In the first series of this introduction to Linux and flash, we began with a basic lesson on flash memory. In part two, we can begin to tackle how Linux interacts with it. From this point forward, we’ll focus on NAND flash, with the following assumptions:
- It has large eraseblocks (several tens of KB).
- It has moderately sized programming pages (a couple of KB in size).
- It may have sub-pages (usually 512 bytes).
- It can only be programmed (change a one to zero) in page-sized (or subpage-sized) chunks.
- If a bit has to be changed from zero to one, it is necessary to erase and rewrite the whole eraseblock.
- Eraseblocks have a limited lifetime (in erase/program cycles).
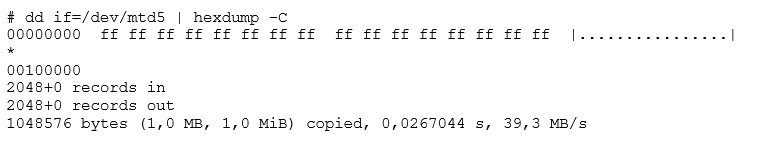
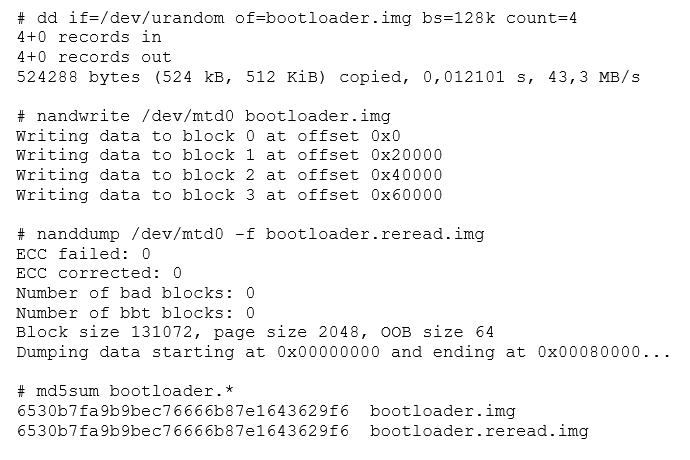
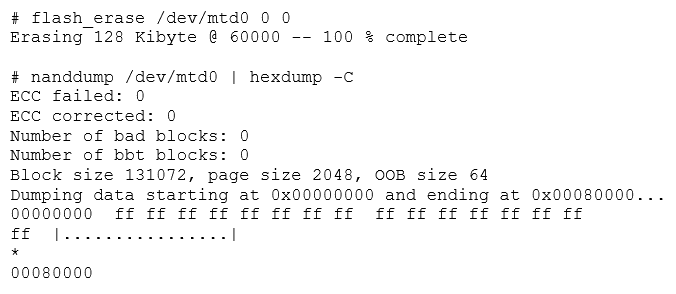
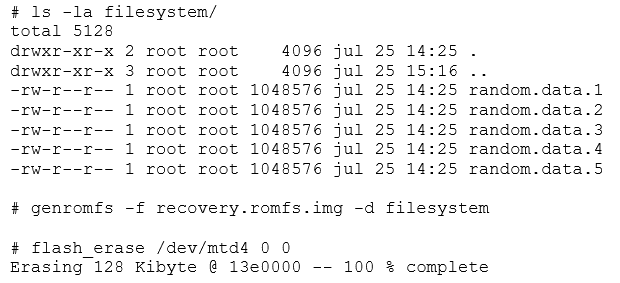
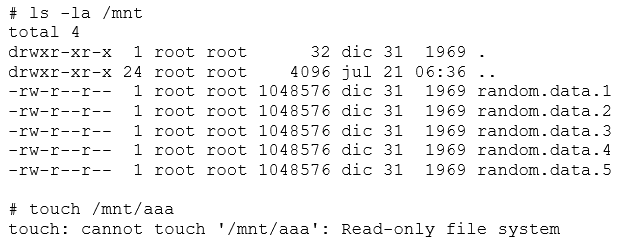
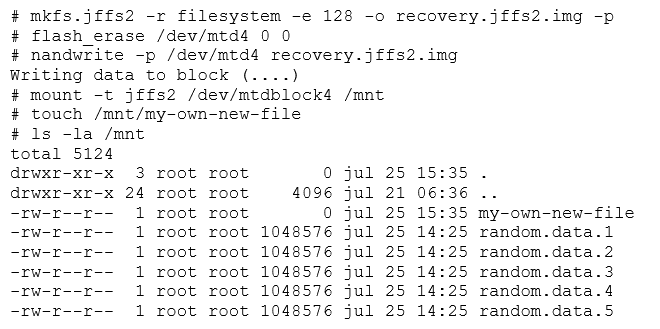
Additionally, Linux handles flash memory using the MTD modules. MTD is neither a block nor character device. Flash memory is handled in large eraseblocks, which can be erased and programmed as a whole. This poses certain difficulties in its handling. It is not possible to use traditional filesystems (like ext2), because flash does not provide a per-block (small sized randomly addressable) access. This means you are limited to erasing a full block, and cannot erase part of one.
Building a Basic Linux Flash Device
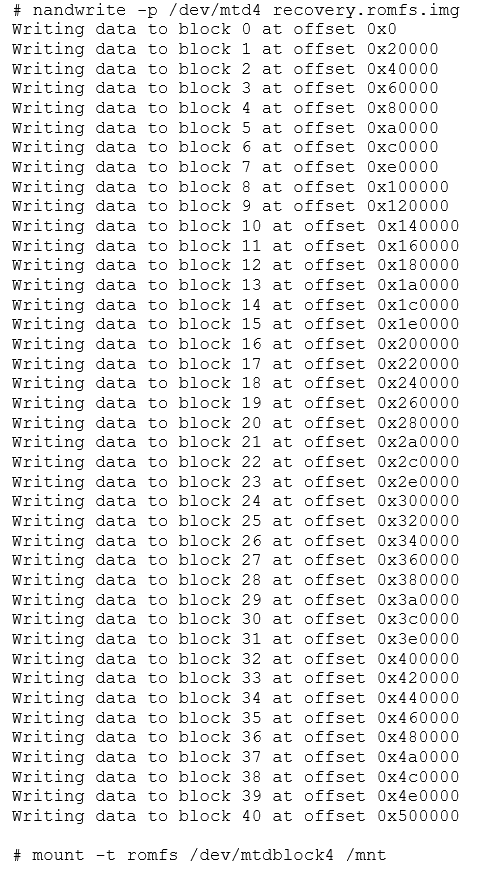
For this exercise, we'll use Linux's NAND simulator, a module that lets you repurpose a part of the RAM as if it were a flash device. This is very useful for testing and practicing. While this "flash" memory will be volatile, there won't have any problems with degradation and the simulator can be used anywhere Linux runs. Eventually, we'll learn to save our own images, so volatility won't be a problem.
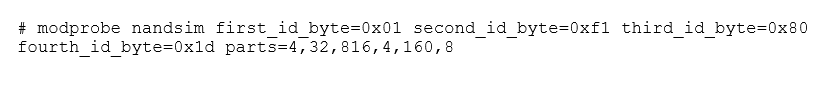
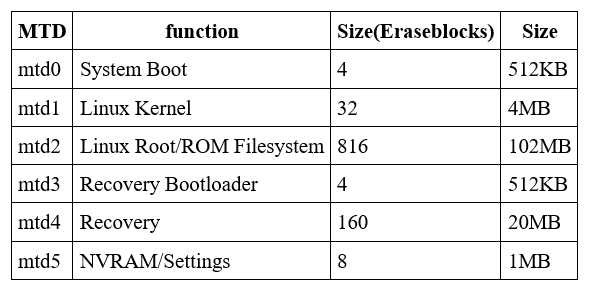
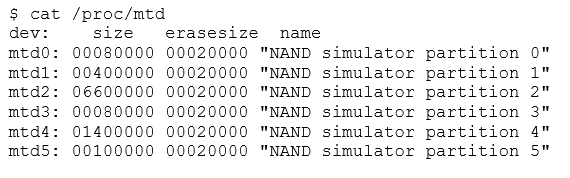
The NAND simulator can be activated by loading the "nandsim" module into the kernel. This can be done by running modprobe as root. In the example below, we're simulating a specific flash device.