You think that you're safe, that your network is secure, that your firewalls are protecting you...but how will you know if you don't test it?
A penetration test, or pen test, is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. You may have also hear the term "Red Hat" or "White Hat" when it comes to testing because, while they are trying to hack into your system, these "attackers" are doing so in an ethical effort to find the vulnerable parts of your network in order to patch them. There are many options for penetration testing - either manual or automated, a pen test systematically compromises servers, endpoints, web applications, wireless networks, network devices, mobile devices, and other points of exposure. With so many things to test and so many options for testing, how do you know if you're getting the most out of your test?
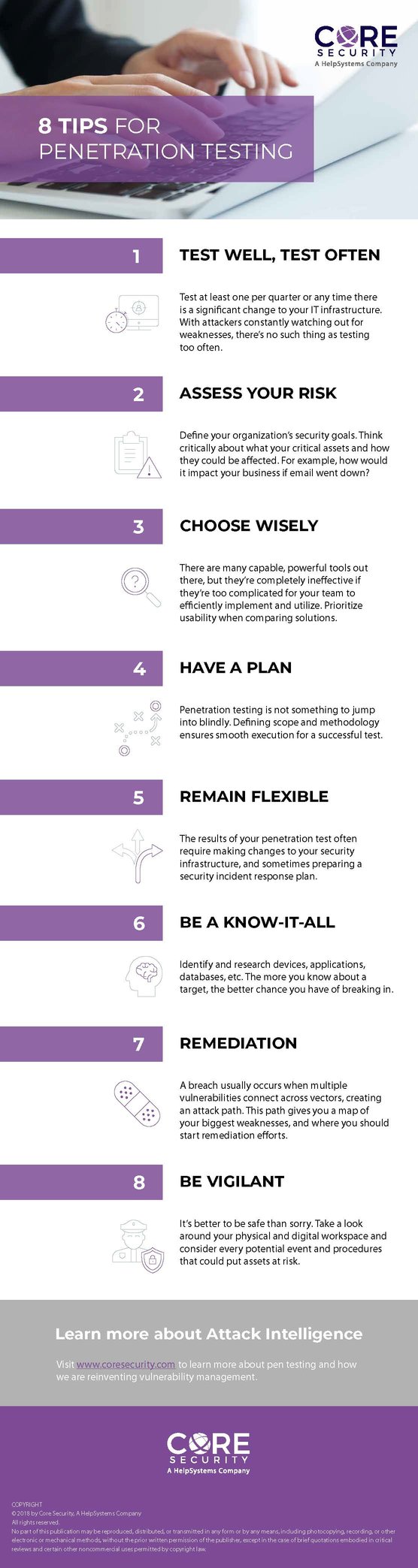
Here are 8 tips for penetration testing:
1. Test well, test often
Test at least once per quarter or any time there is a significant change to your IT infrastructure. With attackers constantly watching out for weaknesses, there’s no such thing as testing too often.
2. Assess your risk
Define your organization’s security goals. Think critically about what your critical assets are and how they could be affected. For example, how would it impact your business if email went down?
3. Choose wisely
There are many capable, powerful tools out there, but they’re completely ineffective if they’re too complicated for your team to efficiently implement and utilize. Prioritize usability when comparing solutions.
4. Have a plan
Penetration testing is not something to jump into blindly. Defining scope and methodology ensures smooth execution for a successful test.
5. Remain flexible
The results of your penetration test often require making changes to your security infrastructure, and sometimes preparing a security incident response plan.
6. Be a know-it-all
Identify and research devices, applications, databases, etc. The more you know about a target, the better chance you have of breaking in.
7. Remediation
A breach usually occurs when multiple vulnerabilities connect across vectors, creating an attack path. This path gives you a map of your biggest weaknesses, and where you should start remediation efforts.
8. Be vigilant
It’s better to be safe than sorry. Take a look around your physical and digital workspace and consider every potential event and procedures that could put assets at risk.
View these pen testing tips as an infographic:
Download the annual "Pen Test Report"
A comprehensive survey of more than 800 individuals on pen testing, focusing on the strengths, needs, and challenges of pen testing, and the role it plays across organizations.