We’re excited to announce the release of Core Impact 21.7, packed with powerful new features, thoughtful enhancements, and critical fixes that further solidify Core Impact as a go-to solution for penetration testers.
This update focuses on extending agent customization options, improving integration with external tools, and optimizing the overall user experience.
Agent Transformations
This new feature provides operators with the ability to customize the Core Impact agent generation process through configuration of specific processing functions.
You can now enhance the effectiveness of your payloads by applying obfuscation techniques or tailoring the implant loader to better suit your operational needs.
When deploying agents, modules request a specific artifact based on the target’s configuration and defined parameters—such as the connection method or port. Core Impact first generates shellcode tailored to those settings. Depending on the exploit or module, that shellcode may then be wrapped into a different format, such as an executable, a library, or a raw payload.
To support customization at key stages of this process, Core Impact introduces two defined hook points:
Shellcode Transformations: Customize shellcode during generation
Binary Transformations: Modify the final wrapped artifact
The provided workflow is as follows:
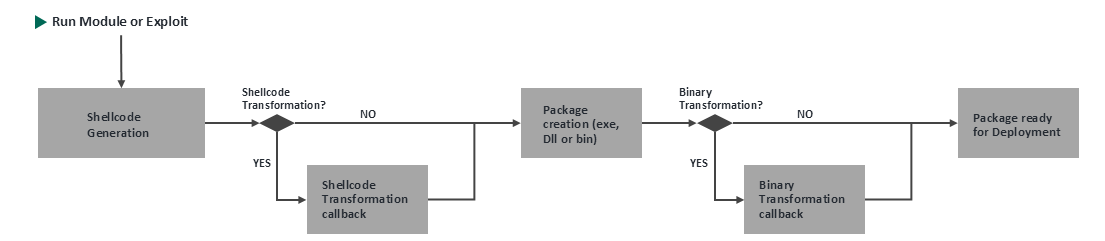
Some callback examples are provided in the product documentation.
Artifact Signing
Core Impact 21.7 introduces the ability to digitally sign generated artifacts and agents, such as executables and DLLs, using custom certificates.
This powerful feature supports two key use cases:
Evading security controls: Leverage trusted signatures to bypass defensive mechanisms
Enhancing operational stealth: Operators can pre-register certificates in EDR exclusion lists, effectively avoiding detection and blocking by strict Attack Surface Reduction (ASR) rules.
For example, in environments using Microsoft Defender for Endpoint, you can add the signing certificate to the Defender Exclusions via PowerShell or Group Policy using the "Path Exclusions" or "Certificate-based ASR Exclusions." This prevents signed payloads from being flagged or blocked by Defender's Attack Surface Reduction rules, enabling smoother execution of implants during controlled engagements.
Quality of Life Updates
New UI for Some Run Module Dialogs: New Host, New Scenario, New Identitie(s), and Exposure Finder.
Native Bloodhound integration: You can now seamlessly connect Core Impact to BloodHound using its native API, making it easier to visualize and exploit Active Directory relationships within your engagement workflows.
SQL Server Upgrade: Core Impact now includes SQL Server 2022 (upgraded from 2014), providing performance, scalability, and security improvements right out of the box.
Final Thoughts
Core Impact 21.7 is a significant step forward in flexibility, usability, and ecosystem integration.
Update now and elevate your testing capabilities with the latest that Core Impact has to offer.
To see a full list of what’s new in Core Impact 21.7, please check out the release notes.
Interested in Core Impact?
See Core Impact's features in action in this 30 minute on-demand demo.



