The PrintNightmare flaw is aptly named—the serious remote code execution vulnerability in the Microsoft Windows Print Spooler service, CVE-2021-34527, can give an attacker the keys to the kingdom. The Print Spooler service does not restrict access to the RpcAddPrinterDriverEx function, allowing a remote authenticated account with low privileges to gain access from a single shared computer. This provides a path for gaining system-level access, including a Windows Domain Controller and Active Directory. From there, an attacker can run arbitrary code, deploy malware, make new user accounts, as well as steal, alter, or delete any data.
Additionally, the vulnerability CVE-2021-1675 also applies to the Print Spooler service. This is a similar, but distinct remote code execution vulnerability that has a local attack vector. While Windows has released a patch, this update doesn’t protect against public exploits.
These vulnerabilities are dangerous enough that the Cybersecurity & Infrastructure Security Agency (CISA) issued an alert advising organizations to take action by downloading security updates and disabling the Print Spooler in Domain Controllers and for systems that do not print.
Luckily, Core Impact customers can be proactive in their response since they can effortlessly run a pen test to see if these vulnerabilities are present in their infrastructures. Our exploits team has rapidly created the Microsoft Windows Print Spooler PrintNightmare Remote Core Execution Exploit, which is now available in the latest release of Core Impact, version 21.1.
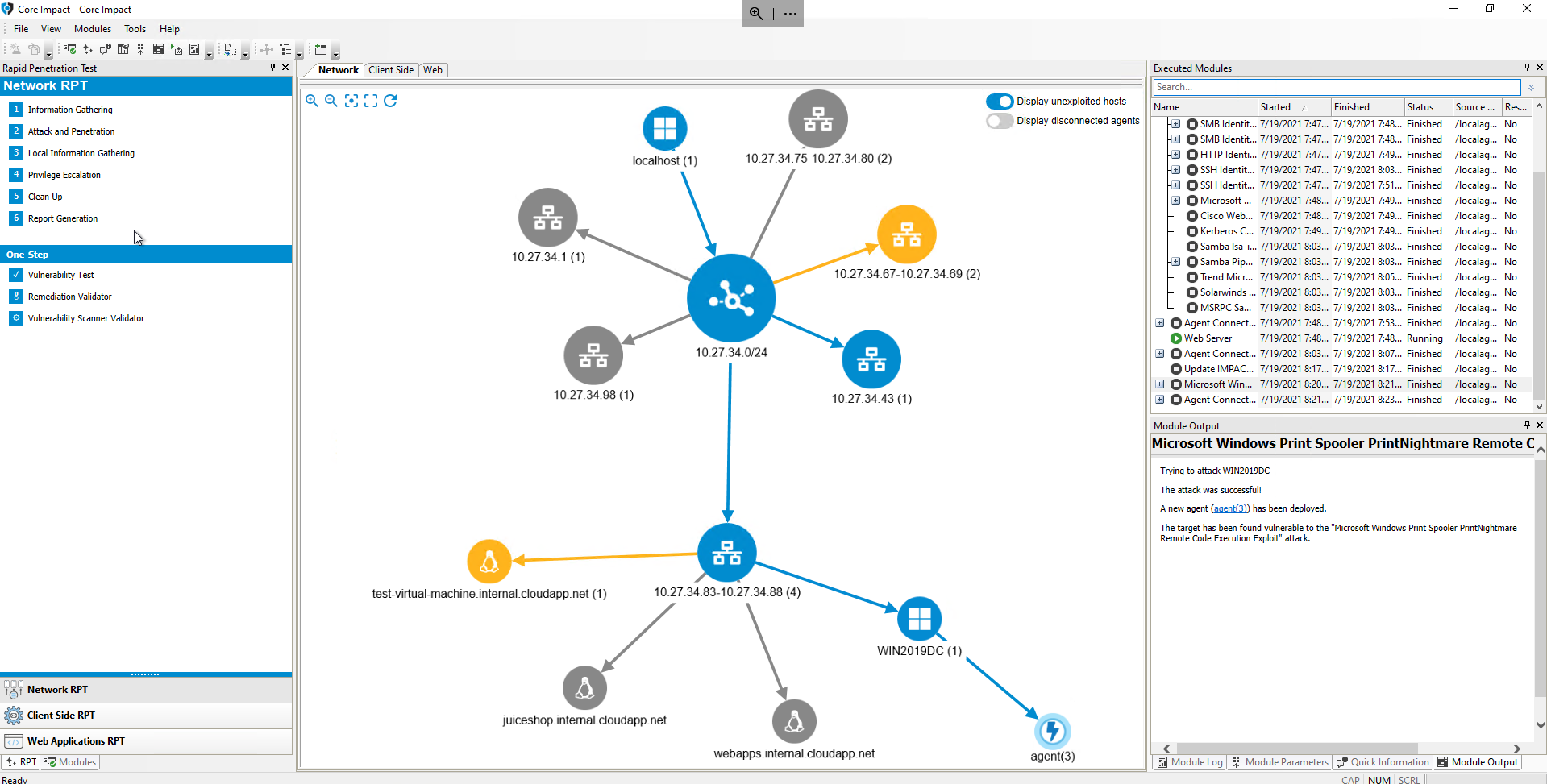
The PrintNightmare exploit being used in a Network Penetration Test on Core Impact
Core Impact’s commercial grade exploit library is regularly updated with new exploits written and tested by pen testing experts. Our exploits team works to swiftly create high value and reliable exploits that will benefit our customers and help them achieve their pen testing goals.
As mentioned earlier, a partial patch is available for CVE-2021-1675 and the latest security update will resolve CVE-2021-34527. There are workarounds available and, as advised by CISA, the option of selectively disabling the Print Spooler. However, workarounds may be incorrectly implemented and patches are not always properly applied—sometimes something as simple as failure to restart can mean that you’re still at risk. The best way to be sure that your IT environment is no longer at risk is to verify remediation efforts using Core Impact’s one-step remediation validator.
Stay Informed of New Core Certified Exploits
Subscribe to our weekly digest to receive regular updates on new exploits available for Core Impact.


