Pivoting is a popular technique that many penetration testers use to get deeper into the network and validate trust relationships between systems. This video covers how to pivot in Core Impact, including how to use agents to setup different vantage points.
The Importance of Pivoting
Pivoting is a popular feature of Core Impact and a technique a lot of penetration testers use to get through firewalls and/or get deeper into the network. Pivoting helps you safely validate the trust relationships between systems and test the “what if” scenarios.
Gathering Credentials
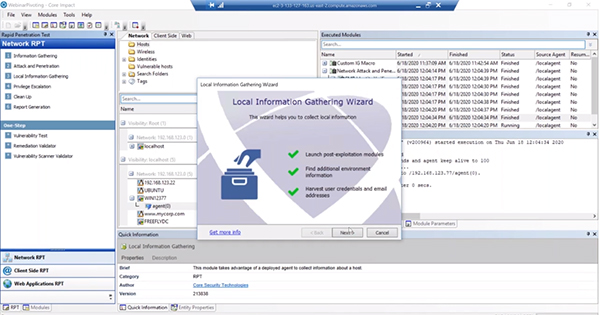
Once we have an agent in place within Core Impact we can look for credentials that might be on the machine by running the Local Information Gathering wizard. You’ll want to run it against all connected agents and select any of the module categories you’d like. Any of the credentials harvested will be listed in your Windows folder.
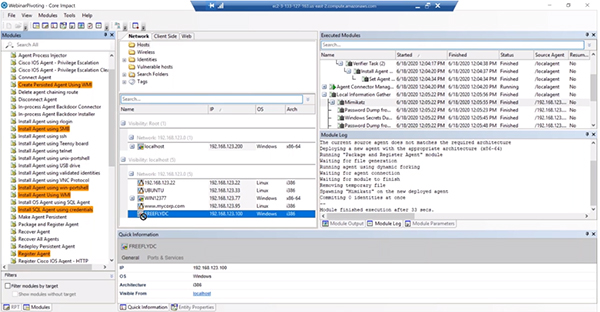
Now that we have some credentials, we can try to attack another machine with it. In this example, we are attacking the FREEFLYDC machine by going to the “Agents” folder and dragging it to the machine. You’ll need to grab the credential that you found earlier for the “Identity.” When you’re doing these types of attacks your connection method is very helpful to understand. Now we have another agent on the DC machine we just attacked.
Network Routes
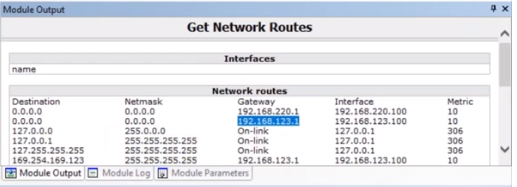
At this point, you can use the search to find the “Get Network Routes” module and drag it onto your new agent. It will automatically run for you and if you select the “Module Output” view it is much easier to read than the log output. We can tell from this that there is an additional network that this device is capable of pivoting off to.
You can do this by right-clicking on the agent within Core Impact and hitting the “Set as Source” option. Now all of the attacks and scanning will be coming from that agent. You’ll find that any OS agent can be used as a pivot point, but some will prove to be a better choice than others. For example: root, admins, super users, etc.
Information Gathering
When you have a privileged agent you can install a Pcap Plugin to give you the capabilities to do passive information gathering. In this example, we ran the Information Gathering RPT on the new agent. You’ll want to enter the new network you found earlier in the “Network Range” field. You’ll see Core Impact scan the additional network from the new agent.
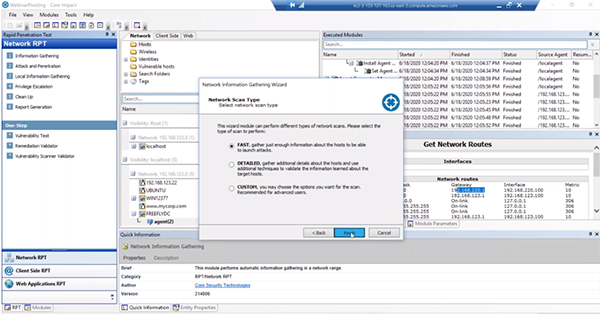
At this point you can continue the cycle to attack and penetrated the new machines found and repeat the process.
Wireshark
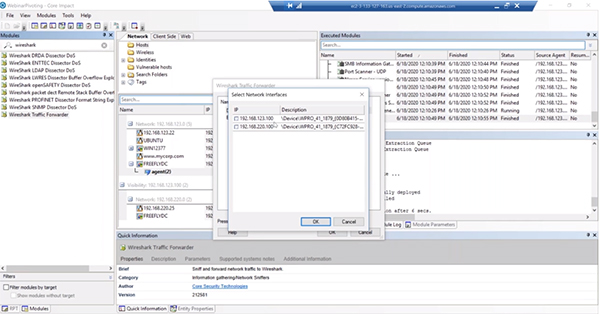
Core Impact does have Wireshark capabilities built into it and it is recommended to open it for greater visibility into what is happening. In order to run that you’ll need to run the Pcap Plugin.