This 10-minute video covers local information gathering, identities, and privilege escalation in Core Impact.
Local Information Gathering
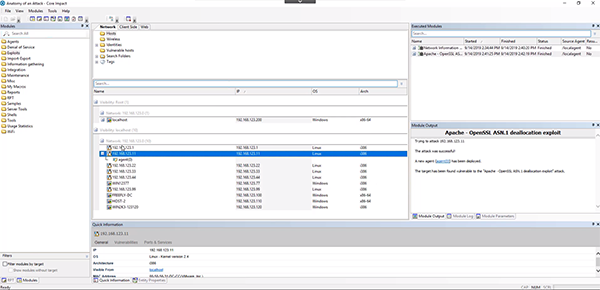
For this tutorial, we already have a pen test in Core Impact in progress. We have a web-facing user portal that we have successfully exploited with an Apache exploit and have a non-privileged agent on it. You can tell the agent is non-privileged because it has a yellow thunderbolt next to it.
Securing a Privileged Agent
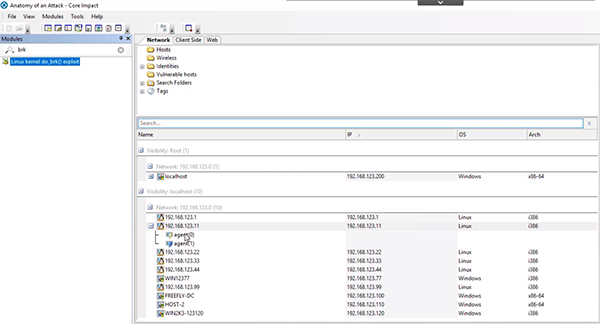
We can use a Linux kernel exploit on the non-privileged agent by dragging it over to the Apache agent. Once the module has completed running, it has popped a new agent and you can tell it is a privileged agent because it have a blue lightning bolt on it. This means the agent is operating as root.
Capturing a User Box
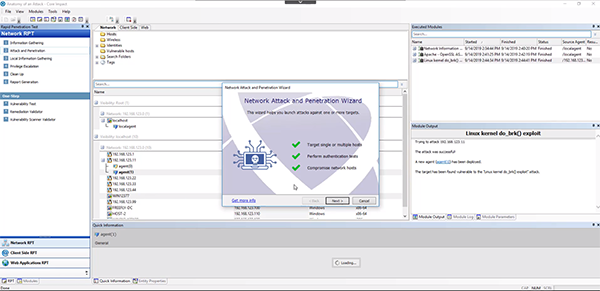
Now that we have a privileged agent on the inside, we can pivot into the network from outside the network. Right click on your privileged agent and select “Set as Source.” This means the system is communicating with the privileged agent and its launching all the exploits and attacks from the agent inside the network. This allows us to bypass everything outside the network. This should allow you to get an agent on the user terminal.
Drag and drop the “Attack and Penetration” RPT down to the box you want to target. You’ll want to stop launching exploits after you get an agent on the box so we don’t overload the system and raise any alarms. Use the standard settings of the rapid penetration test (RPT) to complete the process and get a privileged agent on the Windows box.
Gathering Identities
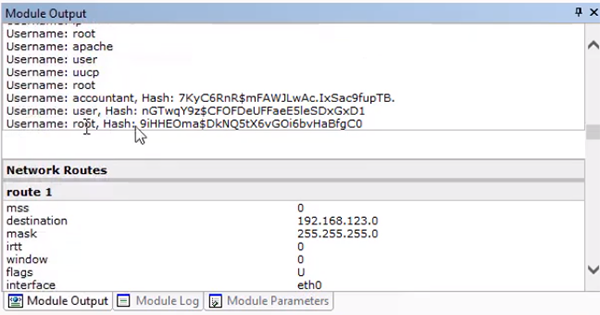
To capture more identities on the network, we can run the “Local Information Gathering” RPT on all the connected agents and use the standard Core Impact settings. This may take a little time since we kept everything selected.
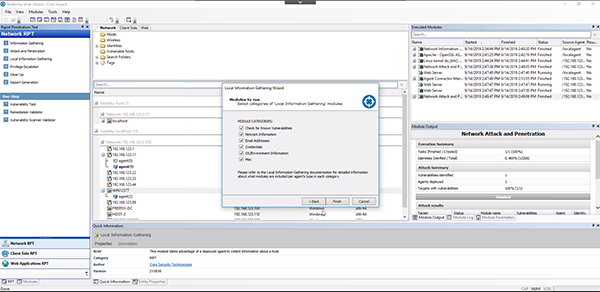
In this tutorial, we found 88 identities. In the “Local Information Gathering” section of the “Module Output” section we can see the lists of usernames and hashes. With this information there are a variety of different paths you can take to exploit the network further.