Cobalt Strike
Software for Adversary Simulations and Red Team Operations
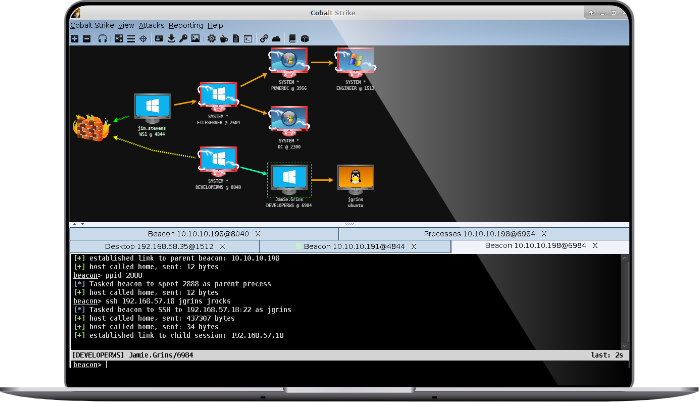
Cobalt Strike is a powerful threat emulation tool that provides a post-exploitation agent and covert channels ideal for Adversary Simulations and Red Team exercises. With Cobalt Strike, companies can emulate the tactics and techniques of a quiet long-term embedded threat actor in an IT network. Malleable C2 lets you change your network indicators to look like different malware each time. These tools complement Cobalt Strike's solid social engineering process, its robust collaboration capability, and unique reports designed to aid blue team training.
Interoperable Products
Cobalt Strike Pricing
New Cobalt Strike licenses cost as low as $3,540*, per user for a one-year license.
If you’re interested in more details on cost check out the full pricing page.