During hardware-oriented engagements, we are sometimes faced with a hardware device's firmware image. This may happen because we downloaded a firmware upgrade image to try to understand a device with a view of finding security flaws, or we may find an unknown device and managed to obtain a flash dump using a security weakness. In any case, knowing how to handle these images can lead to a good understanding of how the device works, and in some cases to a way to get a shell in the device.
This article series will teach you the basics of Linux-based flash memory devices. After a few basic concepts, we'll create our own simulated flash device in part 2 to learn how things work. Once we understand how a device works and how to create one, we'll build on this knowledge and learn how to reverse engineer flash images.
Before getting into Linux, we’ll give a brief overview of how flash memory works. While not comprehensive, this explanation will give a rough idea on how it works for a solid jumping off point.
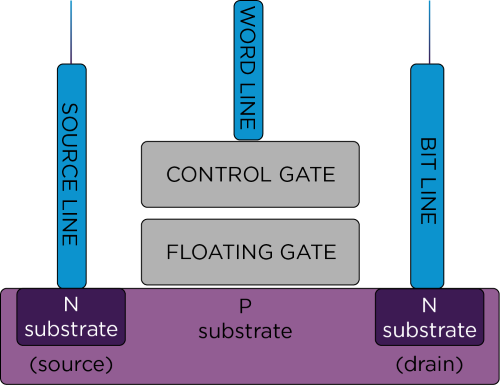
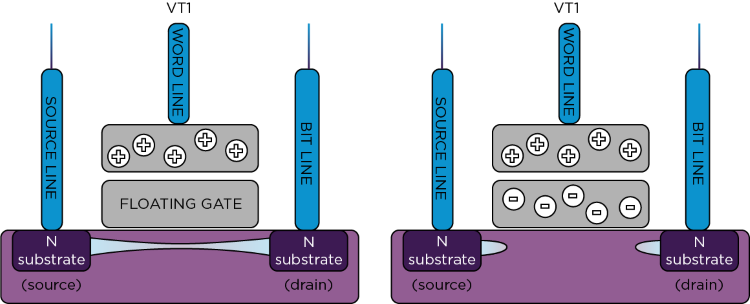
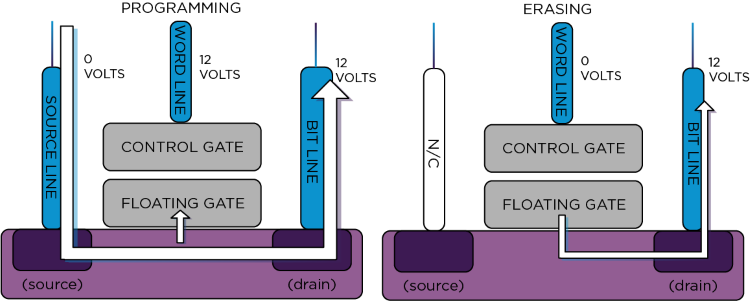
Let's start with how a one-bit flash memory cell works. Flash memory is a type of non-volatile memory composed of cells similar to a field-effect transistor (FET). Each cell can be made to conduct by providing a voltage to a control gate, like an FET, by opening a conducting channel into the substrate. However, unlike a regular FET, the control gate also has a floating part (a part that is not connected to anything), which is how the cell is able to retain data.
Image 1: Flash memory cell