What is Network Security Testing?
Networks are a critical part of every organization, connecting assets so they can communicate with one another. An attack on a network can be devastating, as the threat actor may easily gain access to every device within that network.
Network security testing aims to reduce the risk of successful attacks by finding weaknesses before the attackers do, determining the potential of exploiting them, and providing evidence of the full scope of these vulnerabilities. Comprehensive network security testing typically includes three different assessments:
Vulnerability Scanning
Vulnerability scanners are automated tools that search for and report on which known vulnerabilities are present in an organization’s internal or external network. These scans can give an organization an idea of what security threats they may be facing by giving insights into potential security weaknesses present in their environment.
Internal scans survey the security posture of the target IP-based systems and networks, while external scans survey all Internet-facing assets such as routers, firewalls, web servers, and e-mail servers.
Vulnerability scanners are automated tools that search for and report on which known vulnerabilities are present in an organization’s internal or external network. These scans can give an organization an idea of what security threats they may be facing by giving insights into potential security weaknesses present in their environment.
Internal scans survey the security posture of the target IP-based systems and networks, while external scans survey all Internet-facing assets such as routers, firewalls, web servers, and e-mail servers.
Penetration Testing
Pen testers focus on exploiting and uncovering vulnerabilities on different types of networks, associated devices like routers and switches, and network hosts. Pen tests aim to exploit flaws in these areas, like weak passwords or misconfigured assets, in order to gain access and pivot within the network to find critical systems or data.
Pen testers focus on exploiting and uncovering vulnerabilities on different types of networks, associated devices like routers and switches, and network hosts. Pen tests aim to exploit flaws in these areas, like weak passwords or misconfigured assets, in order to gain access and pivot within the network to find critical systems or data.
Remediation Verification
After a pen test has been completed, organizations will have the opportunity to implement the recommended changes, fixing the weaknesses that were putting them most at risk. After some time has passed, these remediations can be validated by running another test to see if these weaknesses are still present or have been successfully removed.
After a pen test has been completed, organizations will have the opportunity to implement the recommended changes, fixing the weaknesses that were putting them most at risk. After some time has passed, these remediations can be validated by running another test to see if these weaknesses are still present or have been successfully removed.
The Core Security SCS team of experienced cybersecurity professionals specialize in providing network security testing engagements unique to your specific environment.
External Network Security Tests
External networks encompass all public-facing assets, including the internet at large. Threat actors attempt to gain access to an organization’s internal systems by leveraging these external assets. Since many organizational applications, like mail servers, websites, or even customer portals maintain a connection to these external networks, they can provide a doorway if not properly protected. Attackers may attempt to steal sensitive data or take control of an asset and use it for their own purposes, like cryptomining or as part of a botnet.
External network vulnerability scans unveil vulnerabilities that exist in your internet-facing assets, including websites, applications, or API endpoints. These tests examine external network assets for known software security vulnerabilities and identify weaknesses in the access controls, trust relationships, and integration deficiencies that could be utilized as part of a complex attack. External penetration tests use the same techniques as adversaries to attempt to exploit weaknesses in an organization’s front facing perimeter or attempt to bypass them altogether with strategies like a phishing campaign or other social engineering methods.
Internal Network Security Tests
Internal networks are those used solely by individuals given access to an organizational network, like employees, contractors, or vendors. Internal networks consist of any asset restricted to such parties, such as an intranet, cloud storage, or workstations. Unfortunately, internal users have the potential to become insider threats, whether by accidentally opening a phishing email, or purposefully having malicious motives. Such threats pose a particularly large risk, since they already have legitimate access to internal assets. An insider attack can be especially damaging, since these threat actors have far fewer barriers standing between them and an organization’s most sensitive or confidential data.
Internal network vulnerability scans unveil vulnerabilities that exist within your network on assets accessible by employees or contractors. Internal network pen tests assume the role of a disgruntled employee, or a threat actor who has stolen credentials to demonstrate potential weaknesses, like orphaned accounts or poorly managed access privileges. Since these tests start with internal access, they may attempt to achieve more high-value objectives including acquiring high-level privileges, compromising the Domain, or accessing other valuable assets and/or information.
Network Security Testing from Core Security
Our team of experienced cybersecurity professionals provide a variety of custom internal and external network security test offerings, as well as service packages, to help bolster your security program throughout the year. These renewable, annual packages ensure that penetration testing will become a routine practice, providing you with regular insights on your security status and strategies on how to best protect your critical data and assets.
External Network Packages
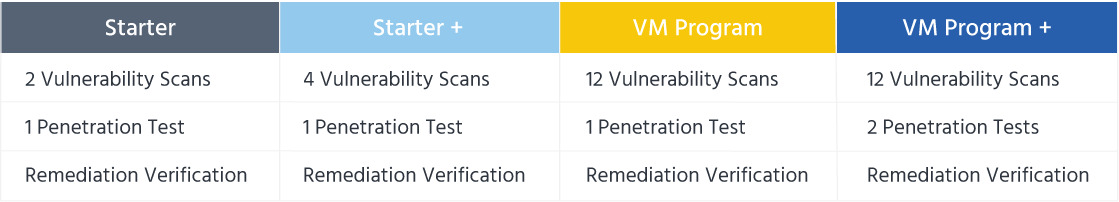
Internal Network Packages
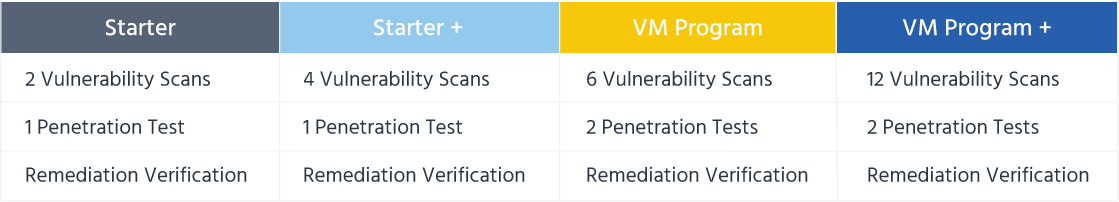
Reporting
Upon completion of a network security test, you will receive a comprehensive report that not only describes the results of the assessment, but also provides suggestions on steps to take for remediation. Details of the report will include:
