Empty grocery shelves can be caused by natural disasters, wars, and trade embargoes, as we’ve seen in recent years. But they can also be the result of successful cyberattacks, which could be more preventable than the other three agents of chaos.
Whether a company sells computer chips or potato chips, if the logistics of production, distribution, or sale are disrupted, shelves will remain empty and consumers without needed supplies. In 2024, both major grocery suppliers and supply management vendors were successfully attacked by malicious actors, causing widespread shortages in meat, poultry, and produce, among other items. While Metropolitan areas were hit hard, rural areas suffered even more greatly, as they often do when the supply chain is interrupted.
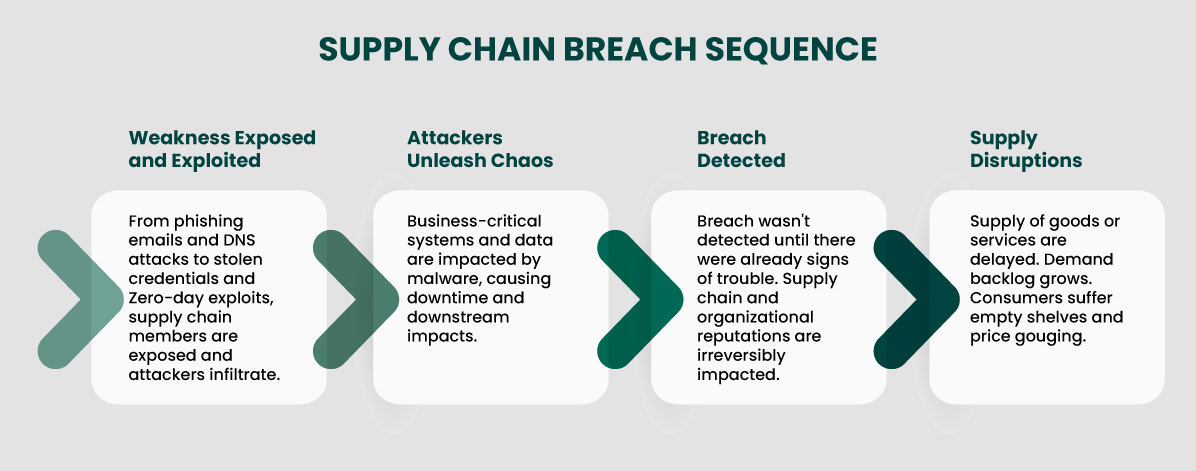
From an offensive security perspective, these real-world effects are the predictable outcome of modern adversaries weaponizing the retail supply chain to create disruption, using tactics like phishing, lateral movement from vendors, software supply chain poisoning, and ransomware.
Supply Chain Weak Points
Three years ago, Gartner predicted that by 2025, 45% of all organizations would have experienced an attack on their software supply chain. Software supply chain issues are just one of the many ways modern adversaries weaponize the retail supply chain and force physical consequences in the “real world.” Other tactics include:
-
Phishing: Malicious emails get sent to supply chain partners. Even employee security awareness training or advanced email cloud security solutions can’t weed out every attack. It only takes one errant click from a distracted employee to give malicious actors an entry.
-
Lateral movement: Once initial access has been gained (via a software bug, clicked phishing link, stolen credential, weak configurations or controls etc.) the attacker moves laterally from the third-party to the upstream organization itself.
-
Ransomware: Once inside the upstream organization (having pivoted from the supply chain partner), ransomware payloads can be dropped and detonated.
This diagram shows a bit more detail in how a supply chain cyberattack could develop and at what stages offensive security measures like red teaming and penetration testing can stop the attack in its path.
Mitigations That Disrupt Adversarial Tactics
Mitigating subversive supply chain attacks means breaking the attack chain at its earliest stages. For example:
-
Vulnerability management can prevent success at even Stage One: Reconnaissance. As attackers look for open vulnerabilities, a good VM program can ensure you find them first and patch them before they become exploited entry points.
-
Penetration testing tests whether those found vulnerabilities are exploitable, stopping the fourth stage of the cyber kill chain: Exploitation. This tells teams where to focus their efforts, and which CVEs are not in dire need of attention. And while prioritizing CVEs is a start, a good pen tester armed with the right software can do so much more.
-
Red teaming goes above and beyond what even pen testing can do by subjecting architectures and defensive measures to the stresses of a real-world attack. Advanced adversary simulation can range from phishing tactics to executive impersonation to APTs, polymorphic malware and more. By testing an organization’s defenses with the best tactics a real-world adversary can offer, retailers can be sure they are more than ready to handle opportunistic threats that come their way.
According to the CISO Benchmark Report by RS-ISAC, a cybersecurity community focused on retail and hospitality, supply chain attacks were the second-most cited cyber risk for CISOs out of a lineup of 350 total risks.
Retailers have two choices: they can either wait around to be surprised when attacks come through their third-party suppliers (the defensive security approach), or they can test themselves with aggressive pen testing and red teaming to find those weak spots ahead of time (the offensive, or “proactive,” security approach).
Why Retailers Must Think Like Attackers
Retailers’ security teams must think like opportunistic cybercriminals to avoid a false sense of security. Adversaries hunt retailers for their large swaths of sensitive data, their financial viability, and the fact that many don’t realize how vulnerable their third parties make them. By understanding these draws and mitigating creative – and often simplistic – techniques with regular offensive security, retailers can keep the proverbial shelves stocked and keep supply chain threats at bay.
Offensive security tools like Core Impact, Cobalt Strike, and Outflank Security Tooling enable penetration testers and red teamers to perform advanced engagements with precision, efficiency and safety.
Arming your teams with these best-in-class tools which are even more powerful when used together. Explore our offensive security bundle offerings.
Bundle Solutions for Maximum Coverage
Our Offensive Security Bundles streamline multiple layers of complexity to create a mature security program and ensure your organization can prevent successful cyberattacks.

