How to Deal with Microsoft Monthly Updates to Reverse Engineer Binary Patches
The new format of Microsoft monthly updates have proven challenging to reverse engineer. We’ve figured out a workaround that we hope will be helpful.
In the original format, the Microsoft updates have always included the full files to patch, and from there it’s relatively straightforward to work on reversing and diffing through only extracting, without installing the patch.
Sometimes the patch cannot be applied, and we get an error when attempting to do so. Other times, the machine has multiple updates piled up, so the update server takes days to complete the process.
If we can get the full files we can start reversing and diffing while the computer updates. Sometimes we just need to apply the update of the vulnerable version to test an exploit and the patched version is just for diffing.
Whatever the reason, you may need the complete file that the actual update is no longer providing. The following tutorial provides a way so you can still access it if you need to.
For this example, we’ll use the update on NTFS.sys. The December 2020 update is the patched version and the November 2020 update is the vulnerable version.
Let’s first download the patched version.
There are two methods for unzipping the MSU. First, let’s go over the traditional way:
expand -F:* update.msu C:<target_dir>* cd <target_dir> expand -F:* update.cab C:<target_dir>
So in this example, it would be:
expand -f:* a.msu "C:\Users\ricnar\Desktop\New folder"
The second method is by using a PowerShell script named PatchExtract.Ps1.
The command to unzip using this script is:
Powershell -ExecutionPolicy Bypass -File PatchExtract.ps1 -Patch a.msu
Results have been tailored for more reliable reading:
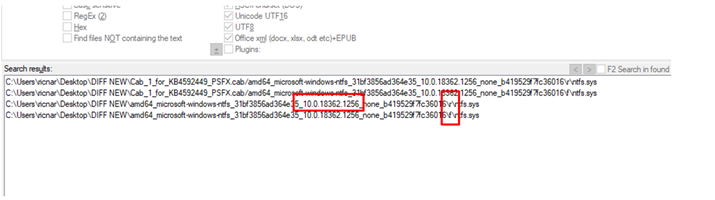
We will get two ntfs.sys files. However, if we look closely, we can see that something is wrong. The size is very small compared to the other ntfs.sys and if we open it in a hexadecimal editor, we can see this:
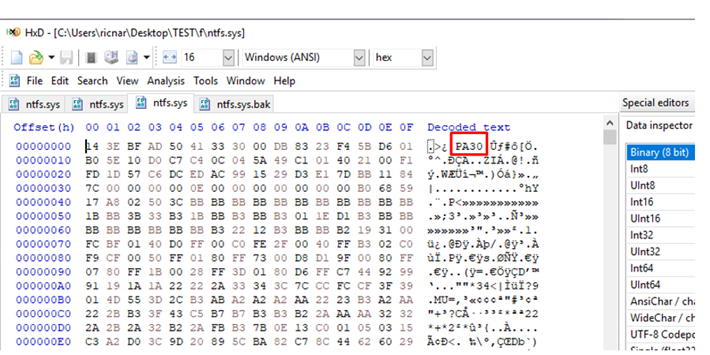
This is not a PE FILE, it is actually a DELTA format used by Microsoft to distribute only a patch, but not the entire file.
The two patch files are inside folders named r and f (forward and reverse patches).
We need to use a script, known as delta_patch.py, to build the complete file from this deltas.
First, we need to search the target machine for the old f, r, and base files using the following PowerShell command:
Get-ChildItem -Recurse C:\windows\WinSxS\ | ? {$_.Name -eq "ntfs.sys"}This allows us to obtain two sets of old f, r, and base. These will always be stored because they are necessary to apply the Delta patches by the same Microsoft updates.
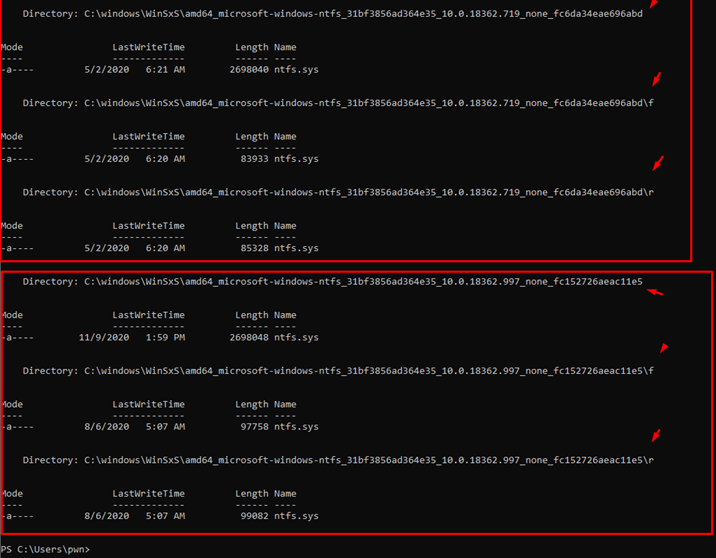
Let’s select the newest one and assume that these Microsoft update problems and errors are caused by very old, stored base files.
We'll then copy the newest set to a work folder:
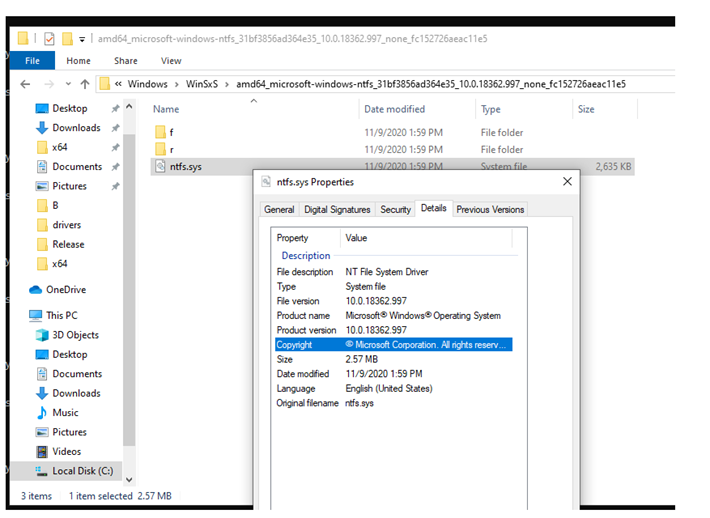
This set has a complete base binary file version 10.0.18362, as well as the r and f folder with their delta patches inside.
Next, we'll copy the delta_patch.py script to this folder:
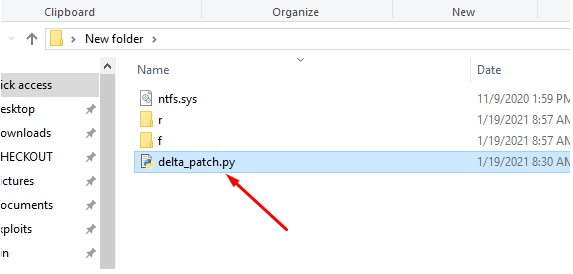
Since we have an old version and have to patch it to get a newer one, we have to use the f file (to move forward) from the December patch and replace only the f file of the chosen set, leaving the original base and r.
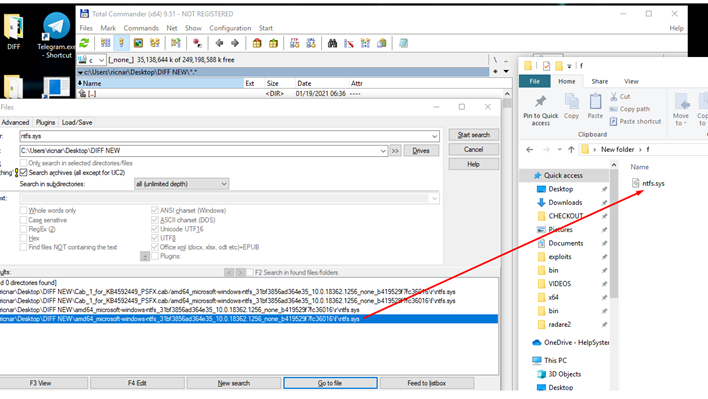
We’ll next replace the ntfs.sys from the set's f folder, with the ntfs.sys from the December update’s f folder.
Then, we’ll open a CMD on the work folder using this command:
python delta_patch.py -i ntfs.sys -o ntfsnew.sys .\r\ntfs.sys .\f\ntfs.sys
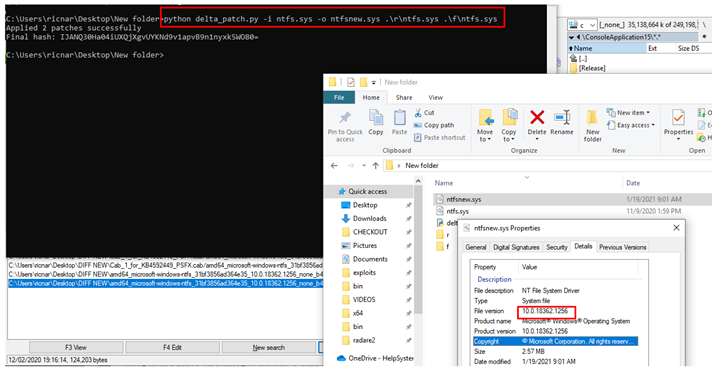
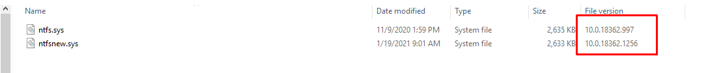
This will allow us to rebuild the December FULL BINARY FILE version 10.0.18362.1256.
If we want the vulnerable version, as seen above, but don't know the exact patch that contains it, we can use this page:
https://ovaldb.altx-soft.ru/Search.aspx
If you register, you'll have full search capabilities. Playing with the field comment, we can get the filters applied in each update:

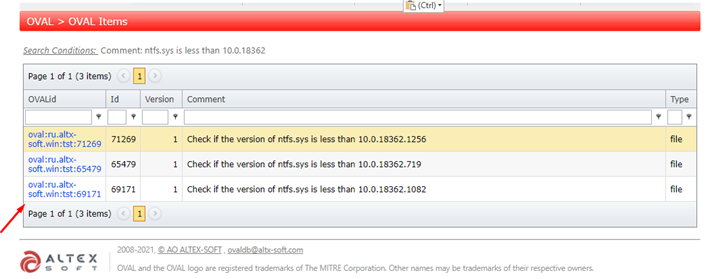
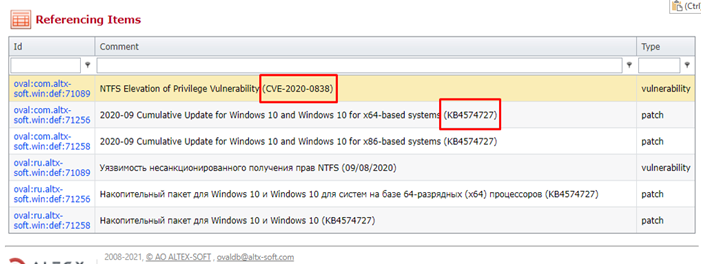
We can also get the CVE and KB of the previous patch.
The previous patch in this example is from November 2020, and has the f and r folder with its deltas inside.
We’ll replace working folder the other version f with this f and apply. the script again. This gets us the complete file for November:
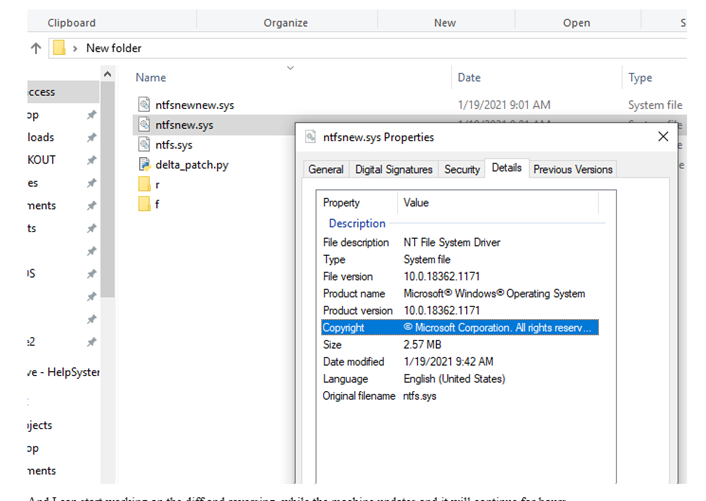
And we can now start working on the diff and reversing, while the machine updates continuously for hours.
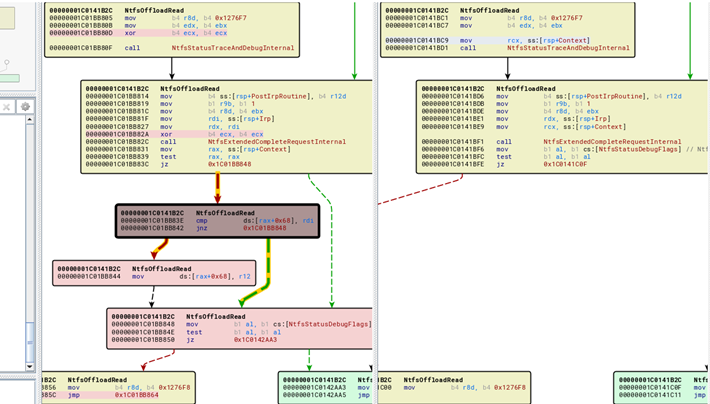
While this does take some effort, it does allow you to get the information you need, despite the new update method.
Want to learn more reversing techniques?
Check out our ongoing series, Reversing and Exploiting with Free Tools.


