One of the key steps of any penetration test starts with conducting information gathering. This video discusses how to perform information gathering across all three of the different vectors available in Core Impact.
Validating Scan Data With Core Impact
For today’s tutorial we’re going to start on the network vector or server side of Core Impact. There are several different scanners that Core Impact integrates with and provides the ability to import the results of your scans. From within the RPT menu, click “Information Gathering” and select the “Import data from results of 3rd party scanner” option. You’ll then just want to select the scanner you want to import from and select the location.
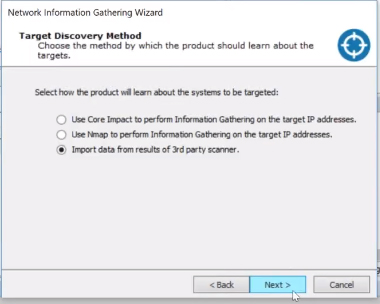
Core Impact is immediately going to go through the information gathering steps with the wizard. You can see it automatically grabs the scanner data and imports it and starts applying the information directly. Very quickly you’ll start seeing the machines you have available, their operating systems, and ports/services that might be listening.
Manual Information Gathering
We’ll run the information gathering RPT again in this example but will run the Nmap on the backend. The RPT wizard guides you through the each of the steps and you can customize as you see fit based on your needs. In this example, we’re going to select the “Detailed” network scan type to run a lot of different steps.
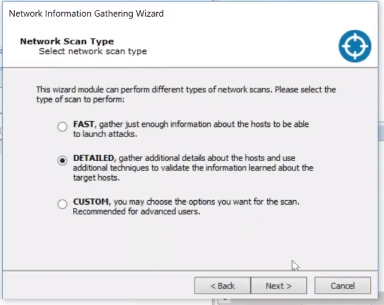
You’ll see Core Impact running through all the RPT steps. It actually puling from the folder system to run each of the applicable phases. It will identify ports on the network and OS detection. It’s important to allow the information gathering step to finish before starting your Attack and Penetration RPTs so you have all the information available to you as possible.
Web Application Information Gathering
When it comes to web application testing, Core Impact offers Information Gathering as well. It can also injest scan data or crawl a site as well. In this example we’ll select the “Information Gathering” option to kick off the RPT and crawl a known web application. Enter the domain you’d like to crawl and your proxy settings (if needed) to start capturing responses.
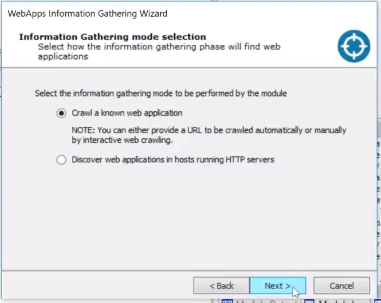
Now we can go directly to the page we’re crawling and start interacting with it to see what Core Impact captures. Back in Core Impact, you can now see a number of pages it captured.
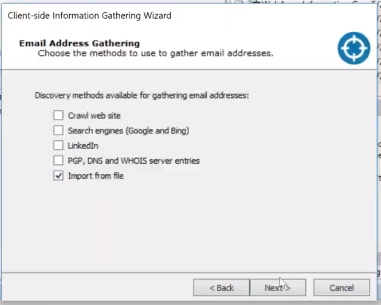
Client Side Information Gathering
You can also use the Information Gathering wizard to gather your details a number of different ways. You can import your contact details from a file and start attacking them with phishing email campaigns.