How Event Manager Helps Organizations Comply with PCI DSS
Using SIEM for PCI DSS compliance
The Payment Card Industry Data Security Standard (PCI-DSS) is administered by the Payment Card Industry Security Standards Council and focuses on securing networks, systems, and other payment card processing equipment. Many organizations must stay in compliance with this standard, as it applies to anyone who accepts credit/debit cards for any product or intangible offering worldwide.
Event Manager is a powerful Security Information and Event Management (SIEM) solution that ensures critical events get the attention they require. In addition to helping your IT environment stay secure, Event Manager helps you follow PCI by providing a compliance view that detects and displays information relevant to PCI and allows you to generate reports that prove adherence and demonstrates customer data is properly managed.
PCI DSS Requirements Event Manager Can Help Satisfy
Event Manager can help you meet many aspects of the PCI requirements. The table below outlines these requirements and explains how Event Manager's monitoring, insights, audit trail, and reporting capabilities can apply.
|
REQUIREMENT |
HOW EVENT MANAGER CAN HELP |
|
Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters. |
|
|
2.2 Develop configuration standards for all system components that address all known security vulnerabilities and are consistent with industry-accepted definitions. Update system configuration standards as new vulnerability issues are identified. |
Documents and audits the security configuration standards of your systems. |
|
2.4 Maintain an inventory of system components that are in scope for PCI DSS. |
Documents and audits the security configuration standards of your systems. |
|
Requirement 6: Develop and maintain secure systems and applications. |
|
|
6.3 Develop internal and external software applications including web-based administrative access to applications in accordance with PCI DSS and based on industry best practices. Incorporate information security throughout the software development life cycle. This applies to all software developed internally as well as bespoke or custom software developed by a third party. |
Ensures pre-production accounts are not deployed into production systems. |
|
Requirement 7: Restrict access to cardholder data by business need-to-know. |
|
|
7.1 Limit access to system components and cardholder data to only those individuals whose job requires such access. |
Reports on requirements to business owners and audit that the enforcing solution continues to meet PCI standards, and has not been subverted. |
|
7.2 Establish an access control system for systems components that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed. |
Reports on requirements to business owners and audit that the enforcing solution continues to meet PCI standards, and has not been subverted. |
| Requirement 8: Identify and authenticate access to system components. | |
|
8.1 Define and implement policies and procedures to ensure proper user identification management for users and administrators on all system components. Assign all users a unique user name before allowing them to access system components or cardholder data. |
Monitors user inactivity to help ensure inactive accounts are removed/disabled within 90 days. Event Manager can prevent repeated access attempts by locking out the user ID after not more than six attempts. |
|
Requirement 10: Track and monitor all access to network resources and cardholder data. |
|
|
10.1 Implement audit trails to link all access to system components to each individual user. |
Provides lists of all login failure events and privilege escalations. Additionally, it can generate reports that can provide detail into any actions taken, including any changes, additions, or deletions to any account by a root or administrator user. |
|
10.2 Implement automated audit trails for all system components. |
Provides lists of all login failure events and privilege escalations. Additionally, it can generate reports that can provide detail into any actions taken, including any changes, additions, or deletions to any account by a root or administrator user. |
|
10.3 Record audit trail entries for all system components for each event. |
Logs and creates audit trail alerts and generate reports. |
|
10.4 Using time synchronization technology, synchronize all critical system clocks and times and implement controls for acquiring, distributing, and storing time. |
Monitors and alerts on any unscheduled time and date changes. |
|
10.5 Secure audit trails so they cannot be altered. |
Transmits all logs to central management for alerting and redundancy. |
|
10.6 Review logs and security events for all system components to identify anomalies or suspicious activity. |
Reports on PCI related security events, and where appropriate generate alerts of suspicious activity for immediate Security Operations center action. |
|
10.7 Retain audit trail history for at least one year; at least three months of history must be immediately available for analysis. |
Defines and implements log retention periods of at least a year inside its database. |
|
Requirement 11: Regularly Test Security Systems & Processes. |
|
|
11.5 Deploy file integrity monitoring software to alert personnel to unauthorized modification of critical system files, configuration files or content files. Configure the software to perform critical file comparisons at least weekly. |
Prioritizes these events and alert appropriate personnel of these changes. |
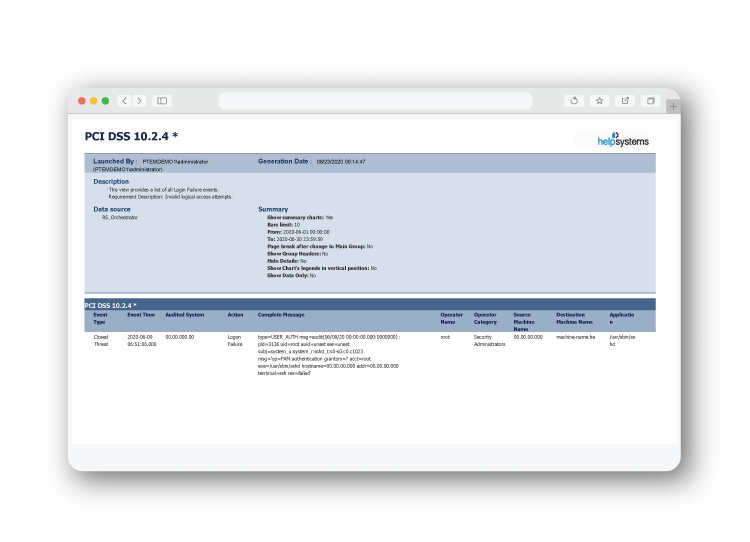
Out-of-the-Box PCI Compliance Reporting
Event Manager's compliance views provide a filtered view of any security events that may be relevant to PCI adherence, including:
- Login failure events
- Privilege escalation and subsequent actions taken
- Changes, additions, or deletions by a root account or administrator
- User inactivity events
- Account lockouts
These views are also used to easily generate built-in reports designed to highlight compliance with PCI-DSS. Reports can be conveniently scheduled to generate at any time.
Additionally, you can create any report you need with an intuitive interface to highlight any events, threats, and incidents. Reports are fully searchable and can also be exported into a variety of formats (PDF, CSV, DOC, XLS). Compliance views and reports are also available for other regulations like GDPR, BRCA, and SOX.
See How Event Manager Fits Into Your Compliance Strategy
Get an in-depth look at our one-size-fits-all SIEM solution with one of our experts and learn how to streamline your security while ensuring adherence to PCI and other regulations.