Demonstrates how to use the Core Impact Windows Secrets Dump module and CloudCyper to gather and crack hashes.
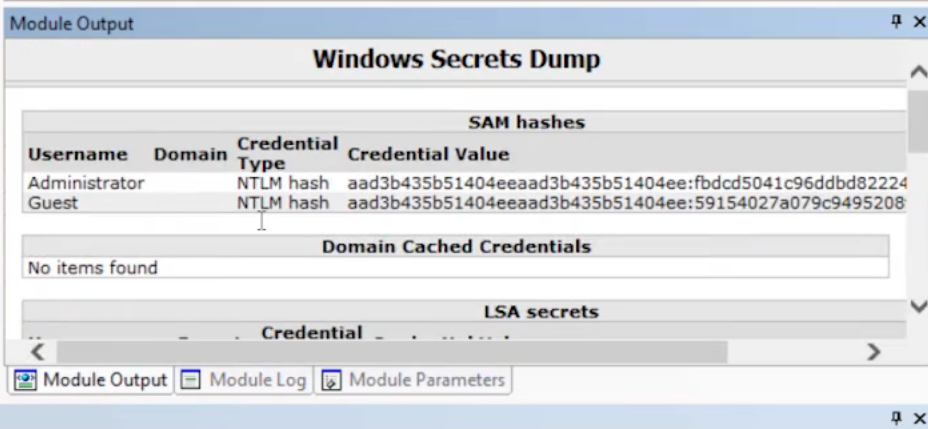
In a previous exercise, we used Mimikatz to gather 17 identities. We’ll now use the Windows Secret Dump module to see if we can gather even more identities. This module dumps any available SAM hashes, LSA secrets, Domain Cached hashes, and Domain credentials (NTDS hashes) from a target system.
Click on the “Hosts” folder on the Network tab. We still have an active agent on the Vagrant box, agent(0).
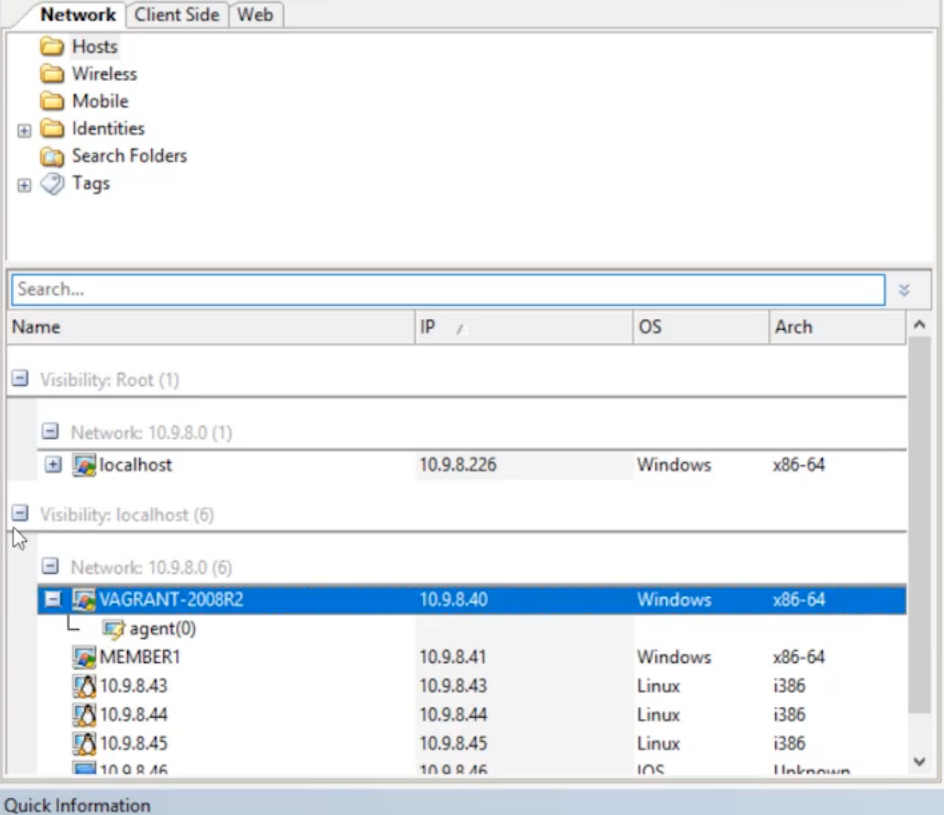
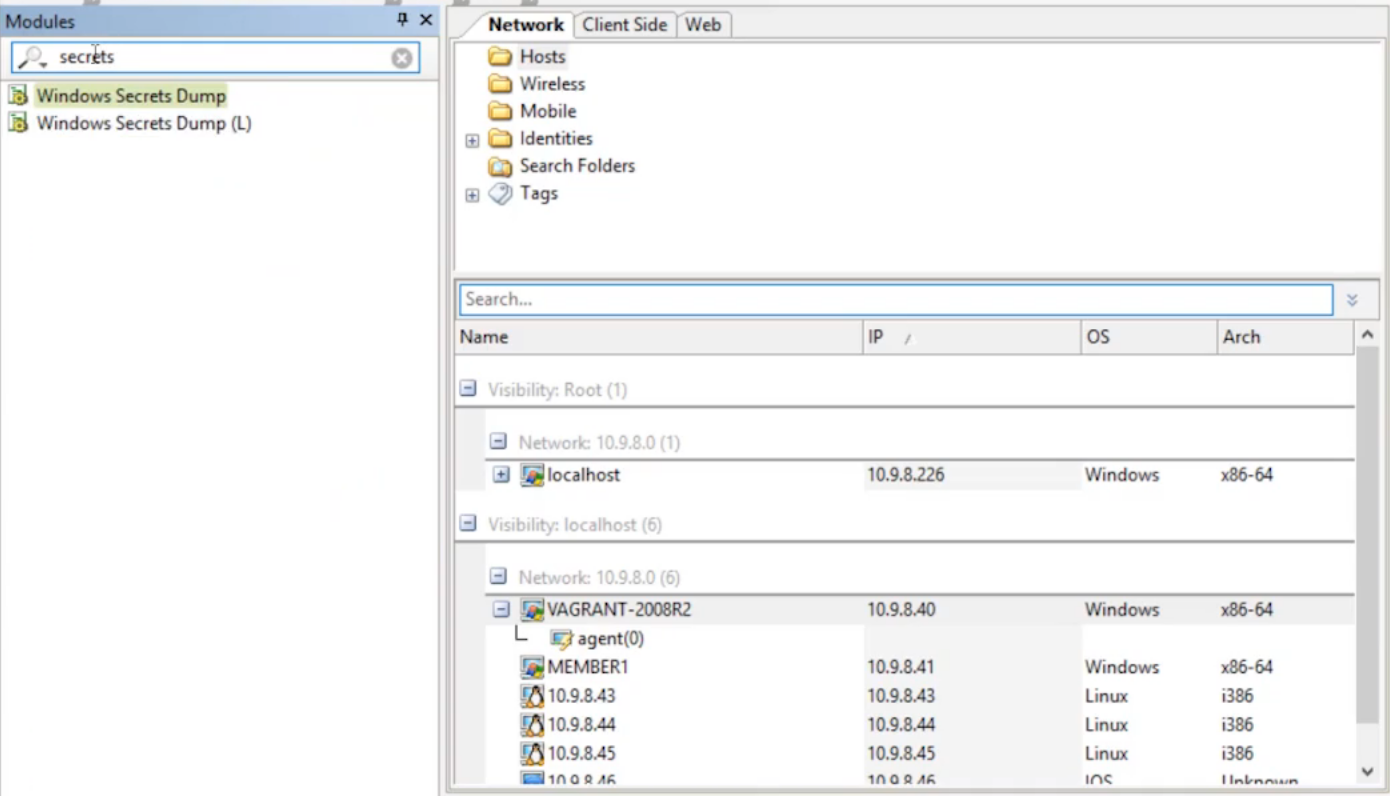
Going back to the modules field, we’ll type “secrets” into to the search bar. Select the Windows Secret Dump and drag it onto Vagrant box.
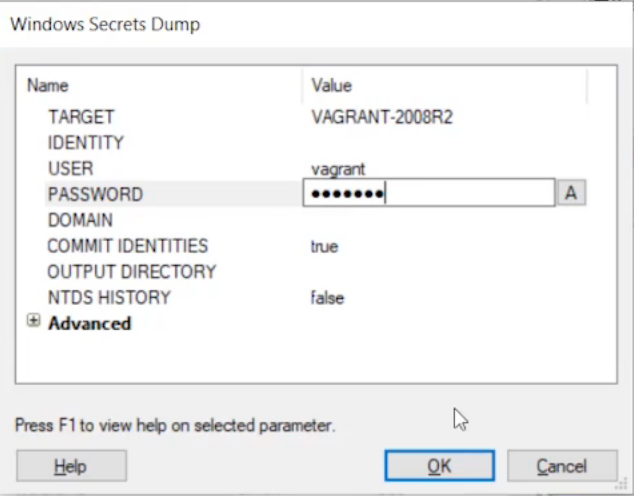
This opens a pop up box. The target is Vagrant, and we’ll use the identity that our agent is under. Hit OK.
The module will finish running after around 10 seconds. Let’s click on the module output tab to see if any secrets were available. Sure enough, there were a lot more identities available, many of which have hashes.
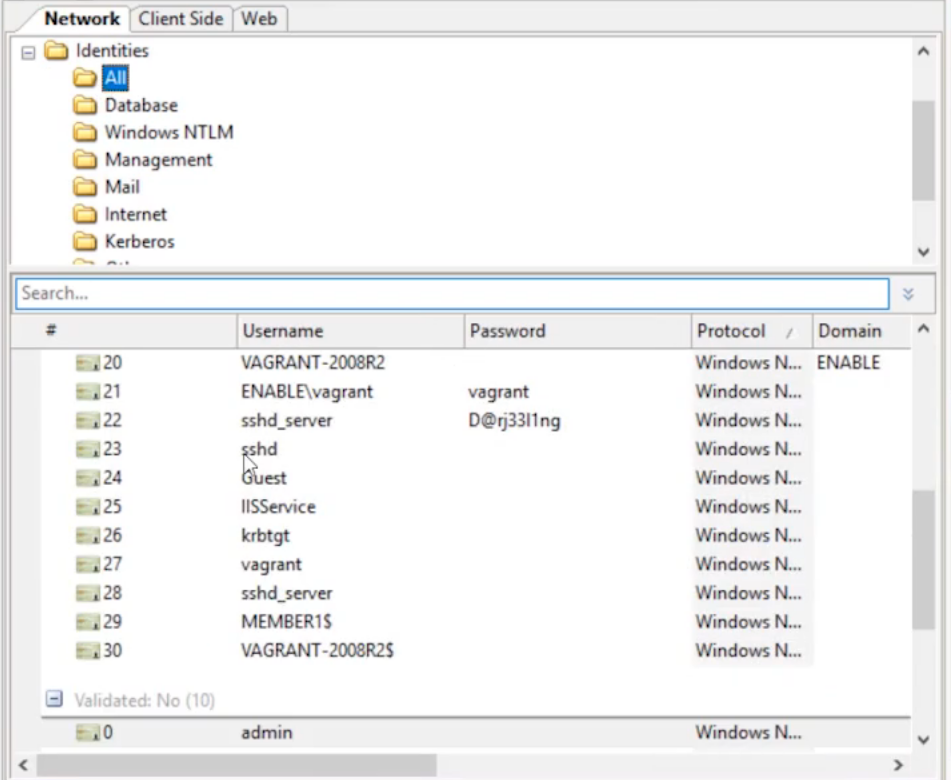
Next, click on the Identities folder. We’re now up to 30 identities, many of which have passwords listed.
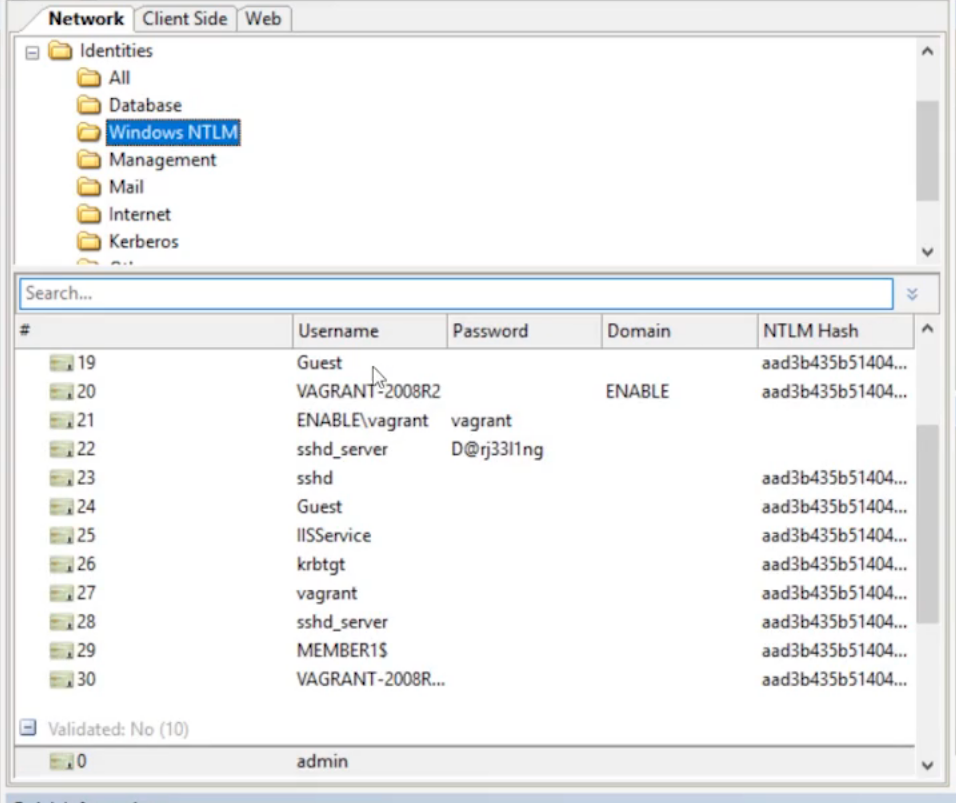
If we click on the Windows NTLM folder, we can see the different hashes.
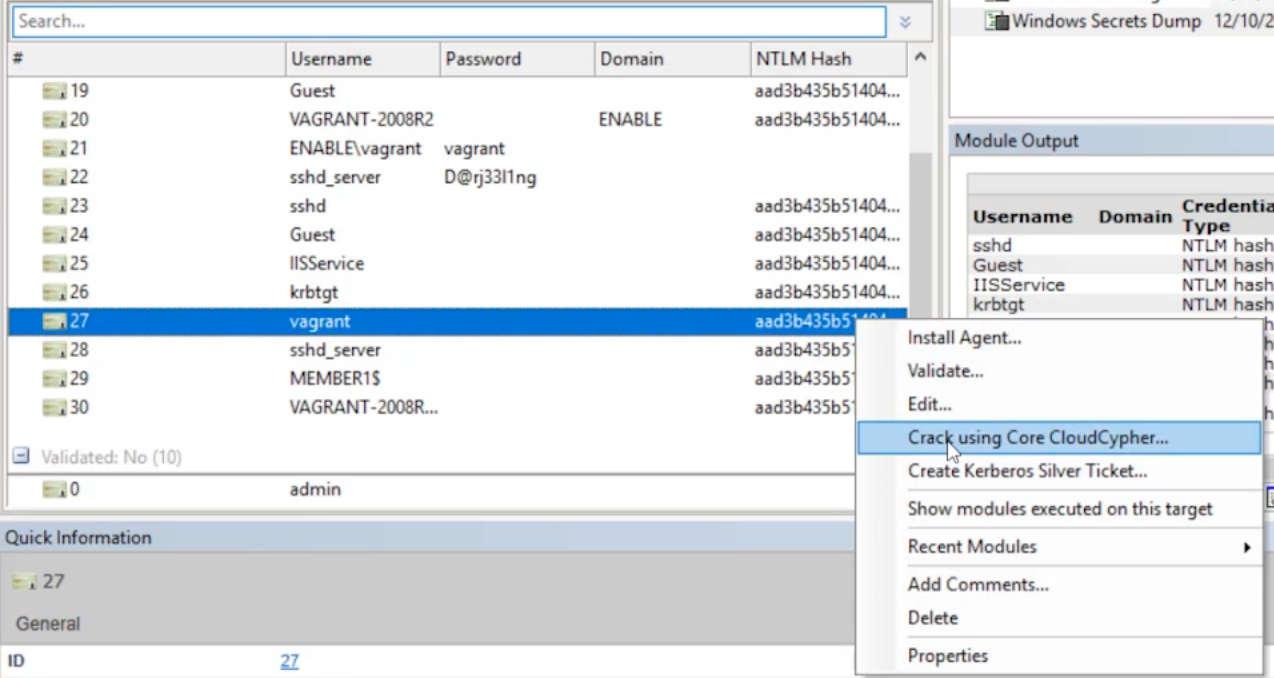
Right click on the vagrant identity and select Crack using Core CloudCypher.
A pop up box will appear. Click OK.
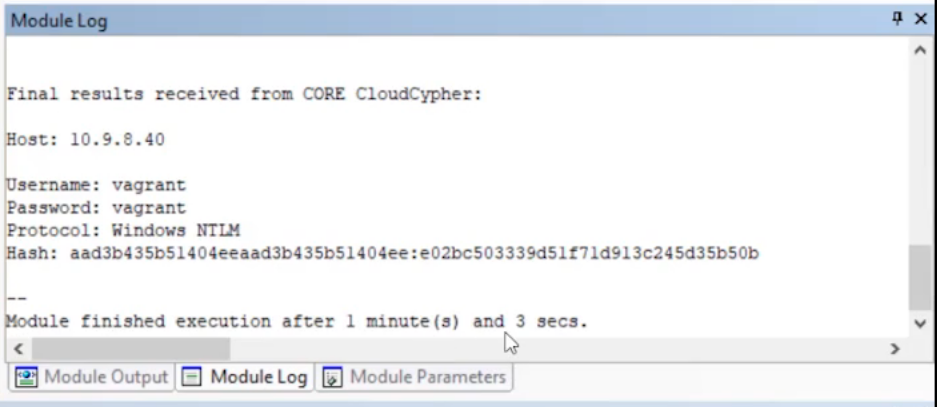
The module will run until it’s finished. Click on the Module Log tab to see the password from the cracked hash.