Core Impact Updates
NTMLrelayx MultiRelay and Keep-Relaying Support
The latest update to Impacket 0.12 introduces the MultiRelay and keep-relaying modes, allowing users to run relays for extended periods and analyze captured connections for each target. The NTLMrelayx module will continuously relay new incoming connections until manually stopped. This feature, combined with the Connection Store released in Core Impact 21.6, gives operators full control over relayed connections.
Improved Module Output for Exploits
With the aim of providing more visibility to the operators for the actions performed in the target systems, we have improved the way the module output is displayed. More information is now provided on the steps performed by the exploits launched during an attack.
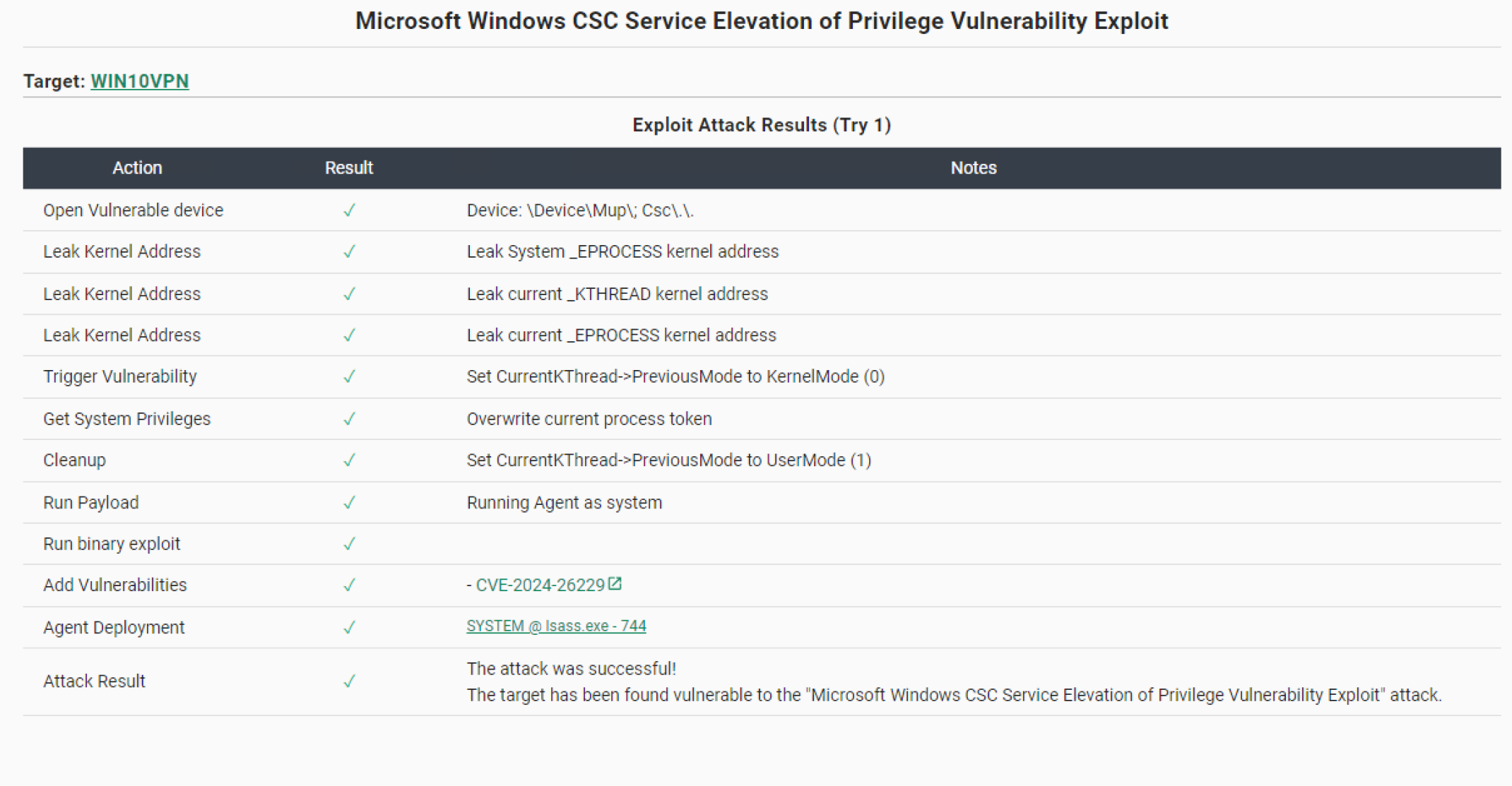
Core Impact Exploit Library Additions
One of Core Impact’s most valuable features is its certified exploit library. Fortra’s Core Security has a team of expert exploit writers that conduct research, evaluating and prioritizing the most relevant vulnerabilities in order to update the library with critical and useful exploits. Additionally, the QA team creates its own clean environment to validate each exploit before its release to ensure our standards and validate that it is safe and ready to use.
While you can keep track of new releases through our exploit mailing list, here is a more detailed summary of some of the most recent additions to the library.
CVE-2024-6769 - Windows System Drive Remapping Local Privilege Escalation Exploit Update
Authors: Ricardo Narvaja and Daniel De Luca (QA)
CVSS: 6.7 MEDIUM
Reference:
- CVE-2024-30051
- Fortra Advisory fr-2024-002 (Full details available in functional PoC from Core Labs)
Key Vulnerability Details
- Improper handling of drive remapping and activation contexts could enable escalation to full SYSTEM privileges
- Affects multiple versions of Windows 10, Windows 11, and Windows Server 2016, 2019, and 2022
- Classified as an Untrusted Search Path (CWE-426)
Exploitation Impact and Mitigation
- Authenticated user with medium privileges could escalate to SYSTEM level privileges
- Could lead to full compromise, with ability to access, manipulate, exfiltrate, or delete sensitive data
- No patch is currently available
Attacks in the Wild
- No major attacks have been reported at this time
Exploitation Mechanism
- First Stage:
This bug is a DLL Hijacking caused by the Drive Remapping of ROOT drive, allowing a MEDIUM INTEGRITY process to be elevated to limited HIGH PRIVILEGES, but without reach the complete privileges to be full Administrator. - If the user belongs to the Local Administrators Group, it continues copying the necessary files to perform the exploitation, MsCtfMonitor.dll to the same folder when the agent runs, TAPI32.Manifest and imm32.dll containing the Impact agent to be deployed, are copied to system32\Tasks too.
- After that, It executes in memory the file sploit.obj that is the executable BOF to perform the first stage, which remaps the ROOT Drive using the NtCreateSymbolicLinkObject function, with that some Services are affected and will attempt to load libraries from the new fake user-controlled system32, in our case CTFMON tries to load the crafted MsCtfMonitor.dll from our fake controlled system32 folder, created by the BOF after remap, next, its DoMsCtfMonitor function is called and executes our code with HIGH INTEGRITY LEVEL with non Administrator privileges.
- Second Stage:
- MsCtfMonitor.dll, has the code to perform the Second Stage, it performs Activation Cache Poisoning registering the crafted TAPI32.Manifest placed in system32\Tasks for TAPI32.dll, After that executing tcmsetup.exe it loads tapi32.dll, and the fake manifest added to the Activation Cache loads the imm32.dll with the second phase Impact Agent to elevate to HIGH with full Administrator privileges.
- Additionally, a module to elevate from Administrator to System can be run as a post-exploitation module (disabled by default in Options).
CVE-2024-36401 - GeoServer Unauthenticated Remote Code Execution Exploit
Authors: Lucas Dominikow and Luis García Sierra (QA)
CVSS: 9.8 CRITICAL
Reference: CVE-2024-36401
Key Vulnerability Details
- Flaw exists in how the GeoTools library API processes property names and allows execution of arbitrary code when evaluating X-path expressions
- Enables Remote Code Execution through specially crafted input against request parameters in Open Geospatial Consortium (OGC)
- Affects versions of GeoServer prior to 2.23.6, 2.24.4, and 2.25.2
- Classified as Improper Control of Generation of Code (CWE-94)
Exploitation Impact and Mitigation
- Unauthenticated attackers can run malicious code on impacted systems
- May lead to full system compromise and access to sensitive data
- Patches have been issued for affected versions and a new release is also available
Attacks in the Wild
- Actively being exploited since July 2024
- Has been added to CISA’s Known Exploited Vulnerabilites Catalog
- Leveraged to propagate Linux backdoor, Sidewalk
- Exploited to deliver reverse proxy server GOREVERSE
- Used as a conduit for Mirai botnet variant, JenX
Exploitation Mechanism
1. Exploit deploys a malicious OGC request parameter.
2. Parameter is processed by GeoServer, triggering the vulnerable API.
3. Expression is processed by the commons-jxpath library.
4. Operator can then deploy an agent.
CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, CVE-2024-47177 - Linux OpenPrinting CUPS-Browsed Remote Code Execution Exploit Chain
Authors: Marcos Accossatto, Arthur Lallemant (QA), and Daniel De Luca (QA)
CVSS: 5.3 MEDIUM , 8.6 HIGH, 8.6 HIGH, 9.0 CRITICAL
Reference: CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, CVE-2024-47177
Key Vulnerability Details
- CVE-2024-47176- Service binds to INADDR_ANY:631, causing it to trust and accept packets from any source
- CVE-2024-47076- Allows processing of invalid and unsanitized IPP attributes, which can lead to attacker-controlled data being used in the CUPS system
- CVE-2024-47175- Permits processing of unsanitized IPP attributes before they are written to a PPD file, enabling injection of malicious data
- CVE-2024-47177- Flaw in the `FoomaticRIPCommandLine` parameter of the cups-filters library allows execution of arbitrary commands
- When chained together, can result in full remote code execution
- CVE-2024-47176 provides initial access through UDP 631, CVE-2024-47076 allows for distribution of malicious printer attributes, CVE-2024-47175 permits PPD file creation, and CVE-2024-47177 enables code execution via foomatic-rip
- Affects all versions of Common Linux Printing System (CUPS) up to 2.01 running and listening on UDP port 631
- Classified as Binding to an Unrestricted IP Address (CWE-1327), Improper Input Validation (CWE-20), and Improper Neutralization of Special Elements used in a Command (CWE-77)
Exploitation Impact and Mitigation
- Attackers can deploy malicious payloads, escalate privileges, and establish persistence
- Can lead to full system compromise
- Multiple Linux distributions have released patches and updates, including Ubuntu, Red Hat, and Debian
Attacks in the Wild
- No major attacks have been reported at this time
Exploitation Mechanism
- Exploit module starts a fake IPP Server that will be used to deliver the payload to exploit the last three vulnerabilities. This will create a fake printer on the system.
- Module sends a packet to the target to exploit the first vulnerability.
- The attack chain is triggered by sending an HTTP request to the CUPS Management Interface to print a test page on the fake printer.
- This request executes the commands that will deploy the agent.
CVE-2024-38054 - Microsoft Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability Exploit
Authors: Cristian Rubio and Arthur Lallemant (QA)
CVSS: 7.8 HIGH
Reference: CVE-2024-38054
Key Vulnerability Details
- A heap-based buffer overflow within the Service Driver can be triggered through malicious input and enable writing beyond allocated buffer boundaries
- Boundary error within the Service Driver can lead to SYSTEM level access and arbitrary memory write
- Affects multiple versions of Windows 10, Windows 11, and Windows Server 2008-2022
- Classified as an Out-of-Bounds Write (CWE-787) and Heap-Based Buffer Overflow (CWE-122)
Exploitation Impact and Mitigation
- Attackers can escalate privileges from a basic user to full SYSTEM access
- May lead to corruption or exfiltration of sensitive data
- Microsoft released a patch for this vulnerability in a July Security Update
Attacks in the Wild
- No major attacks have been reported at this time
Exploitation Mechanism
- Exploit sprays the memory with data queue entries.
- This triggers the OOB write to overwrite the target entry.
- Exploit leaks adjacent pool memory and bypasses KASLR.
- It then forges a data queue entry to get an arbitrary memory read.
- This allows for the leak of the address of the current process token and the address of the SYSTEM process token.
- A new data queue entry is created to leak its IRP.
- The IRP and the data queue entry are then forged.
- SYSTEM privileges can then be attained by reading one byte to trigger the arbitrary write
CVE-2024-26230 - Microsoft Windows Telephony Server Use After Free Local Privilege Escalation Exploit
Authors: Ricardo Narvaja and Luis García Sierra (QA)
CVSS: 7.8 HIGH
Reference: CVE-2024-26320
Key Vulnerability Details
- Elevation of privilege vulnerability can lead to SYSTEM level access
- Affects multiple versions of Windows 10, Windows 11, and Windows Server 2008-2016
- Vulnerability in ClientRequest function of Telephony Service
- Service does not verify objects with “GOLD” magic value are owned by the context handle before freeing them
- A secondary context handle can claim ownership, leaving a dangling pointer and user-after-free vulnerability
- Classified as Use After Free (CWE-416)
Exploitation Impact and Mitigation
- Attackers can escalate privileges to full SYSTEM level
- May lead to complete compromise of targeted systems and access to sensitive data
- Microsoft released a patch for this vulnerability in a April Security Update
Attacks in the Wild
- No major attacks have been reported at this time
Exploitation Mechanism
- Discover an exploit primitive.
- Perform heap feng shui to come up with a memory layout.
- Allocate enough "GOLD" objects using the GetUIDllName function.
- Free some of them to create some holes using the FreeDiagInstance function.
- Allocate a worker "GOLD" object to trigger the use-after-free vulnerability.
- Delete the "RequestMakeCall" key value and create a REG_BINARY type key with controlled. content. Then, I allocate some key value heaps to ensure they occupy the hole left by the worker object.
- XFG mitigation.
CVE-2024-0799, CVE-2024-0800 - Arcserve Unified Data Protection wizardLogin Authentication Bypass Vulnerability Remote Code Execution Exploit Chain
Authors: Marcos Accossatto and Luis García Sierra (QA)
CVSS: 9.8 CRITICAL, 8.8 HIGH
Reference: CVE-2024-0799, CVE-2024-0800
Key Vulnerability Details
- CVE-2024-0799 provides initial access by exploiting UUID validation flaw to bypass authentication
- CVE-2024-0800 uses authenticated session to exploit path traversal vulnerability and upload files
- When chained together, can result in arbitrary file uploads
- Affects all Arcserve UDP 8.1 and 9.2
- Classified as Improper Authentication (CWE-287) and Unrestricted Upload of File with Dangerous Type (CWE-434)
Exploitation Impact and Mitigation
- Unauthenticated attackers can upload malicious files with SYSTEM user privileges
- May lead to data compromise, exfiltration, or corruption
- Patches for both versions have been released
Attacks in the Wild
- No major attacks have been reported at this time
Exploitation Mechanism
- Exploit module uses the first vulnerability to authenticate against the target application using a POST HTTP request to the /management/wizardLogin endpoint.
- This provides a random username and no password parameter.
- It will then use the second vulnerability to upload a JSP file to the Program Files/Arcserve/Unified Data Protection/Management/TOMCAT/webapps/management directory.
- Lastly, it will deploy an agent using a GET HTTP request to the uploaded JSP file inside the /management endpoint.


