Core Impact
Penetration testing software to safely uncover and exploit security weaknesses
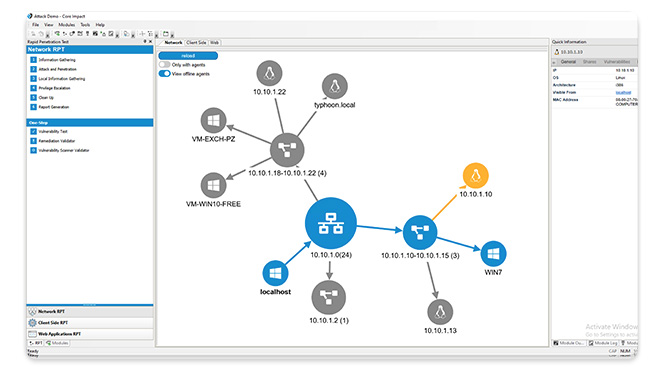
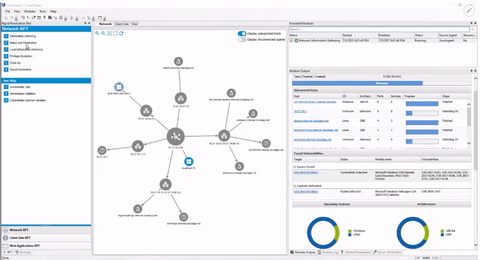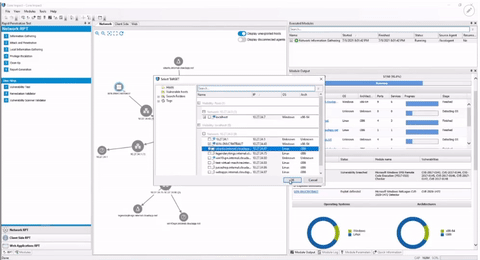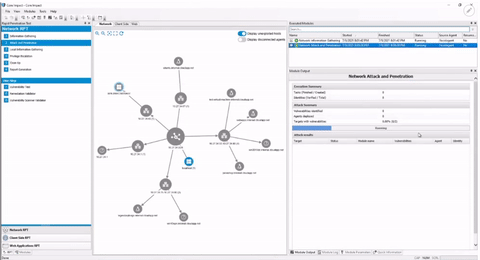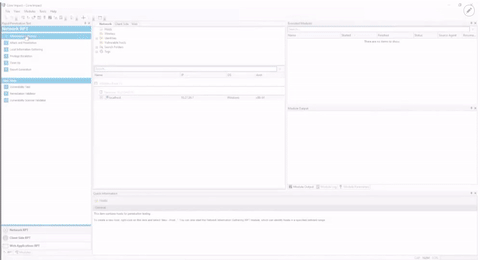
Core Impact is designed to enable security teams to conduct advanced penetration tests with ease. With guided automation and certified exploits, this powerful penetration testing software enables you to safely test your environment using the same techniques as today's attackers.
Replicate attacks across network infrastructure, endpoints, web, and applications to reveal exploited vulnerabilities, empowering you to immediately remediate risks.
Watch a Short Demo
Product Specifications
Platforms Monitored
Core Impact runs on Windows and helps you test the following types of platforms:
- Operating Systems like Windows, Linux, and Mac
- Cloud (Public, Private, Hybrid)
- Databases
- Web Services
- Network Appliances
- Software Applications
- Your Critical Data
Integrations
In order to further centralize your testing environment and increase the breadth of your program, Core Impact integrates with other security testing tools, including:
- Cobalt Strike
- Metasploit
- PowerShell Empire
- Plextrac
Vulnerability Scanner Integration
Core Impact can import data and validate vulnerabilities from multiple scanners, including:
Deployment Options
Core Impact runs on Windows with an integrated SQL database, physical or virtual system.
Product Bundles

Core Impact can be bundled with other offensive security solutions so that you can accelerate your security with centralized, interoperable tools. Craft a security tech stack tailored to your organization's unique needs - all at a discounted rate.
See Core Impact in Action
Conduct advanced penetration tests with ease and efficiency. See how Core Impact can streamline pen testing in your environment by requesting a free trial.
Find Out What Our Users Think: G2 Reviews

Core Impact is a top pen testing solution known for making pen testing accessible, optimizing the use of security resources with an intuitive interface, straightforward automations, and best in class support. Find out more about Core Impact’s strengths by seeing what our users have to say.
Read G2 reviews >
Ready to Begin Using Core Impact?
Explore our pricing page to learn what Core Impact Basic, Pro, and Enterprise have to offer and find the right version for your needs.