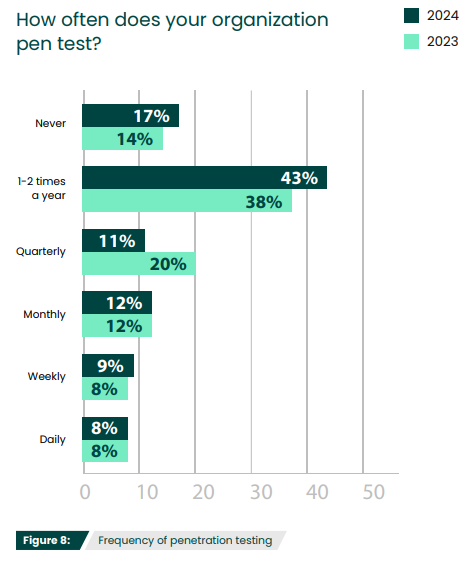
Penetration testing has become an increasingly standard exercise, with organizations using either pen testing services or in-house teams to uncover weaknesses and assess their security posture. Many businesses want to stay proactive about securing their IT environment and find that pen testing helps them stay compliant and prove adherence to regulations or industry best practices. According to the 2024 Pen Testing Report, the majority of cybersecurity professionals (43%) run a penetration test once or twice a year. But is annual testing enough? Let’s explore why organizations should be conducting penetration testing more frequently, and how to find the right balance.
How often does your organization pen test?
Should You Be Pen Testing Daily?
Running penetration tests daily may actually be too much of a drain on all resources—time, budget, and talent. While there are some aspects and types of penetration testing that can be automated, the process itself is not automatic and a human element is still heavily required. While 8% of those surveyed for the 2024Pen Testing Report did say they were running tests daily, it is more likely that they were running vulnerability scans that frequently.
Vulnerability scans are often mistaken as synonymous with penetration tests, but, while they are both important security practices, they are actually quite distinct. Vulnerability scans look for and report if known vulnerabilities are present within an IT environment. The best vulnerability management solutions employ an ongoing process that regularly identifies, evaluates, reports and prioritizes vulnerabilities in network systems and software, presenting the information in an easily understood format so you can protect your business-critical assets efficiently and effectively.
While vulnerability scans provide a valuable picture of what vulnerabilities are present, penetration tests can add more insight by seeing if these vulnerabilities could be leveraged to gain access within your environment. To put it simply, vulnerability scans offer a high-level view, identifying potential risks, while penetration testers zoom in to investigate that potential. Some penetration testing tools, like Core Impact, can integrate with vulnerability scanners such as Fortra VM to validate their findings.
The advantage of vulnerability scans is that most are completely automated, making them much easier to run on a daily basis. Frequently looking at the broad picture of vulnerabilities in your environment can provide a useful bridge between pen tests—alerting you of any new vulnerabilities along with an initial sense of their severity. However, vulnerability scans should not be substituted for regular penetration tests.
The Importance of Retesting
One of the most critical reasons to pen test more frequently is the need for retesting. Retesting involves running the same exact tests as the previous pen testing session in order to verify that remediation efforts were successful. Sometimes changes are made to resolve security weaknesses found in penetration tests, but it’s just assumed that these measures sufficiently fix these issues. How do you know these actions worked unless you put it to the test? Even simple mistakes, such as not restarting the system after applying a patch, can cause a weakness to persist. Retesting against the baseline of an initial test ensures improvements have been successfully implemented and security holes are closed.
While it may seem like a large effort to redo a test you have already completed once, the retesting process should be simplified and more efficient. Third-party services typically provide detailed reports of what actions were taken during the first test, which can then be used to provide instruction on exactly what to do for the retest. Some tools, like Core Impact, allow for pen testing sessions to be saved while they are initially run, logging what attack paths were used. These tests can then be automatically rerun at a later time for remediation validation. Comparing reports from both tests should not only show you that weaknesses have been resolved, it should also reveal if any new vulnerabilities have been uncovered.
Expanding Your Pen Testing Program Without Exhausting Resources
Oftentimes, it is assumed that running a pen test must be comprehensive, assessing the security status of the entire IT environment—the idea of expending such an effort more than once or twice a year can seem overwhelming.
However, pen testing can be done at any scale. In addition to annually running a large-scale assessment, organizations can run strategically scoped tests (and retests) focusing on critical systems. Different resources can also be used for different tests. While third-party services may be ideal for those larger, full infrastructure tests, automated pen testing tools can be used to run basic tests that should be more routine, like validating vulnerability scans, network information gathering, privilege escalation, or phishing simulations.
The Right Testing Frequency
So how often should you pen test? Ultimately, there is not a rigid, specific number. It will depend on the size of your organizations, the scale at which you want to run your tests, and the type of resources you want to use. The “right” frequency is simply one in which you feel you never have to guess at your security status.
Find out how other cybersecurity professionals are pen testing in their organizations
Read the 2024 Penetration Testing Report for more insights about the latest pen testing trends and challenges.

