The belief that Linux is immune to malware has now been thoroughly dismissed, with Linux increasingly becoming a more popular, lucrative target. In fact, research indicates that Linux systems attacks have tripled since 2016 and that attackers of various skill levels have identified opportunities to exploit Linux directly.
With this increasing amount of Linux focused attacks, it’s more important than ever to ensure that your environment is as secure as possible. Despite this, common misconfigurations are still often to blame for serious attacks and breaches.
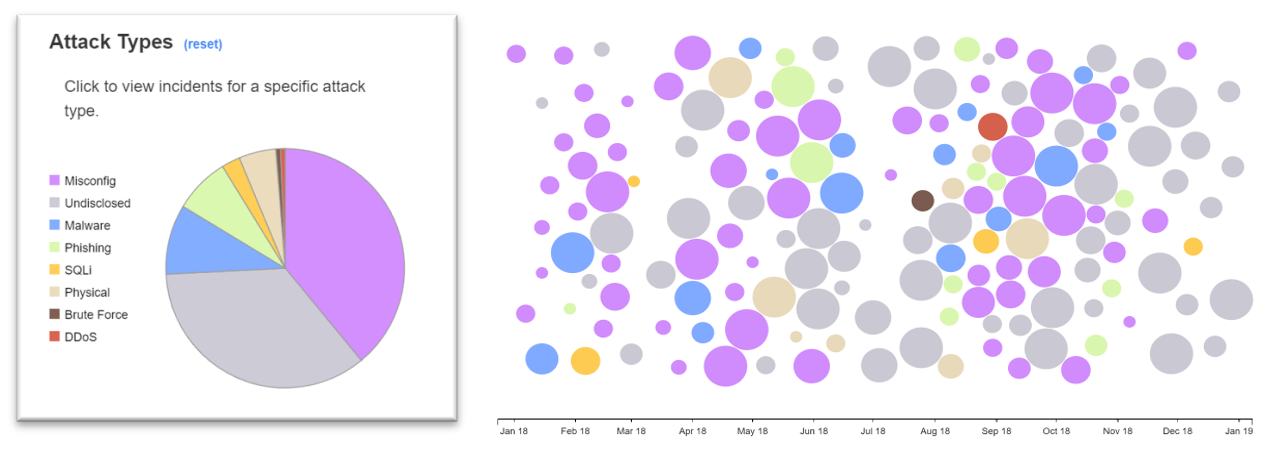
In the above chart, security incidents from January of 2018 through January of 2019 are visually represented through circles. Severity of attacks are indicated by size—the larger the circle, the larger the impact. Given the number of purple circles, which indicate misconfiguration, the fact is that simple misconfiguration of the computer systems was the source of a large percentage of security incidents.
Looking at that flurry of incidents at the start of 2018 many organizations chose to not disclose the reason anymore but there are still a few more large configuration circles. Experts at Fortra know from experience many of these unspecified incidents were configuration related.
Controls were available but either someone did not implement them or they were configured incorrectly which left the systems open to attack. This e-course aims to help you understand and fix basic Linux security mistakes, allowing you to spend time focusing on more complex security problems.