As security threats persist, cybersecurity professionals are increasingly relying on penetration testing to uncover weaknesses and assess their security stance. According to the 2023 Pen Testing Report, 94% of respondents reported pen testing was at least somewhat important to their security posture. Organizations use a variety of methods to conduct such tests, using pen testing services, in-house teams, and/or penetration testing tools to take a proactive approach in protecting their IT infrastructure. But are security teams testing every part of an IT environment? Read on to find out more about which systems and assets may be getting overlooked.
Commonly Pen Tested Environments
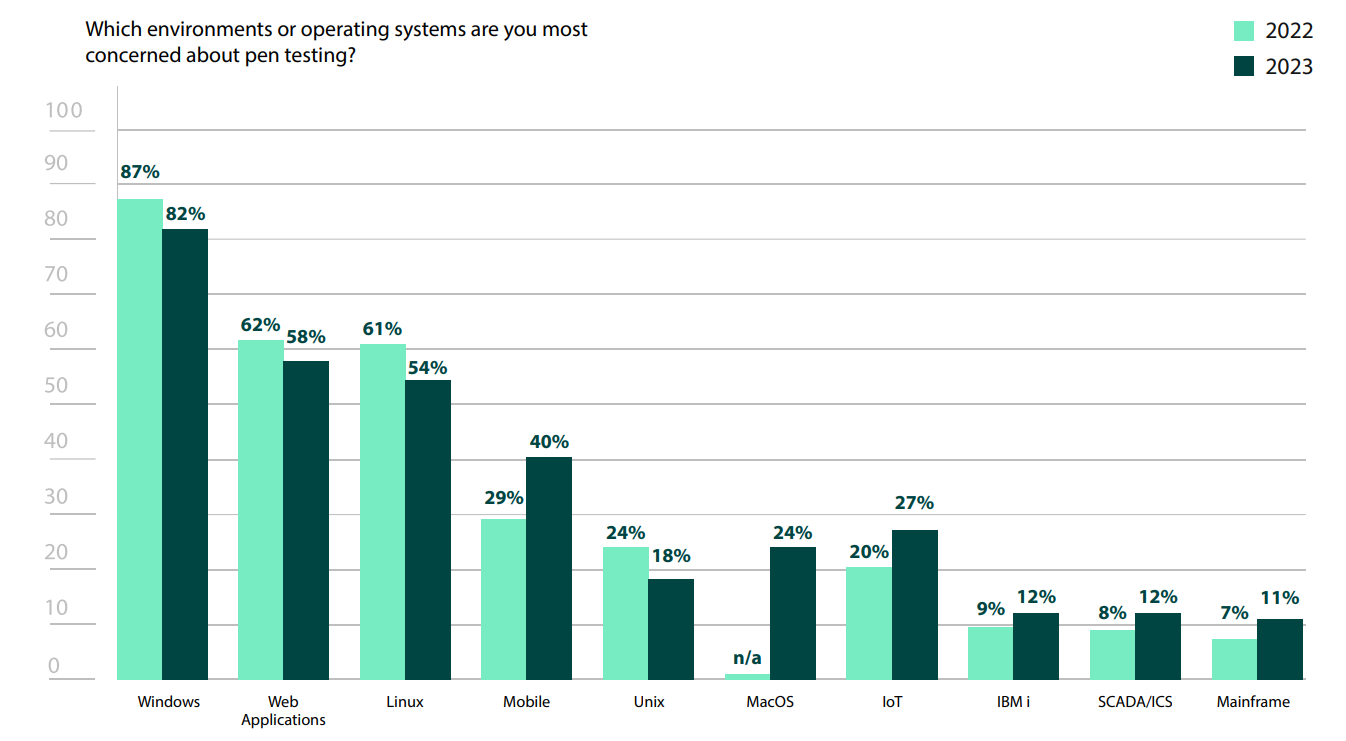
Unsurprisingly, Windows environments are the highest priority for many organizations, with 82% of respondents in the 2023 Pen Testing Report noting their concern about such systems. Though Windows does have a fair number of vulnerabilities, the concern around it is most likely due to the fact that Windows has a strong presence in nearly every organization, typically as the default workstation for employees.
Web applications (62%) are becoming equally ubiquitous and can be an easy attack vector. By their very nature, they have an external facing component that can serve as a starting point. Additionally, web applications commonly have security vulnerabilities that can be exploited—in fact, OWASP recently updated its Top 10 List of critical web application security risks.
Following close behind at 61% is Linux. Linux is often run on enterprise servers, where critical data is stored, so it’s comforting to know that organizations are aware of what a high priority target servers are to threat actors.
To maximize the effectiveness of penetration tests, it’s important to limit the scope. Having too broad of a scope only allows pen testers to scratch the surface of a number of vulnerabilities, instead of gathering valuable intelligence gained by going more in-depth in fewer areas or environments, with clear objectives in mind. For organizations just beginning to mature their security programs by adding in penetration testing, these are sensible environments to prioritize.
Other Environments to Consider
While Windows, web applications, and Linux servers may be the focus of initial penetration testing efforts, it’s important not to forget about other parts of your IT environment. Attackers often rely on this and can sneak in unnoticed, enabling them to linger for longer. Additionally, unlike workstations and servers, many non-traditional assets don’t have antivirus, so there are fewer layers of protection between an attacker and access.
The Internet of Things (IoT)
The Internet of Things (IoT)—a catch all term for the many different devices that have sensors or software that connect them to the Internet—has carved out a foothold in every industry. Hospitals are filled with devices that monitor patient status, home security systems helping monitor homes, and hydroponic sensors to ensure crop vitality on farms. Unfortunately, with these new advances come new risks, as an estimated 1.5 billion IoT breaches occurred in the first half of 2021 alone. This was more than double the amount that occurred in the first part of 2020, so IoT security needs are only growing.
A Holistic View of Cybersecurity
Organizational IT infrastructures have become increasingly multifaceted and sophisticated. While certain assets may seemingly never interact with others, that does not mean they are entirely siloed from one another—they are still part of the infrastructure at large. And when it comes to data breaches, access anywhere can mean access everywhere. Once initial entry is gained, it’s significantly easier to use post-exploitation techniques to pivot elsewhere in the infrastructure. By incorporating penetration testing in less common environments, you can close security gaps, proactively defending your critical data before a breach is even attempted.
Find out how other cybersecurity professionals are pen testing in their organizations
Read the 2024 Penetration Testing Report for more insights about the latest pen testing trends and challenges.