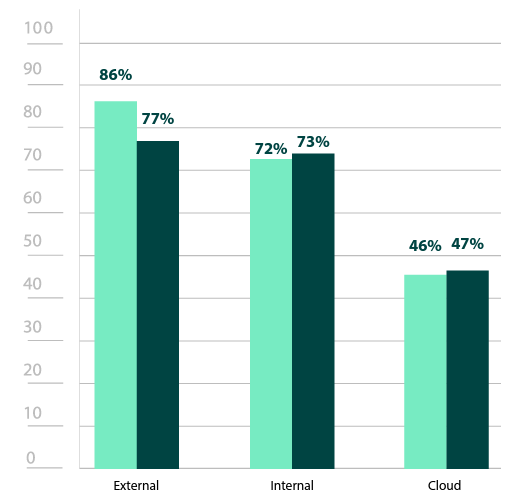
With cybersecurity threats perpetually looming, many organizations have come to rely on penetration testing to assess their security stance and uncover weaknesses. According to the 2023 Pen Testing Report, 86% of respondents reported they pen test at least once a year. But are security teams testing every aspect of their IT infrastructure? Internal and external network penetration tests traditionally focus solely on the on-premise hardware that run an organization’s systems and applications. However, with more services offered through the cloud, the need for pen testing this aspect of your infrastructure should not go overlooked. Read on to learn more about what these different types of tests cover and clear up the misconceptions of cloud pen testing.
Commonly Pen Tested Infrastructures
External Penetration Testing
The 2023 Pen Testing Report revealed that 86% of security professionals pen test their external infrastructure. It is unsurprising that so many cybersecurity professionals prioritize these external networks, as they encompass all public-facing assets—including the internet at large—which are inherently more exposed. Additionally, since many organizational applications, like mail servers, websites, or even customer portals maintain a connection to these external networks, they can provide a doorway from which a threat actor can pivot to other, more sensitive parts of the environment. External penetration tests use the same techniques as adversaries to attempt to exploit weaknesses in an organization’s front facing perimeter or attempt to bypass them altogether with strategies like a phishing campaign or other social engineering methods.
Internal Penetration Testing
Though not as common as external pen testing, 72% of respondents pen test their internal network. This is understandable, since unlike external networks, internal networks are only intended for those explicitly given access to an organizational network. Internal networks can be made up of any number of assets—workstations, smart devices, intranets, etc.—as long as they are exclusively restricted for employee, contractor, or vendor use. Though internal attacks may not be quite as easy to achieve as an external attack, this is no reason to skip out on internal testing.
One of the key reasons why internal testing is so vital is that not only that external attackers can pivot to internal resources using techniques like phishing, but direct attacks are also possible if an employee has malicious motives. Such threats pose a particularly large risk, since they already have legitimate access to internal assets. These threat actors have far fewer barriers standing between them and an organization’s most sensitive or confidential data, which makes them capable of significant damage. One potential scenario is a disgruntled ex-employee who finds their access has not yet been cut off. Internal network pen tests assume the role of an internal threat actor, identifying potential weak points, like orphaned accounts or poorly managed access privileges. Since these tests start with internal access, they may attempt to achieve more high-value objectives including acquiring high-level privileges, compromising the Domain, or accessing other valuable assets and/or information.
Why Cloud Penetration Testing Should Not Be Overlooked
Even though cloud offers an effective, scalable way to provide access to company data, many organizations have developed blind spots when it comes to cloud security. Perhaps the greatest and most common threat seen with cloud services are misconfigurations. This can be because no security policy has been applied, there is lack of oversight, or access is purposefully open for the sake of convenience. Unfortunately, misconfigured cloud servers can result in breaches, data theft, compliance violations, lost revenue, and other damaging consequences.
This has become such a problem that research suggests two-thirds of cloud attacks could be prevented by finding and resolving misconfigurations. Despite the fact that 80% of cybersecurity professionals expressed concern about misconfigurations, less than half of the respondents (46%) in the 2023 Pen Testing Report conduct penetration tests which would easily uncover them.
Part of the reason cloud penetration testing may not be as common is the confusion over where the responsibility for security lies. While many assume that the cloud provider is in charge of the bulk of cybersecurity efforts, it is much more of a shared responsibility. The amount of responsibility varies considerably, with factors like type of service, provider, and geographic location all coming into play. However, there are a few things that always fall on those utilizing the cloud, including aspects of cybersecurity. There is no guarantee that a cloud provider will specify exactly when and where security tools should be leveraged. Organizations using cloud services must take proactive measures—like pen testing—to minimize risk.
How You Can Pen Test Your Cloud Infrastructure
Gartner predicts that by 2025, more than 85% of organizations will operate by the “cloud-first” principle when adopting platforms. Businesses will soon be unable to run without some sort of cloud component. Unfortunately, this near universal cloud adoption will come with corresponding security risks. Additionally, cloud security will become increasingly regulated and routine cloud pen testing may soon be an explicit requirement.
All this means is that when it comes to pen testing your cloud services, sooner is better than later. But just how can you go about it? Organizations can pen test their cloud infrastructure in a number of ways. Third-party services can focus entire engagements on your cloud environments and provide clear guidance on risk prioritization and mediation. But security professionals within an organization are not limited to contracting such services. Even those utilizing them may want to be able to run more frequent routine testing. Automated pen testing tools like Core Impact work for cloud testing just as they do with other environments, enabling security teams to test the security controls for which they are responsible.
As for the cloud providers, there are good indications that they, too, are also taking security more seriously than ever, with companies like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud all investing more than ever into security. While providers do their part, cloud users must commit to be equally diligent in their efforts to create a sunnier forecast for cloud security. Cloud security is a team effort, and users should not hesitate to take the lead and ensure that security is covered from all angles.
Find out how other cybersecurity professionals are pen testing in their organizations
Read the 2023 Penetration Testing Report for more insights about the latest pen testing trends and challenges.
